THE OPTIMIZATION OF STEPPING STONE DETECTION: PACKET CAPTURING STEPS MOHD NIZAM OMAR
... IRIX, and BSD Packet Filter [22]. All of these facilities only work in Unix-based environment. BSD offers substantial performance improvement over existing packet capture facilities, 10 to 150 times faster than Sun’s NIT, and 1.5 times faster than CPSF on the same hardware and traffic mix. In window ...
... IRIX, and BSD Packet Filter [22]. All of these facilities only work in Unix-based environment. BSD offers substantial performance improvement over existing packet capture facilities, 10 to 150 times faster than Sun’s NIT, and 1.5 times faster than CPSF on the same hardware and traffic mix. In window ...
Introduction
... routing information within AS. Exterior Gateway Routing Protocol (EGP) like BGP is used for sharing routing information between ASs. The Information, exchanged using routing protocols, is about all reachable networks. Every router in the Internet must have the information about all networks in its r ...
... routing information within AS. Exterior Gateway Routing Protocol (EGP) like BGP is used for sharing routing information between ASs. The Information, exchanged using routing protocols, is about all reachable networks. Every router in the Internet must have the information about all networks in its r ...
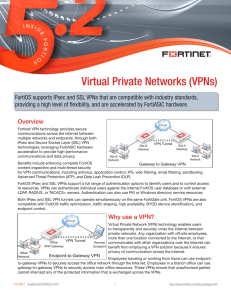
Virtual Private Networks (VPNs)
... FortiOS IPsec VPN FortiOS IPsec VPN supports all of the common industry standard IPsec features, including IKE v1 and v2, manual keys, static and dynamic gateway IP addresses, aggressive and main mode negotiation, pre-shared keys, X.509 security certificates, extended authentication (XAUTH), Diffie ...
... FortiOS IPsec VPN FortiOS IPsec VPN supports all of the common industry standard IPsec features, including IKE v1 and v2, manual keys, static and dynamic gateway IP addresses, aggressive and main mode negotiation, pre-shared keys, X.509 security certificates, extended authentication (XAUTH), Diffie ...
Understanding Simple Network Management Protocol
... Stopping any SNMP service may result in loss of data because the network management system no longer monitors the Cisco Unified Communications Manager network. Do not stop the services unless your technical support team tells you to do so. ...
... Stopping any SNMP service may result in loss of data because the network management system no longer monitors the Cisco Unified Communications Manager network. Do not stop the services unless your technical support team tells you to do so. ...
New ECC Report Style
... regarding partial on-path support, however it is still unclear which performance can be ensured in those contexts. On the other hand, the IEEE-1588v2/SyncE technologies are expected to be operational when they are deployed over a LAN with tightly controlled equipments. Therefore a possible approach ...
... regarding partial on-path support, however it is still unclear which performance can be ensured in those contexts. On the other hand, the IEEE-1588v2/SyncE technologies are expected to be operational when they are deployed over a LAN with tightly controlled equipments. Therefore a possible approach ...
Chapter5 (IPv4 Address)
... A network mask or a default mask in classful addressing is a 32-bit number with n leftmost bits all set to 1s and (32 – n) rightmost bits all set to 0s. It is used by a router to find the network address from the destination address of a packet. The idea of splitting a network into smaller subne ...
... A network mask or a default mask in classful addressing is a 32-bit number with n leftmost bits all set to 1s and (32 – n) rightmost bits all set to 0s. It is used by a router to find the network address from the destination address of a packet. The idea of splitting a network into smaller subne ...
CCNA - College of DuPage
... In the example, all switches have STP enabled: 1. PC1 sends a broadcast out onto the network. 2. Switch S3 is configured with STP and has set the port for Trunk2 to a blocking state. The blocking state prevents ports from being used to forward switch traffic, preventing a loop from occurring. ...
... In the example, all switches have STP enabled: 1. PC1 sends a broadcast out onto the network. 2. Switch S3 is configured with STP and has set the port for Trunk2 to a blocking state. The blocking state prevents ports from being used to forward switch traffic, preventing a loop from occurring. ...
