FileSharing
... Tracker tells client where to find other clients Query other clients for pieces of file Client downloads and uploads parts of file to each other until everyone has it ...
... Tracker tells client where to find other clients Query other clients for pieces of file Client downloads and uploads parts of file to each other until everyone has it ...
Network Intro
... the networks may have incompatible physical addresses & data representations there may be multiple paths from destination to source machines assigned to various functions may change no single entity can know where every thing is response times cannot be guaranteed Solution = "internetworki ...
... the networks may have incompatible physical addresses & data representations there may be multiple paths from destination to source machines assigned to various functions may change no single entity can know where every thing is response times cannot be guaranteed Solution = "internetworki ...
CCNA 3
... • Without summarization, Internet would collapse • Summarization reduces burden on upstream routers • This process of summarization continues until entire network is advertised as a single aggregate route • Summarization is also called supernetting • Possible if the routers of a network run a classl ...
... • Without summarization, Internet would collapse • Summarization reduces burden on upstream routers • This process of summarization continues until entire network is advertised as a single aggregate route • Summarization is also called supernetting • Possible if the routers of a network run a classl ...
06/07 Semester B - City University of Hong Kong
... draw the designed switching network. Note that m = M (N + M)0.5 where m is the number of inlets in primary switch modules. [7 marks] (b) In what sense a multiple-stage switch is better than a single-stage switch? What are the disadvantages of a multiple-stage switch when compared with a single-stag ...
... draw the designed switching network. Note that m = M (N + M)0.5 where m is the number of inlets in primary switch modules. [7 marks] (b) In what sense a multiple-stage switch is better than a single-stage switch? What are the disadvantages of a multiple-stage switch when compared with a single-stag ...
CCNA 3
... • Without summarization, Internet would collapse • Summarization reduces burden on upstream routers • This process of summarization continues until entire network is advertised as a single aggregate route • Summarization is also called supernetting • Possible if the routers of a network run a classl ...
... • Without summarization, Internet would collapse • Summarization reduces burden on upstream routers • This process of summarization continues until entire network is advertised as a single aggregate route • Summarization is also called supernetting • Possible if the routers of a network run a classl ...
Network Topology
... • In 1969; man called Roberts had an issue with network topology • he needed an expert help. for that reason he went to Dr. Frank who's the founder of (NAC) Network Analysis Corporation that is specialized of network topological design • In 1972; the system was ready and researchers have installed t ...
... • In 1969; man called Roberts had an issue with network topology • he needed an expert help. for that reason he went to Dr. Frank who's the founder of (NAC) Network Analysis Corporation that is specialized of network topological design • In 1972; the system was ready and researchers have installed t ...
Talk slides
... periodically. If a loop is detected, the member will disconnect from its parent and rejoin the ...
... periodically. If a loop is detected, the member will disconnect from its parent and rejoin the ...
COS
461:
Computer
Networks
Midterm
Review Spring
2011
... Routers in rest of Internet just need to know how to reach 201.10.0.0/21. Provider can direct IP packets to appropriate customer. ...
... Routers in rest of Internet just need to know how to reach 201.10.0.0/21. Provider can direct IP packets to appropriate customer. ...
arpn-jeas-icstartemplate
... connected conventionally by particular media and interface. In addition, the introduction of all-packet switched system in Long Term Evolution-Advanced (LTE-A) technology has provided a capability to virtualize the network. Based on our knowledge, there are not so many works in this area. The prelim ...
... connected conventionally by particular media and interface. In addition, the introduction of all-packet switched system in Long Term Evolution-Advanced (LTE-A) technology has provided a capability to virtualize the network. Based on our knowledge, there are not so many works in this area. The prelim ...
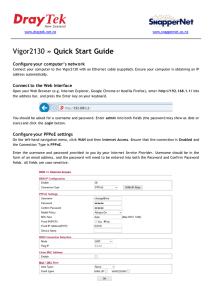
Vigor2130 » Quick Start Guide
... Configure your computer’s network Connect your computer to the Vigor2130 with an Ethernet cable (supplied). Ensure your computer is obtaining an IP address automatically. ...
... Configure your computer’s network Connect your computer to the Vigor2130 with an Ethernet cable (supplied). Ensure your computer is obtaining an IP address automatically. ...
Module 4 Part a - Pohang University of Science and Technology
... ICMP: Internet Control Message Protocol Internet Control Message Protocol (ICMP), RFC792 The purpose of ICMP messages is to provide feedback about problems in the IP network environment Delivered in IP packets ...
... ICMP: Internet Control Message Protocol Internet Control Message Protocol (ICMP), RFC792 The purpose of ICMP messages is to provide feedback about problems in the IP network environment Delivered in IP packets ...
CV (Word) - OoCities
... Engica tech support. Responsible for system documentation such as Product Installation Guide, Installation Verification Procedures, Support Documentation. Handover to production support. Support of system test, UAT and Live environments during Storm period. Calls logged on Vantive Peoplesoft CRM. Su ...
... Engica tech support. Responsible for system documentation such as Product Installation Guide, Installation Verification Procedures, Support Documentation. Handover to production support. Support of system test, UAT and Live environments during Storm period. Calls logged on Vantive Peoplesoft CRM. Su ...
