Chapter 17
... – Acknowledgement points are identified • ACKs are processed further down the tree ...
... – Acknowledgement points are identified • ACKs are processed further down the tree ...
Communication-and-Security-in-M2M
... challenges in M2M systems • Standardization challenges – M2M can replace proprietary tech such as SCADA in the future. Unlike SCADA, M2M devices are able to push data to a server and M2M also works with standardized tech. Such factors will push towards the replacement of proprietary tech with M2M so ...
... challenges in M2M systems • Standardization challenges – M2M can replace proprietary tech such as SCADA in the future. Unlike SCADA, M2M devices are able to push data to a server and M2M also works with standardized tech. Such factors will push towards the replacement of proprietary tech with M2M so ...
Interconnecting Devices
... Can have two or more interfaces When a bit (0,1) arrives, the repeater receives it and regenerates it, the transmits it onto all other interfaces Used in LAN to connect cable segments and extend the maximum cable length extending the geographical LAN range Ethernet 10base5 – Max. segment length ...
... Can have two or more interfaces When a bit (0,1) arrives, the repeater receives it and regenerates it, the transmits it onto all other interfaces Used in LAN to connect cable segments and extend the maximum cable length extending the geographical LAN range Ethernet 10base5 – Max. segment length ...
Chapter 6 Virtual Private Networking Using SSL Connections
... Portal Layouts are applied by selecting from available portal layouts in the configuration of a Domain. When you have completed your Portal Layout, you can apply the Portal Layout to one or more authentication domains (see XREF to apply a Portal Layout to a Domain). You can also make the new portal ...
... Portal Layouts are applied by selecting from available portal layouts in the configuration of a Domain. When you have completed your Portal Layout, you can apply the Portal Layout to one or more authentication domains (see XREF to apply a Portal Layout to a Domain). You can also make the new portal ...
L20WD800 Network Troubleshooting and Walkthrough
... Thank you for activating your free Dynamic DNS account for your Lorex DVR Combo. Once you have set up your Lorex device and configured your network, you will be able to view your video images from anywhere in the world using the URL shown at the end of this message. When you visit the Lorex web site ...
... Thank you for activating your free Dynamic DNS account for your Lorex DVR Combo. Once you have set up your Lorex device and configured your network, you will be able to view your video images from anywhere in the world using the URL shown at the end of this message. When you visit the Lorex web site ...
Basic Setup
... Placing the USB Adapter Cradle You can attach the Wireless Adapter directly to a USB port on your computer, or use the USB cable to extend the range and obtain better wireless reception. Follow these instructions to use the USB cable, plastic cradle, and loop and hook fastener provided in the packag ...
... Placing the USB Adapter Cradle You can attach the Wireless Adapter directly to a USB port on your computer, or use the USB cable to extend the range and obtain better wireless reception. Follow these instructions to use the USB cable, plastic cradle, and loop and hook fastener provided in the packag ...
Linux+ Guide to Linux Certification
... Table 7-7 (continued): Files commonly found in the /proc directory ...
... Table 7-7 (continued): Files commonly found in the /proc directory ...
SNAP Network Operating System - Synapse forums
... details about exceptions caught in users’ code. The debug build runs slightly slower than the normal build and provides a little less code space for user applications, so most users would not run this in a production environment. Most platforms also have an AES-128-capable build available. This buil ...
... details about exceptions caught in users’ code. The debug build runs slightly slower than the normal build and provides a little less code space for user applications, so most users would not run this in a production environment. Most platforms also have an AES-128-capable build available. This buil ...
An Efficient Diffusion Load Balancing Algorithm in Distributed System
... (jobs or tasks) across a set of processors which are connected to a network which may be distributed across the globe. The excess load or remaining unexecuted load from a processor is migrated to other processors which have load below the threshold load [5]. Threshold load is such an amount of load ...
... (jobs or tasks) across a set of processors which are connected to a network which may be distributed across the globe. The excess load or remaining unexecuted load from a processor is migrated to other processors which have load below the threshold load [5]. Threshold load is such an amount of load ...
VINEA: A Policy-based Virtual Network Embedding Architecture
... In this section we define an object model in support of transparency for our policy-based architecture. Transparency is the ability of hiding the complexity of the implementation of mechanisms of a system from both users (of a service or applications) and application programmers. To provide transpar ...
... In this section we define an object model in support of transparency for our policy-based architecture. Transparency is the ability of hiding the complexity of the implementation of mechanisms of a system from both users (of a service or applications) and application programmers. To provide transpar ...
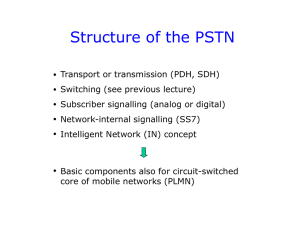
Transport and Signaling in the PSTN
... SPC = 277 means different signalling points (network elements) at different network levels. The Service Information Octet (SIO) indicates whether the DPC and OPC are international or national signalling point codes. F ...
... SPC = 277 means different signalling points (network elements) at different network levels. The Service Information Octet (SIO) indicates whether the DPC and OPC are international or national signalling point codes. F ...
ppt 3.8MB - Star Tap
... – Grid thinking: Provide as much protection that your schedule allows. The connections will not be there in an hour. The more network resources the more protected circuits. ...
... – Grid thinking: Provide as much protection that your schedule allows. The connections will not be there in an hour. The more network resources the more protected circuits. ...
Glossary for Fundamentals of Network Security
... DVD—A removable storage medium like a CD, but with higher capacity. (Chapter 5) dynamic addressing—A system whereby IP addresses are automatically assigned and configured. (Chapter 3) dynamic storage—Beginning with Windows 2000, a storage type option that requires upgrading basic disks, and that all ...
