Securing Your Wireless Network - Homes and Lifestyles of Colorado
... Allow only specific computers to access your wireless network. Every computer that is able to communicate with a network is assigned its own unique Media Access Control (MAC) address. Wireless routers usually have a mechanism to allow only devices with particular MAC addresses access to the network. ...
... Allow only specific computers to access your wireless network. Every computer that is able to communicate with a network is assigned its own unique Media Access Control (MAC) address. Wireless routers usually have a mechanism to allow only devices with particular MAC addresses access to the network. ...
CEIM-Wavefront collaboration announcement
... Collaboration Agreement to boost Quebec’s wireless eco-system system The Centre d’entreprises et d’innovation de Montréal (CEIM) and Wavefront, Canada's National Centre of Excellence for Wireless, are proud to announce their new collaboration to accelerate the growth of Quebec companies active in Ca ...
... Collaboration Agreement to boost Quebec’s wireless eco-system system The Centre d’entreprises et d’innovation de Montréal (CEIM) and Wavefront, Canada's National Centre of Excellence for Wireless, are proud to announce their new collaboration to accelerate the growth of Quebec companies active in Ca ...
$doc.title
... – Containing AP’s name (SSID) and MAC address – Host scans channels, listening for beacon frames – Host selects an access point: associaWon request/response protocol between host and AP ...
... – Containing AP’s name (SSID) and MAC address – Host scans channels, listening for beacon frames – Host selects an access point: associaWon request/response protocol between host and AP ...
PPT
... Idea: allow sender to “reserve” channel rather than random access of data frames: avoid collisions of long data frames • Sender first transmits small request-to-send (RTS) packets to BS using CSMA – RTSs may still collide with each other (but they’re short) ...
... Idea: allow sender to “reserve” channel rather than random access of data frames: avoid collisions of long data frames • Sender first transmits small request-to-send (RTS) packets to BS using CSMA – RTSs may still collide with each other (but they’re short) ...
Business to Business Wireless E
... up the check and deliver it to the raw metal vendor. Then came the ECommerce era, where one could view the stock via a computer and the Internet, enter a charge account, and viola, the raw metal would be delivered. With MCommerce, one can visit the stock, place an order, and process the order, all f ...
... up the check and deliver it to the raw metal vendor. Then came the ECommerce era, where one could view the stock via a computer and the Internet, enter a charge account, and viola, the raw metal would be delivered. With MCommerce, one can visit the stock, place an order, and process the order, all f ...
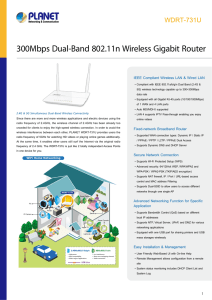
300Mbps Dual-Band 802.11n Wireless Gigabit Router
... Multiple Network Technologies for Incredibly 600Mbps High-Speed Connection The WDRT-731U supports IEEE 802.11a/b/g/n Dual Band standard with 2T2R antenna technology, therefore it can provide the wireless speed up to 300 + 300Mbps which is 12 times faster than that of traditional 11g Access Point. Mo ...
... Multiple Network Technologies for Incredibly 600Mbps High-Speed Connection The WDRT-731U supports IEEE 802.11a/b/g/n Dual Band standard with 2T2R antenna technology, therefore it can provide the wireless speed up to 300 + 300Mbps which is 12 times faster than that of traditional 11g Access Point. Mo ...
Document
... 2. New screen broadcast and media broadcast technology for wireless. 3. With Buffalo Access Point, wireless performance in Genesis is maximized. ...
... 2. New screen broadcast and media broadcast technology for wireless. 3. With Buffalo Access Point, wireless performance in Genesis is maximized. ...
Chapter 7
... – IP addresses such as 204.127.129.1 are divided by periods into four segments called octets – Static IP addresses are permanently assigned and are used by ISPs and Web sites that need to be found at the same address – Dynamic IP address are used by most other users and are temporarily assigned by y ...
