PDF
... not monitored, then ESMs monitoring other hosts may be able to coordinate to derive guarantees about the behavior of unmonitored hosts. For example, if all of a host’s peers are monitored, then all of the host’s inputs and outputs will be seen by at least one ESM, even though the host itself is not ...
... not monitored, then ESMs monitoring other hosts may be able to coordinate to derive guarantees about the behavior of unmonitored hosts. For example, if all of a host’s peers are monitored, then all of the host’s inputs and outputs will be seen by at least one ESM, even though the host itself is not ...
Wireless Communication
... low power for battery use no special permissions or licenses needed to use the LAN robust transmission technology simplified spontaneous cooperation at meetings easy to use for everyone, simple management protection of investment in wired networks security (no one should be able to read my data), pr ...
... low power for battery use no special permissions or licenses needed to use the LAN robust transmission technology simplified spontaneous cooperation at meetings easy to use for everyone, simple management protection of investment in wired networks security (no one should be able to read my data), pr ...
Experiment Manual
... Experiment 3: Simulate a three node point-to-point network with the links connected as follows: n0 n2, n1 n2 and n2 n3. Apply TCP agent between n0-n3 and UDP between n1-n3. Apply relevant applications over TCP and UDP agents changing the parameter and determine the number of packets sent by TC ...
... Experiment 3: Simulate a three node point-to-point network with the links connected as follows: n0 n2, n1 n2 and n2 n3. Apply TCP agent between n0-n3 and UDP between n1-n3. Apply relevant applications over TCP and UDP agents changing the parameter and determine the number of packets sent by TC ...
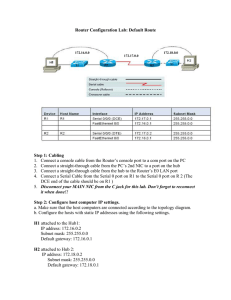
3 Router Configuration - Cisco Networking Academy
... Step 19 Show the active configuration file: Use the tables at the start of the lab to check the configuration you created. Check all IP addresses, subnet masks, passwords, routing protocols, network numbers, and host names. Router #show running-config (or show run) Step 20 Check to see that your ...
... Step 19 Show the active configuration file: Use the tables at the start of the lab to check the configuration you created. Check all IP addresses, subnet masks, passwords, routing protocols, network numbers, and host names. Router #show running-config (or show run) Step 20 Check to see that your ...
P.DG A4001N User Manual
... up to 8 Mbps downstream and 1 Mbps upstream. G.lite (or splitterless) ADSL provides up to 1.5 Mbps downstream and 512 kbps upstream. However, you should note that the actual rate provided by specific service providers may vary dramatically from these upper limits. Data passing between devices connec ...
... up to 8 Mbps downstream and 1 Mbps upstream. G.lite (or splitterless) ADSL provides up to 1.5 Mbps downstream and 512 kbps upstream. However, you should note that the actual rate provided by specific service providers may vary dramatically from these upper limits. Data passing between devices connec ...
I 1 - RPI ECSE - Rensselaer Polytechnic Institute
... Data does not have a clear administrative hierarchy Likely need to support a flat namespace Can one do this scalably? ...
... Data does not have a clear administrative hierarchy Likely need to support a flat namespace Can one do this scalably? ...
SNAP Network Operating System - Synapse forums
... than the Basic Encryption available in the normal firmware builds. (The AES-128 firmware may not be available in all jurisdictions.) SNAP devices from Synapse Wireless will ship with the most current release of the firmware installed. Synapse Wireless continually updates the software to include new fea ...
... than the Basic Encryption available in the normal firmware builds. (The AES-128 firmware may not be available in all jurisdictions.) SNAP devices from Synapse Wireless will ship with the most current release of the firmware installed. Synapse Wireless continually updates the software to include new fea ...
IPv6 Microsegmentation - Interop Conference Presentations
... Change the forwarding paradigm • First-hop network device is a router (layer-3 switch in marketese) • Fake router advertisements or ND/NA messages are not propagated to other hosts Simplistic implementation • Every host is in a dedicated /64 subnet • Default behavior on 3GPP and xDSL networks • Some ...
... Change the forwarding paradigm • First-hop network device is a router (layer-3 switch in marketese) • Fake router advertisements or ND/NA messages are not propagated to other hosts Simplistic implementation • Every host is in a dedicated /64 subnet • Default behavior on 3GPP and xDSL networks • Some ...
EdgeRouter Lite User Guide
... The EdgeOS software consists of five primary tabs, and some of these tabs have sub-tabs. This User Guide covers each tab with a chapter. For details on a specific tab, refer to the appropriate chapter. • Dashboard The “Dashboard Tab” on page 10 displays status information about services and interf ...
... The EdgeOS software consists of five primary tabs, and some of these tabs have sub-tabs. This User Guide covers each tab with a chapter. For details on a specific tab, refer to the appropriate chapter. • Dashboard The “Dashboard Tab” on page 10 displays status information about services and interf ...
(IP) routers
... sustainable network by functioning as a shared backup router. • Current commercial routers was not virtualized but implemented as a proprietary hardware and software. ...
... sustainable network by functioning as a shared backup router. • Current commercial routers was not virtualized but implemented as a proprietary hardware and software. ...
SCRIBE: A large-scale and decentralised application-level multicast infrastructure
... (Scalable Reliable Multicast Protocol) [4] and RMTP (Reliable Message Transport Protocol) [5] have added reliability. However, the use of multicast in applications has been limited because of the lack of wide scale deployment and the issue of how to track group membership. As a result, application-l ...
... (Scalable Reliable Multicast Protocol) [4] and RMTP (Reliable Message Transport Protocol) [5] have added reliability. However, the use of multicast in applications has been limited because of the lack of wide scale deployment and the issue of how to track group membership. As a result, application-l ...
