Ethernet Switches
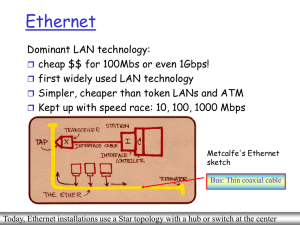
... in shared mode, CSMA/CD is used; short distances between nodes to be efficient uses Star topology with hub, called here ''Buffered Distributor'‘ or switch at center Full-Duplex at 1 Gbps for point-to-point links Serves as a backbone for interconnecting multiple 10Mbps, 100 Mbps Ethernet LANs ...
... in shared mode, CSMA/CD is used; short distances between nodes to be efficient uses Star topology with hub, called here ''Buffered Distributor'‘ or switch at center Full-Duplex at 1 Gbps for point-to-point links Serves as a backbone for interconnecting multiple 10Mbps, 100 Mbps Ethernet LANs ...
Firewall Labs
... bases decrease performance. And because packet filters can only check low-level ...
... bases decrease performance. And because packet filters can only check low-level ...
Performance Enhancement of TFRC in Wireless Networks
... Spec says can use four separate twisted pairs of Cat 3 UTP (now Cat 5e). Utilize three pair in both directions (at 33 1/3 Mbps) with other pair for carrier sense/collision detection. Three-level ternary code is used 8B/6T:: Prior to transmission each set of 8 bits is converted into 6 ternary symbols ...
... Spec says can use four separate twisted pairs of Cat 3 UTP (now Cat 5e). Utilize three pair in both directions (at 33 1/3 Mbps) with other pair for carrier sense/collision detection. Three-level ternary code is used 8B/6T:: Prior to transmission each set of 8 bits is converted into 6 ternary symbols ...
LN_ch07_Networking_Unix_Linux[2]ch14
... • Developed during 70's. 1st public data network interface between public packet-switched networks and customers. Data packet has a 3-byte header a 12 bit connection #, a packet sequence #, an acknowledgment # etc. and up to 126 bytes of data ...
... • Developed during 70's. 1st public data network interface between public packet-switched networks and customers. Data packet has a 3-byte header a 12 bit connection #, a packet sequence #, an acknowledgment # etc. and up to 126 bytes of data ...
Document
... synaptic weights of the network should be updated only if the absolute error on the training sample currently being processed by the network is greater than some prescribed criterion; ...
... synaptic weights of the network should be updated only if the absolute error on the training sample currently being processed by the network is greater than some prescribed criterion; ...
Accurate Real-time Identification of IP Prefix
... AS from originating a prefix it does not own. The Listen and Whisper scheme [46] also helps identify inconsistent routing advertisement, but does not deterministically detect IP hijacking attacks. Similar to our approach, it takes advantage of data plane information. Complimentary to our techniques, ...
... AS from originating a prefix it does not own. The Listen and Whisper scheme [46] also helps identify inconsistent routing advertisement, but does not deterministically detect IP hijacking attacks. Similar to our approach, it takes advantage of data plane information. Complimentary to our techniques, ...
ATCP: TCP for Mobile Ad Hoc Networks
... chines deployed in an ad hoc network will have ATCP installed. Thus, machines with or without ATCP should be able to set up normal TCP connections with machines that may or may not have ATCP. Furthermore, applications running at machines with ATCP should not be aware of ATCP's presence. Functioning ...
... chines deployed in an ad hoc network will have ATCP installed. Thus, machines with or without ATCP should be able to set up normal TCP connections with machines that may or may not have ATCP. Furthermore, applications running at machines with ATCP should not be aware of ATCP's presence. Functioning ...
Chapter 11 Interior Routing Protocols
... • Node maintains vector of link costs for each directly attached network and distance and next-hop vectors for each destination • Used by Routing Information Protocol (RIP) • Requires transmission of lots of information by each router — Distance vector to all neighbors — Contains estimated path cost ...
... • Node maintains vector of link costs for each directly attached network and distance and next-hop vectors for each destination • Used by Routing Information Protocol (RIP) • Requires transmission of lots of information by each router — Distance vector to all neighbors — Contains estimated path cost ...
