Reliable, Low Power Wireless Sensor Networks for the Internet of
... for web-like interaction with wireless sensor nodes. The 6LoWPAN working group has defined an IP adaptation layer that compresses an IP packet’s large headers into small wireless frames or data packets, allowing sensor nodes to be individually addressable by IP addresses. While these upper layers en ...
... for web-like interaction with wireless sensor nodes. The 6LoWPAN working group has defined an IP adaptation layer that compresses an IP packet’s large headers into small wireless frames or data packets, allowing sensor nodes to be individually addressable by IP addresses. While these upper layers en ...
Coexistence of Wi-Fi and Heterogeneous Small Cell
... spectrum available. In USA, Korea and China, deploying LTE-A in unlicensed spectrum does not require changes to the existing LTE-A standards (e.g., 3GPP Rel-10). In most other countries, the regulatory requirements of ‘Listen Before Talk’ in unlicensed spectrum mandate standard modifications (e.g., ...
... spectrum available. In USA, Korea and China, deploying LTE-A in unlicensed spectrum does not require changes to the existing LTE-A standards (e.g., 3GPP Rel-10). In most other countries, the regulatory requirements of ‘Listen Before Talk’ in unlicensed spectrum mandate standard modifications (e.g., ...
Emerging Wireless Standards
... components that will make up 802.11n, a new WLAN standard that promises both higher data rates and increased reliability. Though the specification is not expected to be finalized before end of 2007, the draft is proving to be reasonably stable as it progresses through the formal IEEE review process. ...
... components that will make up 802.11n, a new WLAN standard that promises both higher data rates and increased reliability. Though the specification is not expected to be finalized before end of 2007, the draft is proving to be reasonably stable as it progresses through the formal IEEE review process. ...
Brief - Electronic Privacy Information Center
... right in law to communicate privately across computer networks. The Electronic Communications Privacy Act of 1986 (“ECPA”) ensures the privacy of these communications, and its protections should not be interpreted in an unfair and inconsistent way. The fact that sophisticated parties may be able to ...
... right in law to communicate privately across computer networks. The Electronic Communications Privacy Act of 1986 (“ECPA”) ensures the privacy of these communications, and its protections should not be interpreted in an unfair and inconsistent way. The fact that sophisticated parties may be able to ...
Dual Band (2.4 GHz, 5 GHz) Ethernet Bridge/Router, Serial Server
... options and ease of use make it ideal for commercial enterprise environments. Dual-Band Wi-fi The AirborneM2MTM products establish wireless connections over both 2.4 GHz and 5 GHz bands. Whenever the 2.4 GHz airspace is overcrowded with competing wireless transmission, AirborneM2MTM products can be ...
... options and ease of use make it ideal for commercial enterprise environments. Dual-Band Wi-fi The AirborneM2MTM products establish wireless connections over both 2.4 GHz and 5 GHz bands. Whenever the 2.4 GHz airspace is overcrowded with competing wireless transmission, AirborneM2MTM products can be ...
Quick Start EchoLife Gateway PON Terminal
... Install the device in strict compliance with the requirements of the supplier. Reserve a space of at least 10 cm above and around the device for heat dissipation. During the installation, keep the device away from electric appliances that generate strong magnetic or electric fields, such as microwa ...
... Install the device in strict compliance with the requirements of the supplier. Reserve a space of at least 10 cm above and around the device for heat dissipation. During the installation, keep the device away from electric appliances that generate strong magnetic or electric fields, such as microwa ...
Chapter6
... host: must associate with an AP scans channels, listening for beacon frames containing AP’s name (SSID) and MAC address selects AP to associate with may perform authentication [Chapter 8] will typically run DHCP to get IP address in AP’s subnet ...
... host: must associate with an AP scans channels, listening for beacon frames containing AP’s name (SSID) and MAC address selects AP to associate with may perform authentication [Chapter 8] will typically run DHCP to get IP address in AP’s subnet ...
Chapter 12 Outline
... There has also been some concern over the so-called “WAP GAP.” (1) Confidentiality of information is vulnerable where the two different networks meet, the WAP gateway. (2) WTLS acts as the security protocol for the WAP network, and TLS is the standard for the Internet, so the WAP gateway has to perf ...
