NAVAL POSTGRADUATE SCHOOL
... configuration files is difficult and even impossible in some cases where the network has a large number of concurrently running routing processes distributed over many routers and variable network delays make the interactions between these processes too complex to understand exactly. This research t ...
... configuration files is difficult and even impossible in some cases where the network has a large number of concurrently running routing processes distributed over many routers and variable network delays make the interactions between these processes too complex to understand exactly. This research t ...
12.4 was released in May of 2005
... • Used for inline intrusion prevention and event notification • Dynamically loads attack signatures to the router • Integrates technology from Cisco IDS Sensor families Cisco IDS 4200 Series Appliances, Cisco Catalyst® 6500 IDS Module, Network Module IDS appliance (NM-CIDS) ...
... • Used for inline intrusion prevention and event notification • Dynamically loads attack signatures to the router • Integrates technology from Cisco IDS Sensor families Cisco IDS 4200 Series Appliances, Cisco Catalyst® 6500 IDS Module, Network Module IDS appliance (NM-CIDS) ...
Animation - Cisco Communities
... In 6.2(2); VLAN translation allows OTV to map a local VLAN (in DC 1) to a remote VLAN (in DC 2). In previous NX-OS releases, the extended VLANs had to be identical in each site (ie. X to X). With the VLAN mapping feature, VLANs can be translated, so they can be different in each site (ie. X to Y to ...
... In 6.2(2); VLAN translation allows OTV to map a local VLAN (in DC 1) to a remote VLAN (in DC 2). In previous NX-OS releases, the extended VLANs had to be identical in each site (ie. X to X). With the VLAN mapping feature, VLANs can be translated, so they can be different in each site (ie. X to Y to ...
Paper Title (use style: paper title)
... Currently, multicast scoping technique uses either the “Time To Live” field in the IPv4 packet header or the scope field in case of IPv6. In IPv6, the scope filed is an integrated part of the multicast address itself. The IETF has particularly defined guidelines that explain how to assign and alloca ...
... Currently, multicast scoping technique uses either the “Time To Live” field in the IPv4 packet header or the scope field in case of IPv6. In IPv6, the scope filed is an integrated part of the multicast address itself. The IETF has particularly defined guidelines that explain how to assign and alloca ...
Avaya Session Border Controller for Enterprise
... Avaya is not responsible for the contents or reliability of any linked websites referenced within this site or documentation provided by Avaya. Avaya is not responsible for the accuracy of any information, statement or content provided on these sites and does not necessarily endorse the products, se ...
... Avaya is not responsible for the contents or reliability of any linked websites referenced within this site or documentation provided by Avaya. Avaya is not responsible for the accuracy of any information, statement or content provided on these sites and does not necessarily endorse the products, se ...
Cisco ASR 5x00 Packet Data Serving Node Administration Guide Version 15.0
... Cisco and the Cisco Logo are trademarks of Cisco Systems, Inc. and/or its affiliates in the U.S. and other countries. A listing of Cisco's trademarks can be found at www.cisco.com/go/trademarks. Third party trademarks mentioned are the property of their respective owners. The use of the word partner ...
... Cisco and the Cisco Logo are trademarks of Cisco Systems, Inc. and/or its affiliates in the U.S. and other countries. A listing of Cisco's trademarks can be found at www.cisco.com/go/trademarks. Third party trademarks mentioned are the property of their respective owners. The use of the word partner ...
NWare Device Reference - Peavey Digital Research
... shown on the display at the back of the unit. ...
... shown on the display at the back of the unit. ...
TCP/IP Network Administration - U
... ABORT keyword : A.3. chat Abstract Syntax Notation One (ASN.1) : 11.9. Simple Network Management Protocol access control : 12.5. Access Control levels of : 9.1.2.1. The share command services to place under, listed : 12.5.1. wrapper software for : 12.5. Access Control ACKD command, in POP : 3.4.2. P ...