Explain the Role of VLANs in a Converged Network
... © 2006 Cisco Systems, Inc. All rights reserved. ...
... © 2006 Cisco Systems, Inc. All rights reserved. ...
Emerging_Wireless_Standards2
... improvements in reliability, comparable to increasing the transmit power by a factor of ...
... improvements in reliability, comparable to increasing the transmit power by a factor of ...
IP Datagram Header - California State University, Long Beach
... FLAGS -- 3-bit field with individual bits specifying whether the datagram is a fragment FRAGMENT OFFSET -- 13-bit field that specifies where in the original datagram the data in this fragment belongs (the value of the field is multiplied by 8 to obtain an offset) ...
... FLAGS -- 3-bit field with individual bits specifying whether the datagram is a fragment FRAGMENT OFFSET -- 13-bit field that specifies where in the original datagram the data in this fragment belongs (the value of the field is multiplied by 8 to obtain an offset) ...
Network Working Group S. Blake Request for
... This memo provides information for the Internet community. It does not specify an Internet standard of any kind. Distribution of this memo is unlimited. Copyright Notice Copyright (C) The Internet Society (1998). ...
... This memo provides information for the Internet community. It does not specify an Internet standard of any kind. Distribution of this memo is unlimited. Copyright Notice Copyright (C) The Internet Society (1998). ...
Personal Area Networks: Bluetooth or IEEE 802.11? | SpringerLink
... Interconnecting all our electronic devices we carry around, such as cellular phones, PDAs, and laptops, with wireless links requires a cheap, low-power radio technology that still delivers good performance. In this context, the Bluetooth wireless technology was developed to meet the requirements int ...
... Interconnecting all our electronic devices we carry around, such as cellular phones, PDAs, and laptops, with wireless links requires a cheap, low-power radio technology that still delivers good performance. In this context, the Bluetooth wireless technology was developed to meet the requirements int ...
TeamSpeak 3 And Broadband
... It is a simple process to hack specific routers with new firmware, enabling the establishment of wide band, high speed; self-discovering, self-healing Amateur radio IP based networks ...
... It is a simple process to hack specific routers with new firmware, enabling the establishment of wide band, high speed; self-discovering, self-healing Amateur radio IP based networks ...
Scheduler
... varied type of applications (such as voice, video, real-time streaming data) concurrently using the network. These applications typically require different levels of performance in terms of loss, delay, and throughput. This tutorial provides a theoretical overview of the basic functional blocks used ...
... varied type of applications (such as voice, video, real-time streaming data) concurrently using the network. These applications typically require different levels of performance in terms of loss, delay, and throughput. This tutorial provides a theoretical overview of the basic functional blocks used ...
Leading Networking Solutions for Industrial
... network topologies are simplified — resulting in recovery from media failure within 500 ms down to 10 ms (FastMRP). Sustainable Security Solutions Comprehensive security features in switches, routers and firewalls according to latest standards like IEC62443 and best practices offers all around prote ...
... network topologies are simplified — resulting in recovery from media failure within 500 ms down to 10 ms (FastMRP). Sustainable Security Solutions Comprehensive security features in switches, routers and firewalls according to latest standards like IEC62443 and best practices offers all around prote ...
Wireless LAN technology is being recognized and accepted or
... Temporal Key Integrity Protocol (TKIP) as a short-term solution, known as WiFi Protected Access (WPA), to address problems with WEP and to support legacy systems. 6 It is a cipher suite that consists of three protocols: a cryptographic message integrity algorithm, a key mixing algorithm, and an enha ...
... Temporal Key Integrity Protocol (TKIP) as a short-term solution, known as WiFi Protected Access (WPA), to address problems with WEP and to support legacy systems. 6 It is a cipher suite that consists of three protocols: a cryptographic message integrity algorithm, a key mixing algorithm, and an enha ...
