PhoneNet: a Phone-to-Phone Network for Group Communication in a LAN.
... In PhoneNet, we run the switchboard alongside NOX. In order to establish participants, one of the participants would act as an initiator and perform the following three steps: (1) discover the NOX in the network, (2) set up a chat room on the NOX, and (3) invite other participants and have them subs ...
... In PhoneNet, we run the switchboard alongside NOX. In order to establish participants, one of the participants would act as an initiator and perform the following three steps: (1) discover the NOX in the network, (2) set up a chat room on the NOX, and (3) invite other participants and have them subs ...
Lecture 3 - Network hardware, Ethernet
... • Implemented on coaxial cable of up to 500 meters in length • Hosts connect by “tapping” into it. – Taps at least 2.5 meters apart ...
... • Implemented on coaxial cable of up to 500 meters in length • Hosts connect by “tapping” into it. – Taps at least 2.5 meters apart ...
paper
... (or scheduling) deals with the supply of network resources random slotted-ALOHA-like mechanism. The network is assuch as interference-free sets of links, whereas the concern of sumed to operate in time slots and, for every slot, a node is resource allocation is how to assign the available resources ...
... (or scheduling) deals with the supply of network resources random slotted-ALOHA-like mechanism. The network is assuch as interference-free sets of links, whereas the concern of sumed to operate in time slots and, for every slot, a node is resource allocation is how to assign the available resources ...
Chapter 1: Foundation
... Delay X Bandwidth How many bits the sender must transmit before the first bit arrives at the receiver if the sender keeps the pipe full Takes another one-way latency to receive a response from the receiver If the sender does not fill the pipe—send a whole delay × bandwidth product’s worth of data be ...
... Delay X Bandwidth How many bits the sender must transmit before the first bit arrives at the receiver if the sender keeps the pipe full Takes another one-way latency to receive a response from the receiver If the sender does not fill the pipe—send a whole delay × bandwidth product’s worth of data be ...
View File
... Each interface defines what information and services a layer must provide for the layer above it. Well defined interfaces and layer functions provide modularity to a network Organizations of the layers Network support layers : Layers 1, 2, 3 User support layer : Layer 5, 6, 7 ...
... Each interface defines what information and services a layer must provide for the layer above it. Well defined interfaces and layer functions provide modularity to a network Organizations of the layers Network support layers : Layers 1, 2, 3 User support layer : Layer 5, 6, 7 ...
Boguslawski, P., Mahdjoubi, L., Zverovich, V. and Fadli, F. (2016)
... However, in case of emergency situation everybody most likely would like to leave the building as soon as possible. It may be difficult if the evacuation routes and location of dangerous areas are unknown. A similar situation applies to rescue teams, which come to the scene and need to get to people ...
... However, in case of emergency situation everybody most likely would like to leave the building as soon as possible. It may be difficult if the evacuation routes and location of dangerous areas are unknown. A similar situation applies to rescue teams, which come to the scene and need to get to people ...
5. Fixed and mobile convergence
... Fixed and Mobile Convergence (FMC) is concerned with the provision of network and service capabilities, which are independent of the access technique. This does not necessarily imply the physical convergence of networks. It is concerned with the development of converged network capabilities and supp ...
... Fixed and Mobile Convergence (FMC) is concerned with the provision of network and service capabilities, which are independent of the access technique. This does not necessarily imply the physical convergence of networks. It is concerned with the development of converged network capabilities and supp ...
Novell IPX - Austin Community College
... When a host on one network segment transmits data to a host on another network segment, and the two are connected by two or more switches, each switch receives the data frames, looks up the location of the receiving device, and forwards the frame. Because each switch forwarded the frame, there is a ...
... When a host on one network segment transmits data to a host on another network segment, and the two are connected by two or more switches, each switch receives the data frames, looks up the location of the receiving device, and forwards the frame. Because each switch forwarded the frame, there is a ...
VPN and NAT
... gateway between internal hosts and the Internet – Internal hosts send requests to the application gateway – Application gateway passes the request to the destination host – Destination host sends reply to the application gateway – Application gateway passes reply to originating internal host ...
... gateway between internal hosts and the Internet – Internal hosts send requests to the application gateway – Application gateway passes the request to the destination host – Destination host sends reply to the application gateway – Application gateway passes reply to originating internal host ...
A Scalable Self-organizing Map Algorithm for Textual Classification
... Intuition Behind the Technique • Our objective is to modify the SOM algorithm so as to be able to compute distances to all nodes(Step 3) and update the weights of nodes (Step 4) at a number of iterations proportional to the number of non-zero coordinates in the input vector, represented here as P. ...
... Intuition Behind the Technique • Our objective is to modify the SOM algorithm so as to be able to compute distances to all nodes(Step 3) and update the weights of nodes (Step 4) at a number of iterations proportional to the number of non-zero coordinates in the input vector, represented here as P. ...
