Networks and Communications
... A WAN spans a large geographical area and connects networks such as metropolitan area networks, public access networks, value added networks, and virtual private networks together. ...
... A WAN spans a large geographical area and connects networks such as metropolitan area networks, public access networks, value added networks, and virtual private networks together. ...
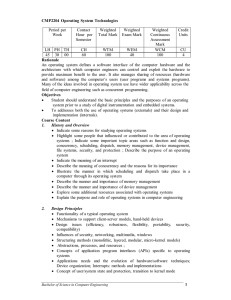
CMP2204 Operating System Technologies
... An operating system defines a software interface of the computer hardware and the architecture with which computer engineers can control and exploit the hardware to provide maximum benefit to the user. It also manages sharing of resources (hardware and software) among the computer’s users (user prog ...
... An operating system defines a software interface of the computer hardware and the architecture with which computer engineers can control and exploit the hardware to provide maximum benefit to the user. It also manages sharing of resources (hardware and software) among the computer’s users (user prog ...
CSC 482/582: Computer Security
... Malware Domain List (dangerous DNS domains) Risks Digest (discussion) Symantec (monthly threat reports) ...
... Malware Domain List (dangerous DNS domains) Risks Digest (discussion) Symantec (monthly threat reports) ...
CBA Hardware,Software, and - CBA-Survival
... The first part of an URL indicates the protocol required to access the page. The second part of an URL specifies the IP address or a domain name. The top-level domain at the end of the URL indicates the type of organization or ...
... The first part of an URL indicates the protocol required to access the page. The second part of an URL specifies the IP address or a domain name. The top-level domain at the end of the URL indicates the type of organization or ...
Current Issues in Maintaining a Secure System
... and adware detection tools • Microsoft has a beta version spyware detection and removal software available • Reinforces the importance of automated protection and monitoring ...
... and adware detection tools • Microsoft has a beta version spyware detection and removal software available • Reinforces the importance of automated protection and monitoring ...
Lecture 12
... Company wants to keep its IP addresses secret, but wants a consultant to analyze logs for an address scanning attack ...
... Company wants to keep its IP addresses secret, but wants a consultant to analyze logs for an address scanning attack ...
PROFESSIONAL JOB DESCRIPTION Network Support Engineer
... PROFESSIONAL JOB DESCRIPTION Exempt; Full‐time POSITION TITLE: ...
... PROFESSIONAL JOB DESCRIPTION Exempt; Full‐time POSITION TITLE: ...
Sentry System Health Monitoring Technical Requirements
... Sentry incorporates dual network interfaces in its design making it possible to reside on multiple networks simultaneously. This allows isolated security networks to be monitored from one interface and the Sentry appliance to report alert data back to the CSC on the other interface. ...
... Sentry incorporates dual network interfaces in its design making it possible to reside on multiple networks simultaneously. This allows isolated security networks to be monitored from one interface and the Sentry appliance to report alert data back to the CSC on the other interface. ...
Computer Information System
... In addition to computing concepts, CIS 101 uses a variant of Java based language for coding exercises. Students will not be learning or using the whole language. Instead, students will explore coding in a few well carved-out areas, by completing examples and exercises within those areas. 1. Analyze ...
... In addition to computing concepts, CIS 101 uses a variant of Java based language for coding exercises. Students will not be learning or using the whole language. Instead, students will explore coding in a few well carved-out areas, by completing examples and exercises within those areas. 1. Analyze ...
Assessment and Authorization for Cloud Computing
... requires an organizational defined setting) ...
... requires an organizational defined setting) ...
Chapter No. 08
... Analog – Special purpose computer based on continuous data and produce approximate results Digital Computers – General purpose Computers based on discrete date and produce accurate results Hybrid – Combination of Digital and Analog computers. ICMAP-Shakeel ...
... Analog – Special purpose computer based on continuous data and produce approximate results Digital Computers – General purpose Computers based on discrete date and produce accurate results Hybrid – Combination of Digital and Analog computers. ICMAP-Shakeel ...
Telecommunications - Spruce Creek High School
... A WAN spans a large geographical area and connects networks such as metropolitan area networks, public access networks, value added networks, and virtual private networks together. ...
... A WAN spans a large geographical area and connects networks such as metropolitan area networks, public access networks, value added networks, and virtual private networks together. ...