... ABORT keyword : A.3. chat Abstract Syntax Notation One (ASN.1) : 11.9. Simple Network Management Protocol access control : 12.5. Access Control levels of : 9.1.2.1. The share command services to place under, listed : 12.5.1. wrapper software for : 12.5. Access Control ACKD command, in POP : 3.4.2. P ...
PDF
... reliable performance of a managed network. Because some devices have a limited ability to run management software, most of the computer processing burden is assumed by the NMS. The NMS runs the network management applications, such as Fabric Manager, that present management information to network ma ...
... reliable performance of a managed network. Because some devices have a limited ability to run management software, most of the computer processing burden is assumed by the NMS. The NMS runs the network management applications, such as Fabric Manager, that present management information to network ma ...
Command Line Interface Guide
... How This Guide is Organized This guide is intended to help you configure and manage the router using the Command Line Interface. The guide assumes that you have read the information about the router and installed the hardware using the Internet Quick Start Guide. The guide is divided into eight part ...
... How This Guide is Organized This guide is intended to help you configure and manage the router using the Command Line Interface. The guide assumes that you have read the information about the router and installed the hardware using the Internet Quick Start Guide. The guide is divided into eight part ...
Cisco Wide Area Application Services Software Version 5.4
... application delivery even more. The challenges of data-retention policies and business-continuance, disasterrecovery, and compliance requirements exacerbate the problem, given a heavily distributed infrastructure and already overburdened WAN environment. A centralized IT infrastructure allows CapEx ...
... application delivery even more. The challenges of data-retention policies and business-continuance, disasterrecovery, and compliance requirements exacerbate the problem, given a heavily distributed infrastructure and already overburdened WAN environment. A centralized IT infrastructure allows CapEx ...
PDF - Complete Book (1.66 MB)
... The Cisco BTS 10200 Softswitch is a software-based, class-independent network switch. It provides call-control intelligence for establishing, maintaining, routing, and terminating voice calls on media gateways (MGWs) in the packet network, while seamlessly operating with legacy circuit-switched netw ...
... The Cisco BTS 10200 Softswitch is a software-based, class-independent network switch. It provides call-control intelligence for establishing, maintaining, routing, and terminating voice calls on media gateways (MGWs) in the packet network, while seamlessly operating with legacy circuit-switched netw ...
Commissioning Guide
... This document is a guide to NE80E/40E commissioning and verification. It describes how to commission hardware, links, services, and maintenance and management during deployment, ensuring stable and reliable operation of NE80E/40Es on networks. The intended audience of this document includes installa ...
... This document is a guide to NE80E/40E commissioning and verification. It describes how to commission hardware, links, services, and maintenance and management during deployment, ensuring stable and reliable operation of NE80E/40Es on networks. The intended audience of this document includes installa ...
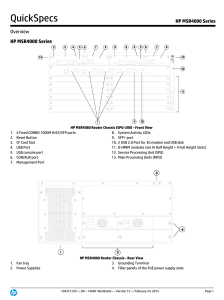
HP MSR4000 Series
... acts as a part of the management and backup function to provide backup for device interfaces; delivers reliability by switching traffic over to a backup interface when the primary one fails Virtual Router Redundancy Protocol (VRRP) allows groups of two routers to dynamically back each other up to cr ...
... acts as a part of the management and backup function to provide backup for device interfaces; delivers reliability by switching traffic over to a backup interface when the primary one fails Virtual Router Redundancy Protocol (VRRP) allows groups of two routers to dynamically back each other up to cr ...
8 Security
... The present document has been developed within the 3rd Generation Partnership Project (3GPP TM) and may be further elaborated for the purposes of 3GPP. The present document has not been subject to any approval process by the 3GPP Organisational Partners and shall not be implemented. This Specificati ...
... The present document has been developed within the 3rd Generation Partnership Project (3GPP TM) and may be further elaborated for the purposes of 3GPP. The present document has not been subject to any approval process by the 3GPP Organisational Partners and shall not be implemented. This Specificati ...
ROUTE Chapter 3
... the router will wait to receive a Hello packet before declaring the neighbor "down." • If the Dead interval expires before the routers receive a Hello packet, OSPF will remove that neighbor from its link-state database. • The router floods the link-state information about the "down" neighbor out all ...
