DSL-302T ADSL Modem User`s Manual
... shall be to replace the non-conforming Software (or defective media) with software that substantially conforms to D-Link’s functional specifications for the Software or to refund at D-Link’s sole discretion. Except as otherwise agreed by D-Link in writing, the replacement Software is provided only t ...
... shall be to replace the non-conforming Software (or defective media) with software that substantially conforms to D-Link’s functional specifications for the Software or to refund at D-Link’s sole discretion. Except as otherwise agreed by D-Link in writing, the replacement Software is provided only t ...
Energy-Aware Adaptive Routing Solutions in IP-over-WDM Networks Filip Idzikowski
... of GA. EWA outperformed LFA and achieved results similar to the GA, having lower computation times and smoother changes of power consumption. The overload is marginal, and observed mainly in the initial phase of the evaluation, when EWA could not use the network configuration from previous time peri ...
... of GA. EWA outperformed LFA and achieved results similar to the GA, having lower computation times and smoother changes of power consumption. The overload is marginal, and observed mainly in the initial phase of the evaluation, when EWA could not use the network configuration from previous time peri ...
Slide 1
... – It requires ability to send and receive at the same time - here the received signal is weak compared to the sent signal, so it’s expensive to make hardware to do this – The hidden terminal problem and fading make it impossible to detect all collisions ...
... – It requires ability to send and receive at the same time - here the received signal is weak compared to the sent signal, so it’s expensive to make hardware to do this – The hidden terminal problem and fading make it impossible to detect all collisions ...
Network Probe User Guide
... Changing the data in the charts ............................................................................................. 20 Sorting a table column ........................................................................................................ 22 Searching for network traffic details .. ...
... Changing the data in the charts ............................................................................................. 20 Sorting a table column ........................................................................................................ 22 Searching for network traffic details .. ...
Avaya Virtual Services Platform 8404
... every service change; service change is only configured at the Edge of the network, and this has dramatic impacts for the entire change paradigm. Network segmentation means that each service is uniquely encapsulated and carried independent of every other service. Leveraging a single unified protoco ...
... every service change; service change is only configured at the Edge of the network, and this has dramatic impacts for the entire change paradigm. Network segmentation means that each service is uniquely encapsulated and carried independent of every other service. Leveraging a single unified protoco ...
slides - network systems lab @ sfu
... •Using this protocol, peers can advertise their own resources, network service, identity, and discover the resources from other peers • Peer resources are published using XML-based metadata format ...
... •Using this protocol, peers can advertise their own resources, network service, identity, and discover the resources from other peers • Peer resources are published using XML-based metadata format ...
ex4-3-o-can
... • Paying for Frame Relay: • Oversubscription: • Service providers sometimes sell more capacity than they have on the assumption that not everyone will demand their entitled capacity all of the time. • Because of oversubscription, there will be instances when the sum of CIRs from multiple PVCs to a g ...
... • Paying for Frame Relay: • Oversubscription: • Service providers sometimes sell more capacity than they have on the assumption that not everyone will demand their entitled capacity all of the time. • Because of oversubscription, there will be instances when the sum of CIRs from multiple PVCs to a g ...
Passive Online Rogue Access Point Detection Using Sequential
... be difficult to manage. In contrast, our approach only requires a single monitoring point, and is easy to manage and maintain. The focus of [27] is on detecting protected layer3 rogue APs. Our approach is equally applicable to detect layer-2 or layer-3 rogue devices. The studies of [13, 19] detect r ...
... be difficult to manage. In contrast, our approach only requires a single monitoring point, and is easy to manage and maintain. The focus of [27] is on detecting protected layer3 rogue APs. Our approach is equally applicable to detect layer-2 or layer-3 rogue devices. The studies of [13, 19] detect r ...
Lecture 8 - cda college
... ATM LAN Design Uses LAN Emulation (LANE) Technique used to adapt ATM to Ethernet network by creating a multicast network to enable preassigned groups of Ethernet nodes to receive transmissions Vital for integrating ATM with non-ATM networks Uses ATM’s connection-oriented technology without requirin ...
