Part 1
... IP addressing: introduction Q: how are interfaces actually connected? A: we’ll learn about that in chapter 5, 6. ...
... IP addressing: introduction Q: how are interfaces actually connected? A: we’ll learn about that in chapter 5, 6. ...
Discovering Computers Fundamentals 3rd Edition
... act as server and other computers, or clients, access server ...
... act as server and other computers, or clients, access server ...
ZMS - TSC Innovation Co.,Ltd.
... elements and provisions subscribers and end-to-end services within the Zhone environment. It also handles element software downloads. The manager supports the use of templates, which allow the operator to streamline configuration tasks. Accounting Manager collects information on subscriber voice and ...
... elements and provisions subscribers and end-to-end services within the Zhone environment. It also handles element software downloads. The manager supports the use of templates, which allow the operator to streamline configuration tasks. Accounting Manager collects information on subscriber voice and ...
Chapter 4 slides - Uppsala University
... telephones simple inside network, complexity inside complexity at “edge” network many link types different characteristics uniform service difficult Network Layer ...
... telephones simple inside network, complexity inside complexity at “edge” network many link types different characteristics uniform service difficult Network Layer ...
Slide 1
... packets, modifies them, and inserts them back into network. • It is technically possible for the attacker to control what data are sent between the two hosts. • Can be achieved by ARP poisoning. – The attacker sets up two NICs and sends packets to each host, falsely notifying the host of the other h ...
... packets, modifies them, and inserts them back into network. • It is technically possible for the attacker to control what data are sent between the two hosts. • Can be achieved by ARP poisoning. – The attacker sets up two NICs and sends packets to each host, falsely notifying the host of the other h ...
01a-TheBigPicture-PartA
... Objected Oriented Languages – Allows programmers to group data and program instructions together into modules or objects that can more easily be maintained by the ...
... Objected Oriented Languages – Allows programmers to group data and program instructions together into modules or objects that can more easily be maintained by the ...
CA Performance Management for Enterprises
... monitors, stores, analyzes and displays massive amounts of performance information for assuring quality across service providers’ complex, multi-technology, multi-vendor network infrastructures. Designed for high scalability at low cost, the solution enables proactive capacity planning and problem-s ...
... monitors, stores, analyzes and displays massive amounts of performance information for assuring quality across service providers’ complex, multi-technology, multi-vendor network infrastructures. Designed for high scalability at low cost, the solution enables proactive capacity planning and problem-s ...
True Number Portability and Advanced Call Screening in a SIP
... plugged into an Ethernet port Support IP using an IP address that is obtained by Dynamic Host Configuration Protocol ( DHCP) » If the location is changed, the IP address automatically changed ...
... plugged into an Ethernet port Support IP using an IP address that is obtained by Dynamic Host Configuration Protocol ( DHCP) » If the location is changed, the IP address automatically changed ...
Cube400 IP - shm metering logo
... It is possible to change the Network setup using the browser by typing new values into the boxes in the Network Setup Pages. NOTE: As you change network settings using this method communications with the meter may be lost in the browser. For example if the IP Address is changed the meter will only b ...
... It is possible to change the Network setup using the browser by typing new values into the boxes in the Network Setup Pages. NOTE: As you change network settings using this method communications with the meter may be lost in the browser. For example if the IP Address is changed the meter will only b ...
Configuring Disk Quotas
... configure a printer in Red Hat Linux. This tool helps maintain the printer configuration file, print spool directories, and print filters. Starting with version 9, Red Hat Linux defaults to the CUPS (Common Unix Printing System). To use the Printer Configuration Tool you must have root privileges. T ...
... configure a printer in Red Hat Linux. This tool helps maintain the printer configuration file, print spool directories, and print filters. Starting with version 9, Red Hat Linux defaults to the CUPS (Common Unix Printing System). To use the Printer Configuration Tool you must have root privileges. T ...
ppt - Stanford Crypto group
... Label traffic flows at the edge of the network and let core routers identify the required class of service ...
... Label traffic flows at the edge of the network and let core routers identify the required class of service ...
1. Server and mainframes are types of computers used for
... users. large organizations. It is not designed for Need to be placed in a special individuals. and secured room which has a control climate. Allow user to access network through It is powerful yet expensive. client/server computing. Can be used by hundred of thousand of people at the same ...
... users. large organizations. It is not designed for Need to be placed in a special individuals. and secured room which has a control climate. Allow user to access network through It is powerful yet expensive. client/server computing. Can be used by hundred of thousand of people at the same ...
Discuss the Importance of Computer Networks
... Software and Protocols Client-Server Network Software Both client software and server software are needed on a clientserver network Client software makes requests Server software fulfills them ...