FOI Memo 5492 Nr 3
... organisational approaches was that we must stick to a precise terminology. In other words, the search was based on the degree of conformity to the term “comprehensive security”. Since that approach produced such scant results, the search was widened one level by scanning for those organisations whos ...
... organisational approaches was that we must stick to a precise terminology. In other words, the search was based on the degree of conformity to the term “comprehensive security”. Since that approach produced such scant results, the search was widened one level by scanning for those organisations whos ...
William Stallings Data and Computer Communications
... "All members of the UCSC community have an explicit responsibility to foster an environment of trust, honesty, fairness, respect, and responsibility. All members of the university community are expected to present as their original work only that which is truly their own. All members of the communit ...
... "All members of the UCSC community have an explicit responsibility to foster an environment of trust, honesty, fairness, respect, and responsibility. All members of the university community are expected to present as their original work only that which is truly their own. All members of the communit ...
Getting Security Right in Wireless Sensor Networks
... net infrastructure to everything. WSNs are already in use in critical were sent by a malicious attacker. An extreme monitoring and control applications around the planet. Any loss of example is a message like “here’s a new prosecurity in these systems may have real and direct consequences gram for y ...
... net infrastructure to everything. WSNs are already in use in critical were sent by a malicious attacker. An extreme monitoring and control applications around the planet. Any loss of example is a message like “here’s a new prosecurity in these systems may have real and direct consequences gram for y ...
Tool: Spector CNE Tool: Track4Win
... • It reduces security breaches. • It detects the use of organization resources to engage in illegal or unethical activities. • It limits legal liability (including sexual and racial harassment). • It enforces PC and Internet acceptable-use policies. ...
... • It reduces security breaches. • It detects the use of organization resources to engage in illegal or unethical activities. • It limits legal liability (including sexual and racial harassment). • It enforces PC and Internet acceptable-use policies. ...
A Need for Security. - Simpson Security Papers
... paper and the toner. Common uses for this product are: transcripts, deposit receipts, lottery tickets, estate wills, warranties/guarantees, bank notes, titles, checks, and many more uses. DesignSecure™ – The original decorated safety paper featuring the well-known Basketweave® pattern. This product ...
... paper and the toner. Common uses for this product are: transcripts, deposit receipts, lottery tickets, estate wills, warranties/guarantees, bank notes, titles, checks, and many more uses. DesignSecure™ – The original decorated safety paper featuring the well-known Basketweave® pattern. This product ...
Microsoft Azure Overview - Purdue University :: Computer Science
... Idle connection culling Generated server names ...
... Idle connection culling Generated server names ...
Abstract - Compassion Software Solutions
... Malicious URLs have been widely used to mount various cyber attacks including spamming, phishing and malware. Phishing is a security attack that involves obtaining sensitive or otherwise private data by presenting oneself as a trustworthy entity. Phishes often exploit users’ trust on the appearance ...
... Malicious URLs have been widely used to mount various cyber attacks including spamming, phishing and malware. Phishing is a security attack that involves obtaining sensitive or otherwise private data by presenting oneself as a trustworthy entity. Phishes often exploit users’ trust on the appearance ...
Security
... System design should be public Default should be n access Check for current authority Give each process least privilege possible Protection mechanism should be ...
... System design should be public Default should be n access Check for current authority Give each process least privilege possible Protection mechanism should be ...
Hacking Overview - Computer Engineering
... IP Address Spoofing: Send out IP packages with false IP addresses. If an attacker sits on a link through which traffic between two sites flows, the attacker can inject spoofed packages to “hijack the session”. Attacker inserts commands into the connection. Details omitted. ...
... IP Address Spoofing: Send out IP packages with false IP addresses. If an attacker sits on a link through which traffic between two sites flows, the attacker can inject spoofed packages to “hijack the session”. Attacker inserts commands into the connection. Details omitted. ...
Security - Glasnost
... System design should be public Default should be n access Check for current authority Give each process least privilege possible Protection mechanism should be ...
... System design should be public Default should be n access Check for current authority Give each process least privilege possible Protection mechanism should be ...
Presentation
... • The Network Opera4ons Centers Provide a variety of services. The Chennai server, for example provides Billing and Authen4ca4on Services, NMS services monitoring devices across our hotels as ...
... • The Network Opera4ons Centers Provide a variety of services. The Chennai server, for example provides Billing and Authen4ca4on Services, NMS services monitoring devices across our hotels as ...