... the router will wait to receive a Hello packet before declaring the neighbor "down." • If the Dead interval expires before the routers receive a Hello packet, OSPF will remove that neighbor from its link-state database. • The router floods the link-state information about the "down" neighbor out all ...
profesores.usfq.edu.ec
... the router will wait to receive a Hello packet before declaring the neighbor "down." • If the Dead interval expires before the routers receive a Hello packet, OSPF will remove that neighbor from its link-state database. • The router floods the link-state information about the "down" neighbor out all ...
... the router will wait to receive a Hello packet before declaring the neighbor "down." • If the Dead interval expires before the routers receive a Hello packet, OSPF will remove that neighbor from its link-state database. • The router floods the link-state information about the "down" neighbor out all ...
SAN Design Reference Guide
... paths to connect servers and storage systems. To take full advantage of its capabilities, the SAN is maintained separately from parallel general-purpose networks. The network topology is the physical arrangement of interconnected hardware components. In a basic topology, a Fibre Channel switch inter ...
... paths to connect servers and storage systems. To take full advantage of its capabilities, the SAN is maintained separately from parallel general-purpose networks. The network topology is the physical arrangement of interconnected hardware components. In a basic topology, a Fibre Channel switch inter ...
TS 133 107
... print versions of the present document shall not be modified without the prior written authorization of ETSI. In case of any existing or perceived difference in contents between such versions and/or in print, the only prevailing document is the print of the Portable Document Format (PDF) version kep ...
... print versions of the present document shall not be modified without the prior written authorization of ETSI. In case of any existing or perceived difference in contents between such versions and/or in print, the only prevailing document is the print of the Portable Document Format (PDF) version kep ...
Palo Alto Networks Administrator’s Guide Release 5.0
... Configuring Layer 2 Interfaces. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . Configuring Layer 2 Subinterfaces. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . Configuring Layer 3 Interfaces. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . Con ...
... Configuring Layer 2 Interfaces. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . Configuring Layer 2 Subinterfaces. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . Configuring Layer 3 Interfaces. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . Con ...
Small Network Equipment 2015 Annual Report
... Under the Voluntary Agreement, at least 90% of all small network equipment purchased by service providers or sold by manufacturers at retail after December 31, 2015 must meet the energy efficiency standards established under the Voluntary Agreement. Early implementation has resulted in 89.6% of serv ...
... Under the Voluntary Agreement, at least 90% of all small network equipment purchased by service providers or sold by manufacturers at retail after December 31, 2015 must meet the energy efficiency standards established under the Voluntary Agreement. Early implementation has resulted in 89.6% of serv ...
IPv6 Primer
... between hosts on a LAN, VLAN or WAN Requires a 6to4 gateway for packets to leave the local LAN ...
... between hosts on a LAN, VLAN or WAN Requires a 6to4 gateway for packets to leave the local LAN ...
PDF
... Cisco 4G LTE NIMs needs an active SIM card provided by a service provider. The SIM cards are usually provided in an unlocked state so that it can be used without a Personal Identification Number (PIN). If the SIM is unlocked, it can be inserted into a 4G LTE NIM and used ...
... Cisco 4G LTE NIMs needs an active SIM card provided by a service provider. The SIM cards are usually provided in an unlocked state so that it can be used without a Personal Identification Number (PIN). If the SIM is unlocked, it can be inserted into a 4G LTE NIM and used ...
PacketStar PSAX Simple Network Management Protocol (SNMP
... traps associated with the PSAX Multiservice Media Gateways system software Release 9.0.0. All available possible causes and corrective actions for the console interface are also provided for these trap messages. For descriptions of each MIB object associated with the trap names, see Chapter 4. Table ...
... traps associated with the PSAX Multiservice Media Gateways system software Release 9.0.0. All available possible causes and corrective actions for the console interface are also provided for these trap messages. For descriptions of each MIB object associated with the trap names, see Chapter 4. Table ...