10 March 2009 - Computer Science
... algorithm used and then together with the recovered session key to decrypt to plain text. Of course the algorithm used for encryption is dependant on the protocol used and the algorithms that were negotiated between client and server. Investigate sensible means to store symmetric keys for later use. ...
... algorithm used and then together with the recovered session key to decrypt to plain text. Of course the algorithm used for encryption is dependant on the protocol used and the algorithms that were negotiated between client and server. Investigate sensible means to store symmetric keys for later use. ...
Security - Computer Science Department
... “Information Security and Externalities” Chapter 1 of “Security Engineering” ...
... “Information Security and Externalities” Chapter 1 of “Security Engineering” ...
Vocabulary words with definitions
... to a computer to display information to an audience. The most common devices are video projection units and video converters for television monitor. Database: A collection or listing of information, usually organized with searchable elements or fields. For example, a library catalog can be searched ...
... to a computer to display information to an audience. The most common devices are video projection units and video converters for television monitor. Database: A collection or listing of information, usually organized with searchable elements or fields. For example, a library catalog can be searched ...
introduction to the course
... • Students will learn more about system administration. This is more important than hardware. On a free operating system, we can justify covering it. • Learning by doing gets across some important concepts used in the software. • Linux and X11 can have a bad time working with hardware. Hardware know ...
... • Students will learn more about system administration. This is more important than hardware. On a free operating system, we can justify covering it. • Learning by doing gets across some important concepts used in the software. • Linux and X11 can have a bad time working with hardware. Hardware know ...
The United States Secret Service - Federal Reserve Bank of San
... The Director of the United States Secret Service shall take appropriate actions ...
... The Director of the United States Secret Service shall take appropriate actions ...
2 marks - KV Institute of Management and Information Studies
... owner of BillClinton.com, for example, the real former president cannot legally use his own name as a domain. He would have to pursue a lawsuit to compel the cybersquatter to relinquish the name, or actually pay whatever price the current owner assigns. Until a federal AntiCybersquatting Consumer Pr ...
... owner of BillClinton.com, for example, the real former president cannot legally use his own name as a domain. He would have to pursue a lawsuit to compel the cybersquatter to relinquish the name, or actually pay whatever price the current owner assigns. Until a federal AntiCybersquatting Consumer Pr ...
INFORMATION TECHNOLOGY CONCEPTS (54)
... the statement is True; mark Column B if the statement is False. 1. ROM is memory that can be both read and written to. 2. You can increase your computer’s memory capacity by adding an additional hard drive. 3. A company can connect to a branch office in another state by using a LAN. 4. A network int ...
... the statement is True; mark Column B if the statement is False. 1. ROM is memory that can be both read and written to. 2. You can increase your computer’s memory capacity by adding an additional hard drive. 3. A company can connect to a branch office in another state by using a LAN. 4. A network int ...
Be my host: What to ask about free services that may be hosting your
... The increasing use of third-party file-hosting services raises at least three questions worth considering BY RICHARD MARTINEZ, SAMUEL WALLING Traditionally, privacy and cybersecurity efforts have focused on how companies can protect their IT assets from intrusion. Literally billions of dollars have ...
... The increasing use of third-party file-hosting services raises at least three questions worth considering BY RICHARD MARTINEZ, SAMUEL WALLING Traditionally, privacy and cybersecurity efforts have focused on how companies can protect their IT assets from intrusion. Literally billions of dollars have ...
Hacking
... Applications on a system use ports to listen for network traffic or send it out. 216 ports available, some for known services such as http (80), ftp, ... Port scans send various type of IP packages to target on different ports. Reaction tells them whether the port is open (an application liste ...
... Applications on a system use ports to listen for network traffic or send it out. 216 ports available, some for known services such as http (80), ftp, ... Port scans send various type of IP packages to target on different ports. Reaction tells them whether the port is open (an application liste ...
Class2
... A LAN is usually owned by one organization, but a WAN often connects different groups in different countries ...
... A LAN is usually owned by one organization, but a WAN often connects different groups in different countries ...
Chap 9 - IUP Personal Websites
... incoming/outgoing packets and letting them pass or not based on IP addresses of source and destination ...
... incoming/outgoing packets and letting them pass or not based on IP addresses of source and destination ...
User Threat Quotient Brochure
... In its current phase, Cyberoam s User Threat Quotient (UTQ) studies the web behavior of users by analyzing massive data of allowed and denied web traf c for web categories like IP Address, P2P, Phishing and Fraud, Porn, SPAM URL, Spyware, URL Translation Sites and more that pose security and legal r ...
... In its current phase, Cyberoam s User Threat Quotient (UTQ) studies the web behavior of users by analyzing massive data of allowed and denied web traf c for web categories like IP Address, P2P, Phishing and Fraud, Porn, SPAM URL, Spyware, URL Translation Sites and more that pose security and legal r ...
User Threat Quotient (UTQ)
... In its current phase, Cyberoam s User Threat Quotient (UTQ) studies the web behavior of users by analyzing massive data of allowed and denied web traf c for web categories like IP Address, P2P, Phishing and Fraud, Porn, SPAM URL, Spyware, URL Translation Sites and more that pose security and legal r ...