... – IP addresses such as 204.127.129.1 are divided by periods into four segments called octets – Static IP addresses are permanently assigned and are used by ISPs and Web sites that need to be found at the same address – Dynamic IP address are used by most other users and are temporarily assigned by y ...
MST200 OuTdOOR WIReleSS MeSH AcceSS
... Running the Aruba MeshOS operating system, the MST200 features a single 5-GHz 2x2 MIMO radio with dual spatial streams and patented Adaptive Wireless Routing™ (AWR™) technology. Together, these features offer unparalleled speed, reliability, and low latency for voice, video and other real-time multi ...
... Running the Aruba MeshOS operating system, the MST200 features a single 5-GHz 2x2 MIMO radio with dual spatial streams and patented Adaptive Wireless Routing™ (AWR™) technology. Together, these features offer unparalleled speed, reliability, and low latency for voice, video and other real-time multi ...
... 120 buildings 415 equipment rooms 100,000 horizontal links 27,000 active wired Ethernet connections 1500 access switches 450 distribution switches 50 routers (core, IPv6, data-center, WAN, border) 13,000 phones (5000 that never get used) 5000 cable television connections 200 modem pool connections ...
How to view Edimax IP Camera from Internet
... Select the adapter you are currently using. It could be an Airport card, a third-party Wireless card, or an Ethernet Adapter. Write down the IP address, subnet mask, Router, and DNS server address. We use an usb wireless card in this example. Its IP address 10.0.1.2 told us that the IP addresses use ...
... Select the adapter you are currently using. It could be an Airport card, a third-party Wireless card, or an Ethernet Adapter. Write down the IP address, subnet mask, Router, and DNS server address. We use an usb wireless card in this example. Its IP address 10.0.1.2 told us that the IP addresses use ...
How to configure Access Point as a Repeater to expand wireless
... Select the adapter you are currently using. It could be an Airport card, a third-party Wireless card, or an Ethernet Adapter. Write down the IP address, subnet mask, Router, and DNS server address. We use an usb wireless card in this example. Its IP address 10.0.1.2 told us that the IP addresses use ...
... Select the adapter you are currently using. It could be an Airport card, a third-party Wireless card, or an Ethernet Adapter. Write down the IP address, subnet mask, Router, and DNS server address. We use an usb wireless card in this example. Its IP address 10.0.1.2 told us that the IP addresses use ...
Open AirGATE™
... OAG is a member of the AirAWARE™ family of connectivity solutions for mobile computers. OAG system software enables wireless connectivity between mobile computers running AirVU emulators that are AirGATE Enabled and enterprise networks. With OAG, mobile wireless computers appear as stationary TCP/IP ...
... OAG is a member of the AirAWARE™ family of connectivity solutions for mobile computers. OAG system software enables wireless connectivity between mobile computers running AirVU emulators that are AirGATE Enabled and enterprise networks. With OAG, mobile wireless computers appear as stationary TCP/IP ...
RICON_GTech Case_Study
... Milli Piyango’s previous network was based on IP ADSL with over five thousand lotto terminal distributed right throughout Turkey. The efficiency of the system was not optimal, with slow transaction speeds on a network that had limited scalability. In order to overcome the above limitations the syste ...
... Milli Piyango’s previous network was based on IP ADSL with over five thousand lotto terminal distributed right throughout Turkey. The efficiency of the system was not optimal, with slow transaction speeds on a network that had limited scalability. In order to overcome the above limitations the syste ...
ppt
... • No base stations • Nodes can only transmit to other nodes within link coverage • Nodes self-organize and route among themselves ...
... • No base stations • Nodes can only transmit to other nodes within link coverage • Nodes self-organize and route among themselves ...
$doc.title
... • Relay responsible for sending packets between wired network and wireless host(s) in its “area” • E.g., cell towers, 802.11 access points ...
... • Relay responsible for sending packets between wired network and wireless host(s) in its “area” • E.g., cell towers, 802.11 access points ...
