The Interplanetary Internet Implemented on a Terrestrial testbed
... future deep space network architecture which will survive such extreme conditions. The remote networks of the solar system such as the Earth based Internet and other planetary networks support various protocols and they hook up to the IPN backbone by choosing among mobile satellite gateways that wou ...
... future deep space network architecture which will survive such extreme conditions. The remote networks of the solar system such as the Earth based Internet and other planetary networks support various protocols and they hook up to the IPN backbone by choosing among mobile satellite gateways that wou ...
Chapter 20-22
... Filling and updating routing tables (by finding the shortest paths from each source to each destination) This part is called Routing Deciding which output interface an incoming packet should be transmitted on (by referring to the routing table). This part is called Forwarding ...
... Filling and updating routing tables (by finding the shortest paths from each source to each destination) This part is called Routing Deciding which output interface an incoming packet should be transmitted on (by referring to the routing table). This part is called Forwarding ...
Dynamic Bayesian Networks
... gur eS3: Network prior. Existing biology iscaptured and integrated during modeling using aprior probability tribution on graphs P (G) ∝ exp(λf (G)), with f (G) = − |E (G)\ E ∗ | where E (G) is the set of edges ntained in G and E ∗ is a set of a priori expected edges. The graph shows edge set E ∗ . E ...
... gur eS3: Network prior. Existing biology iscaptured and integrated during modeling using aprior probability tribution on graphs P (G) ∝ exp(λf (G)), with f (G) = − |E (G)\ E ∗ | where E (G) is the set of edges ntained in G and E ∗ is a set of a priori expected edges. The graph shows edge set E ∗ . E ...
Slides
... • Each condi7onal probability distribu7on is a factor. Trivial ! • Also works when condi7oning on some evidence. • Can we go from a Bayesian Network to an undirected graph that’s an I-‐map? Ask about examp ...
... • Each condi7onal probability distribu7on is a factor. Trivial ! • Also works when condi7oning on some evidence. • Can we go from a Bayesian Network to an undirected graph that’s an I-‐map? Ask about examp ...
Go There!
... 2. Performs the ANDing operation 3. Looks for entry in routing table 4. Re-encapsulates packet into a frame 5. Switches the packet out the correct interface ...
... 2. Performs the ANDing operation 3. Looks for entry in routing table 4. Re-encapsulates packet into a frame 5. Switches the packet out the correct interface ...
The first full core brand franchise Hilton Hotel in Britain, Micron
... At the beginning of the installation, Micron commissioned a hosted telephony solution to facilitate the pre opening activities. Because of the level of interest in this landmark project, the solution needed to be scalable and flexible in order to best represent the prestigious Hilton brand. The solu ...
... At the beginning of the installation, Micron commissioned a hosted telephony solution to facilitate the pre opening activities. Because of the level of interest in this landmark project, the solution needed to be scalable and flexible in order to best represent the prestigious Hilton brand. The solu ...
1. Introduction
... 2.2.2Pastry routing procedure The Pastry routing procedure is as follows [4]: Given a message, a node first tries to route the message to its leaf set. If the key is not represented in the leaf set, the node then tries to forward the message to an entry in its routing table that shares a common pref ...
... 2.2.2Pastry routing procedure The Pastry routing procedure is as follows [4]: Given a message, a node first tries to route the message to its leaf set. If the key is not represented in the leaf set, the node then tries to forward the message to an entry in its routing table that shares a common pref ...
Document
... summarize info about an area and (2) send info amongst areas • A special area called the backbone is used to tie together all of the areas – backbone is primary area and all other areas are secondary areas – backbone area uses backbone routers ...
... summarize info about an area and (2) send info amongst areas • A special area called the backbone is used to tie together all of the areas – backbone is primary area and all other areas are secondary areas – backbone area uses backbone routers ...
User-Perceived Performance Measurement on the Internet
... Users are relatively distant from the network administrators IP is the only service provided by the network SNMP or something like it? No… ...
... Users are relatively distant from the network administrators IP is the only service provided by the network SNMP or something like it? No… ...
IPv6
... Priority: identify priority among datagrams in flow Flow Label: identify datagrams in same “flow.” (concept of“flow” not well defined). Next header: identify upper layer protocol for data ...
