paper - Command and Control Research Portal
... increase overall bandwidth at the tactical level, this paper will only discuss the SkyCAP software suite and its application to current UHF SATCOM capability. The ability to execute true distributed and collaborative planning for amphibious operations, including ship-toobjective maneuver, selected i ...
... increase overall bandwidth at the tactical level, this paper will only discuss the SkyCAP software suite and its application to current UHF SATCOM capability. The ability to execute true distributed and collaborative planning for amphibious operations, including ship-toobjective maneuver, selected i ...
transparencies - Indico
... First ideas on SCI started in 1987 resulting in an accepted standard: ANSI/IEEE 1596/1992. SCI first of all an OPEN distributed bus, with network capabilities. Physical connections are based on parallel serial links with ring oriented interconnects able to connect up to 64 K nodes. Including switche ...
... First ideas on SCI started in 1987 resulting in an accepted standard: ANSI/IEEE 1596/1992. SCI first of all an OPEN distributed bus, with network capabilities. Physical connections are based on parallel serial links with ring oriented interconnects able to connect up to 64 K nodes. Including switche ...
The Internet and Its Uses
... specific mode. In general, it is standard practice here at the University of Illinois U-C campus to hand configure all switch uplink interfaces and router interfaces to a specific mode of operation, and not rely on any of the autonegotiating or auto-sensing systems. ...
... specific mode. In general, it is standard practice here at the University of Illinois U-C campus to hand configure all switch uplink interfaces and router interfaces to a specific mode of operation, and not rely on any of the autonegotiating or auto-sensing systems. ...
Employing a secure Virtual Private Network (VPN)
... GHOSTNet is a secure and anonymous Virtual Private Network (VPN) service. Coupling Ethernet tunneling and proxy services to provide users safe and anonymous Internet access, GHOSTNet utilizes TLS (SSL) protocol with AES-256 encryption to secure the network along with PKI certificates and HMAC protec ...
... GHOSTNet is a secure and anonymous Virtual Private Network (VPN) service. Coupling Ethernet tunneling and proxy services to provide users safe and anonymous Internet access, GHOSTNet utilizes TLS (SSL) protocol with AES-256 encryption to secure the network along with PKI certificates and HMAC protec ...
Virtual Private Networks (VPN`s)
... A well-designed VPN uses several methods for keeping your connection and data secure: Firewalls Encryption IPSec AAA Server You can set firewalls to restrict the number of open ports, what type of packets are passed through and which protocols are allowed through. ...
... A well-designed VPN uses several methods for keeping your connection and data secure: Firewalls Encryption IPSec AAA Server You can set firewalls to restrict the number of open ports, what type of packets are passed through and which protocols are allowed through. ...
Study on a Fast OSPF Route Reconstruction Method Under Network
... by original OSPF. General speaking, this time length of communication failure is very long for many applications on networks. Thus, when the DR has ceased the routing operation on OSPF networks by the network failure, it takes long time to recover the network operation. There is a simple method to r ...
... by original OSPF. General speaking, this time length of communication failure is very long for many applications on networks. Thus, when the DR has ceased the routing operation on OSPF networks by the network failure, it takes long time to recover the network operation. There is a simple method to r ...
DEFT: Distributed Exponentially-weighted Flow Splitting
... link-state routing protocols, and link weights is a concise form of configuration state, with one parameter on each unidirectional link. The weights have natural default values (e.g., inversely proportional to link capacity or proportional to propagation delay). If the topology changes, the routers ...
... link-state routing protocols, and link weights is a concise form of configuration state, with one parameter on each unidirectional link. The weights have natural default values (e.g., inversely proportional to link capacity or proportional to propagation delay). If the topology changes, the routers ...
Efficient Network Level Beamforming Training for IEEE 802.11ad
... if the devices have their beams pointing towards each other. Beamforming training (BF) is used to help choose the best beam direction pair that gives the highest channel gain. Beamforming at 60 GHz has received a lot of attention in the literature for point to point communication and there has been ...
... if the devices have their beams pointing towards each other. Beamforming training (BF) is used to help choose the best beam direction pair that gives the highest channel gain. Beamforming at 60 GHz has received a lot of attention in the literature for point to point communication and there has been ...
