PDF
... The Cisco® Gigabit Ethernet Dual-Identity Enhanced High-Speed WAN Interface Card (EHWIC) brings both Small Form-Factor Pluggable (SFP) and copper (RJ-45) Gigabit Ethernet connectivity to Cisco Integrated Services Routers (ISRs) to accelerate applications such as Ethernet WAN access, inter-VLAN routi ...
... The Cisco® Gigabit Ethernet Dual-Identity Enhanced High-Speed WAN Interface Card (EHWIC) brings both Small Form-Factor Pluggable (SFP) and copper (RJ-45) Gigabit Ethernet connectivity to Cisco Integrated Services Routers (ISRs) to accelerate applications such as Ethernet WAN access, inter-VLAN routi ...
NETGEAR Wireless-N Router WNR2000 User Manual , Inc.
... Logging In To Your Wireless Router ...............................................................................1-2 Selecting a Language for Your Screen Display ..............................................................1-5 Configuring Your Internet Connection Using the Smart Setup Wizard ..... ...
... Logging In To Your Wireless Router ...............................................................................1-2 Selecting a Language for Your Screen Display ..............................................................1-5 Configuring Your Internet Connection Using the Smart Setup Wizard ..... ...
PowerSum ELFEXT
... Because of the fact that the transmission speed is depending on the encoding technique, we do not use the term Mbps to compare cables to each other, but we use MHz which is the parameter expressing the bandwidth of the cable. ...
... Because of the fact that the transmission speed is depending on the encoding technique, we do not use the term Mbps to compare cables to each other, but we use MHz which is the parameter expressing the bandwidth of the cable. ...
Point-to-Point Protocol (PPP)
... The first phase of LCP operation is link establishment. This phase must complete successfully, before any Network layer packets can be exchanged. During link establishment, the LCP opens the connection and negotiates the configuration parameters. The link establishment process starts with the initia ...
... The first phase of LCP operation is link establishment. This phase must complete successfully, before any Network layer packets can be exchanged. During link establishment, the LCP opens the connection and negotiates the configuration parameters. The link establishment process starts with the initia ...
User Guide Verizon FiOS®Router Model 9100EM
... This equipment is designated to connect to the telephone network or premises wiring using a compatible modular jack that is Part 68 compliant. An FCC compliant telephone cord and modular plug is provided with the equipment. See the Installation Information section of this User Guide for details. A p ...
... This equipment is designated to connect to the telephone network or premises wiring using a compatible modular jack that is Part 68 compliant. An FCC compliant telephone cord and modular plug is provided with the equipment. See the Installation Information section of this User Guide for details. A p ...
TCP/IP Tutorial and Technical Overview
... This edition applies to Transmission Control Protocol/Internet Protocol (TCP/IP) in general and selected IBM and OEM implementations thereof. Comments may be addressed to: IBM Corporation, International Technical Support Organization Dept. HZ8 Building 678 P.O. Box 12195 Research Triangle Park, NC 2 ...
... This edition applies to Transmission Control Protocol/Internet Protocol (TCP/IP) in general and selected IBM and OEM implementations thereof. Comments may be addressed to: IBM Corporation, International Technical Support Organization Dept. HZ8 Building 678 P.O. Box 12195 Research Triangle Park, NC 2 ...
PDF - Complete Book (887.0 KB)
... via the public Internet without firewall restrictions, the Cisco AnyConnect VPN Client is not required. ...
... via the public Internet without firewall restrictions, the Cisco AnyConnect VPN Client is not required. ...
Guide DynaStar 1500 (DS1500-XFR) X.25 Frame Router
... Note: This equipment has been tested and found to comply with the limits for a Class A digital device, pursuant to part 15 of the FCC Rules. These limits are designed to provide reasonable protection against harmful interference when the equipment is operated in a commercial environment. This equipm ...
... Note: This equipment has been tested and found to comply with the limits for a Class A digital device, pursuant to part 15 of the FCC Rules. These limits are designed to provide reasonable protection against harmful interference when the equipment is operated in a commercial environment. This equipm ...