... Software and Protocols Client-Server Network Software Both client software and server software are needed on a clientserver network Client software makes requests Server software fulfills them ...
Delivery
... node in the group can receive any of the messages intended for that group Anycast (rarely) is useful in situations such as sending a message to a router, which typically has ...
... node in the group can receive any of the messages intended for that group Anycast (rarely) is useful in situations such as sending a message to a router, which typically has ...
IPv6 Rationale and Features
... is not reachable and routable from the public network. Therefore, the application does not work. For example, FTP [RFC959] with its separate control and data connections does not work if a NAT is in the path between the server and the client. To overcome this limitation, the NAT must understand each ...
... is not reachable and routable from the public network. Therefore, the application does not work. For example, FTP [RFC959] with its separate control and data connections does not work if a NAT is in the path between the server and the client. To overcome this limitation, the NAT must understand each ...
IP_Suite - Virginia Tech
... • Packets are routed to an organization based on the network address •To find the network address apply a netmask (default mask) AND netmask with address A netmask will retain the Netid of the block and sets the Hostid to 0s e.g., 190.240.7.91 class B, default mask is 255.255.0.0 network ad ...
... • Packets are routed to an organization based on the network address •To find the network address apply a netmask (default mask) AND netmask with address A netmask will retain the Netid of the block and sets the Hostid to 0s e.g., 190.240.7.91 class B, default mask is 255.255.0.0 network ad ...
CS335 Networking & Network Administration
... Routed protocols Any network protocol that provides enough information in its network layer address to allow a packet to be forwarded. Routed protocols define the field formats within a packet. Uses the routing table to forward packets. IP is an example of a routed protocol. Routing protocols Su ...
... Routed protocols Any network protocol that provides enough information in its network layer address to allow a packet to be forwarded. Routed protocols define the field formats within a packet. Uses the routing table to forward packets. IP is an example of a routed protocol. Routing protocols Su ...
3rd Edition: Chapter 2
... Problem definition (or research questions) Related work (no need to be complete) Approach (+supporting materials) Plans (including refining research questions + experimenting about ideas) 2: Application Layer ...
... Problem definition (or research questions) Related work (no need to be complete) Approach (+supporting materials) Plans (including refining research questions + experimenting about ideas) 2: Application Layer ...
CONNECTRIX VDX-6740B
... The Connectrix® VDX-6740B Top-of-Rack (ToR) switch redefines IP storage connectivity as the first Ethernet fabric switch purpose-built for IP storage. Designed for storage workloads it offers the network availability, deterministic performance and agility required for today’s business-critical appli ...
... The Connectrix® VDX-6740B Top-of-Rack (ToR) switch redefines IP storage connectivity as the first Ethernet fabric switch purpose-built for IP storage. Designed for storage workloads it offers the network availability, deterministic performance and agility required for today’s business-critical appli ...
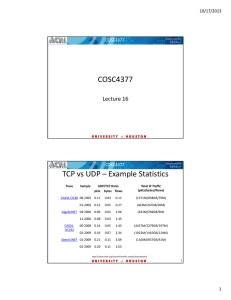
COSC4377 TCP vs UDP – Example Statistics
... routers. Routers advertise prefixes that identify the subnet(s) associated with a link, while hosts generate an "interface identifier" that uniquely identifies an interface on a subnet. An address is formed by combining the two. In the absence of routers, a host can only generate link‐local addre ...
... routers. Routers advertise prefixes that identify the subnet(s) associated with a link, while hosts generate an "interface identifier" that uniquely identifies an interface on a subnet. An address is formed by combining the two. In the absence of routers, a host can only generate link‐local addre ...
Class notes - Center For Information Management, Integration and
... • span a large geographic area, cross public property • often based on services provided by 3rd party companies, use telephone networks for transmission from one node to another • can be used to connect several LANs together • Routers attached to each LAN filter the network traffic to and from the W ...
... • span a large geographic area, cross public property • often based on services provided by 3rd party companies, use telephone networks for transmission from one node to another • can be used to connect several LANs together • Routers attached to each LAN filter the network traffic to and from the W ...
Lec02c-Interconnection Networks Part 2
... • Let s be the binary representation of the source and d be that of the destination processor. • The data traverses the link to the first switching node. If the most significant bits of s and d are the same, then the data is routed in pass-through mode by the switch else, it switches to crossover. • ...
... • Let s be the binary representation of the source and d be that of the destination processor. • The data traverses the link to the first switching node. If the most significant bits of s and d are the same, then the data is routed in pass-through mode by the switch else, it switches to crossover. • ...