Artificial Immune Systems - Brunel University Research Archive
... The Negative Selection is one of the mechanisms of the natural immune system that has inspired the developments of most of the existing Artificial Immune systems. In the T-cell maturation process of the immune system, if a Tcell in thymus recognizes any self cell, it is eliminated before deploying f ...
... The Negative Selection is one of the mechanisms of the natural immune system that has inspired the developments of most of the existing Artificial Immune systems. In the T-cell maturation process of the immune system, if a Tcell in thymus recognizes any self cell, it is eliminated before deploying f ...
Plug-In Wi-Fi® RANGE EXTENDER
... wireless performance with protected mode OFF. Conversely, in an environment with HEAVY 802.11g or 802.11b traffic or interference, you will achieve the best wireless performance with protected mode ON. This will ensure wireless performance is not affected. ...
... wireless performance with protected mode OFF. Conversely, in an environment with HEAVY 802.11g or 802.11b traffic or interference, you will achieve the best wireless performance with protected mode ON. This will ensure wireless performance is not affected. ...
www.yorktech.com
... Understand the function of a router. Understand the structure of a routing table. Choose between static or dynamic routing on your ...
... Understand the function of a router. Understand the structure of a routing table. Choose between static or dynamic routing on your ...
here - Campaign[x]
... Read Me First: How to Use This Deck This deck is designed to give you the information you need to develop your Borderless Networks sales pitch. Read slides 4–7 to understand the market factors that have led to the development of the Borderless Network Architecture and the role it plays in forward ...
... Read Me First: How to Use This Deck This deck is designed to give you the information you need to develop your Borderless Networks sales pitch. Read slides 4–7 to understand the market factors that have led to the development of the Borderless Network Architecture and the role it plays in forward ...
The Internet and Its Uses
... The routing process requires the source device to determine if the destination device is local or remote to the local subnet. –The source device accomplishes this by comparing the source and destination addresses against the subnet mask. –Once the destination address has been determined to be on a ...
... The routing process requires the source device to determine if the destination device is local or remote to the local subnet. –The source device accomplishes this by comparing the source and destination addresses against the subnet mask. –Once the destination address has been determined to be on a ...
Trickle: A Userland Bandwidth Shaper for Unix-like Systems
... and resides in the operating system kernel. Network traffic is not associated with the local processes responsible for generating the traffic. Rather, other criteria such as IP, TCP or UDP protocols and destination IP addresses are used in classifying network traffic for shaping. These policies are ...
... and resides in the operating system kernel. Network traffic is not associated with the local processes responsible for generating the traffic. Rather, other criteria such as IP, TCP or UDP protocols and destination IP addresses are used in classifying network traffic for shaping. These policies are ...
Cytoscape
... Analysis Find clusters (highly interconnected regions) from loaded networks clusters may have different mean depending on the type of network : in ppi : they have been shown to be protein complexes and part of pathways in protein similarity network : they represent protein families ...
... Analysis Find clusters (highly interconnected regions) from loaded networks clusters may have different mean depending on the type of network : in ppi : they have been shown to be protein complexes and part of pathways in protein similarity network : they represent protein families ...
Technical University Berlin Telecommunication Networks Group Optimization of Handover Performance
... a new one. In these cases, an unnecessary handover is triggered. While with ECS a single handover impairs the communication quality less than with LCS, the overall number of handovers — necessary and unnecessary – is higher. At all, there might be no improvement by the ECS algorithm. An alternative ...
... a new one. In these cases, an unnecessary handover is triggered. While with ECS a single handover impairs the communication quality less than with LCS, the overall number of handovers — necessary and unnecessary – is higher. At all, there might be no improvement by the ECS algorithm. An alternative ...
Distance Vector Routing Protocols
... • The command passive-interface is used to prevent routers from sending routing updates thorough an interface • This is to prevent devices from learning about routes you would prefer they not know about • This disables the sending out of RIP updates from that interface, but the router still receives ...
... • The command passive-interface is used to prevent routers from sending routing updates thorough an interface • This is to prevent devices from learning about routes you would prefer they not know about • This disables the sending out of RIP updates from that interface, but the router still receives ...
profinet - Siemens
... very closely resembles that of PROFIBUS. For example, a SIMATIC ET 200SP station can be converted to PROFINET through simple replacement of an interface module: Simply change the configuration and reload it – done. Do I have to convert plants completely or is gradual conversion also a possibility? E ...
... very closely resembles that of PROFIBUS. For example, a SIMATIC ET 200SP station can be converted to PROFINET through simple replacement of an interface module: Simply change the configuration and reload it – done. Do I have to convert plants completely or is gradual conversion also a possibility? E ...
c 2009 IEEE. Personal use of this material is permitted. However
... nodes are equally likely to encounter each other, and nodes need to assess the probability that they will encounter the destination node. Additionally, Hsu and Helmy performed an analysis on real world encounters based on network traffic traces of different university campus wireless networks [22]. ...
... nodes are equally likely to encounter each other, and nodes need to assess the probability that they will encounter the destination node. Additionally, Hsu and Helmy performed an analysis on real world encounters based on network traffic traces of different university campus wireless networks [22]. ...
