A Software Development Kit to exploit RINA
... Unifies networking and distributed computing: the network is a distributed application that provides IPC • 3 There is a single type of layer with programmable functions, that repeats as many times as needed by the network designers • 4 All layers provide the same service: communication (flows) bet ...
... Unifies networking and distributed computing: the network is a distributed application that provides IPC • 3 There is a single type of layer with programmable functions, that repeats as many times as needed by the network designers • 4 All layers provide the same service: communication (flows) bet ...
OSPF
... –Commands used to modify bandwidth value • Bandwidth command – Example: Router(config-if)#bandwidthbandwidth-kbps ...
... –Commands used to modify bandwidth value • Bandwidth command – Example: Router(config-if)#bandwidthbandwidth-kbps ...
LAN Connection and IP Networks
... otherwise authorize in writing. Memotec Inc. reserves the right to make changes without notice in product or component design as warranted by evolution in user needs or progress in engineering or manufacturing technology. Changes which affect the operation of the unit will be documented in the next ...
... otherwise authorize in writing. Memotec Inc. reserves the right to make changes without notice in product or component design as warranted by evolution in user needs or progress in engineering or manufacturing technology. Changes which affect the operation of the unit will be documented in the next ...
DVB BlueBook A079
... IPDC DVB-T/H Bearer (data transmission baseband) and the IPDC DVB-T/H Network is expected to make available on the IPDC DVB-T/H Bearer. IP datagram stream: A stream of IPv6 or IPv4 datagrams each sharing the same IP source and destination address. An IP datagram stream is identified within an IP pla ...
... IPDC DVB-T/H Bearer (data transmission baseband) and the IPDC DVB-T/H Network is expected to make available on the IPDC DVB-T/H Bearer. IP datagram stream: A stream of IPv6 or IPv4 datagrams each sharing the same IP source and destination address. An IP datagram stream is identified within an IP pla ...
Wireless Design - Kenneth M. Chipps Ph.D. Home Page
... Capacity • Capacity is designed to support a large number of users using high bandwidth requirement applications such as voice and video • The focus for this type of design is a high density of access points, which can mean stacking access points physically on top of each other, to serve an area Co ...
... Capacity • Capacity is designed to support a large number of users using high bandwidth requirement applications such as voice and video • The focus for this type of design is a high density of access points, which can mean stacking access points physically on top of each other, to serve an area Co ...
Lab 11.6.1: Basic OSPF Configuration Lab (Instructor Version)
... All contents are Copyright © 1992–2007 Cisco Systems, Inc. All rights reserved. This document is Cisco Public Information. ...
... All contents are Copyright © 1992–2007 Cisco Systems, Inc. All rights reserved. This document is Cisco Public Information. ...
OS fingerprinting with IPv6
... those specific vulnerabilities and gain control over the system with little effort (Allen, ...
... those specific vulnerabilities and gain control over the system with little effort (Allen, ...
IPv6 and the Security of Your Network and Systems
... Your Users May Decide to “Informally” Try It… • Some sites which rely heavily on firewalls and perimeter security may decide to forego or postpone deployment of native IPv6. Having made the decision to do so, folks may emit a big relieved sigh, believing that by “sitting this dance out,” they will h ...
... Your Users May Decide to “Informally” Try It… • Some sites which rely heavily on firewalls and perimeter security may decide to forego or postpone deployment of native IPv6. Having made the decision to do so, folks may emit a big relieved sigh, believing that by “sitting this dance out,” they will h ...
Project Title Date Submitted
... Since M2M applications have a strong bias towards the uplink, and most of the uplink traffic is dedicated to provide non-realtime periodic monitoring report from remote sensors, the UL grants to huge number of M2M devices can be scheduled in a sequential manner to significantly reduce the chance of ...
... Since M2M applications have a strong bias towards the uplink, and most of the uplink traffic is dedicated to provide non-realtime periodic monitoring report from remote sensors, the UL grants to huge number of M2M devices can be scheduled in a sequential manner to significantly reduce the chance of ...
Putting BGP on the Right Path: Better Performance via Next-Hop Routing
... Today’s BGP provides network operators with very unsatisfactory means for handling data-plane performance issues and security threats, as reflected in poor network performance and in serious security breaches. We argue that such important objectives should be handled outside the routing protocol [12 ...
