0110/0111/0115 Access Point
... The Intermec access points are long-range, high-performance local area network (LAN) products that bridge Intermec’s 2.4 GHz radio frequency (RF) network and your wired (Ethernet or token ring) network. The access points operate at the Data Link level (layer 2) of the OSI model, providing protocolin ...
... The Intermec access points are long-range, high-performance local area network (LAN) products that bridge Intermec’s 2.4 GHz radio frequency (RF) network and your wired (Ethernet or token ring) network. The access points operate at the Data Link level (layer 2) of the OSI model, providing protocolin ...
Reference Manual for the ProSafe Dual Band Wireless VPN Firewall
... Routing Information Protocol ................................................................................... B-2 IP Addresses and the Internet ....................................................................................... B-2 Netmask ..................................................... ...
... Routing Information Protocol ................................................................................... B-2 IP Addresses and the Internet ....................................................................................... B-2 Netmask ..................................................... ...
Executive Summary
... workshops to ensure that the Study was able to set the direction of insights obtained from the industry and educational institutions. Likewise, all outcomes and findings were derived from the analysis of the provided information is based on best-effort basis, and therefore may not be fully represent ...
... workshops to ensure that the Study was able to set the direction of insights obtained from the industry and educational institutions. Likewise, all outcomes and findings were derived from the analysis of the provided information is based on best-effort basis, and therefore may not be fully represent ...
LABEL SPACE REDUCTION IN GMPLS AND ALL-OPTICAL LABEL SWAPPING NETWORKS
... Traditional Wavelength-Routing Switches (WRS) are still the most reliable technology used by ISPs nowadays. WRSs take advantage of the multiplexing capabilities of optical fibers to more efficiently route demands, a feature called WDM. With WDM, an optical fiber can be multiplexed into hundreds of w ...
... Traditional Wavelength-Routing Switches (WRS) are still the most reliable technology used by ISPs nowadays. WRSs take advantage of the multiplexing capabilities of optical fibers to more efficiently route demands, a feature called WDM. With WDM, an optical fiber can be multiplexed into hundreds of w ...
Release Notes for RingMaster Version 7.7.3.1
... Juniper sends two kinds of tokens electronically, in e-mail, in response to ordered licenses: Software Serial Numbers, and Authorization Codes. Software Serial numbers are sent when you order a base system (e.g., WLM-RTMS). Authorization Codes ( "AuthCodes") are sent when an additional capacity or f ...
... Juniper sends two kinds of tokens electronically, in e-mail, in response to ordered licenses: Software Serial Numbers, and Authorization Codes. Software Serial numbers are sent when you order a base system (e.g., WLM-RTMS). Authorization Codes ( "AuthCodes") are sent when an additional capacity or f ...
WiMax – Overview
... interface specification (officially known as the IEEE WirelessMAN* standard). This wireless broadband access standard could supply the missing link for the “last mile” connection in wireless metropolitan area networks. Wireless broadband access is set up like cellular systems, using base stations th ...
... interface specification (officially known as the IEEE WirelessMAN* standard). This wireless broadband access standard could supply the missing link for the “last mile” connection in wireless metropolitan area networks. Wireless broadband access is set up like cellular systems, using base stations th ...
ICMP and TCP - La Salle University
... Address Mask Request/Reply We discussed diskless workstation which do not know their IP address when they boot and use RARP to determine it. There is an ICMP packet used if a host does not know its subnet mask. ...
... Address Mask Request/Reply We discussed diskless workstation which do not know their IP address when they boot and use RARP to determine it. There is an ICMP packet used if a host does not know its subnet mask. ...
6400LF EdgeMarc Brochure
... 1 X 10/100/1000 Mbps Ethernet LAN interface High availability option for redundancy ...
... 1 X 10/100/1000 Mbps Ethernet LAN interface High availability option for redundancy ...
Compatible Systems Reference Guides
... The File menu’s options are primarily focused on the creation, editing and saving of configuration files and device configuration files. The two types of configuration files are different in that generic configuration files have not been associated with any particular device. These files can be used ...
... The File menu’s options are primarily focused on the creation, editing and saving of configuration files and device configuration files. The two types of configuration files are different in that generic configuration files have not been associated with any particular device. These files can be used ...
CNC 8055 Educational
... newer). The possible connections are: • Connection from a PC: The connection may be initiated at any PC and addressed to any CNC. Two PC's cannot be connected to each other. To establish the connection, the WinDNC allows the user to enter the CNC's IP address to be used for the connection. • Connect ...
... newer). The possible connections are: • Connection from a PC: The connection may be initiated at any PC and addressed to any CNC. Two PC's cannot be connected to each other. To establish the connection, the WinDNC allows the user to enter the CNC's IP address to be used for the connection. • Connect ...
Cisco IP SLA`s
... Cisco router to server • Threshold notifications when end point is not available What is the availability of a Network File System (NFS) server used to store business critical data from a remote site ? ...
... Cisco router to server • Threshold notifications when end point is not available What is the availability of a Network File System (NFS) server used to store business critical data from a remote site ? ...
CN 2015 1-2 - DSpace
... connection to a called party before any communication is possible. It maintain the connection to transfer message The circuit is terminated when the connection is closed. ...
... connection to a called party before any communication is possible. It maintain the connection to transfer message The circuit is terminated when the connection is closed. ...
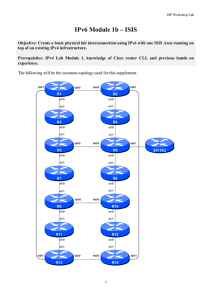
Module 01 - IPv6 ISIS and iBGP
... This workshop will adopt the recommendations of RFC6164 and use a /127 mask for each point-to-point link – even though the link still has a /64 reserved for it. With this revised system, the address plan for IPv6 is greatly simplified. ISPs assign a single /48 for their network infrastructure, and t ...