No Slide Title
... establish one PVC connection to another physical interface or sub-interface on a remote router. In this case, each pair of the point-to-point routers is on its own subnet and each point-to-point sub-interface would have a single DLCI. In a point-to-point environment, each sub-interface is acting lik ...
... establish one PVC connection to another physical interface or sub-interface on a remote router. In this case, each pair of the point-to-point routers is on its own subnet and each point-to-point sub-interface would have a single DLCI. In a point-to-point environment, each sub-interface is acting lik ...
MPLS Bandwidth Assured Layer 2 Services
... • Transparent LAN service (pointto-point TLS or EWS - EoMPLS) • VPLS • Switched backbone • Point-to-point TLS (Ethernet Wire Service) • Multipoint TLS over L2 core (EMS) • Ethernet access into MPLS/VPN supported in the MPLS VPN Application MPLS Oct Announcement ...
... • Transparent LAN service (pointto-point TLS or EWS - EoMPLS) • VPLS • Switched backbone • Point-to-point TLS (Ethernet Wire Service) • Multipoint TLS over L2 core (EMS) • Ethernet access into MPLS/VPN supported in the MPLS VPN Application MPLS Oct Announcement ...
Exploration CCNA4 - Information Systems Technology
... When you build a WAN, there is always 3 components, –DTE –DCE –The component sits in the middle, joining the 2 access points. ...
... When you build a WAN, there is always 3 components, –DTE –DCE –The component sits in the middle, joining the 2 access points. ...
of disk - EECS Instructional Support Group Home Page
... • Shared vs. Switched: • Switched: pairs (“point-topoint” connections) communicate at same time • Shared: 1 at a time (CSMA/CD) ...
... • Shared vs. Switched: • Switched: pairs (“point-topoint” connections) communicate at same time • Shared: 1 at a time (CSMA/CD) ...
3810 Switch Series PDF
... • Border Gateway Protocol (BGP) provides IPv4 Border Gateway Protocol routing, which is scalable, robust, and flexible • Routing Information Protocol (RIP) provides RIPv1, RIPv2, and RIPng Security • Source-port filtering allows only specified ports to communicate with each other • RADIUS/TACACS+ ea ...
... • Border Gateway Protocol (BGP) provides IPv4 Border Gateway Protocol routing, which is scalable, robust, and flexible • Routing Information Protocol (RIP) provides RIPv1, RIPv2, and RIPng Security • Source-port filtering allows only specified ports to communicate with each other • RADIUS/TACACS+ ea ...
Window Query Processing in Highly Dynamic Geo
... • Energy efficiency. Sensor nodes are driven by a extremely frugal battery resource, which necessitates the network design and operation be done in an energy-efficient manner. In order to maximize the lifetime of sensor networks, the system needs a suite of aggressive energy optimization techniques, ...
... • Energy efficiency. Sensor nodes are driven by a extremely frugal battery resource, which necessitates the network design and operation be done in an energy-efficient manner. In order to maximize the lifetime of sensor networks, the system needs a suite of aggressive energy optimization techniques, ...
Powerpoint - Workshops
... examples are ISIS and OSPF used for carrying infrastructure addresses NOT used for carrying Internet prefixes or customer prefixes design goal is to minimise number of prefixes in IGP to aid scalability and rapid convergence ...
... examples are ISIS and OSPF used for carrying infrastructure addresses NOT used for carrying Internet prefixes or customer prefixes design goal is to minimise number of prefixes in IGP to aid scalability and rapid convergence ...
IPv6-Only UE + 464xLAT
... • Most things work fine with IPv6-only + NAT64/DNS64 • Web, email, … work fine. No user impact • ~85% of Android apps work fine, similar general experience with Symbian apps (Ovi) • Apps are developed in modern SDKs with high-level APIs that work well with IPv6 • Some things don’t work with IPv6-onl ...
... • Most things work fine with IPv6-only + NAT64/DNS64 • Web, email, … work fine. No user impact • ~85% of Android apps work fine, similar general experience with Symbian apps (Ovi) • Apps are developed in modern SDKs with high-level APIs that work well with IPv6 • Some things don’t work with IPv6-onl ...
Buffer Allocation in Wireless Multimedia Networks Using
... Wireless multimedia networks are the need of today’s society. There is tremendous demand for multimedia applications over wireless cellular networks. Some of the applications are, video conferencing, Internet multimedia games, and e-commerce. To provide all such applications in wireless networks, we ...
... Wireless multimedia networks are the need of today’s society. There is tremendous demand for multimedia applications over wireless cellular networks. Some of the applications are, video conferencing, Internet multimedia games, and e-commerce. To provide all such applications in wireless networks, we ...
DRCP - Telcordia
... When moving within the foreign domain, MH retains its care-of-address. Base stations are capable of decapsulating packets and forwarding it to the mobile host. Base station also determines whether to redirect the registration to special routers in the domain or to the HA. ...
... When moving within the foreign domain, MH retains its care-of-address. Base stations are capable of decapsulating packets and forwarding it to the mobile host. Base station also determines whether to redirect the registration to special routers in the domain or to the HA. ...
Recursive InterNetwork Architecture (RINA)

The Recursive InterNetwork Architecture (RINA) is a computer network architecture that unifies distributed computing and telecommunications. RINA's fundamental principle is that computer networking is just Inter-Process Communication or IPC. RINA reconstructs the overall structure of the Internet, forming a model that comprises a single repeating layer, the DIF (Distributed IPC Facility), which is the minimal set of components required to allow distributed IPC between application processes. RINA inherently supports mobility, multi-homing and Quality of Service without the need for extra mechanisms, provides a secure and programmable environment, motivates for a more competitive marketplace, and allows for a seamless adoption.