... Today’s BGP provides network operators with very unsatisfactory means for handling data-plane performance issues and security threats, as reflected in poor network performance and in serious security breaches. We argue that such important objectives should be handled outside the routing protocol [12 ...
Summit Installation and User Guide
... SUMMIT SWITCH MODELS The Summit family of switches is comprised of six models, as follows: • Summit1 • Summit2 • Summit3 • Summit4 • Summit4/FX • Summit48 ...
... SUMMIT SWITCH MODELS The Summit family of switches is comprised of six models, as follows: • Summit1 • Summit2 • Summit3 • Summit4 • Summit4/FX • Summit48 ...
6rd - Enabling IPv6 Customers on an IPv4
... RG need to get an IPv4 address first, from SP assignment RG will generate IPv6 prefix from 6rd prefix and ipv4 address RG configured exactly as for any native IPv6 connectivity to LAN side SLACC or DHCPv6 LAN station use ipv6 prefix to generate ipv6 address. Most browsers will prefer ...
... RG need to get an IPv4 address first, from SP assignment RG will generate IPv6 prefix from 6rd prefix and ipv4 address RG configured exactly as for any native IPv6 connectivity to LAN side SLACC or DHCPv6 LAN station use ipv6 prefix to generate ipv6 address. Most browsers will prefer ...
Cisco IP SLA`s
... • Threshold notifications when end point is not available What is the availability of a Network File System (NFS) server used to store business critical data from a remote site ? ...
... • Threshold notifications when end point is not available What is the availability of a Network File System (NFS) server used to store business critical data from a remote site ? ...
Ingate Firewall & SIParator Training
... 10 Years in SIP Protocol Audience – Show of Hands How many of you are familiar with the SIP Protocol? How many of you own an Ingate? Are you planning to buy an Ingate in the near future? Are you concerned about SIP Interop? Are you concerned about SIP Security? ...
... 10 Years in SIP Protocol Audience – Show of Hands How many of you are familiar with the SIP Protocol? How many of you own an Ingate? Are you planning to buy an Ingate in the near future? Are you concerned about SIP Interop? Are you concerned about SIP Security? ...
SnapGear Administration Guide Firmware Version 3.1.5
... Software Product, including all computer programs and documentation, and erasing any copies residing on computer equipment. This Agreement also will automatically terminate if you do not comply with any terms or conditions of this Agreement. Upon such termination you agree to destroy the Software Pr ...
... Software Product, including all computer programs and documentation, and erasing any copies residing on computer equipment. This Agreement also will automatically terminate if you do not comply with any terms or conditions of this Agreement. Upon such termination you agree to destroy the Software Pr ...
PDF-p. 30
... IPRs essential or potentially essential to the present document may have been declared to ETSI. The information pertaining to these essential IPRs, if any, is publicly available for ETSI members and non-members, and can be found in ETSI SR 000 314: "Intellectual Property Rights (IPRs); Essential, or ...
... IPRs essential or potentially essential to the present document may have been declared to ETSI. The information pertaining to these essential IPRs, if any, is publicly available for ETSI members and non-members, and can be found in ETSI SR 000 314: "Intellectual Property Rights (IPRs); Essential, or ...
Netvisor nvOS Configuration Guide
... This publication is for experienced network administrators responsible for configuring and maintaining Pluribus Networks switches with some expertise in the following areas: ...
... This publication is for experienced network administrators responsible for configuring and maintaining Pluribus Networks switches with some expertise in the following areas: ...
Model FVL328 ProSafe High-Speed VPN Firewall Reference
... It is hereby certified that the FVL328 Prosafe High Speed VPN Firewall has been suppressed in accordance with the conditions set out in the BMPT-AmtsblVfg 243/1991 and Vfg 46/1992. The operation of some equipment (for example, test transmitters) in accordance with the regulations may, however, be su ...
... It is hereby certified that the FVL328 Prosafe High Speed VPN Firewall has been suppressed in accordance with the conditions set out in the BMPT-AmtsblVfg 243/1991 and Vfg 46/1992. The operation of some equipment (for example, test transmitters) in accordance with the regulations may, however, be su ...
