Measurement guide and report template
... netsh interface ip delete arpcache This command also requires administrative privileges: Command Prompt (run as admin). Investigate the other parameters of arp (arp /?)! During this task we use DNS (Domain Name System) too. This protocol assigns domain names to IP addresses (more on this later). Lik ...
... netsh interface ip delete arpcache This command also requires administrative privileges: Command Prompt (run as admin). Investigate the other parameters of arp (arp /?)! During this task we use DNS (Domain Name System) too. This protocol assigns domain names to IP addresses (more on this later). Lik ...
How to Set Up Automatic Subnet Scan Using SolarWinds® IP Address Manager
... configure the transient period for any number of consecutive days up to one year. During a subsequent scan, if the network device appears online again, IPAM shows its associated status as "used." SolarWinds IPAM continuously scans all managed IP addresses on your network. If a device fails to respon ...
... configure the transient period for any number of consecutive days up to one year. During a subsequent scan, if the network device appears online again, IPAM shows its associated status as "used." SolarWinds IPAM continuously scans all managed IP addresses on your network. If a device fails to respon ...
Quality of Service in mobile ad hoc networks: a
... a cost-effective and cheaper way to share information among many mobile hosts. The unique characteristics of an ad hoc network differentiate it from other classes of networks. The mobile devices are connected through wireless links that may have several effects such as fading, environmental, obstacl ...
... a cost-effective and cheaper way to share information among many mobile hosts. The unique characteristics of an ad hoc network differentiate it from other classes of networks. The mobile devices are connected through wireless links that may have several effects such as fading, environmental, obstacl ...
Arista 7050SX 10/40G Data Center Switch Series
... The Arista 7050SX switches are members of the Arista 7050X series and key components of the Arista portfolio of data center switches. The Arista 7050X series are purpose-built 10/40GbE data center switches in compact and energy efficient form factors with wire speed Layer 2 and Layer 3 features comb ...
... The Arista 7050SX switches are members of the Arista 7050X series and key components of the Arista portfolio of data center switches. The Arista 7050X series are purpose-built 10/40GbE data center switches in compact and energy efficient form factors with wire speed Layer 2 and Layer 3 features comb ...
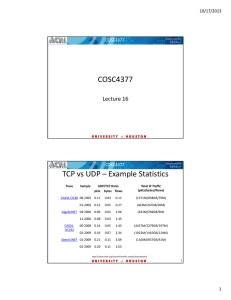
COSC4377 TCP vs UDP – Example Statistics
... – Stateless auto‐configuration requires no manual configuration of hosts, minimal (if any) configuration of routers, and no additional servers. The stateless mechanism allows a host to generate its own addresses using a combination of locally available information and information advertised by r ...
... – Stateless auto‐configuration requires no manual configuration of hosts, minimal (if any) configuration of routers, and no additional servers. The stateless mechanism allows a host to generate its own addresses using a combination of locally available information and information advertised by r ...
Presentation
... on the same physical network as well as prevent data network security threats from affecting voice services Shift from the traditional, reactive mindset of monitoring PBX-based voice to a proactive mindset where problems are identified before they affect service Create new, effective support mod ...
... on the same physical network as well as prevent data network security threats from affecting voice services Shift from the traditional, reactive mindset of monitoring PBX-based voice to a proactive mindset where problems are identified before they affect service Create new, effective support mod ...
Part 4
... For each conversation between geo points (A,B) we increase the intensity on the line between A and B Leskovec&Faloutsos, WWW 2008 ...
... For each conversation between geo points (A,B) we increase the intensity on the line between A and B Leskovec&Faloutsos, WWW 2008 ...
NetPointPro Family System Manual
... The unit maintains two software versions for safety. In the event that there is an issue with an upgrade, the previous version can always be reloaded. ...
... The unit maintains two software versions for safety. In the event that there is an issue with an upgrade, the previous version can always be reloaded. ...
Integrating Cisco Press Resources into the Academy Classroom
... select routes either dynamically, using routing protocols, or statically, with the engineer configuring the routers with routing information. • Logical addressing—Routers rely on the logical addressing defined by Layer 3 protocols. Layer 3 addressing (IP addressing) allows addresses to be grouped fo ...
... select routes either dynamically, using routing protocols, or statically, with the engineer configuring the routers with routing information. • Logical addressing—Routers rely on the logical addressing defined by Layer 3 protocols. Layer 3 addressing (IP addressing) allows addresses to be grouped fo ...
COEN 252 Computer Forensics
... MAC, a Linux laptop that has been compromised and is used for a Denial of Service attack. ...
... MAC, a Linux laptop that has been compromised and is used for a Denial of Service attack. ...
PVA-1000 Capture Agent
... All statements, technical information and recommendations related to the products herein are based upon information believed to be reliable or accurate. However, the accuracy or completeness thereof is not guaranteed, and no responsibility is assumed for any inaccuracies. The user assumes all risks ...