... There has also been some concern over the so-called “WAP GAP.” (1) Confidentiality of information is vulnerable where the two different networks meet, the WAP gateway. (2) WTLS acts as the security protocol for the WAP network, and TLS is the standard for the Internet, so the WAP gateway has to perf ...
GEPS Programming Tutorial
... placement of the sensors themselves; node configuration is largely automated and can be managed from a remote network server. Maintenance may consist only of battery replacement once every few years, in the case of battery-powered sensors. Sensors using energy harvesting techniques may require no sc ...
... placement of the sensors themselves; node configuration is largely automated and can be managed from a remote network server. Maintenance may consist only of battery replacement once every few years, in the case of battery-powered sensors. Sensors using energy harvesting techniques may require no sc ...
HWBA54G Manual
... This equipment has been tested and found to comply with the regulations for a Class B digital device, pursuant to Part 15 of the FCC Rules. These limits are designed to provide reasonable protection against harmful interference when the equipment is operated in a commercial environment. This equipme ...
... This equipment has been tested and found to comply with the regulations for a Class B digital device, pursuant to Part 15 of the FCC Rules. These limits are designed to provide reasonable protection against harmful interference when the equipment is operated in a commercial environment. This equipme ...
Complete Wireless Network Upgrade for Flagstaff Campus
... networking equipment for home use, built in wireless capability in laptops, commercial hot spots in hotels, coffee shops, and other public areas. It is becoming common to have broad coverage in University campuses. NAU requires a modern wireless network and an underlying network infrastructure in or ...
... networking equipment for home use, built in wireless capability in laptops, commercial hot spots in hotels, coffee shops, and other public areas. It is becoming common to have broad coverage in University campuses. NAU requires a modern wireless network and an underlying network infrastructure in or ...
Wells Public Library`s
... anywhere in the building, and also directly outside the building. Usually, within a minute of turning on your computer, the wireless card senses a signal and your computer will connect to our wireless network. If it does not automatically connect, you may have to help your computer detect our networ ...
... anywhere in the building, and also directly outside the building. Usually, within a minute of turning on your computer, the wireless card senses a signal and your computer will connect to our wireless network. If it does not automatically connect, you may have to help your computer detect our networ ...
Implementing IEEE 802.11b/g wireless Local Area Networks
... Two types or modes of WLANs exist; the technology that provides connectivity to the infrastructure network and the technology that provides the connectivity of one device to another or an adhoc network. This is also depicted in Figure 1.1 [3-5]. IEEE 802.11-based WLANs work in both modes. WLANs do n ...
... Two types or modes of WLANs exist; the technology that provides connectivity to the infrastructure network and the technology that provides the connectivity of one device to another or an adhoc network. This is also depicted in Figure 1.1 [3-5]. IEEE 802.11-based WLANs work in both modes. WLANs do n ...
slides
... Illustrated here is a very simple computer network, consisting of computers, a network operating system residing on a dedicated server computer, cable (wiring) connecting the devices, network interface cards (NIC), switches, and a router. ...
... Illustrated here is a very simple computer network, consisting of computers, a network operating system residing on a dedicated server computer, cable (wiring) connecting the devices, network interface cards (NIC), switches, and a router. ...
Terminal Bridge Extension Over Distributed Architecture
... • Wireless networks have become common varying from small Bluetooth networks to large-scale GSM networks • Combining different networks provides a situation where we can use “best features from every technology” • However, no general model for using these different wireless technologies together ...
... • Wireless networks have become common varying from small Bluetooth networks to large-scale GSM networks • Combining different networks provides a situation where we can use “best features from every technology” • However, no general model for using these different wireless technologies together ...
Wireless Communications and Networks
... displaying a few lines of text E.g., browsers of most mobile wireless devices use wireless markup language (WML) instead of HTML ...
... displaying a few lines of text E.g., browsers of most mobile wireless devices use wireless markup language (WML) instead of HTML ...
Wireless Communications and Networks
... displaying a few lines of text E.g., browsers of most mobile wireless devices use wireless markup language (WML) instead of HTML ...
... displaying a few lines of text E.g., browsers of most mobile wireless devices use wireless markup language (WML) instead of HTML ...
CBR400 Compact Broadband N Router
... like travel, mobile workgroups, or stationary remote Internet access, you can rely on CradlePoint’s advanced networking features like WiPipe Security, VPN Termination, and Failover/Failback (which protects network uptime in case primary data service fails) - to keep your business online. Standard on ...