Compatible Systems Reference Guides
... Introduction The default passwords as shipped from the factory are letmein. It is strongly recommended that the password be changed using the [ General ] section. Once the passwords are set, the same passwords are used by CompatiView. Modes of Operation There are two modes of operation in the Comma ...
... Introduction The default passwords as shipped from the factory are letmein. It is strongly recommended that the password be changed using the [ General ] section. Once the passwords are set, the same passwords are used by CompatiView. Modes of Operation There are two modes of operation in the Comma ...
NGN_internship
... direction of the future-however when looking at a future PSTN scale solution service providers must ensure that the following key requirements are met to provide equivalence with the PSTN: ...
... direction of the future-however when looking at a future PSTN scale solution service providers must ensure that the following key requirements are met to provide equivalence with the PSTN: ...
Application Notes for HP ProCurve Networking Switches connected
... QoS testing verified that when the ProCurve Switch interfaces are over subscribed with low priority data traffic, the higher priority VoIP media, signaling and SCN traffic still got through the over subscribed LAN interfaces. Prioritization of voice traffic was achieved by implementing Layer 3 DiffS ...
... QoS testing verified that when the ProCurve Switch interfaces are over subscribed with low priority data traffic, the higher priority VoIP media, signaling and SCN traffic still got through the over subscribed LAN interfaces. Prioritization of voice traffic was achieved by implementing Layer 3 DiffS ...
Объединенный институт ядерных исследов
... The protocol between CERN, Russia and JINR on participation in LCG Project was approved in 2003. MoU on Worldwide LHC Computing Grid (WLCG) was signed by JINR in October 2007 The tasks of the JINR in the WLCG: •WLCG-infrastructure support and development at JINR; • participation in WLCG middleware t ...
... The protocol between CERN, Russia and JINR on participation in LCG Project was approved in 2003. MoU on Worldwide LHC Computing Grid (WLCG) was signed by JINR in October 2007 The tasks of the JINR in the WLCG: •WLCG-infrastructure support and development at JINR; • participation in WLCG middleware t ...
IEEE C802.16m-09/1156 Project Title
... IEEE C802.16m-09/1156 During HO preparation phase, the target ABS may allocate a dedicated ranging code or opportunity to the AMS via the serving ABS through the AAI_HO-CMD message. The target ABS shall select the dedicated ranging code from the group of codes which are allocated for handover purpo ...
... IEEE C802.16m-09/1156 During HO preparation phase, the target ABS may allocate a dedicated ranging code or opportunity to the AMS via the serving ABS through the AAI_HO-CMD message. The target ABS shall select the dedicated ranging code from the group of codes which are allocated for handover purpo ...
Single Packet IP Traceback in AS-level Partial Deployment Scenario
... reconstructed, it sends queries to its level-2 SPIE-deployed AS neighbors (2-hop away from the current AS), and so on. This process continues until the STM gets the origin of attack packet or it cannot trace anymore. The number of the levels to which the STM can dispatch queries depends on the imple ...
... reconstructed, it sends queries to its level-2 SPIE-deployed AS neighbors (2-hop away from the current AS), and so on. This process continues until the STM gets the origin of attack packet or it cannot trace anymore. The number of the levels to which the STM can dispatch queries depends on the imple ...
Cloud and Network Services
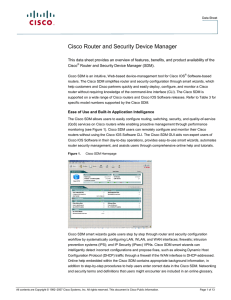
... When deploying a new router, Cisco SDM users can configure a Cisco IOS Software firewall quickly and using the best practices recommended by the International Computer Security Association (ICSA) and the Cisco Technical Assistance Center (TAC). An advanced firewall wizard allows a single-step deploy ...
... When deploying a new router, Cisco SDM users can configure a Cisco IOS Software firewall quickly and using the best practices recommended by the International Computer Security Association (ICSA) and the Cisco Technical Assistance Center (TAC). An advanced firewall wizard allows a single-step deploy ...