IP Datagram - La Salle University
... Reassembly uses the sequence numbers and the offsets to rebuild the datagram. IP does not guarantee datagram delivery. If part of a fragment is received, the destination sets a timer to receive the other pieces. If all fragments are not received within the time period, the destination can request a ...
... Reassembly uses the sequence numbers and the offsets to rebuild the datagram. IP does not guarantee datagram delivery. If part of a fragment is received, the destination sets a timer to receive the other pieces. If all fragments are not received within the time period, the destination can request a ...
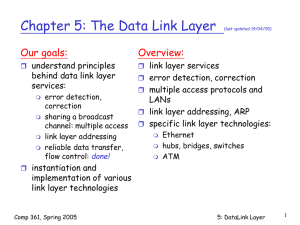
Chapter 5 outline
... Random Access Protocols When node has packet to send transmit at full channel data rate R. no a priori coordination among nodes two or more transmitting nodes -> “collision”, random access MAC protocol specifies: how to detect collisions how to recover from collisions (e.g., via delay ...
... Random Access Protocols When node has packet to send transmit at full channel data rate R. no a priori coordination among nodes two or more transmitting nodes -> “collision”, random access MAC protocol specifies: how to detect collisions how to recover from collisions (e.g., via delay ...
Ayodele Damola
... sharing content such as video, audio, and software. The traffic generated by these applications represents a large proportion of Internet traffic. For the broadband access network providers P2P traffic presents several problems. This thesis identifies the performance and business issues that P2P tra ...
... sharing content such as video, audio, and software. The traffic generated by these applications represents a large proportion of Internet traffic. For the broadband access network providers P2P traffic presents several problems. This thesis identifies the performance and business issues that P2P tra ...
chapter5
... Two types of “links”: point-to-point PPP for dial-up access point-to-point link between Ethernet switch and host broadcast (shared wire or medium) traditional Ethernet upstream HFC 802.11 wireless LAN ...
... Two types of “links”: point-to-point PPP for dial-up access point-to-point link between Ethernet switch and host broadcast (shared wire or medium) traditional Ethernet upstream HFC 802.11 wireless LAN ...
mpls
... In MPLS Domain, all the traffic in a set of FECs might follow the same route. Example – a set of distinct address prefixes might all have the same egress node. In such case, the union of those FECs it itself a FEC. The procedure of binding a single label to a union of FECs which is itself a FEC, and ...
... In MPLS Domain, all the traffic in a set of FECs might follow the same route. Example – a set of distinct address prefixes might all have the same egress node. In such case, the union of those FECs it itself a FEC. The procedure of binding a single label to a union of FECs which is itself a FEC, and ...
Address Resolution Protocol
... In order for devices to be able to communicate with each when they are not part of the same network, the 48-bit MAC address must be mapped to an IP address. Some of the Layer 3 protocols used to perform the mapping are: • Address Resolution Protocol (ARP) • Reverse ARP (RARP) • Serial Line ARP (SLAR ...
... In order for devices to be able to communicate with each when they are not part of the same network, the 48-bit MAC address must be mapped to an IP address. Some of the Layer 3 protocols used to perform the mapping are: • Address Resolution Protocol (ARP) • Reverse ARP (RARP) • Serial Line ARP (SLAR ...
module10b
... router Donna and Nancy, and between router Donna and Susan. For each segment there will be a DR/BDR election. You can see that router Nancy is the DR for the 192.168.12.0/24 segment and router Susan is the DR for the 192.168.23.0/24 segment. ...
... router Donna and Nancy, and between router Donna and Susan. For each segment there will be a DR/BDR election. You can see that router Nancy is the DR for the 192.168.12.0/24 segment and router Susan is the DR for the 192.168.23.0/24 segment. ...
Chapter 5 outline
... Random Access Protocols When node has packet to send transmit at full channel data rate R. no a priori coordination among nodes two or more transmitting nodes -> “collision”, random access MAC protocol specifies: how to detect collisions how to recover from collisions (e.g., via delay ...
... Random Access Protocols When node has packet to send transmit at full channel data rate R. no a priori coordination among nodes two or more transmitting nodes -> “collision”, random access MAC protocol specifies: how to detect collisions how to recover from collisions (e.g., via delay ...
Powerpoint
... neighbor external password 7 020A0559 neighbor external maximum-prefix 220000 [warning-only] neighbor 10.200.0.1 peer-group external ...
... neighbor external password 7 020A0559 neighbor external maximum-prefix 220000 [warning-only] neighbor 10.200.0.1 peer-group external ...
Chapter 5
... Random Access Protocols When node has packet to send transmit at full channel data rate R. no a priori coordination among nodes two or more transmitting nodes -> “collision”, random access MAC protocol specifies: how to detect collisions how to recover from collisions (e.g., via delay ...
... Random Access Protocols When node has packet to send transmit at full channel data rate R. no a priori coordination among nodes two or more transmitting nodes -> “collision”, random access MAC protocol specifies: how to detect collisions how to recover from collisions (e.g., via delay ...
ip-shiv2004-routing-I
... Bridges therefore have “L2 forwarding tables,” and use dynamic learning algorithms to build it locally. Even this allows LANs to scale, by limiting broadcasts and collisions to collision domains, and using bridges to interconnect collision domains. The learning algorithm is purely local, oppor ...
... Bridges therefore have “L2 forwarding tables,” and use dynamic learning algorithms to build it locally. Even this allows LANs to scale, by limiting broadcasts and collisions to collision domains, and using bridges to interconnect collision domains. The learning algorithm is purely local, oppor ...