Computer Networks and Internets By Douglas E Comer
... 2 Explosive growth 3 Internet 4 Economic impact 5 Complexity 6 Abstractions and concepts 7 On-line resources ...
... 2 Explosive growth 3 Internet 4 Economic impact 5 Complexity 6 Abstractions and concepts 7 On-line resources ...
CIS 175 Lecture Notes
... 2 Explosive growth 3 Internet 4 Economic impact 5 Complexity 6 Abstractions and concepts 7 On-line resources ...
... 2 Explosive growth 3 Internet 4 Economic impact 5 Complexity 6 Abstractions and concepts 7 On-line resources ...
Cross-Domain and Cross-Layer Coarse Grained Quality of
... The increasingly popular Internet with a steadily growing user base, the resulting traffic load and its rising usage for time and loss critical services, such as voice over IP, video streaming and gaming, consists of about 30,000 interconnected service provider networks. Those interconnections are b ...
... The increasingly popular Internet with a steadily growing user base, the resulting traffic load and its rising usage for time and loss critical services, such as voice over IP, video streaming and gaming, consists of about 30,000 interconnected service provider networks. Those interconnections are b ...
Cisco WRVS4400N Wireless-N Gigabit Security Router
... The Wireless-N Gigabit Security Router can connect your local area network (LAN) or a group of PCs interconnected in your home or office to the Internet. You can use one public IP address from the ISP through WAN port and use the router’s Network Address Translation (NAT) technology to share this si ...
... The Wireless-N Gigabit Security Router can connect your local area network (LAN) or a group of PCs interconnected in your home or office to the Internet. You can use one public IP address from the ISP through WAN port and use the router’s Network Address Translation (NAT) technology to share this si ...
N600 Wireless Dual Band Router WNDR3400v2 User Manual
... The router lets you access your network from virtually anywhere within the operating range of your wireless network. However, the operating distance or range of your wireless connection can vary significantly depending on the physical placement of your router. For example, the thickness and number o ...
... The router lets you access your network from virtually anywhere within the operating range of your wireless network. However, the operating distance or range of your wireless connection can vary significantly depending on the physical placement of your router. For example, the thickness and number o ...
BROCADE NETIRON XMR 4000, 8000 16000, 32000
... Industry-leading performance for MPLS services, providing several service choices: IP over MPLS, MPLS over GRE Virtual Leased Line (VLL), Virtual Private LAN Service (VPLS), BGP/ MPLS VPN, Multi-VRF, and routing over VPLS High-performance, robust routing via Brocade Direct Routing for complete, dist ...
... Industry-leading performance for MPLS services, providing several service choices: IP over MPLS, MPLS over GRE Virtual Leased Line (VLL), Virtual Private LAN Service (VPLS), BGP/ MPLS VPN, Multi-VRF, and routing over VPLS High-performance, robust routing via Brocade Direct Routing for complete, dist ...
The Internet of TR-069 Things: One Exploit to
... - Close all open ports to the WAN , accept those which are required and monitored. - Read Misfortune Cookie FAQ at: http://mis.fortunecook.ie ...
... - Close all open ports to the WAN , accept those which are required and monitored. - Read Misfortune Cookie FAQ at: http://mis.fortunecook.ie ...
Cisco Application Control Engine and Cisco Nexus 7000 Series Integration White Paper
... As the IT landscape rapidly changes, cost reduction pressures, focus on time to market, and employee empowerment are leading enterprises and IT service providers to develop innovative strategies to address these challenges. In the past, environments that needed additional security and isolation requ ...
... As the IT landscape rapidly changes, cost reduction pressures, focus on time to market, and employee empowerment are leading enterprises and IT service providers to develop innovative strategies to address these challenges. In the past, environments that needed additional security and isolation requ ...
PRAISE FOR IP STORAGE NETWORKING: STRAIGHT
... Straight to the Core goes beyond technical descriptions to the business reasons and justifications for implementing a storage architecture.” —Doug Ingraham, Senior Manager of Product Management in Cisco's Storage Technology Group “As today's enterprise continues to become more data-intensive, custom ...