OfficeServ 7400 GWIMT/GWIM User Manual
... Support of IP Multicast − Support of IGMPv1(Internet Group Management Protocol version1), IGMPv2 protocols − Support of Distance Vector Multicast Routing Protocol (DVMRP), (Protocol Independent Multicast-Sparse Mode) PIM-SM multicast routing protocol ...
... Support of IP Multicast − Support of IGMPv1(Internet Group Management Protocol version1), IGMPv2 protocols − Support of Distance Vector Multicast Routing Protocol (DVMRP), (Protocol Independent Multicast-Sparse Mode) PIM-SM multicast routing protocol ...
AlliedWare Plus™ OS How To | Introduction
... LLDP for Media Endpoint Devices (LLDP-MED) is an extension of LLDP used between LAN network connectivity devices – such as switches – and the media endpoint devices connected to them – such as IP phones. A powerful feature of LLDP-MED is its ability to carry configuration instructions from the switc ...
... LLDP for Media Endpoint Devices (LLDP-MED) is an extension of LLDP used between LAN network connectivity devices – such as switches – and the media endpoint devices connected to them – such as IP phones. A powerful feature of LLDP-MED is its ability to carry configuration instructions from the switc ...
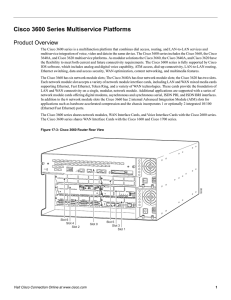
Cisco 3600 Series Multiservice Platforms
... The Cisco 3600 series is a multifunction platform that combines dial access, routing, and LAN-to-LAN services and multiservice integration of voice, video and data in the same device. The Cisco 3600 series includes the Cisco 3660, the Cisco 3640A, and Cisco 3620 multiservice platforms. As modular so ...
... The Cisco 3600 series is a multifunction platform that combines dial access, routing, and LAN-to-LAN services and multiservice integration of voice, video and data in the same device. The Cisco 3600 series includes the Cisco 3660, the Cisco 3640A, and Cisco 3620 multiservice platforms. As modular so ...
Networking Overview
... Reserved --- reserved for future use (or for clever attackers…) Window --- controls number of outstanding packets; prevents one side from sending too fast (flow control) Checksum --- error detection (uses CRC) ...
... Reserved --- reserved for future use (or for clever attackers…) Window --- controls number of outstanding packets; prevents one side from sending too fast (flow control) Checksum --- error detection (uses CRC) ...
2 - Cambridge Computer Laboratory
... Addressing (at a conceptual level) • Assume all hosts have unique IDs • No particular structure to those IDs • Later in topic I will talk about real IP addressing • Do I route on location or identifier? • If a host moves, should its address change? – If not, how can you build scalable Internet? – I ...
... Addressing (at a conceptual level) • Assume all hosts have unique IDs • No particular structure to those IDs • Later in topic I will talk about real IP addressing • Do I route on location or identifier? • If a host moves, should its address change? – If not, how can you build scalable Internet? – I ...
PDF
... A cost-effective, secure, and high-performance network switching foundation for small and medium-sized businesses (SMBs) Today’s innovative technologies have helped SMBs become more competitive than ever before. However, modern business technologies also can present significant challenges. As busine ...
... A cost-effective, secure, and high-performance network switching foundation for small and medium-sized businesses (SMBs) Today’s innovative technologies have helped SMBs become more competitive than ever before. However, modern business technologies also can present significant challenges. As busine ...
Ch-5 Presentation
... source and the destination for LANs and WANs. Latency has at least three sources: – First, there is the time it takes the source NIC to place voltage pulses on the wire and the time it takes the receiving NIC to interpret these pulses. This is sometimes called NIC delay. – Second, there is the actua ...
... source and the destination for LANs and WANs. Latency has at least three sources: – First, there is the time it takes the source NIC to place voltage pulses on the wire and the time it takes the receiving NIC to interpret these pulses. This is sometimes called NIC delay. – Second, there is the actua ...


![LN_ch07_Networking_Unix_Linux[2]ch14](http://s1.studyres.com/store/data/008747649_1-f6bc28385c6088d404edcf68eef533e5-300x300.png)