Introduction Chapter 1
... (using compression techniques). These data transfers typically generate bursty traffic, have delay and jitter constraints, and endure for long sessions. For these applications the use of CO packet-switched networks are ideal because bandwidth is not wasted between bursts of data, which will occur wh ...
... (using compression techniques). These data transfers typically generate bursty traffic, have delay and jitter constraints, and endure for long sessions. For these applications the use of CO packet-switched networks are ideal because bandwidth is not wasted between bursts of data, which will occur wh ...
CCNA 1 - Cisco
... CCNA v3.1 to CCNA Discovery or CCNA Exploration Student Migration Guidelines Student migration guidelines offer flexibility to assist moving to the new, improved curricula No direct mapping exists between CCNA v3.1 and CCNA Discovery or CCNA Exploration ...
... CCNA v3.1 to CCNA Discovery or CCNA Exploration Student Migration Guidelines Student migration guidelines offer flexibility to assist moving to the new, improved curricula No direct mapping exists between CCNA v3.1 and CCNA Discovery or CCNA Exploration ...
of disk - EECS Instructional Support Group Home Page
... • Key to protocol families is that communication occurs logically at the same level of the protocol, called peer-topeer… …but is implemented via services at the next lower level • Encapsulation: carry higher level information within lower level “envelope” ...
... • Key to protocol families is that communication occurs logically at the same level of the protocol, called peer-topeer… …but is implemented via services at the next lower level • Encapsulation: carry higher level information within lower level “envelope” ...
csci5211: Computer Networks and Data Communications
... • Current scheme employs active probing for available bandwidth – Simple heuristics to eliminate unnecessary probes – Focus of our current research winter 2008 ...
... • Current scheme employs active probing for available bandwidth – Simple heuristics to eliminate unnecessary probes – Focus of our current research winter 2008 ...
Exploration CCNA4 - Information Systems Technology
... Virtual Circuits The connection through a Frame Relay network between two DTEs is called a virtual circuit (VC). –The circuits are virtual because there is no direct electrical connection from end to end. –With VCs, any single site can communicate with any other single site without using multiple ...
... Virtual Circuits The connection through a Frame Relay network between two DTEs is called a virtual circuit (VC). –The circuits are virtual because there is no direct electrical connection from end to end. –With VCs, any single site can communicate with any other single site without using multiple ...
hp-storage- sales - training
... Protect and optimize your investment – HP ProLiant server hardware supports iLO2 remote management, HP SIM, and HP PSP – Industry-standard building blocks: Intel processors, SATA/SAS drives, and SAS interconnects – It’s Windows, so it integrates seamlessly into your existing Windows environment, run ...
... Protect and optimize your investment – HP ProLiant server hardware supports iLO2 remote management, HP SIM, and HP PSP – Industry-standard building blocks: Intel processors, SATA/SAS drives, and SAS interconnects – It’s Windows, so it integrates seamlessly into your existing Windows environment, run ...
... • Technology design guides provide deployment details, information about validated products and software, and best practices for specific types of technology. • Solution design guides integrate or reference existing CVDs, but also include product features and functionality across Cisco products an ...
Layer 3 - Ohio Supercomputer Center
... Terminology: Internet Architecture Stack Layer 4 Layer 4 End-Application Layer ...
... Terminology: Internet Architecture Stack Layer 4 Layer 4 End-Application Layer ...
PDF
... advertises its own capabilities. If the connected device also supports autonegotiation, Cisco SM-X Layer 2/3 ESM port negotiates the best connection (that is, the fastest line speed that both devices support and full-duplex transmission if the attached device supports it) and configures itself accor ...
... advertises its own capabilities. If the connected device also supports autonegotiation, Cisco SM-X Layer 2/3 ESM port negotiates the best connection (that is, the fastest line speed that both devices support and full-duplex transmission if the attached device supports it) and configures itself accor ...
Comtech CDM 570/570L Vipersat
... Comtech reserves the right to revise this publication at any time without obligation to provide notification of such revision. Comtech periodically revises and improves its products and, therefore, the information in this document is subject to change without prior notice. Comtech makes no warranty ...
... Comtech reserves the right to revise this publication at any time without obligation to provide notification of such revision. Comtech periodically revises and improves its products and, therefore, the information in this document is subject to change without prior notice. Comtech makes no warranty ...
P.DG A4001N User Manual
... up to 8 Mbps downstream and 1 Mbps upstream. G.lite (or splitterless) ADSL provides up to 1.5 Mbps downstream and 512 kbps upstream. However, you should note that the actual rate provided by specific service providers may vary dramatically from these upper limits. Data passing between devices connec ...
... up to 8 Mbps downstream and 1 Mbps upstream. G.lite (or splitterless) ADSL provides up to 1.5 Mbps downstream and 512 kbps upstream. However, you should note that the actual rate provided by specific service providers may vary dramatically from these upper limits. Data passing between devices connec ...
Customizable virtual private network service with QoS
... VANESA. The idea here is similar to the concept of a software toolkit for deploying virtual networks as described in [13] by Ferrari and Delgrossi. VANESA provides a simple interface for the network administrator to con®gure VPN properties such as the virtual topology, bandwidth requirements of virt ...
... VANESA. The idea here is similar to the concept of a software toolkit for deploying virtual networks as described in [13] by Ferrari and Delgrossi. VANESA provides a simple interface for the network administrator to con®gure VPN properties such as the virtual topology, bandwidth requirements of virt ...
Phillipe Lemonnier`s presentation
... Technologies used for IP transport (OSI level 2) don’t lose bits : they ...
... Technologies used for IP transport (OSI level 2) don’t lose bits : they ...