NTC-8000-01 User Guide
... This document is intended to be used by system integrators or experienced hardware installers who are comfortable with all aspects of IP based networking and have an understanding of wireless technologies. ...
... This document is intended to be used by system integrators or experienced hardware installers who are comfortable with all aspects of IP based networking and have an understanding of wireless technologies. ...
Protection Switching - ECSE - Rensselaer Polytechnic Institute
... Rensselaer Polytechnic Institute ...
... Rensselaer Polytechnic Institute ...
NPort 5600-8-DT/DTL Series User’s Manual Seventh Edition, February 2014 www.moxa.com/product
... Moxa provides this document as is, without warranty of any kind, either expressed or implied, including, but not limited to, its particular purpose. Moxa reserves the right to make improvements and/or changes to this manual, or to the products and/or the programs described in this manual, at any tim ...
... Moxa provides this document as is, without warranty of any kind, either expressed or implied, including, but not limited to, its particular purpose. Moxa reserves the right to make improvements and/or changes to this manual, or to the products and/or the programs described in this manual, at any tim ...
Best Practices for Building a Virtualized SPARC Computing
... existing CDOMs, to enable the full functionality that Enterprise Manager Ops Center provides to the Virtualization Infrastructure layer, use Enterprise Manager Ops Center to discover the hardware and to deploy the CDOM on top of bare metal hardware. It is recommended that any server that is deployed ...
... existing CDOMs, to enable the full functionality that Enterprise Manager Ops Center provides to the Virtualization Infrastructure layer, use Enterprise Manager Ops Center to discover the hardware and to deploy the CDOM on top of bare metal hardware. It is recommended that any server that is deployed ...
IDS definition and classification
... • Some authors consider an IPS a new (fourth) generation IDS – a convergence of firewall and IDS. • IPS use IDS algorithms to monitor and drop/allow traffic based on expert analysis. • The ”firewall” part of an IPS can prevent malicious traffic from entering/exiting the network. It can also alert th ...
... • Some authors consider an IPS a new (fourth) generation IDS – a convergence of firewall and IDS. • IPS use IDS algorithms to monitor and drop/allow traffic based on expert analysis. • The ”firewall” part of an IPS can prevent malicious traffic from entering/exiting the network. It can also alert th ...
IPv6 Transition Mechanisms and Strategies
... permanent and used for Identifications The Care-of-Address is the second IP address that is related to a foreign network, and that changes each time the host attaches to a different physical network (used for routing) A Mobile Host (MH) is allowed to roam to any IP network while other nodes conn ...
... permanent and used for Identifications The Care-of-Address is the second IP address that is related to a foreign network, and that changes each time the host attaches to a different physical network (used for routing) A Mobile Host (MH) is allowed to roam to any IP network while other nodes conn ...
Detecting Malicious SMB Activity Using Bro
... using evasion techniques. Bro Network Security Monitor (Bro) provides an alternative solution that allows for rapid detection through custom scripts and log data. Bro is an open source network security framework based on Unix, and can be used as an intrusion detection system (Bro, 2014). Bro passive ...
... using evasion techniques. Bro Network Security Monitor (Bro) provides an alternative solution that allows for rapid detection through custom scripts and log data. Bro is an open source network security framework based on Unix, and can be used as an intrusion detection system (Bro, 2014). Bro passive ...
wienet - Wieland Electric Inc.
... Wieland's wienet VPN industrial routers ensure increased efficiency and data security. Whether it is about the control of machines, monitoring of production lines or the coordination of all production areas a permanent communication between devices is needed to complete such a complex task. Access t ...
... Wieland's wienet VPN industrial routers ensure increased efficiency and data security. Whether it is about the control of machines, monitoring of production lines or the coordination of all production areas a permanent communication between devices is needed to complete such a complex task. Access t ...
HPE SN6000B Fibre Channel Switch
... storage technology to work for you. We work closely with you as your strategic partner, leveraging our full services portfolio to make sure that everything works to optimize your enterprise. Choose from services aligned to our storage product offerings and lifecycle. From mission-critical onsite ser ...
