Wireless LAN
... – Can be used with either Win95/98 or Win NT – Must be used on a computer with both Wireless and wired network connections – Can use remote administration to set parameters or monitor network ...
... – Can be used with either Win95/98 or Win NT – Must be used on a computer with both Wireless and wired network connections – Can use remote administration to set parameters or monitor network ...
reliability of wireless networks and devices
... consider to decrease the number of network failures and to cope with failures when they do occur. INTRODUCTION “A wireless network is a flexible data communications system, which uses wireless media such as radio frequency technology to transmit and receive data over the air, minimizing the need for ...
... consider to decrease the number of network failures and to cope with failures when they do occur. INTRODUCTION “A wireless network is a flexible data communications system, which uses wireless media such as radio frequency technology to transmit and receive data over the air, minimizing the need for ...
Liberty-i Wireless Glossary
... Encryption is the conversion of data into a form that cannot be easily understood by unauthorized people. Decryption is the process of converting encrypted data back into its original form, so it can be understood. Simple ciphers include the substitution of letters for numbers or the rotation of let ...
... Encryption is the conversion of data into a form that cannot be easily understood by unauthorized people. Decryption is the process of converting encrypted data back into its original form, so it can be understood. Simple ciphers include the substitution of letters for numbers or the rotation of let ...
Information Technology and Protection Considerations for E
... (SSID) over the air at regular intervals. This feature was designed for businesses and mobile hotspots where Wi-Fi clients may roam in and out of range. In the home, this roaming feature is unnecessary, and it increases the likelihood someone will try to log in to your home network. Fortunately, mos ...
... (SSID) over the air at regular intervals. This feature was designed for businesses and mobile hotspots where Wi-Fi clients may roam in and out of range. In the home, this roaming feature is unnecessary, and it increases the likelihood someone will try to log in to your home network. Fortunately, mos ...
Chapter 6 slides, Computer Networking, 3rd edition
... 2.4-5 GHz range up to 54 Mbps All use CSMA/CA for ...
... 2.4-5 GHz range up to 54 Mbps All use CSMA/CA for ...
PowerPoint Title
... coverage over some relatively large contiguous geographic serving area. vertically-integrated, top-down, service-provider approach to delivering wireless Internet access ...
... coverage over some relatively large contiguous geographic serving area. vertically-integrated, top-down, service-provider approach to delivering wireless Internet access ...
Mobile RFID of Wireless Mesh Network for Intelligent Safety Care
... Wireless Mesh Network Mesh networking is a way to route data, voice and instructions between nodes. It allows for continuous connections and reconfiguration around broken or blocked paths by hopping from node to node until the destination is reached [5]. A mesh network whose nodes are all connected ...
... Wireless Mesh Network Mesh networking is a way to route data, voice and instructions between nodes. It allows for continuous connections and reconfiguration around broken or blocked paths by hopping from node to node until the destination is reached [5]. A mesh network whose nodes are all connected ...
Faculty of Computer Science & Engineering Chapter 04 .Wireless
... laptop. The client wants to purchase a hardware solution that will permit each sales person to have wireless network connectivity for his or her PC and laptop. Only the PC or the laptop needs network access at any given time, and both have USB support. Which of the following solutions would work? Ch ...
... laptop. The client wants to purchase a hardware solution that will permit each sales person to have wireless network connectivity for his or her PC and laptop. Only the PC or the laptop needs network access at any given time, and both have USB support. Which of the following solutions would work? Ch ...
An Investigation into Signal Strength of 802.11n WLAN
... increasing bandwidth and date rate requirements but also provide efficient wireless transmission between the communicating devices. This quest for more efficient communication has prompted the need for a deeper understanding of the wireless channels upon which these devices communicate (Liechty, 20 ...
... increasing bandwidth and date rate requirements but also provide efficient wireless transmission between the communicating devices. This quest for more efficient communication has prompted the need for a deeper understanding of the wireless channels upon which these devices communicate (Liechty, 20 ...
Networking Security - Northwestern Networks Group
... no base stations nodes can only transmit to other nodes within link ...
... no base stations nodes can only transmit to other nodes within link ...
Wireless Electronic Notice Board
... ZigBee is targeted at applications that require a low data rate, long battery life, and secure networking. ZigBee has a defined rate of 250 kbit/s, best suited for periodic or intermittent data or a single signal transmission from a sensor or input device. Applications include wireless light switche ...
