CIMARRON TELEPHONE COMPANY BROADBAND
... High Speed Internet Service increases, and as demand for higher bandwidth applications increases, we monitor effects on network performance and plan upgrades. We upgrade our capacity when network usage equals 80% of network capacity. Effects on end user experience: Periods of high network demand may ...
... High Speed Internet Service increases, and as demand for higher bandwidth applications increases, we monitor effects on network performance and plan upgrades. We upgrade our capacity when network usage equals 80% of network capacity. Effects on end user experience: Periods of high network demand may ...
MICRO-35 Tutorial - Applied Research Laboratory
... c) Uses dense wavelength division multiplexing (DWDM) d) Not cutting edge technology ...
... c) Uses dense wavelength division multiplexing (DWDM) d) Not cutting edge technology ...
PORTO - Politecnico di Torino
... a simple evaluation of P2P-TV systems, focusing on their impact on the transport network. A preliminary distinction must be done: when using a general P2P application, two different topologies have to be considered: i) a logical topology at application level, made up by peers, which is created and ...
... a simple evaluation of P2P-TV systems, focusing on their impact on the transport network. A preliminary distinction must be done: when using a general P2P application, two different topologies have to be considered: i) a logical topology at application level, made up by peers, which is created and ...
Chap. 2 Basic concepts
... because every device must be connected to every other device, installation and reconfiguration are difficult the sheer bulk of the wiring can be greater than the available space(in walls, ceiling, or floors) can accommodate the hardware required to connect each link(I/O port and cable) can be pro ...
... because every device must be connected to every other device, installation and reconfiguration are difficult the sheer bulk of the wiring can be greater than the available space(in walls, ceiling, or floors) can accommodate the hardware required to connect each link(I/O port and cable) can be pro ...
ppt
... • Both can be learned from data, but –learning structure is much harder than learning parameters –learning when some nodes are hidden, or with missing data harder still ...
... • Both can be learned from data, but –learning structure is much harder than learning parameters –learning when some nodes are hidden, or with missing data harder still ...
Chapter 6 Computers in Your Future Template
... As a caller moves from one area to another, a new cell site steps in to keep the signal strong. The sites are connected to a Mobile Telephone Switching Office (MTSO), which is connected to the standard PSTN telephone system. ...
... As a caller moves from one area to another, a new cell site steps in to keep the signal strong. The sites are connected to a Mobile Telephone Switching Office (MTSO), which is connected to the standard PSTN telephone system. ...
chap2_2ed_5July02 - Mount Holyoke College
... packet processing • + Bridge tables are self learning • - All traffic confined to spanning tree, even when alternative bandwidth is available • - Bridges do not offer protection from broadcast storms ...
... packet processing • + Bridge tables are self learning • - All traffic confined to spanning tree, even when alternative bandwidth is available • - Bridges do not offer protection from broadcast storms ...
Slides - TERENA Networking Conference 2008
... QoS guarantees – Many applications requiring high bandwidth and/or low delay e.g.: video streaming, video conferencing, remote editing of files, well performing use of remote services ...
... QoS guarantees – Many applications requiring high bandwidth and/or low delay e.g.: video streaming, video conferencing, remote editing of files, well performing use of remote services ...
1 - Cisco Support Community
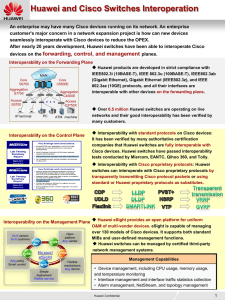
... China Telcom's HQ campus network ODS upgrade project: The gateway originally deployed on Cisco C3560 was moved to the S9300 CSS system newly deployed on the network. The S9300 switches worked as aggregation switches and used CSS technology to improve network reliability. Cisco 3560 and Huawei S9300 ...
... China Telcom's HQ campus network ODS upgrade project: The gateway originally deployed on Cisco C3560 was moved to the S9300 CSS system newly deployed on the network. The S9300 switches worked as aggregation switches and used CSS technology to improve network reliability. Cisco 3560 and Huawei S9300 ...
ppt
... Uses Link State algorithm LS packet dissemination Topology map at each node Route computation using Dijkstra’s algorithm OSPF advertisement carries one entry per neighbor ...
... Uses Link State algorithm LS packet dissemination Topology map at each node Route computation using Dijkstra’s algorithm OSPF advertisement carries one entry per neighbor ...
Empirical testing of the impact of different types of proximities on the
... • Border and even local effects have a strong impact on IP connectivity reflecting both cost constraints but also prospects for demand for local communications • Novelty of research: spatial and quantitative perspective on digital ...
... • Border and even local effects have a strong impact on IP connectivity reflecting both cost constraints but also prospects for demand for local communications • Novelty of research: spatial and quantitative perspective on digital ...
