The Eavesdropper`s Dilemma
... syntax and semantics of communicated messages. Most eavesdropping systems rely on these standards to reduce the amount of information that must be captured and subsequently processed. Although recording only the traffic that abides by specifications is useful in the absence of active countermeasures ...
... syntax and semantics of communicated messages. Most eavesdropping systems rely on these standards to reduce the amount of information that must be captured and subsequently processed. Although recording only the traffic that abides by specifications is useful in the absence of active countermeasures ...
Network V
... value is decreased by at least one each time the packet is processed by a router (that is, each hop). When the value becomes zero, the router discards or drops the packet and it is removed from the network data flow. Protocol: This 8-bit binary value indicates the data payload type that the packet ...
... value is decreased by at least one each time the packet is processed by a router (that is, each hop). When the value becomes zero, the router discards or drops the packet and it is removed from the network data flow. Protocol: This 8-bit binary value indicates the data payload type that the packet ...
VPN Routers - D-Link
... Supports one USB 2.0 device to extend functionality via D-Link’s SharePort® feature. ...
... Supports one USB 2.0 device to extend functionality via D-Link’s SharePort® feature. ...
2 Huawei LTE PTT Broadband Trunking Solution
... Similar to the public mobile communications network, the trunking communications network is also developed from the analog technology to the digital technology and from only having voice services to having voice and data services. The 1G trunking communications network is an analog system that uses ...
... Similar to the public mobile communications network, the trunking communications network is also developed from the analog technology to the digital technology and from only having voice services to having voice and data services. The 1G trunking communications network is an analog system that uses ...
Wireless Training Guide - Broward County Public Schools
... •The response can contain additional information, if the client asked for it. •The server records that the IP address is in use. 5. Client releases You Can Have it Back •The client finishes it’s work, and send a DHCPRELEASE packet saying “I’m done with the IP address.” •The server records that the I ...
... •The response can contain additional information, if the client asked for it. •The server records that the IP address is in use. 5. Client releases You Can Have it Back •The client finishes it’s work, and send a DHCPRELEASE packet saying “I’m done with the IP address.” •The server records that the I ...
Tutorial Outline - Electrical Engineering Department
... Explicit Routing - MPLS vs. Traditional Routing •Connectionless nature of IP implies that routing is based on information in each packet header •Source routing is possible, but path must be contained in each IP header •Lengthy paths increase size of IP header, make it variable size, increase overhe ...
... Explicit Routing - MPLS vs. Traditional Routing •Connectionless nature of IP implies that routing is based on information in each packet header •Source routing is possible, but path must be contained in each IP header •Lengthy paths increase size of IP header, make it variable size, increase overhe ...
Issue - IETF
... Unicast solutions carry packets from edge to edge. Multicast signalling and content distribution has to pass from one multicast router to the next within the network interior. ...
... Unicast solutions carry packets from edge to edge. Multicast signalling and content distribution has to pass from one multicast router to the next within the network interior. ...
ppt
... traffic, but revenue from first class important to economic base (will pay for more plentiful bandwidth overall) • Not motivated by real-time! Motivated by economics and assurances © Srinivasan Seshan, 2002 ...
... traffic, but revenue from first class important to economic base (will pay for more plentiful bandwidth overall) • Not motivated by real-time! Motivated by economics and assurances © Srinivasan Seshan, 2002 ...
Efficient Micro-Mobility using Intra-domain Multicast
... throughout its movement within the domain. This allows for lighter-weight security during handover, as it is used for micro-mobility (i.e., intra-domain). In this paper we present two different approaches to multicast-based micro mobility, one approach is based on mobility proxies and the other base ...
... throughout its movement within the domain. This allows for lighter-weight security during handover, as it is used for micro-mobility (i.e., intra-domain). In this paper we present two different approaches to multicast-based micro mobility, one approach is based on mobility proxies and the other base ...