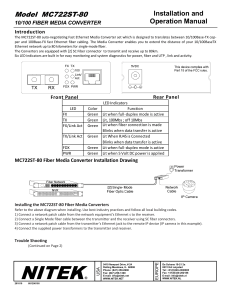
MC722ST-80
... Blinks when data transfer is active Lit When RJ45 is Connected Blinks when data transfer is active Lit when full‐duplex mode is active Lit when 5 Volt DC power is applied ...
... Blinks when data transfer is active Lit When RJ45 is Connected Blinks when data transfer is active Lit when full‐duplex mode is active Lit when 5 Volt DC power is applied ...
with four-month extension to 31 August 2016 for 5/SA1 network costs
... The amount of data forecast to be generated and stored is astounding. This will drive an exponential growth in network traffic. IP backbone trunks will need to be 400Gbps by 2020 & a terabit by 2025 ...
... The amount of data forecast to be generated and stored is astounding. This will drive an exponential growth in network traffic. IP backbone trunks will need to be 400Gbps by 2020 & a terabit by 2025 ...
Week_Five_Network
... and technical goals for a corporate network design, it might be necessary to recommend a network topology of many interrelated components. The task is made easier if you can “divide and conquer” the job and develop the design in independent layers. Network design experts can develop a hierarchical n ...
... and technical goals for a corporate network design, it might be necessary to recommend a network topology of many interrelated components. The task is made easier if you can “divide and conquer” the job and develop the design in independent layers. Network design experts can develop a hierarchical n ...
Chapter 5 Overview of Network Services - computerscience
... • To use Active Directory, at least one server must be configured as a Domain Controller (DC). • It is recommended that there be at least two DCs in each domain, for fault tolerance. • Replication is the process of copying data from one computer to one or more other computers and synchronizing that ...
... • To use Active Directory, at least one server must be configured as a Domain Controller (DC). • It is recommended that there be at least two DCs in each domain, for fault tolerance. • Replication is the process of copying data from one computer to one or more other computers and synchronizing that ...
Communication Systems and Networks
... outperforms AODV in less stressful situationssmall number of nodes and lower mobility. AODV outperforms DSR in more stressful situations. DSR consistently generates less routing load than ...
... outperforms AODV in less stressful situationssmall number of nodes and lower mobility. AODV outperforms DSR in more stressful situations. DSR consistently generates less routing load than ...
Global surveillance and response to the threat
... national (e.g. Sentiweb in France). This approach to information gathering is being increasingly used by healthcare professionals, an example being the Global Public Health Information Network (GPHIN), an electronic surveillance system developed by Health Canada which has search engines that activel ...
... national (e.g. Sentiweb in France). This approach to information gathering is being increasingly used by healthcare professionals, an example being the Global Public Health Information Network (GPHIN), an electronic surveillance system developed by Health Canada which has search engines that activel ...
layer - Open Learning Environment - Free University of Bozen
... Receives data from the above, splits it up into smaller units that are then passed to the network layer Separates the “user/application layers” (above) from the “communication layers” (below) First layer that virtually connects the two endpoints directly Determines the main features underlying users ...
... Receives data from the above, splits it up into smaller units that are then passed to the network layer Separates the “user/application layers” (above) from the “communication layers” (below) First layer that virtually connects the two endpoints directly Determines the main features underlying users ...
reportfeb13
... attention as a means of providing critical information in disaster environments. First responders at a disaster site must be able to transmit and receive critical information related to Building design and floor plan, Building structural integrity, Stability and safety of building pathways, and Loca ...
... attention as a means of providing critical information in disaster environments. First responders at a disaster site must be able to transmit and receive critical information related to Building design and floor plan, Building structural integrity, Stability and safety of building pathways, and Loca ...
Topology Selection Criteria for a Virtual Topology Controller based
... others. We present the following weight selection strategies for evaluating topologies. Our motivation in selecting different weights for different attractors is based on a few factors. First, the attractor update strategy is not optimal (line 8), and it is hard to devise an optimal update. For exam ...
... others. We present the following weight selection strategies for evaluating topologies. Our motivation in selecting different weights for different attractors is based on a few factors. First, the attractor update strategy is not optimal (line 8), and it is hard to devise an optimal update. For exam ...
Traffic Measurement and Analysis of Wide Area
... This paper presents some results regarding the bandwidth utilization of the WAN link connecting the UiTM Perlis campus network and UiTM Shah Alam campus network. Our study utilized a passive measurement of the traffic that passed through the port of core switch that is connected to the router that h ...
... This paper presents some results regarding the bandwidth utilization of the WAN link connecting the UiTM Perlis campus network and UiTM Shah Alam campus network. Our study utilized a passive measurement of the traffic that passed through the port of core switch that is connected to the router that h ...