Network Test 3 Study Guide
... A computer on a LAN can communicate with other devices on the same LAN because a switch uses the computer’s physical address. However, when a computer wants to communicate with a device on another network, it must send the packet to the router so the computer needs to know the address of the router. ...
... A computer on a LAN can communicate with other devices on the same LAN because a switch uses the computer’s physical address. However, when a computer wants to communicate with a device on another network, it must send the packet to the router so the computer needs to know the address of the router. ...
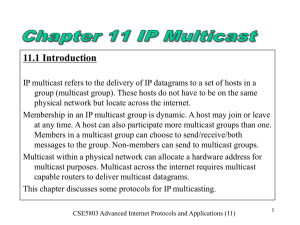
IP Multicast
... routers when a multicast group has a large number of members and multiple senders. • A multicast group requires a core (rendez-vous point). • Receivers “join” the (shortest-path) tree rooted at the core only one tree per multicast group (used for multiple senders). • Sources send multicast data to ...
... routers when a multicast group has a large number of members and multiple senders. • A multicast group requires a core (rendez-vous point). • Receivers “join” the (shortest-path) tree rooted at the core only one tree per multicast group (used for multiple senders). • Sources send multicast data to ...
Achieving WAN Operational Efficiency with the Cisco ASR 1000 Series
... Operational efficiency: Integrated devices have fewer components and fewer user interfaces to manage. Troubleshooting faults and errors is easier with integrated technology as compared to overlay appliances ...
... Operational efficiency: Integrated devices have fewer components and fewer user interfaces to manage. Troubleshooting faults and errors is easier with integrated technology as compared to overlay appliances ...
Group Address
... inform other routers that 128.186.4.0/24 has a G1 member. • When router A receives the next G1 packet from S1, it will calculate the path and forward the packet to the FDDI ring 128.186.3.0. Routers B, C, D and F will all calculate paths to 128.186.4.0/24, with only D forwarding the packet to G. Rou ...
... inform other routers that 128.186.4.0/24 has a G1 member. • When router A receives the next G1 packet from S1, it will calculate the path and forward the packet to the FDDI ring 128.186.3.0. Routers B, C, D and F will all calculate paths to 128.186.4.0/24, with only D forwarding the packet to G. Rou ...
Firewall
... Allow for unrestricted Internet access from all the machines in LAN Allow for SSH access to the firewall machine from outside LAN Permit Auth, that is used by services like SMTP and IRC LAN is hosting a web server (on behalf of the whole LAN) and that this HTTPD server is running on machine 192.168. ...
... Allow for unrestricted Internet access from all the machines in LAN Allow for SSH access to the firewall machine from outside LAN Permit Auth, that is used by services like SMTP and IRC LAN is hosting a web server (on behalf of the whole LAN) and that this HTTPD server is running on machine 192.168. ...
5 Requirements - ISO/IEC JTC1 SC25 WG1 Home Page
... layers of specific WAN or HAN protocols are not specified, but are left entirely to the product manufacturer. The RGIP and other protocol stacks rely on an interoperability language (specified in the International Standard, ISO/IEC 18012) that resides above lay er seven, the application layer (of th ...
... layers of specific WAN or HAN protocols are not specified, but are left entirely to the product manufacturer. The RGIP and other protocol stacks rely on an interoperability language (specified in the International Standard, ISO/IEC 18012) that resides above lay er seven, the application layer (of th ...
7050TX-48
... switches offer low latency and a shared 12 MB packet buffer pool that is allocated dynamically to ports that are congested. With typical power consumption of less than 5 watts per 10GbE port the 7050TX Series are power efficient. An optional builtin SSD supports advanced logging, data capture and other ...
... switches offer low latency and a shared 12 MB packet buffer pool that is allocated dynamically to ports that are congested. With typical power consumption of less than 5 watts per 10GbE port the 7050TX Series are power efficient. An optional builtin SSD supports advanced logging, data capture and other ...
Broadband Internet Performance: A View From the
... the same access link. Han et al. [18] measured access network performance from a laptop that searched for open wireless networks. This approach is convenient because it does not require user intervention, but it does not scale to a large number of access networks, cannot collect continuous measureme ...
... the same access link. Han et al. [18] measured access network performance from a laptop that searched for open wireless networks. This approach is convenient because it does not require user intervention, but it does not scale to a large number of access networks, cannot collect continuous measureme ...
ruggedcom rx1500/1501
... OSPF is a routing protocol that determines the best path for routing IP traffic over a TCP/IP network based on link states between nodes and several quality parameters. OSPF is an interior gateway protocol (IGP), which is designed to work within an autonomous system. It is also a link state protocol ...
... OSPF is a routing protocol that determines the best path for routing IP traffic over a TCP/IP network based on link states between nodes and several quality parameters. OSPF is an interior gateway protocol (IGP), which is designed to work within an autonomous system. It is also a link state protocol ...
Stored Media Streaming in BitTorrent-like P2P Networks
... In RedCarpet, the stored media file is divided into segments, each segment comprising consecutive pieces. The authors apply random, local-rarest, and sequential download policies to choosing a piece from the target segment (each segment is picked sequentially). On the other hand, we propose download ...