... storage technology to work for you. We work closely with you as your strategic partner, leveraging our full services portfolio to make sure that everything works to optimize your enterprise. Choose from services aligned to our storage product offerings and lifecycle. From mission-critical onsite ser ...
3 What is MMS? - ECO Documentation Database
... MMS has been standardized by 3GPP [1, 2] and the standards have been published by ETSI. WAP is an industry standard produced by the WAP-forum, which has been integrated into the Open Mobile Alliance (OMA, http://www.openmobilealliance.org/). The work of the WAP Forum continues in the different Worki ...
... MMS has been standardized by 3GPP [1, 2] and the standards have been published by ETSI. WAP is an industry standard produced by the WAP-forum, which has been integrated into the Open Mobile Alliance (OMA, http://www.openmobilealliance.org/). The work of the WAP Forum continues in the different Worki ...
Broadband Router with built-in ADSL Modem
... device, pursuant to Part 15 of the FCC Rules. These limits are designed to provide reasonable protection against harmful interference in a residential installation. This equipment generates, uses and can radiate radio frequency energy and, if not installed and used in accordance with instructions, m ...
... device, pursuant to Part 15 of the FCC Rules. These limits are designed to provide reasonable protection against harmful interference in a residential installation. This equipment generates, uses and can radiate radio frequency energy and, if not installed and used in accordance with instructions, m ...
Read more - Broadband Internet Technical Advisory Group
... transport protocol or set of protocols. The purpose of these separate connection control and signaling protocols is to allow the parties involved in the communication to establish, control, and terminate connections. Many services that provide VoIP capability also support other forms of real-time me ...
... transport protocol or set of protocols. The purpose of these separate connection control and signaling protocols is to allow the parties involved in the communication to establish, control, and terminate connections. Many services that provide VoIP capability also support other forms of real-time me ...
Introduction to Routing and Packet Forwarding
... – R3 receives PPP frame – R3 then strips off PPP frame – R3 Examines destination IP – R3 consults routing table looking for destination IP – After finding destination IP in routing table, R3 is directly connected to destination via its fast Ethernet interface – R3 re-encapsulates IP packet with a ne ...
... – R3 receives PPP frame – R3 then strips off PPP frame – R3 Examines destination IP – R3 consults routing table looking for destination IP – After finding destination IP in routing table, R3 is directly connected to destination via its fast Ethernet interface – R3 re-encapsulates IP packet with a ne ...
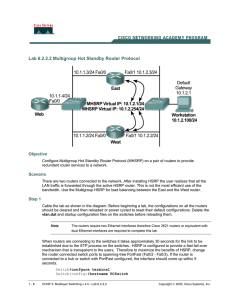
Lab 6.2.2.2 Multigroup Hot Standby Router Protocol
... If the ping does not work, go back and troubleshoot the configuration. Change the IP address of the workstation to another valid IP address (For example, 10.1.2.101) and then ping 10.1.1.4 again. Observe the lights on the routers and switch ports. Repeat this process several times using other valid ...
... If the ping does not work, go back and troubleshoot the configuration. Change the IP address of the workstation to another valid IP address (For example, 10.1.2.101) and then ping 10.1.1.4 again. Observe the lights on the routers and switch ports. Repeat this process several times using other valid ...
ITE PC v4.0 Chapter 1 - Prof. dr. Razvan Daniel ZOTA
... © 2008 Cisco Systems, Inc. All rights reserved. ...
... © 2008 Cisco Systems, Inc. All rights reserved. ...
Sample Chapter
... Protocol layering enables us to divide a complex task into several smaller and simpler tasks. For example, in Figure 2.2, we could have used only one machine to do the job of all three machines. However, if Maria and Ann decide that the encryption/ decryption done by the machine is not enough to pro ...
... Protocol layering enables us to divide a complex task into several smaller and simpler tasks. For example, in Figure 2.2, we could have used only one machine to do the job of all three machines. However, if Maria and Ann decide that the encryption/ decryption done by the machine is not enough to pro ...
twamp - rfc-5357 - H
... Latency/Delay measurements is NTP (Network Time Protocol) with his millisecond accuracy. ...
... Latency/Delay measurements is NTP (Network Time Protocol) with his millisecond accuracy. ...