Symantec Software Datasheet
... connection. As with all corporate processes, policy serves as the basis for evaluations and actions. ...
... connection. As with all corporate processes, policy serves as the basis for evaluations and actions. ...
Use of a WDM network
... – 20% in case of ATM (TCP ACKs don’t fit in one ATM cell with LLC/SNAP encapsulation and ACKs are 45% of packets) – 4.4% for SONET relative to IP over PPP over fiber/WDM ...
... – 20% in case of ATM (TCP ACKs don’t fit in one ATM cell with LLC/SNAP encapsulation and ACKs are 45% of packets) – 4.4% for SONET relative to IP over PPP over fiber/WDM ...
No Slide Title - Ed Lazowska
... find the physical address on that network of a router that can get a packet one step closer to its destination Packet format physical address ...
... find the physical address on that network of a router that can get a packet one step closer to its destination Packet format physical address ...
Presentation Title Presentation Title Presentation Title
... • Use Bayesian probabilistic approach for mixing second hand information from neighboring nodes with directly observed information to calculate trust1 • Trust-based models usually involve high computational overhead, and building an efficient scheme for resource-constrained WSNs is a very challengin ...
... • Use Bayesian probabilistic approach for mixing second hand information from neighboring nodes with directly observed information to calculate trust1 • Trust-based models usually involve high computational overhead, and building an efficient scheme for resource-constrained WSNs is a very challengin ...
CCNA - Day 1 - UMT Admin Panel
... An extended star topology links individual stars together by connecting the hubs and/or switches.This topology can extend the scope and coverage of the network. ...
... An extended star topology links individual stars together by connecting the hubs and/or switches.This topology can extend the scope and coverage of the network. ...
Analysis of Attack - FSU Computer Science
... Involves the attacker gaining access to a host in the network and disconnecting it Attacker then inserts another machine with the same IP address, which will allow the attacker access to all information on the original system UDP and TCP don’t check the validity of an IP address which is why this at ...
... Involves the attacker gaining access to a host in the network and disconnecting it Attacker then inserts another machine with the same IP address, which will allow the attacker access to all information on the original system UDP and TCP don’t check the validity of an IP address which is why this at ...
Acceptable Use Policy for Technology
... not allow others to use their account or use the accounts of others, with or without the account owner’s authorization. ...
... not allow others to use their account or use the accounts of others, with or without the account owner’s authorization. ...
Efficient Clustering using ECATCH Algorithm to Extend
... emphasized in the literature [1]. Many routing protocols with many different ideas have been proposed in the literature to make the network energy efficient [14]. Cluster based routing protocol is one of these efficient ideas, where sensor nodes are divided into number of groups, each group is calle ...
... emphasized in the literature [1]. Many routing protocols with many different ideas have been proposed in the literature to make the network energy efficient [14]. Cluster based routing protocol is one of these efficient ideas, where sensor nodes are divided into number of groups, each group is calle ...
Connectivity representation in the LHCb Online
... • Type : data, trigger… • Status (functional or dead) Enough information to generate a routing table ...
... • Type : data, trigger… • Status (functional or dead) Enough information to generate a routing table ...
The network layer
... The main task of the application layer is to provide services for users. One way to satisfy these demands is to create different client-server application programs for each desired service. Programs such as file transfer programs (FTP and SMTP), and so on are already available. However, it would be ...
... The main task of the application layer is to provide services for users. One way to satisfy these demands is to create different client-server application programs for each desired service. Programs such as file transfer programs (FTP and SMTP), and so on are already available. However, it would be ...
Information Technology and Protection Considerations for E
... to them. Many such products offer the owner an option to key in the MAC addresses of their home equipment, that restricts the network to only allow connections from those devices. Do this, but also know that the feature is not so powerful as it may seem. Hackers and their software programs can fake ...
... to them. Many such products offer the owner an option to key in the MAC addresses of their home equipment, that restricts the network to only allow connections from those devices. Do this, but also know that the feature is not so powerful as it may seem. Hackers and their software programs can fake ...
Building a UTP networking cable and connecting two computers
... just mapped, in this case the other computer’s hard disk. Depending on the network and share permissions you can use this window just like it was a second hard disk on the compter you are on. You can get information from it and you can send information to it. It functions like a part of your compute ...
... just mapped, in this case the other computer’s hard disk. Depending on the network and share permissions you can use this window just like it was a second hard disk on the compter you are on. You can get information from it and you can send information to it. It functions like a part of your compute ...
Slide 1
... • Core gateways make up the Internet backbone • Network nodes – Allowed one default gateway • Assigned manually, automatically (DHCP) ...
... • Core gateways make up the Internet backbone • Network nodes – Allowed one default gateway • Assigned manually, automatically (DHCP) ...