1. Use Cases
... 4. Register Traps (TrapInfo objects) to the Monitor module using/scanning the MIBTree. 2a. If the configuration file is unavailable or could not be parsed, do nothing and skip to line no.3 1. Failed to obtain information from the Moscad. 2. Elements defined in the configuration file do not appear in ...
... 4. Register Traps (TrapInfo objects) to the Monitor module using/scanning the MIBTree. 2a. If the configuration file is unavailable or could not be parsed, do nothing and skip to line no.3 1. Failed to obtain information from the Moscad. 2. Elements defined in the configuration file do not appear in ...
Networks of Workstations - Wright State University
... • Messages are sequences of bytes moving between processes • The sender and receiver must agree on the type structure of values in the message • “Marshalling” of data ...
... • Messages are sequences of bytes moving between processes • The sender and receiver must agree on the type structure of values in the message • “Marshalling” of data ...
IP: Addresses and Forwarding - RPI ECSE
... other routers’ Hellos by listing their RouterIDs “Link” relationship for purposes of Dijkstra maintained by each node sending a single Hello packet, instead of N packets. What about “flooding adjacencies”, I.e., Whom to send (flood) LSAs when a router generates or learns a new LSA? Does it nee ...
... other routers’ Hellos by listing their RouterIDs “Link” relationship for purposes of Dijkstra maintained by each node sending a single Hello packet, instead of N packets. What about “flooding adjacencies”, I.e., Whom to send (flood) LSAs when a router generates or learns a new LSA? Does it nee ...
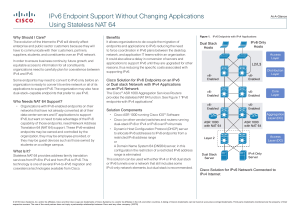
IPv6 Endpoint Support Without Changing Applications Using Stateless NAT 64
... © 2010 Cisco Systems, Inc. and/or its affiliates. Cisco and the Cisco Logo are trademarks of Cisco Systems, Inc. and/or its affiliates in the U.S. and other countries. A listing of Cisco's trademarks can be found at www.cisco.com/go/trademarks. Third-party trademarks mentioned are the property of th ...
... © 2010 Cisco Systems, Inc. and/or its affiliates. Cisco and the Cisco Logo are trademarks of Cisco Systems, Inc. and/or its affiliates in the U.S. and other countries. A listing of Cisco's trademarks can be found at www.cisco.com/go/trademarks. Third-party trademarks mentioned are the property of th ...
SK-NET FDDI
... • Transceiver is the receptacle (and its electronic components) on the adapter for the connection to the network. Network interface cards for fiber cabling use "fiber-optic transceivers". • SC is a standardized low cost fiber-optic cable type. Different from MIC cable (supporting two optical connect ...
... • Transceiver is the receptacle (and its electronic components) on the adapter for the connection to the network. Network interface cards for fiber cabling use "fiber-optic transceivers". • SC is a standardized low cost fiber-optic cable type. Different from MIC cable (supporting two optical connect ...
Chapter5_4th - Computer Science Division
... transmit at full channel data rate R. no a priori coordination among nodes two or more transmitting nodes ➜ “collision”, random access MAC protocol specifies: how to detect collisions how to recover from collisions (e.g., via delayed ...
... transmit at full channel data rate R. no a priori coordination among nodes two or more transmitting nodes ➜ “collision”, random access MAC protocol specifies: how to detect collisions how to recover from collisions (e.g., via delayed ...
chapter5 - Computer Science Division
... transmit at full channel data rate R. no a priori coordination among nodes two or more transmitting nodes ➜ “collision”, random access MAC protocol specifies: how to detect collisions how to recover from collisions (e.g., via delayed ...
... transmit at full channel data rate R. no a priori coordination among nodes two or more transmitting nodes ➜ “collision”, random access MAC protocol specifies: how to detect collisions how to recover from collisions (e.g., via delayed ...
chapter5
... If you use these slides (e.g., in a class) in substantially unaltered form, that you mention their source (after all, we’d like people to use our book!) If you post any slides in substantially unaltered form on a www site, that you note that they are adapted from (or perhaps identical to) our sl ...