... ATM LAN Design Uses LAN Emulation (LANE) Technique used to adapt ATM to Ethernet network by creating a multicast network to enable preassigned groups of Ethernet nodes to receive transmissions Vital for integrating ATM with non-ATM networks Uses ATM’s connection-oriented technology without requirin ...
iCAMView - SuperDroid Robots
... iCAMView is a compact stand-alone web-server capable of remote video surveillance. It can be accessed from anywhere in the world via a standard browser by entering the IP, account and password. Each system can simultaneously support any two combinations of USB PC cameras be it regular, infrared or p ...
... iCAMView is a compact stand-alone web-server capable of remote video surveillance. It can be accessed from anywhere in the world via a standard browser by entering the IP, account and password. Each system can simultaneously support any two combinations of USB PC cameras be it regular, infrared or p ...
Mobile Communications
... low power for battery use no special permissions or licenses needed to use the LAN robust transmission technology simplified spontaneous cooperation at meetings easy to use for everyone, simple management protection of investment in wired networks security (no one should be able to read my data), pr ...
... low power for battery use no special permissions or licenses needed to use the LAN robust transmission technology simplified spontaneous cooperation at meetings easy to use for everyone, simple management protection of investment in wired networks security (no one should be able to read my data), pr ...
DHCP - Personal Web Pages
... Allows DHCP server to differentiate between the two kinds of client machines e.g. process requests from two types of modems appropriately Some types of set-top boxes also set the VCI (Option 60) to inform ...
... Allows DHCP server to differentiate between the two kinds of client machines e.g. process requests from two types of modems appropriately Some types of set-top boxes also set the VCI (Option 60) to inform ...
NAT - Hong Kong University of Science and Technology
... far as outside word is concerned: no need to be allocated range of addresses from ISP: - just one IP address is used for all devices can change addresses of devices in local network without notifying outside world can change ISP without changing addresses of devices in local network devices ...
... far as outside word is concerned: no need to be allocated range of addresses from ISP: - just one IP address is used for all devices can change addresses of devices in local network without notifying outside world can change ISP without changing addresses of devices in local network devices ...
Interphase 4515 / 4525 / 4575 Manual
... This equipment has been tested and found to comply with the limits for a Class B digital device, pursuant to Part 15, Subpart B of the FCC Rules. This equipment generates, uses, and can radiate radio frequency energy. If not installed and used in accordance with the instructions, it may cause interf ...
... This equipment has been tested and found to comply with the limits for a Class B digital device, pursuant to Part 15, Subpart B of the FCC Rules. This equipment generates, uses, and can radiate radio frequency energy. If not installed and used in accordance with the instructions, it may cause interf ...
Data - WordPress.com
... low power for battery use no special permissions or licenses needed to use the LAN robust transmission technology simplified spontaneous cooperation at meetings easy to use for everyone, simple management protection of investment in wired networks security (no one should be able to read my data), pr ...
... low power for battery use no special permissions or licenses needed to use the LAN robust transmission technology simplified spontaneous cooperation at meetings easy to use for everyone, simple management protection of investment in wired networks security (no one should be able to read my data), pr ...
International Technical Support Organization High
... When you send information to IBM, you grant IBM a non-exclusive right to use or distribute the information in any way it believes appropriate without incurring any obligation to you. Copyright International Business Machines Corporation 1992 1993 1995. All rights reserved. Note to U.S. Government ...
... When you send information to IBM, you grant IBM a non-exclusive right to use or distribute the information in any way it believes appropriate without incurring any obligation to you. Copyright International Business Machines Corporation 1992 1993 1995. All rights reserved. Note to U.S. Government ...
Integrating Cisco Press Resources into the
... • Link-state routing raises two concerns: – During the initial discovery process, link-state routing protocols flood the network with LSAs • Significantly decreases the network’s capability to transport data • This is temporary, but noticeable ...