Network Planning Technical Sub
... added in residence halls this month and two more in other areas. Students in residence halls continue to request more wireless coverage, particularly in their rooms. Installation of digital signage in eleven locations continues to be planned and worked on, with the first installation planned at the ...
... added in residence halls this month and two more in other areas. Students in residence halls continue to request more wireless coverage, particularly in their rooms. Installation of digital signage in eleven locations continues to be planned and worked on, with the first installation planned at the ...
Chapter 6 slides, Computer Networking, 3rd edition
... connect to larger Internet: mesh net no base station, no connection to larger Internet. May have to relay to reach other a given wireless node MANET, VANET ...
... connect to larger Internet: mesh net no base station, no connection to larger Internet. May have to relay to reach other a given wireless node MANET, VANET ...
HOW TO CREATE YOUR KORCETT ACCOUNT HELP!
... call the Korcett Support Team at 1-800-379-3729. Our awesome Support Team can help you troubleshoot. ...
... call the Korcett Support Team at 1-800-379-3729. Our awesome Support Team can help you troubleshoot. ...
Introduction to Mobile Computing CNT 5517-5564
... Lack of de-facto general architecture: handhelds, communicators, laptops, and other devices ...
... Lack of de-facto general architecture: handhelds, communicators, laptops, and other devices ...
NEXWAY Workshop Afternoon session A- Workshop - 14.00
... time, wireless and packet traffic in a single transport network. The proposed model combines different technologies as connection and connectionless networks, optical cable and wireless (microwave/ millimetre wave or optical wireless) and it is suitable for a variety of purposes and services in orde ...
... time, wireless and packet traffic in a single transport network. The proposed model combines different technologies as connection and connectionless networks, optical cable and wireless (microwave/ millimetre wave or optical wireless) and it is suitable for a variety of purposes and services in orde ...
Access Point
... FHSS is a transmission technology used in WLAN transmissions where the data signal is modulated with a narrowband carrier signal that "hops" in a random but predictable sequence from frequency to frequency as a function of time over a wide band of frequencies. ...
... FHSS is a transmission technology used in WLAN transmissions where the data signal is modulated with a narrowband carrier signal that "hops" in a random but predictable sequence from frequency to frequency as a function of time over a wide band of frequencies. ...
Wi-Fi
Wi-Fi (or WiFi) is a local area wireless computer networking technology that allows electronic devices to network, mainly using the 2.4 gigahertz (12 cm) UHF and 5 gigahertz (6 cm) SHF ISM radio bands.The Wi-Fi Alliance defines Wi-Fi as any ""wireless local area network"" (WLAN) product based on the Institute of Electrical and Electronics Engineers' (IEEE) 802.11 standards. However, the term ""Wi-Fi"" is used in general English as a synonym for ""WLAN"" since most modern WLANs are based on these standards. ""Wi-Fi"" is a trademark of the Wi-Fi Alliance. The ""Wi-Fi Certified"" trademark can only be used by Wi-Fi products that successfully complete Wi-Fi Alliance interoperability certification testing.Many devices can use Wi-Fi, e.g. personal computers, video-game consoles, smartphones, digital cameras, tablet computers and digital audio players. These can connect to a network resource such as the Internet via a wireless network access point. Such an access point (or hotspot) has a range of about 20 meters (66 feet) indoors and a greater range outdoors. Hotspot coverage can be as small as a single room with walls that block radio waves, or as large as many square kilometres achieved by using multiple overlapping access points. Wi-Fi can be less secure than wired connections, such as Ethernet, precisely because an intruder does not need a physical connection. Web pages that use TLS are secure, but unencrypted internet access can easily be detected by intruders. Because of this, Wi-Fi has adopted various encryption technologies. The early encryption WEP proved easy to break. Higher quality protocols (WPA, WPA2) were added later. An optional feature added in 2007, called Wi-Fi Protected Setup (WPS), had a serious flaw that allowed an attacker to recover the router's password. The Wi-Fi Alliance has since updated its test plan and certification program to ensure all newly certified devices resist attacks.