9Ethernet
... If a host detects a collision while it is sending the first 64 bits of a frame then CSMA/CD works and the frame will get resent later. If the host has sent 64 bits and then detects a collision, it is too late. It will not resend. Latency must be small enough so that all collisions are detected in ti ...
... If a host detects a collision while it is sending the first 64 bits of a frame then CSMA/CD works and the frame will get resent later. If the host has sent 64 bits and then detects a collision, it is too late. It will not resend. Latency must be small enough so that all collisions are detected in ti ...
Mobile - CSE, IIT Bombay
... • When a new ack is received with receiver’s advertised window = 0, the sender enters persist mode • Sender does not send any data in persist mode ...
... • When a new ack is received with receiver’s advertised window = 0, the sender enters persist mode • Sender does not send any data in persist mode ...
PDF Datasheet – NSA Series
... with an extensive array of advanced networking and flexible configuration features. The NSA Series offers an affordable platform that is easy to deploy and manage in a wide variety of large, branch office and distributed network environments. ...
... with an extensive array of advanced networking and flexible configuration features. The NSA Series offers an affordable platform that is easy to deploy and manage in a wide variety of large, branch office and distributed network environments. ...
OSS Community Structure - University of Notre Dame
... Structure", NAACSOS2005, Notre Dame, IN, June 2005. Jin Xu, Yongqin Gao, Scott Christley, Greg Madey, "A Topological Analysis of the Open Source Software Development Community", The 38th Hawaii International Conference on Systems ...
... Structure", NAACSOS2005, Notre Dame, IN, June 2005. Jin Xu, Yongqin Gao, Scott Christley, Greg Madey, "A Topological Analysis of the Open Source Software Development Community", The 38th Hawaii International Conference on Systems ...
IP address
... (or site). • The addresses can reflect this hierarchy in the physical network. • Ex: – If the campus is granted 65536 addresses,the first 2 bytes can define the whole network (site); the third byte can define the subnet; and the fourth byte can define a host on a subnet. – The first 2bytes,are the s ...
... (or site). • The addresses can reflect this hierarchy in the physical network. • Ex: – If the campus is granted 65536 addresses,the first 2 bytes can define the whole network (site); the third byte can define the subnet; and the fourth byte can define a host on a subnet. – The first 2bytes,are the s ...
pptx - Cambridge Computer Laboratory
... Addressing (at a conceptual level) • Assume all hosts have unique IDs • No particular structure to those IDs • Later in topic I will talk about real IP addressing • Do I route on location or identifier? • If a host moves, should its address change? – If not, how can you build scalable Internet? – I ...
... Addressing (at a conceptual level) • Assume all hosts have unique IDs • No particular structure to those IDs • Later in topic I will talk about real IP addressing • Do I route on location or identifier? • If a host moves, should its address change? – If not, how can you build scalable Internet? – I ...
PDF
... The increase in 3G and 4G mobile wireless broadband usage is an indication of even more dramatic growth, which is expected to result from the introduction of High-Speed Packet Access (HSPA), Evolved High-Speed Packet Access (HSPA+), and LTE technologies. To meet the demand and deliver services that ...
... The increase in 3G and 4G mobile wireless broadband usage is an indication of even more dramatic growth, which is expected to result from the introduction of High-Speed Packet Access (HSPA), Evolved High-Speed Packet Access (HSPA+), and LTE technologies. To meet the demand and deliver services that ...
Toward an IPv6 world in mobile networks – mechanisms
... domain name system records, the DNS64 returns this record unchanged and the UE uses IPv6 to connect to the server directly. Otherwise, the DNS64 returns a synthesized address, and packets using that address are automatically routed to the NAT64. The NAT64 will perform address translation and forward ...
... domain name system records, the DNS64 returns this record unchanged and the UE uses IPv6 to connect to the server directly. Otherwise, the DNS64 returns a synthesized address, and packets using that address are automatically routed to the NAT64. The NAT64 will perform address translation and forward ...
IPV6 Essentials - AFCEA International
... – Now based only in IP header information – Flow label, sender address, destination address ...
... – Now based only in IP header information – Flow label, sender address, destination address ...