Mobile Ad-hoc Clouds
... landscape. The ease of access to a pool of devices is much more arbitrary and based purely on the needs of the user. This pool can act as a provider of an infrastructure for various services that can be processed with volunteer node participation, where the node in the vicinity is itself a service p ...
... landscape. The ease of access to a pool of devices is much more arbitrary and based purely on the needs of the user. This pool can act as a provider of an infrastructure for various services that can be processed with volunteer node participation, where the node in the vicinity is itself a service p ...
Firewall and Network Address Translation Feature
... firewalls no longer talk about packets, IP addresses and ports. Instead they focus on applications, users and content. It classifies traffic by the application’s identity in order to enable visibility and control of all types of application. The AR-Series firewalls view the physical network in terms ...
... firewalls no longer talk about packets, IP addresses and ports. Instead they focus on applications, users and content. It classifies traffic by the application’s identity in order to enable visibility and control of all types of application. The AR-Series firewalls view the physical network in terms ...
思科运营商网络研讨会: 苏远超 思科中国电信运营商事业部 高级顾问工程师 2011.10.27
... Cisco’s solution offers 68% savings on power consumption vs Alcatel over a 3 year period. ...
... Cisco’s solution offers 68% savings on power consumption vs Alcatel over a 3 year period. ...
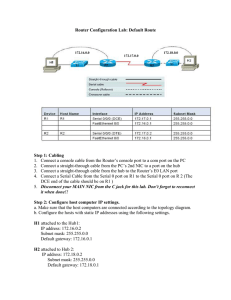
3 Router Configuration - Cisco Networking Academy
... b. Each interface should be shown separately, with a status line that tells you if that interface is up and running. The interface that connects the 2 R1s will only be up if both ends are configured properly. You should see: “Serial 0 is up, Line Protocol is up” c. If you get a message that Serial 0 ...
... b. Each interface should be shown separately, with a status line that tells you if that interface is up and running. The interface that connects the 2 R1s will only be up if both ends are configured properly. You should see: “Serial 0 is up, Line Protocol is up” c. If you get a message that Serial 0 ...
Machine-to-Machine (M2M) Gateway: Trusted and Connected
... machines than people and Machine-to-Machine (M2M) technology will help us to be more energy and cost-efficient, safer and more secure. This is the era of connected intelligence. The number of mobile connections is forecast by the GSM association to grow to 50 billion by the end of the decade. There ...
... machines than people and Machine-to-Machine (M2M) technology will help us to be more energy and cost-efficient, safer and more secure. This is the era of connected intelligence. The number of mobile connections is forecast by the GSM association to grow to 50 billion by the end of the decade. There ...
Introduction
... Case 2 : No Physical Multicast Support Most WANs do not support physical multicast addressing . To send a multicast packet through these networks, a process called tunneling is used. In tunneling , the multicast packet is encapsulated in a unicast packet and sent through the network, where it emer ...
... Case 2 : No Physical Multicast Support Most WANs do not support physical multicast addressing . To send a multicast packet through these networks, a process called tunneling is used. In tunneling , the multicast packet is encapsulated in a unicast packet and sent through the network, where it emer ...
Network Security: GSM and 3G Security
... FRESH prevents the replay of old signalling messages if the RNC reuses old session keys (need to check the spec for when this can happen…) ...
... FRESH prevents the replay of old signalling messages if the RNC reuses old session keys (need to check the spec for when this can happen…) ...
AT16827: TCP/IP Server-Client with CycloneTCP
... Each layer of the protocol stack is responsible for a particular level of functionality. For example, the physical layer takes care of electrical transmission of bits across a medium. Each higher layer in the stack utilizes the underlying layers. There is no overlap in functions between the layers. ...
... Each layer of the protocol stack is responsible for a particular level of functionality. For example, the physical layer takes care of electrical transmission of bits across a medium. Each higher layer in the stack utilizes the underlying layers. There is no overlap in functions between the layers. ...
Avionics
... ARINC 429 is no more sufficient: too many buses are needed ARINC 629 is too expensive Why Ethernet technology ? I I I I ...
... ARINC 429 is no more sufficient: too many buses are needed ARINC 629 is too expensive Why Ethernet technology ? I I I I ...
SpeedStream - Bell Customer Support Centre
... The following describes your license to use the software (the “Software”) that has been provided with your SSN DSL customer premises equipment (“Hardware”) and the limited warranty that SSN provides on its Software and Hardware. Software License The Software is protected by copyright laws and intern ...
... The following describes your license to use the software (the “Software”) that has been provided with your SSN DSL customer premises equipment (“Hardware”) and the limited warranty that SSN provides on its Software and Hardware. Software License The Software is protected by copyright laws and intern ...
The TCP Segment Header - CIS @ Temple University
... Of the several timers TCP maintains the most important is the retransmission timer RTO, (also called timeout) . After each segment is sent, TCP starts a retransmission timer, if ACK arrives before timer expires, cancel timer. If timer expires first, consider segment lost. ...
... Of the several timers TCP maintains the most important is the retransmission timer RTO, (also called timeout) . After each segment is sent, TCP starts a retransmission timer, if ACK arrives before timer expires, cancel timer. If timer expires first, consider segment lost. ...



![here - Campaign[x]](http://s1.studyres.com/store/data/008744944_1-0f4fd57a8eb108cf9826822f0ba0b000-300x300.png)