... ZigBee is targeted at applications that require a low data rate, long battery life, and secure networking. ZigBee has a defined rate of 250 kbit/s, best suited for periodic or intermittent data or a single signal transmission from a sensor or input device. Applications include wireless light switche ...
comparisons of wired and wireless networks: a review
... wired setup uses physical cables to transfer data between different devices and computer systems. Most wired networks use Ethernet cables to transfer data between connected PCs. In a small wired network, a single router may be used to connect all the computers. Larger networks often involve multiple ...
... wired setup uses physical cables to transfer data between different devices and computer systems. Most wired networks use Ethernet cables to transfer data between connected PCs. In a small wired network, a single router may be used to connect all the computers. Larger networks often involve multiple ...
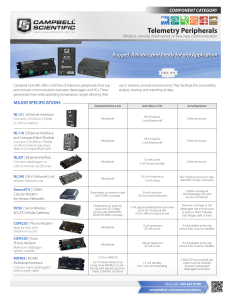
Telemetry Peripherals
... NL116 | Ethernet Interface and CompactFlash Module Connects CR1000 or CR3000 to LAN or Internet and stores data on a CompactFlash card ...
... NL116 | Ethernet Interface and CompactFlash Module Connects CR1000 or CR3000 to LAN or Internet and stores data on a CompactFlash card ...
Part I: Introduction - Northwestern University
... no base stations nodes can only transmit to other nodes within link ...
... no base stations nodes can only transmit to other nodes within link ...
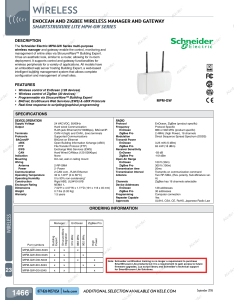
wireless
... ENOCEAN AND ZIGBEE WIRELESS MANAGER AND GATEWAY SMARTSTRUXURE LITE MPM-GW SERIES DESCRIPTION The Schneider Electric MPM-GW Series multi-purpose wireless manager and gateway enable the control, monitoring and management of entire sites via StruxureWare™ Building Expert. It has an aesthetic look, simi ...
... ENOCEAN AND ZIGBEE WIRELESS MANAGER AND GATEWAY SMARTSTRUXURE LITE MPM-GW SERIES DESCRIPTION The Schneider Electric MPM-GW Series multi-purpose wireless manager and gateway enable the control, monitoring and management of entire sites via StruxureWare™ Building Expert. It has an aesthetic look, simi ...
On Mobile Mesh Networks - International Journal of Open
... working group [6], which, inheriting the TCP/IP protocols stack layering, assumed an IP-centric view of a MANET [7]. Authors in [8] propose a variation of MANET – Autonomous Mobile Mesh Networks (AMMNET). In a standard wireless mesh network, stationary mesh nodes provide routing and relay capabiliti ...
... working group [6], which, inheriting the TCP/IP protocols stack layering, assumed an IP-centric view of a MANET [7]. Authors in [8] propose a variation of MANET – Autonomous Mobile Mesh Networks (AMMNET). In a standard wireless mesh network, stationary mesh nodes provide routing and relay capabiliti ...
Wireless & Mobile Technologies
... Personal Area Network (PAN) Operate in the gigahertz frequency spectrum but differ from other wireless technologies in the range of service, network capacity and data bit transfer rate. Designed to operate over a much smaller service area. Devices that participate in these types of peer based ...
... Personal Area Network (PAN) Operate in the gigahertz frequency spectrum but differ from other wireless technologies in the range of service, network capacity and data bit transfer rate. Designed to operate over a much smaller service area. Devices that participate in these types of peer based ...
Quick Start Guide 11b/g Wireless Long Range Multi
... operates seamlessly in the 2.4 GHz frequency spectrum supporting the 802.11b (2.4GHz, 11Mbps) and super high speed of 802.11g (2.4GHz, 108Mbps) wireless standards. It supports high output power level settings, bandwidth selection, RSSI indicator and antenna diversity which enable the best transmitti ...
... operates seamlessly in the 2.4 GHz frequency spectrum supporting the 802.11b (2.4GHz, 11Mbps) and super high speed of 802.11g (2.4GHz, 108Mbps) wireless standards. It supports high output power level settings, bandwidth selection, RSSI indicator and antenna diversity which enable the best transmitti ...