TR-M2M-0009v0.7.0 oneM2M Protocol Analysis
... This is a draft oneM2M document and should not be relied upon; the final version, if any, will be made available by oneM2M Partners Type 1. ...
... This is a draft oneM2M document and should not be relied upon; the final version, if any, will be made available by oneM2M Partners Type 1. ...
oneM2M-TR-0009-Protocol_Analysis-V0_4_0
... This is a draft oneM2M document and should not be relied upon; the final version, if any, will be made available by oneM2M Partners Type 1. ...
... This is a draft oneM2M document and should not be relied upon; the final version, if any, will be made available by oneM2M Partners Type 1. ...
Protocol Analysis
... This is a draft oneM2M document and should not be relied upon; the final version, if any, will be made available by oneM2M Partners Type 1. ...
... This is a draft oneM2M document and should not be relied upon; the final version, if any, will be made available by oneM2M Partners Type 1. ...
6 Multi-layer Recovery Strategy in Resilient Packet
... point-to-point circuit-switched services such as voice services. On the other hand, for metropolitan environments, Ethernet technology may offer a simpler and cost-effective solution for the transport of the data traffic. However, because Ethernet is optimized for point-to-point or meshed topologies ...
... point-to-point circuit-switched services such as voice services. On the other hand, for metropolitan environments, Ethernet technology may offer a simpler and cost-effective solution for the transport of the data traffic. However, because Ethernet is optimized for point-to-point or meshed topologies ...
IMTC H.323 Forum Launch
... Switched optical networks Optics in access and metropolitan networks Optical interfaces Optical/IP network OAM and protection and restoration WDM and C&D-WDM Signalling and routing Optical fibres, cables and components Optical network management Optical switching equipment Network performance (IP/Op ...
... Switched optical networks Optics in access and metropolitan networks Optical interfaces Optical/IP network OAM and protection and restoration WDM and C&D-WDM Signalling and routing Optical fibres, cables and components Optical network management Optical switching equipment Network performance (IP/Op ...
Chapter
... • Phone calls over IP are no better than over satellite! (too much DELAY) • Phone calls have really bad voice quality! (too many phone calls – ADMISSION CONTROL) ...
... • Phone calls over IP are no better than over satellite! (too much DELAY) • Phone calls have really bad voice quality! (too many phone calls – ADMISSION CONTROL) ...
AirLink Raven XE - Sierra Wireless Source
... Due to the nature of wireless communications, transmission and reception of data can never be guaranteed. Data may be delayed, corrupted (i.e., have errors) or be totally lost. Although significant delays or losses of data are rare when wireless devices such as the Sierra Wireless AirLink Raven XE a ...
... Due to the nature of wireless communications, transmission and reception of data can never be guaranteed. Data may be delayed, corrupted (i.e., have errors) or be totally lost. Although significant delays or losses of data are rare when wireless devices such as the Sierra Wireless AirLink Raven XE a ...
cis185-ROUTE-lecture2-EIGRP-Part2
... Automatically maps the IP address of the devices at the other end of the PVCs to the local DLCI number. Split horizon is disabled by default on Frame Relay physical interfaces. Routes from Router R2 can be sent to Router R3, and vise-versa. Note: Inverse ARP does not provide dynamic mapping ...
... Automatically maps the IP address of the devices at the other end of the PVCs to the local DLCI number. Split horizon is disabled by default on Frame Relay physical interfaces. Routes from Router R2 can be sent to Router R3, and vise-versa. Note: Inverse ARP does not provide dynamic mapping ...
document
... Entirely new transport protocol – Hard to deploy widely – End-to-end protocol needs to be efficient on wired networks too – Must implement much of TCP’s flow control Modifications to TCP – Maintain end-to-end semantics – May or may not be backwards compatible Split-connection TCP – Breaks end- ...
... Entirely new transport protocol – Hard to deploy widely – End-to-end protocol needs to be efficient on wired networks too – Must implement much of TCP’s flow control Modifications to TCP – Maintain end-to-end semantics – May or may not be backwards compatible Split-connection TCP – Breaks end- ...