... Straight to the Core goes beyond technical descriptions to the business reasons and justifications for implementing a storage architecture.” —Doug Ingraham, Senior Manager of Product Management in Cisco's Storage Technology Group “As today's enterprise continues to become more data-intensive, custom ...
Cisco RV180/RV180W Administration Guide
... remote workers. The RV180W features multi-function operation allowing the device to function as a wireless router, bridge, or access point. Both products include 4-port Gigabit Ethernet LAN ports, a Gigabit Ethernet WAN port, and an intuitive browser-based device manager. ...
... remote workers. The RV180W features multi-function operation allowing the device to function as a wireless router, bridge, or access point. Both products include 4-port Gigabit Ethernet LAN ports, a Gigabit Ethernet WAN port, and an intuitive browser-based device manager. ...
ITU ngn-fg-book-2 http://Certificate.Moscow
... service level agreement (SLA) is a formal definition of the contractual relationship between service provider and its end user [14]. It specifies what the end user wants and what the supplier commits to provide. It defines the level for the quality of services provided, setting performance objective ...
... service level agreement (SLA) is a formal definition of the contractual relationship between service provider and its end user [14]. It specifies what the end user wants and what the supplier commits to provide. It defines the level for the quality of services provided, setting performance objective ...
TIA-1112
... Interworking between CS Networks Supporting ISUP and the IM CN Subsystem.................................................. 8 7.2.1 Services Performed by Network Entities in the Control Plane ..................................................................... 8 7.2.1.1 Services Performed by the SS7 ...
... Interworking between CS Networks Supporting ISUP and the IM CN Subsystem.................................................. 8 7.2.1 Services Performed by Network Entities in the Control Plane ..................................................................... 8 7.2.1.1 Services Performed by the SS7 ...
DVTel EA-201 Encoder User Manual
... locally (not through the network and change it using the Unified Configurator. If necessary, configure the LAN/WAN to support the EA-201 IP address. Note: If you plan to use an Administrative user name and password on the unit, you can use it only for Telnet and Web server access. You do not need th ...
... locally (not through the network and change it using the Unified Configurator. If necessary, configure the LAN/WAN to support the EA-201 IP address. Note: If you plan to use an Administrative user name and password on the unit, you can use it only for Telnet and Web server access. You do not need th ...
Supporting Differentiated Service Classes: Queue Scheduling
... different queue scheduling disciplines, each attempting to find the correct balance between complexity, control, and fairness. The queue scheduling disciplines supported by router vendors are implementation-specific, which means that there are no real industry standards. However, a vendor sometimes ...
... different queue scheduling disciplines, each attempting to find the correct balance between complexity, control, and fairness. The queue scheduling disciplines supported by router vendors are implementation-specific, which means that there are no real industry standards. However, a vendor sometimes ...
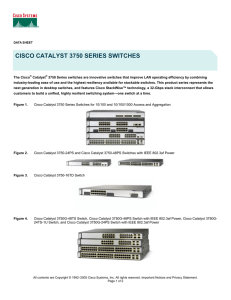
CISCO CATALYST 3750 SERIES SWITCHES
... • Cisco Express Forwarding hardware routing architecture delivers extremely high-performance IP routing. • Basic IP unicast routing protocols (static, Routing Information Protocol Version 1 [RIPv1], and RIPv2) are supported for small-network routing applications. • IPv6 routing support in hardware f ...
... • Cisco Express Forwarding hardware routing architecture delivers extremely high-performance IP routing. • Basic IP unicast routing protocols (static, Routing Information Protocol Version 1 [RIPv1], and RIPv2) are supported for small-network routing applications. • IPv6 routing support in hardware f ...
Cisco 1700 Series Modular Access Routers
... Preventing unauthorized users from entering the corporate network is an essential role of any security system. A network-based IDS provides around-the-clock network surveillance, analyzing packets and data streams and searching for signs of unauthorized activity. When it identifies unauthorized acti ...
... Preventing unauthorized users from entering the corporate network is an essential role of any security system. A network-based IDS provides around-the-clock network surveillance, analyzing packets and data streams and searching for signs of unauthorized activity. When it identifies unauthorized acti ...