Penetration Testing Presentation
... • “the practice of obtaining confidential information by manipulation of legitimate users” (Wikipedia) • Examples: Lord Nikon and Cereal Killah from Hackers (the most realistic hacking movie ever). • Relying on people not reading the EULAs – the ...
... • “the practice of obtaining confidential information by manipulation of legitimate users” (Wikipedia) • Examples: Lord Nikon and Cereal Killah from Hackers (the most realistic hacking movie ever). • Relying on people not reading the EULAs – the ...
Document
... Configure, verify and analyze static NAT, dynamic NAT and NAT with overloading. Instructor Note: This activity can be completed individually or in small or large groups. ...
... Configure, verify and analyze static NAT, dynamic NAT and NAT with overloading. Instructor Note: This activity can be completed individually or in small or large groups. ...
layer - Open Learning Environment - Free University of Bozen
... OSI – Interaction Modalities • Connectionless: every package managed independently from the others – No guaranteed QoS – No memory nor negotiation, just isolated ...
... OSI – Interaction Modalities • Connectionless: every package managed independently from the others – No guaranteed QoS – No memory nor negotiation, just isolated ...
A Study on Quality of Service Issues
... Can be reduced by using Jitter buffers – To allow for variable packet arrival times and still achieve steady stream of packets, the receiver holds the first packet in a jitter buffer , before playing it out. ...
... Can be reduced by using Jitter buffers – To allow for variable packet arrival times and still achieve steady stream of packets, the receiver holds the first packet in a jitter buffer , before playing it out. ...
354603Specification
... The Dual Band Repeater is Mainly used for providing free WiFi service in big area such as factory, community, street or etc. For example, the normal enhancer can expend distance up to 300 meters away. If there are more repeaters or more bigger power repeater, the range will extended further; the Rep ...
... The Dual Band Repeater is Mainly used for providing free WiFi service in big area such as factory, community, street or etc. For example, the normal enhancer can expend distance up to 300 meters away. If there are more repeaters or more bigger power repeater, the range will extended further; the Rep ...
What is a TOPOLOGY? Network topology is the arrangement of the
... 2) Cable length required for this topology is the least compared to other networks. 3) Bus topology costs very less. 4) Linear Bus network is mostly used in small networks. Good for LAN. Disadvantages (Drawbacks) of Linear Bus Topology 1) There is a limit on central cable length and number of nodes ...
... 2) Cable length required for this topology is the least compared to other networks. 3) Bus topology costs very less. 4) Linear Bus network is mostly used in small networks. Good for LAN. Disadvantages (Drawbacks) of Linear Bus Topology 1) There is a limit on central cable length and number of nodes ...
File
... Chapter 1 Computer Networks and the Internet 1 1.1 What Is the Internet? 2 1.2 The Network Edge 9 1.3 The Network Core 22 1.4 Delay, Loss, and Throughput in Packet-Switched Networks 35 1.5 Protocol Layers and Their Service Models 47 1.6 Networks Under Attack 55 1.7 History of Compute ...
... Chapter 1 Computer Networks and the Internet 1 1.1 What Is the Internet? 2 1.2 The Network Edge 9 1.3 The Network Core 22 1.4 Delay, Loss, and Throughput in Packet-Switched Networks 35 1.5 Protocol Layers and Their Service Models 47 1.6 Networks Under Attack 55 1.7 History of Compute ...
Telecommunication Transmission and Switching System
... •The source may be a simple telephone microphone, keyboard •The destination may be a simple telephone speaker, monitor ...
... •The source may be a simple telephone microphone, keyboard •The destination may be a simple telephone speaker, monitor ...
Distributed Systems3. Protocol Hierarchies, OSI and TCP/IP
... • We can take the OSI reference model for the physical layer + data link ...
... • We can take the OSI reference model for the physical layer + data link ...
Windows 2000 Advanced Server
... E-commerce applications that handle heavier workloads and high-priority processes. Server Clusters provide high availability for applications using failover. Multiple nodes use Network Load Balancing. NLB balances the load of IP traffic across a set of up to 32 identical servers. Note: With .Net ser ...
... E-commerce applications that handle heavier workloads and high-priority processes. Server Clusters provide high availability for applications using failover. Multiple nodes use Network Load Balancing. NLB balances the load of IP traffic across a set of up to 32 identical servers. Note: With .Net ser ...
Multi-Mode ADSL Bridge/Router
... upgraded from a G.Lite service to a Full-Rate service or vice versa ...
... upgraded from a G.Lite service to a Full-Rate service or vice versa ...
IPv6 for UPnP Forum
... Teredo: Automatic tunneling of IPv6 over UDP/IPv4 Works through NAT, may be blocked by firewalls ISATAP: Automatic tunneling of IPv6 over IPv4 For connecting IPv6 islands to IPv4 network in the enterprise Enables gradual migration to IPv6 ...
... Teredo: Automatic tunneling of IPv6 over UDP/IPv4 Works through NAT, may be blocked by firewalls ISATAP: Automatic tunneling of IPv6 over IPv4 For connecting IPv6 islands to IPv4 network in the enterprise Enables gradual migration to IPv6 ...