... Priority: identify priority among datagrams in flow Flow Label: identify datagrams in same “flow.” (concept of“flow” not well defined). Next header: identify upper layer protocol for data ...
Glossary for Ingrasys FISC Servers
... NetWare 3.x servers store all the information about users, groups, passwords, and rights in a database stored on the server called the bindery. NetWare 4.x servers (NDS applied) can appear to have a bindery through bindery emulation, a feature which is enabled by default. There is a separate bindery ...
... NetWare 3.x servers store all the information about users, groups, passwords, and rights in a database stored on the server called the bindery. NetWare 4.x servers (NDS applied) can appear to have a bindery through bindery emulation, a feature which is enabled by default. There is a separate bindery ...
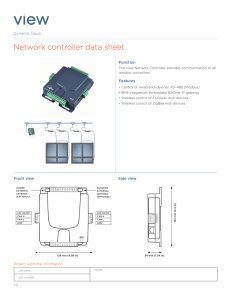
network controller data sheet
... The View network controller carries a warranty for a period of 5 years from date of delivery by View. Refer to standard warranty terms and conditions for more details. ...
... The View network controller carries a warranty for a period of 5 years from date of delivery by View. Refer to standard warranty terms and conditions for more details. ...
Introduction to Computer Networking - PDST
... Wireless networks can be configured in an ad hoc/peer-to-peer arrangement or as a local area network. Ad Hoc/Peer-to-Peer Configuration This is the most basic wireless network configuration. It relies on the wireless network adapters installed in the computers that are communicating with each other. ...
... Wireless networks can be configured in an ad hoc/peer-to-peer arrangement or as a local area network. Ad Hoc/Peer-to-Peer Configuration This is the most basic wireless network configuration. It relies on the wireless network adapters installed in the computers that are communicating with each other. ...
Investor Presentation
... – For TDM or legacy services they need additional overlay networks for each service type – Current profits are based on wealth of existing legacy services (Leased Line, FR, ATM...) for business customers and Mobile Backhaul for Mobile Operators • Traditional services are still the dominant element i ...
... – For TDM or legacy services they need additional overlay networks for each service type – Current profits are based on wealth of existing legacy services (Leased Line, FR, ATM...) for business customers and Mobile Backhaul for Mobile Operators • Traditional services are still the dominant element i ...
TREND Big Picture on Energy-Efficient Backbone Networks Esther Le Rouzic, Raluca-Maria Indre
... ENERGY EFFICIENT NETWORK OPERATION ...
... ENERGY EFFICIENT NETWORK OPERATION ...
IP spoofing - University Of Worcester
... TOC/TOU (Time of check/Time of use) hacking tool that “watches” access to web apps via the TCP/UDP port depends on the fact that a user privilege change doesn’t come into effect until they log out and log in again » TOC is when the user logs on… » TOU is when that web app is actually used by the ...
... TOC/TOU (Time of check/Time of use) hacking tool that “watches” access to web apps via the TCP/UDP port depends on the fact that a user privilege change doesn’t come into effect until they log out and log in again » TOC is when the user logs on… » TOU is when that web app is actually used by the ...
PARAM Padma SuperComputer
... PARAM Padma has 12 PARAMNet II switches connected to two-level configuration to form 64 node CLOS network ...
... PARAM Padma has 12 PARAMNet II switches connected to two-level configuration to form 64 node CLOS network ...
slides presentation - comp
... • Connection of two IPv6-only IMS islands has to be made over IPv4 network. • Compare with 6bone. ...
... • Connection of two IPv6-only IMS islands has to be made over IPv4 network. • Compare with 6bone. ...
ATIS NGN
... • A FOUR layer FUNCTIONAL model is used • Transport is IP based with appropriate interfaces to User side, Other networks, and upper layer functional entities (FEs) • Session admission, authentication and enforcement of policy are executed via the “Session and Policy” control functions • Value-added ...
... • A FOUR layer FUNCTIONAL model is used • Transport is IP based with appropriate interfaces to User side, Other networks, and upper layer functional entities (FEs) • Session admission, authentication and enforcement of policy are executed via the “Session and Policy” control functions • Value-added ...