... like travel, mobile workgroups, or stationary remote Internet access, you can rely on CradlePoint’s advanced networking features like WiPipe Security, VPN Termination, and Failover/Failback (which protects network uptime in case primary data service fails) - to keep your business online. Standard on ...
PDF - International Journal of Recent Scientific Research
... protocol for signaling. SIP is an RFC (Request for Comment) Standard from the IETF (Internet Engineering Task Force), responsible for administering and developing protocols that define the Internet. SIP translates the user name to the current network address, manages the call admission, dropping, or ...
... protocol for signaling. SIP is an RFC (Request for Comment) Standard from the IETF (Internet Engineering Task Force), responsible for administering and developing protocols that define the Internet. SIP translates the user name to the current network address, manages the call admission, dropping, or ...
Wireless (In)Security or Why You Will WEEP When You Learn
... WEP usually disabled by default. • Most public WLAN APs like those at airports, hotels, cafes, etc. never enable WEP. • Only ~20% of companies seem to use WEP. • WEP is severely broken anyway (more later). ...
... WEP usually disabled by default. • Most public WLAN APs like those at airports, hotels, cafes, etc. never enable WEP. • Only ~20% of companies seem to use WEP. • WEP is severely broken anyway (more later). ...
Introduction to Mobile Computing - UF CISE
... devices, and disk space) • Lack of de-facto general architecture: handhelds, communicators, laptops, and other devices ...
... devices, and disk space) • Lack of de-facto general architecture: handhelds, communicators, laptops, and other devices ...
Wireless Expands M D to More of the Plant
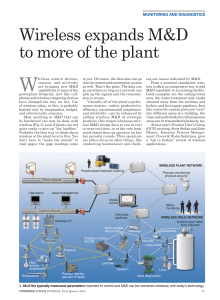
... three buckets: The field devices and links, the network infrastructure, and the solutions, or what you actually do with the monitored points. The links and infrastructure (Fig 2) are industrial, ruggedized versions of similar equipment you use at home or in the office. Each field device has an anten ...
... three buckets: The field devices and links, the network infrastructure, and the solutions, or what you actually do with the monitored points. The links and infrastructure (Fig 2) are industrial, ruggedized versions of similar equipment you use at home or in the office. Each field device has an anten ...
Components of LPW Devices - Renesas e
... Throughput – amount of payload per time Latency – time it takes for a specific data item to arrive. Reliability – odds of all data arriving up corrupted ...
... Throughput – amount of payload per time Latency – time it takes for a specific data item to arrive. Reliability – odds of all data arriving up corrupted ...
Wi-Fi
Wi-Fi (or WiFi) is a local area wireless computer networking technology that allows electronic devices to network, mainly using the 2.4 gigahertz (12 cm) UHF and 5 gigahertz (6 cm) SHF ISM radio bands.The Wi-Fi Alliance defines Wi-Fi as any ""wireless local area network"" (WLAN) product based on the Institute of Electrical and Electronics Engineers' (IEEE) 802.11 standards. However, the term ""Wi-Fi"" is used in general English as a synonym for ""WLAN"" since most modern WLANs are based on these standards. ""Wi-Fi"" is a trademark of the Wi-Fi Alliance. The ""Wi-Fi Certified"" trademark can only be used by Wi-Fi products that successfully complete Wi-Fi Alliance interoperability certification testing.Many devices can use Wi-Fi, e.g. personal computers, video-game consoles, smartphones, digital cameras, tablet computers and digital audio players. These can connect to a network resource such as the Internet via a wireless network access point. Such an access point (or hotspot) has a range of about 20 meters (66 feet) indoors and a greater range outdoors. Hotspot coverage can be as small as a single room with walls that block radio waves, or as large as many square kilometres achieved by using multiple overlapping access points. Wi-Fi can be less secure than wired connections, such as Ethernet, precisely because an intruder does not need a physical connection. Web pages that use TLS are secure, but unencrypted internet access can easily be detected by intruders. Because of this, Wi-Fi has adopted various encryption technologies. The early encryption WEP proved easy to break. Higher quality protocols (WPA, WPA2) were added later. An optional feature added in 2007, called Wi-Fi Protected Setup (WPS), had a serious flaw that allowed an attacker to recover the router's password. The Wi-Fi Alliance has since updated its test plan and certification program to ensure all newly certified devices resist attacks.