... This workshop will adopt the recommendations of RFC6164 and use a /127 mask for each point-to-point link – even though the link still has a /64 reserved for it. With this revised system, the address plan for IPv6 is greatly simplified. ISPs assign a single /48 for their network infrastructure, and t ...
CNAC - Cisco
... Reverse Engineering Performed – 335 of primarily the most popular Cisco chassis were tested to determine the optimal SNMP and CLI commands which yield the best possible electronic asset ID values with minimal data using read-only security ...
... Reverse Engineering Performed – 335 of primarily the most popular Cisco chassis were tested to determine the optimal SNMP and CLI commands which yield the best possible electronic asset ID values with minimal data using read-only security ...
Network Analysis Module
... with a simple workflow approach—from monitoring overall network health to analyzing a variety of detailed metrics and troubleshooting with packet-level details. • Supports network-services layers such as application optimization. • Offers a versatile combination of real-time traffic analysis, hist ...
... with a simple workflow approach—from monitoring overall network health to analyzing a variety of detailed metrics and troubleshooting with packet-level details. • Supports network-services layers such as application optimization. • Offers a versatile combination of real-time traffic analysis, hist ...
Reference Manual for the 108 Mbps Wireless Firewall Router WGT624
... MAC Addresses and Address Resolution Protocol ................................................. B-8 Related Documents ................................................................................................. B-9 Domain Name Server ............................................................. ...
... MAC Addresses and Address Resolution Protocol ................................................. B-8 Related Documents ................................................................................................. B-9 Domain Name Server ............................................................. ...
Description
... The purchased products, services and features are stipulated by the contract made between Huawei and the customer. All or part of the products, services and features described in this document may not be within the purchase scope or the usage scope. Unless otherwise specified in the contract, all st ...
... The purchased products, services and features are stipulated by the contract made between Huawei and the customer. All or part of the products, services and features described in this document may not be within the purchase scope or the usage scope. Unless otherwise specified in the contract, all st ...
Slide 1
... •When using this configuration the Blaster Managers and Sink Systems are both free and not machine locked, the user interface allows local access to system information only – The user can download and install multiple copies of this free software. The Blaster Remote Manager controls the Blaster Mana ...
... •When using this configuration the Blaster Managers and Sink Systems are both free and not machine locked, the user interface allows local access to system information only – The user can download and install multiple copies of this free software. The Blaster Remote Manager controls the Blaster Mana ...
Next Generation Car Network - FlexRay
... The CAN network has reached its performance limits with a maximum speed of 1 Mbps. With a maximum data rate of 10 Mbps available on two channels, giving a gross data rate of up to 20Mbit/sec, FlexRay potentially offers 20 times higher net bandwidth than CAN when used in the same application. ...
... The CAN network has reached its performance limits with a maximum speed of 1 Mbps. With a maximum data rate of 10 Mbps available on two channels, giving a gross data rate of up to 20Mbit/sec, FlexRay potentially offers 20 times higher net bandwidth than CAN when used in the same application. ...
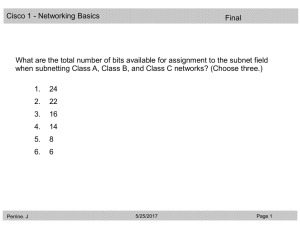
ITE PC v4.0 Chapter 1
... networking device interfaces, and the cables that connect them. Types of network media include twisted-pair copper cables, fiberoptic cables, coaxial cables, or wireless. Different types of network media have different features and benefits. Ethernet is the most common local area network (LAN) ...
... networking device interfaces, and the cables that connect them. Types of network media include twisted-pair copper cables, fiberoptic cables, coaxial cables, or wireless. Different types of network media have different features and benefits. Ethernet is the most common local area network (LAN) ...
Link OAM (IEEE 802.3ah)
... • Utilizes a “slow” protocol limited to 10 packets per second • OAMPDUs identified by MAC address and Ethernet Length/Type/subtype field • Uses a protocol sub layer between physical and Data link layers ...
... • Utilizes a “slow” protocol limited to 10 packets per second • OAMPDUs identified by MAC address and Ethernet Length/Type/subtype field • Uses a protocol sub layer between physical and Data link layers ...
Cisco Catalyst 3550 Series Switches for Metro Access
... TLS can transparently send and receive traffic from other metro sites through the service provider network as though the sites were within the same corporate LAN. In addition to Layer 2 VPN services, Multi-VRF CE (Virtual Routing Forwarding Customer Edge, also called VRF-lite) and Border Gateway Pro ...
... TLS can transparently send and receive traffic from other metro sites through the service provider network as though the sites were within the same corporate LAN. In addition to Layer 2 VPN services, Multi-VRF CE (Virtual Routing Forwarding Customer Edge, also called VRF-lite) and Border Gateway Pro ...
Slides
... Previously: Large-scale detection at Fortune 5 Bro user for 2+ years Focus on network forensics and incident response Twitter: @jshlbrd ...
... Previously: Large-scale detection at Fortune 5 Bro user for 2+ years Focus on network forensics and incident response Twitter: @jshlbrd ...
3346 Software User Guide V6.3
... Netopia and Cayman are registered trademarks, and “Making Broadband Work” is a trademark of Netopia, Inc. All rights reserved. Ethernet is a registered trademark of Xerox Corporation. Microsoft and Windows are registered trademarks of Microsoft Corporation. All other trademarks are the property of t ...
... Netopia and Cayman are registered trademarks, and “Making Broadband Work” is a trademark of Netopia, Inc. All rights reserved. Ethernet is a registered trademark of Xerox Corporation. Microsoft and Windows are registered trademarks of Microsoft Corporation. All other trademarks are the property of t ...