... • Link-state routing raises two concerns: – During the initial discovery process, link-state routing protocols flood the network with LSAs • Significantly decreases the network’s capability to transport data • This is temporary, but noticeable ...
information
... A malicious node M can listen all the nodes when the others nodes can only listen their closest neighbors Node M first changes its MAC address to the MAC address of the node A Node M moves closer to node B than node A is, and stays out of range of node A Node M announces node B a shorter path to rea ...
... A malicious node M can listen all the nodes when the others nodes can only listen their closest neighbors Node M first changes its MAC address to the MAC address of the node A Node M moves closer to node B than node A is, and stays out of range of node A Node M announces node B a shorter path to rea ...
Ubee DDW36C Advanced Wireless Gateway
... Copyright 2015 Ubee Interactive. All rights reserved. This document contains proprietary information of Ubee and is not to be disclosed or used except in accordance with applicable agreements. This material is protected by the copyright laws of the United States and other countries. It may not be re ...
... Copyright 2015 Ubee Interactive. All rights reserved. This document contains proprietary information of Ubee and is not to be disclosed or used except in accordance with applicable agreements. This material is protected by the copyright laws of the United States and other countries. It may not be re ...
DHCP - Personal Web Pages
... Allows DHCP server to differentiate between the two kinds of client machines e.g. process requests from two types of modems appropriately Some types of set-top boxes also set the VCI (Option 60) to inform ...
... Allows DHCP server to differentiate between the two kinds of client machines e.g. process requests from two types of modems appropriately Some types of set-top boxes also set the VCI (Option 60) to inform ...
Flowpoint and SmartSwitch Router DSL Devices
... (d) Any other rights or limitations regarding the use, duplication, or disclosure of this computer software are to be expressly stated in, or incorporated in, the contract. (e) This Notice shall be marked on any reproduction of this computer software, in whole or in part. ...
... (d) Any other rights or limitations regarding the use, duplication, or disclosure of this computer software are to be expressly stated in, or incorporated in, the contract. (e) This Notice shall be marked on any reproduction of this computer software, in whole or in part. ...
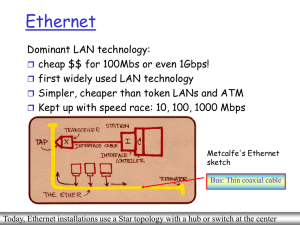
Ethernet Switches
... Ethernet Frame Structure Sending adapter encapsulates IP datagram (or other network layer protocol packet) in Ethernet frame ...
... Ethernet Frame Structure Sending adapter encapsulates IP datagram (or other network layer protocol packet) in Ethernet frame ...
VINEA: A Policy-based Virtual Network Embedding Architecture
... has bounds on embedding efficiency and on convergence embedding time, over a single provider, or across multiple federated providers. The performance of representative novel policy configurations are compared over a prototype implementation. We also present an object model as a foundation for a prot ...
... has bounds on embedding efficiency and on convergence embedding time, over a single provider, or across multiple federated providers. The performance of representative novel policy configurations are compared over a prototype implementation. We also present an object model as a foundation for a prot ...
JXTA Overview - 123SeminarsOnly.com
... creation of peers, peer groups and security primitives. • Service Layer. The Service layer includes the services that are not completely necessary for P2P networking, but are often used to make some tasks easier. • Application Layer. Implementations of integrated applications: i P2P instant messagin ...
... creation of peers, peer groups and security primitives. • Service Layer. The Service layer includes the services that are not completely necessary for P2P networking, but are often used to make some tasks easier. • Application Layer. Implementations of integrated applications: i P2P instant messagin ...
Recursive InterNetwork Architecture (RINA)

The Recursive InterNetwork Architecture (RINA) is a computer network architecture that unifies distributed computing and telecommunications. RINA's fundamental principle is that computer networking is just Inter-Process Communication or IPC. RINA reconstructs the overall structure of the Internet, forming a model that comprises a single repeating layer, the DIF (Distributed IPC Facility), which is the minimal set of components required to allow distributed IPC between application processes. RINA inherently supports mobility, multi-homing and Quality of Service without the need for extra mechanisms, provides a secure and programmable environment, motivates for a more competitive marketplace, and allows for a seamless adoption.