... In RedCarpet, the stored media file is divided into segments, each segment comprising consecutive pieces. The authors apply random, local-rarest, and sequential download policies to choosing a piece from the target segment (each segment is picked sequentially). On the other hand, we propose download ...
ARP Spoofing Prevention ................................44
... coffee shops and universities. Innovative ways to utilize WLAN technology are allowing people to work and communicate more efficiently. Increased mobility and the absence of cabling and other types of fixed infrastructure have proven to be beneficial to many users. Wireless adapter cards used on lap ...
... coffee shops and universities. Innovative ways to utilize WLAN technology are allowing people to work and communicate more efficiently. Increased mobility and the absence of cabling and other types of fixed infrastructure have proven to be beneficial to many users. Wireless adapter cards used on lap ...
Network Configuration Example Adding a New Routing Device to
... to log in to the router management console interface for the first time, how to log in to your routing device’s management Ethernet port, and how to start the command-line interface (CLI) in configuration mode. From configuration mode, you will learn how to configure your administration user account ...
... to log in to the router management console interface for the first time, how to log in to your routing device’s management Ethernet port, and how to start the command-line interface (CLI) in configuration mode. From configuration mode, you will learn how to configure your administration user account ...
IPV6 - Workshops
... routing prefix and m bits to the subnet identifier. 64 bits are available for interface identifiers, which are constructed based on the IEEE “EUI-64” format. ...
... routing prefix and m bits to the subnet identifier. 64 bits are available for interface identifiers, which are constructed based on the IEEE “EUI-64” format. ...
Tutorial on Signaling System 7 (SS7)
... routes each incoming message to an outgoing signaling link based on routing information contained in the SS7 message. Because it acts as a network hub, an STP provides improved utilization of the SS7 network by eliminating the need for direct links between signaling points. An STP may perform global ...
... routes each incoming message to an outgoing signaling link based on routing information contained in the SS7 message. Because it acts as a network hub, an STP provides improved utilization of the SS7 network by eliminating the need for direct links between signaling points. An STP may perform global ...
NOTICE OF USE AND DISCLOSURE
... Class C – Continuously listening ......................................................................................... 70 17 Class C: Continuously listening end-device................................................................ 71 17.1 Second receive window duration for Class C ............. ...
... Class C – Continuously listening ......................................................................................... 70 17 Class C: Continuously listening end-device................................................................ 71 17.1 Second receive window duration for Class C ............. ...
Strategy for VOIP
... – seamless merging of LAN/WAN – avoids duplication of paging protocols, resulting in cost ...
... – seamless merging of LAN/WAN – avoids duplication of paging protocols, resulting in cost ...
Document
... 4 subnets can be represented with 2 bits (22 = 4) For a class B address, which already uses 16 bits for the network portion, the address would use 18 bits for the subnet portion ...
... 4 subnets can be represented with 2 bits (22 = 4) For a class B address, which already uses 16 bits for the network portion, the address would use 18 bits for the subnet portion ...
lect22 - Computer and Information Sciences
... Routers vs. Bridges Bridges + and + Bridge operation is simpler requiring less processing bandwidth - Topologies are restricted with bridges: a spanning tree must be built to avoid cycles - Bridges do not offer protection from broadcast storms (endless broadcasting by a host will be forwarded by a ...
... Routers vs. Bridges Bridges + and + Bridge operation is simpler requiring less processing bandwidth - Topologies are restricted with bridges: a spanning tree must be built to avoid cycles - Bridges do not offer protection from broadcast storms (endless broadcasting by a host will be forwarded by a ...
Document
... Used to send a large amount of information that is divided into multiple packets for transmission Uses packet sequence numbers to verify packet order and acknowledges the receipt of each packet The lost or improperly delivered packets, which are not acknowledged as a successful receipt, can be ...
... Used to send a large amount of information that is divided into multiple packets for transmission Uses packet sequence numbers to verify packet order and acknowledges the receipt of each packet The lost or improperly delivered packets, which are not acknowledged as a successful receipt, can be ...
Presentation - Constantia Fibre
... Open Access – Link Africa provides each last mile link to the market on an open access basis. This “plug and play” connectivity is attractive to licensed service providers and enables competition, greater choice, and ultimately the consumer benefits from this. Route Redundancy – Link Africa is the o ...
... Open Access – Link Africa provides each last mile link to the market on an open access basis. This “plug and play” connectivity is attractive to licensed service providers and enables competition, greater choice, and ultimately the consumer benefits from this. Route Redundancy – Link Africa is the o ...
Gnutella2: A Better Gnutella?
... Gnutella has some serious flaws (scalability, performance, lack of cooperation incentives and servent abuse). Gnutella2 ...
... Gnutella has some serious flaws (scalability, performance, lack of cooperation incentives and servent abuse). Gnutella2 ...
PPT - Mobile Multimedia Laboratory
... • Fully distributed systems are hard to monitor – Performance predictions are simply guesses • What happens when we modify a strategy? – Existing simulators were not detailed enough • Some omit large parts of the protocol • Others only work over abstract networks • Most are custom-built and hard to ...
... • Fully distributed systems are hard to monitor – Performance predictions are simply guesses • What happens when we modify a strategy? – Existing simulators were not detailed enough • Some omit large parts of the protocol • Others only work over abstract networks • Most are custom-built and hard to ...