... DVD—A removable storage medium like a CD, but with higher capacity. (Chapter 5) dynamic addressing—A system whereby IP addresses are automatically assigned and configured. (Chapter 3) dynamic storage—Beginning with Windows 2000, a storage type option that requires upgrading basic disks, and that all ...
Personal Area Networks: Bluetooth or IEEE 802.11? | SpringerLink
... Interconnecting all our electronic devices we carry around, such as cellular phones, PDAs, and laptops, with wireless links requires a cheap, low-power radio technology that still delivers good performance. In this context, the Bluetooth wireless technology was developed to meet the requirements int ...
... Interconnecting all our electronic devices we carry around, such as cellular phones, PDAs, and laptops, with wireless links requires a cheap, low-power radio technology that still delivers good performance. In this context, the Bluetooth wireless technology was developed to meet the requirements int ...
DualAligner: a dual alignment-based strategy to align protein
... with hard constraints given by a set of must-link pairs of proteins. These must-link pairs are identified by sequence orthologs. More recently, the ILP-based Natalie proposes a Lagrangian relaxation approach to solve the problem approximately (Pache and Aloy, 2012). PINALOG combines both the similar ...
... with hard constraints given by a set of must-link pairs of proteins. These must-link pairs are identified by sequence orthologs. More recently, the ILP-based Natalie proposes a Lagrangian relaxation approach to solve the problem approximately (Pache and Aloy, 2012). PINALOG combines both the similar ...
TCP and UDP
... delivers duplicate copies of a given message limits messages to some finite size delivers messages after an arbitrarily long delay ...
... delivers duplicate copies of a given message limits messages to some finite size delivers messages after an arbitrarily long delay ...
Expanded Notes: DHCP in the Network
... network. With static IP addressing, the administrator assigns an IP number and subnet mask to each host in the network—whether it is a PC, router, or another piece of electronic equipment. Each network interface that connects to the network requires this information. The administrator also assigns a ...
... network. With static IP addressing, the administrator assigns an IP number and subnet mask to each host in the network—whether it is a PC, router, or another piece of electronic equipment. Each network interface that connects to the network requires this information. The administrator also assigns a ...
FiOS Gateway USER GUIDE - Frontier Communications
... • HAN Expansion Port - provides for future hardware upgrades to add support for Home Area Networking capabilities. • Ethernet WAN - connects your Gateway to the Internet using an Ethernet cable. • Coax WAN and LAN - connects your Gateway to the Internet and/or to other MoCA devices using a coaxi ...
... • HAN Expansion Port - provides for future hardware upgrades to add support for Home Area Networking capabilities. • Ethernet WAN - connects your Gateway to the Internet using an Ethernet cable. • Coax WAN and LAN - connects your Gateway to the Internet and/or to other MoCA devices using a coaxi ...
Dynamic Host Configuration Protocol
... • DHCP Service down or missing Relay Agent • ipconfig /all or ifconfig –a • Windows: 169.254.xx.xx addresses on an interface or showing up on a network segment (no local DHCP server or relay). ...
... • DHCP Service down or missing Relay Agent • ipconfig /all or ifconfig –a • Windows: 169.254.xx.xx addresses on an interface or showing up on a network segment (no local DHCP server or relay). ...
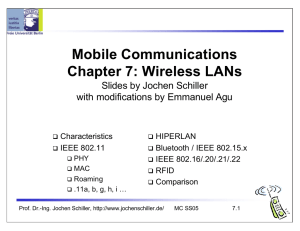
Mobile Communications Chapter 7: Wireless LANs
... if the medium is free for the duration of an Inter-Frame Space (IFS), the station can start sending (IFS depends on service type) if the medium is busy, the station has to wait for a free IFS, then the station must additionally wait a random back-off time (collision avoidance, multiple of slot-time) ...
... if the medium is free for the duration of an Inter-Frame Space (IFS), the station can start sending (IFS depends on service type) if the medium is busy, the station has to wait for a free IFS, then the station must additionally wait a random back-off time (collision avoidance, multiple of slot-time) ...
Growing University in Namibia Moves to Next-Generation
... and the need for increased scalability. He began moving the university toward a virtualized solution with two Cisco® ASA 5585-X Series Next-Generation Firewalls supporting about 26 virtual firewalls. The Cisco ASA 5585-X firewalls were the only such devices that Maartens could find that had 10 GB/s ...
... and the need for increased scalability. He began moving the university toward a virtualized solution with two Cisco® ASA 5585-X Series Next-Generation Firewalls supporting about 26 virtual firewalls. The Cisco ASA 5585-X firewalls were the only such devices that Maartens could find that had 10 GB/s ...
Measurement guide and report template
... netsh interface ip delete arpcache This command also requires administrative privileges: Command Prompt (run as admin). Investigate the other parameters of arp (arp /?)! During this task we use DNS (Domain Name System) too. This protocol assigns domain names to IP addresses (more on this later). Lik ...
... netsh interface ip delete arpcache This command also requires administrative privileges: Command Prompt (run as admin). Investigate the other parameters of arp (arp /?)! During this task we use DNS (Domain Name System) too. This protocol assigns domain names to IP addresses (more on this later). Lik ...
VLSM and CIDR
... The purpose of VLSM is to alleviate the shortage of IP addresses VLSM allows: More than one subnet mask within the same NW Or . . . Multiple SNMasks with ONE IP Address Use of long mask on networks with few hosts Use of short mask on networks with many hosts In order to use VLSM, the routing protoco ...
... The purpose of VLSM is to alleviate the shortage of IP addresses VLSM allows: More than one subnet mask within the same NW Or . . . Multiple SNMasks with ONE IP Address Use of long mask on networks with few hosts Use of short mask on networks with many hosts In order to use VLSM, the routing protoco ...