... All statements, technical information and recommendations related to the products herein are based upon information believed to be reliable or accurate. However, the accuracy or completeness thereof is not guaranteed, and no responsibility is assumed for any inaccuracies. The user assumes all risks ...
Re-ECN - Bob Briscoe
... ‘do-nothing’ doesn’t maintain liberal status quo, we just get more walls ...
... ‘do-nothing’ doesn’t maintain liberal status quo, we just get more walls ...
Network Protocols Pre.
... MAC, a Linux laptop that has been compromised and is used for a Denial of Service attack. ...
... MAC, a Linux laptop that has been compromised and is used for a Denial of Service attack. ...
Document
... Update messages tx to neighbours. Two ways • Not using split horizon technique: Updates are sent to all the neighbours. • Using split horizon technique. Updates sent to all the neighbours, except to those who informed about the best route. TCP/IP Architecture Advanced Features ...
... Update messages tx to neighbours. Two ways • Not using split horizon technique: Updates are sent to all the neighbours. • Using split horizon technique. Updates sent to all the neighbours, except to those who informed about the best route. TCP/IP Architecture Advanced Features ...
Multilayer Perceptron
... If neuron j lies in the output layer, the desired response dj(n) is known and the error ej(n) can be computed the local gradient δj(n) can be computed, and the weights updated using the delta rule (as given by the equations on the preceding slides) ...
... If neuron j lies in the output layer, the desired response dj(n) is known and the error ej(n) can be computed the local gradient δj(n) can be computed, and the weights updated using the delta rule (as given by the equations on the preceding slides) ...
Trading Structure for Randomness in Wireless Opportunistic Routing
... Network coding offers an elegant solution to the above problem. In our example, the destination has overheard one of the transmitted packets, p1 , but node R is unaware of this fortunate reception. With network coding, node R naturally forwards linear combinations of the received packets. For exampl ...
... Network coding offers an elegant solution to the above problem. In our example, the destination has overheard one of the transmitted packets, p1 , but node R is unaware of this fortunate reception. With network coding, node R naturally forwards linear combinations of the received packets. For exampl ...
Information Retrieval in Peer to Peer Systems
... integrates the contents of A in its own index in such a way that searching for a keyword becomes efficient (i.e. an inverted index) some node B can search the community by sending a query message to R if we suppose that A can satisfy B query criterion then R responds to B request with A's address ...
... integrates the contents of A in its own index in such a way that searching for a keyword becomes efficient (i.e. an inverted index) some node B can search the community by sending a query message to R if we suppose that A can satisfy B query criterion then R responds to B request with A's address ...
Applying SDN Architecture to 5G Slicing
... Major components of SDN are resources and controllers. Service delivery (send, receive, transmit, transform data) makes use of resources; provisioning, management and control of services and related resources is executed via the controller. Resources and the views onto them are not limited to just n ...
... Major components of SDN are resources and controllers. Service delivery (send, receive, transmit, transform data) makes use of resources; provisioning, management and control of services and related resources is executed via the controller. Resources and the views onto them are not limited to just n ...
AirLive AC.TOP Manual
... Federal Communication Commission Interference Statement This equipment has been tested and found to comply with the limits for a Class B digital device, pursuant to Part 15 of the FCC Rules. These limits are designed to provide reasonable protection against harmful interference in a residential inst ...
... Federal Communication Commission Interference Statement This equipment has been tested and found to comply with the limits for a Class B digital device, pursuant to Part 15 of the FCC Rules. These limits are designed to provide reasonable protection against harmful interference in a residential inst ...
Link Layer - Gordon College
... Random Access Protocols When node has packet to send transmit at full channel data rate R. no “pre-arranged” coordination among nodes two or more transmitting nodes ➜ “collision”, random access MAC protocol specifies: how to detect collisions how to recover from collisions (e.g., via ...
... Random Access Protocols When node has packet to send transmit at full channel data rate R. no “pre-arranged” coordination among nodes two or more transmitting nodes ➜ “collision”, random access MAC protocol specifies: how to detect collisions how to recover from collisions (e.g., via ...
Buffer-Sizing---CAIDA---May-2005 - McKeown Group
... Network users don’t like buffers Network operators don’t like buffers Router architects don’t like buffers We don’t need big buffers We’d often be better off with smaller ones ...
... Network users don’t like buffers Network operators don’t like buffers Router architects don’t like buffers We don’t need big buffers We’d often be better off with smaller ones ...
5 Configuring Settings on the Cisco Unified Wireless IP Phone 7925G
... You can control whether a Cisco Unified Wireless IP Phone 7925G has access to the Network Profiles menu from the Cisco Unified Communications Manager Administration Phone Configuration page. Use the Settings Access field in the Product Specific Configuration section of the phone configuration page. ...
... You can control whether a Cisco Unified Wireless IP Phone 7925G has access to the Network Profiles menu from the Cisco Unified Communications Manager Administration Phone Configuration page. Use the Settings Access field in the Product Specific Configuration section of the phone configuration page. ...