... If you use these slides (e.g., in a class) in substantially unaltered form, that you mention their source (after all, we’d like people to use our book!) If you post any slides in substantially unaltered form on a www site, that you note that they are adapted from (or perhaps identical to) our sl ...
User Manual for the NETGEAR PS121 Mini Print Server
... VCCI Statement This equipment is in the Class B category (information equipment to be used in a residential area or an adjacent area thereto) and conforms to the standards set by the Voluntary Control Council for Interference by Data Processing Equipment and Electronic Office Machines aimed at preve ...
... VCCI Statement This equipment is in the Class B category (information equipment to be used in a residential area or an adjacent area thereto) and conforms to the standards set by the Voluntary Control Council for Interference by Data Processing Equipment and Electronic Office Machines aimed at preve ...
lim-previous-version
... 2 years as a researcher for ‘Telephone Number Mapping (ENUM)’ I wrote related ‘internet-draft’, and became a author of ‘RFC5346 Operational Requirements for ENUM-Based Softswitch Use’in 2008. ...
... 2 years as a researcher for ‘Telephone Number Mapping (ENUM)’ I wrote related ‘internet-draft’, and became a author of ‘RFC5346 Operational Requirements for ENUM-Based Softswitch Use’in 2008. ...
the document - Support
... of flexible data reliability policies, allowing data copies to be stored on different servers. Data will not be lost even if a server is faulty. FusionStorage also protects valid data slices against loss. If a hard disk or server is faulty, valid data can be rebuilt concurrently. It takes less than ...
... of flexible data reliability policies, allowing data copies to be stored on different servers. Data will not be lost even if a server is faulty. FusionStorage also protects valid data slices against loss. If a hard disk or server is faulty, valid data can be rebuilt concurrently. It takes less than ...
telecommunication and information networks the network services
... – Skype uses cipher. Unlike traditional telephone communication and other VoIP-systems, transfering of voice information ciphers with the help of 128-bites and more cryptographic codes, that makes practically impossible the passive interception of Skype conversations and impossibility to decipher th ...
... – Skype uses cipher. Unlike traditional telephone communication and other VoIP-systems, transfering of voice information ciphers with the help of 128-bites and more cryptographic codes, that makes practically impossible the passive interception of Skype conversations and impossibility to decipher th ...
2. - people
... 2. Switching is functioning only in Ethernet. (Please recall that Data Link header is also called as Ethernet header.) 3. Switching is in layer 2 Data Link layer 4. Switching is faster than routing 5. Switch can separate collision domain. ...
... 2. Switching is functioning only in Ethernet. (Please recall that Data Link header is also called as Ethernet header.) 3. Switching is in layer 2 Data Link layer 4. Switching is faster than routing 5. Switch can separate collision domain. ...
Unit 5 - WordPress.com
... The multistage switch has one drawback-blocking during heavy traffics. The whole idea of multistage switching is to share crosspoints in the middle stage crossbars. In a network, a cross-bar switch is a device that is capable of channeling data between any two devices that are attached to it up to i ...
... The multistage switch has one drawback-blocking during heavy traffics. The whole idea of multistage switching is to share crosspoints in the middle stage crossbars. In a network, a cross-bar switch is a device that is capable of channeling data between any two devices that are attached to it up to i ...
TL-WN350G_350GD User Guide - TP-Link
... The TP-LINK TL-WN350G/TL-WN350GD 54M Wireless PCI Adapter will provide you the flexibility to install your PC in the most convenient location available, without the cost of running network cables. The Adapter's auto-sensing capability allows high packet transfer rate of up to 54Mbps for maximum thro ...
... The TP-LINK TL-WN350G/TL-WN350GD 54M Wireless PCI Adapter will provide you the flexibility to install your PC in the most convenient location available, without the cost of running network cables. The Adapter's auto-sensing capability allows high packet transfer rate of up to 54Mbps for maximum thro ...