Wireless Networks and Mobile Communication Systems NET 332D
... Microwave is also used for satellite communications. › Radio Range: Frequencies in the range 30 MHz to 1 GHz are suitable for omnidirectional applications. › The infrared portion of the spectrum. This covers, roughly, from 3 × 1011 to 2 × 1014 Hz. Infrared is useful in local point-to-point and multi ...
... Microwave is also used for satellite communications. › Radio Range: Frequencies in the range 30 MHz to 1 GHz are suitable for omnidirectional applications. › The infrared portion of the spectrum. This covers, roughly, from 3 × 1011 to 2 × 1014 Hz. Infrared is useful in local point-to-point and multi ...
XML: Part
... Hardening Wireless Local Area Networks (WLAN) • By 2007, >98% of all notebooks will be wirelessenabled • Serious security vulnerabilities have also been created by wireless data technology: – Unauthorized users can access the wireless signal from outside a building and connect to the network – Atta ...
... Hardening Wireless Local Area Networks (WLAN) • By 2007, >98% of all notebooks will be wirelessenabled • Serious security vulnerabilities have also been created by wireless data technology: – Unauthorized users can access the wireless signal from outside a building and connect to the network – Atta ...
Module 2 - Santa Fe College
... When you configure an access point, some configuration utilities use the term mixed mode to designate a network with both 802.11n and non-802.11n clients. In this configuration, one radio transmitter is used for legacy clients, and the remaining radio transmitters are used for 802.11n clients. Many ...
... When you configure an access point, some configuration utilities use the term mixed mode to designate a network with both 802.11n and non-802.11n clients. In this configuration, one radio transmitter is used for legacy clients, and the remaining radio transmitters are used for 802.11n clients. Many ...
SkyPilot Network Overview
... Advanced Antenna Array Patent-Pending Antenna Array • 8 sectorized antennas, each a 45° beam (360° total coverage) • “Big ears” – 18 dBi / antenna ...
... Advanced Antenna Array Patent-Pending Antenna Array • 8 sectorized antennas, each a 45° beam (360° total coverage) • “Big ears” – 18 dBi / antenna ...
Workware Wireless FAQ - AV/IT Installer
... operate well with the wireless system. For optimal performance, it is recommended that a gigabit connection be used. Which wireless network security protocols are supported and which wireless standards and frequency bands are supported? Security Protocols 64/128 bit WEP/WPA/WPA2-PSK Standards and F ...
... operate well with the wireless system. For optimal performance, it is recommended that a gigabit connection be used. Which wireless network security protocols are supported and which wireless standards and frequency bands are supported? Security Protocols 64/128 bit WEP/WPA/WPA2-PSK Standards and F ...
Wi-Fi
Wi-Fi (or WiFi) is a local area wireless computer networking technology that allows electronic devices to network, mainly using the 2.4 gigahertz (12 cm) UHF and 5 gigahertz (6 cm) SHF ISM radio bands.The Wi-Fi Alliance defines Wi-Fi as any ""wireless local area network"" (WLAN) product based on the Institute of Electrical and Electronics Engineers' (IEEE) 802.11 standards. However, the term ""Wi-Fi"" is used in general English as a synonym for ""WLAN"" since most modern WLANs are based on these standards. ""Wi-Fi"" is a trademark of the Wi-Fi Alliance. The ""Wi-Fi Certified"" trademark can only be used by Wi-Fi products that successfully complete Wi-Fi Alliance interoperability certification testing.Many devices can use Wi-Fi, e.g. personal computers, video-game consoles, smartphones, digital cameras, tablet computers and digital audio players. These can connect to a network resource such as the Internet via a wireless network access point. Such an access point (or hotspot) has a range of about 20 meters (66 feet) indoors and a greater range outdoors. Hotspot coverage can be as small as a single room with walls that block radio waves, or as large as many square kilometres achieved by using multiple overlapping access points. Wi-Fi can be less secure than wired connections, such as Ethernet, precisely because an intruder does not need a physical connection. Web pages that use TLS are secure, but unencrypted internet access can easily be detected by intruders. Because of this, Wi-Fi has adopted various encryption technologies. The early encryption WEP proved easy to break. Higher quality protocols (WPA, WPA2) were added later. An optional feature added in 2007, called Wi-Fi Protected Setup (WPS), had a serious flaw that allowed an attacker to recover the router's password. The Wi-Fi Alliance has since updated its test plan and certification program to ensure all newly certified devices resist attacks.