... In its current phase, Cyberoam s User Threat Quotient (UTQ) studies the web behavior of users by analyzing massive data of allowed and denied web traf c for web categories like IP Address, P2P, Phishing and Fraud, Porn, SPAM URL, Spyware, URL Translation Sites and more that pose security and legal r ...
Cyber Solutions for NEI 08-09 Whitepaper 119 KB
... The SecurityST Active Directory user and management functions can be used to limit functions for operators while enabling security functions for administrative users only. There is physical partitioning in the network levels between the Control Network (UDH) and the Supervisory Network (PDH). In add ...
... The SecurityST Active Directory user and management functions can be used to limit functions for operators while enabling security functions for administrative users only. There is physical partitioning in the network levels between the Control Network (UDH) and the Supervisory Network (PDH). In add ...
5.advantages and disadvantages
... highlight the benefits of HAN technology to facilitate its adoption. Not useful unless many people adopt it. It can be useful within few centimeters only. ...
... highlight the benefits of HAN technology to facilitate its adoption. Not useful unless many people adopt it. It can be useful within few centimeters only. ...
Senior Systems Administrator - Texarkana Independent School District
... 11. Oversee installation, configuration, maintenance, and troubleshooting of network hardware, software, and peripheral devices. 12. Manage and/or provide guidance to junior members of the team. 13. Conduct research on network products, services, protocols, and standards in support of network procur ...
... 11. Oversee installation, configuration, maintenance, and troubleshooting of network hardware, software, and peripheral devices. 12. Manage and/or provide guidance to junior members of the team. 13. Conduct research on network products, services, protocols, and standards in support of network procur ...
shuffling:improving data security in ad hoc networks based
... often than to other nodes, the attacker will be able to expect that the node is important for the network, and disabling it could bring the entire network down. Unlike passive attacks, active attacks are often detectable. An active attack can mainly be: Blackhole attack, where a malicious node uses ...
... often than to other nodes, the attacker will be able to expect that the node is important for the network, and disabling it could bring the entire network down. Unlike passive attacks, active attacks are often detectable. An active attack can mainly be: Blackhole attack, where a malicious node uses ...
Mark Boyer - Methods of securing data in window networks
... The process of securing data in windows networks is a very important task, especially if you are involved with a company or business. The loss or theft of data from a top secret sector of a company could be catastrophic. Items such as people’s personal files, bank account information, and things of ...
... The process of securing data in windows networks is a very important task, especially if you are involved with a company or business. The loss or theft of data from a top secret sector of a company could be catastrophic. Items such as people’s personal files, bank account information, and things of ...
Visualizing Threats: Improved Cyber Security Through Network
... The applications built using KeyLines run in virtually any web browser and any device. A flexible architecture means they can be deployed into existing IT environments, as part of a dashboard or as standalone tools. Data can be pulled from multiple sources and interactive charts can be ...
... The applications built using KeyLines run in virtually any web browser and any device. A flexible architecture means they can be deployed into existing IT environments, as part of a dashboard or as standalone tools. Data can be pulled from multiple sources and interactive charts can be ...
Chapter07
... 19. What is a rootkit and how does it work? A rootkit is a set of software tools used by an attacker to break into a computer and obtain special operating system privileges in order to both perform unauthorized functions and also hide all traces of its existence. A rootkit often includes several pro ...
... 19. What is a rootkit and how does it work? A rootkit is a set of software tools used by an attacker to break into a computer and obtain special operating system privileges in order to both perform unauthorized functions and also hide all traces of its existence. A rootkit often includes several pro ...
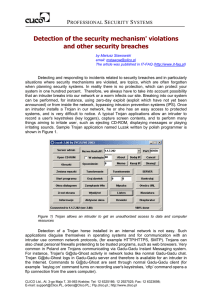
Detection of the security mechanism` violations and other
... detection break-ins (i.e. attacks resulting in unauthorized control over the system) and explaining security breaches. The analysis of events logged by IDP/IDS systems is difficult because Internet worms generate many attacks and therefore well-thought-of intruders' attacks can go unspotted. The ana ...
... detection break-ins (i.e. attacks resulting in unauthorized control over the system) and explaining security breaches. The analysis of events logged by IDP/IDS systems is difficult because Internet worms generate many attacks and therefore well-thought-of intruders' attacks can go unspotted. The ana ...
Rimini Street Technology Solution Brief-Oracle Security-LT
... browser plugins, and PCI tokenizing — keep core systems operating while enabling necessary changes in the business environment. To address security concerns, you can utilize compensating controls, such as application firewalls that provide “virtual patching” capabilities. Instead of manually finding a ...
... browser plugins, and PCI tokenizing — keep core systems operating while enabling necessary changes in the business environment. To address security concerns, you can utilize compensating controls, such as application firewalls that provide “virtual patching” capabilities. Instead of manually finding a ...
Robust. Reliable. Factory Line. Industrial Security redefined protecting industrial networks
... (QoS) functionalities and helps with intrusion detection and antivirus protection. The mGuard portfolio is complemented by a highly scalable device management software. Innominate products are marketed worldwide under the mGuard brand through system integrators and OEM partners. Further information ...
... (QoS) functionalities and helps with intrusion detection and antivirus protection. The mGuard portfolio is complemented by a highly scalable device management software. Innominate products are marketed worldwide under the mGuard brand through system integrators and OEM partners. Further information ...
Management Information Systems
... Less powerful and less expensive than supercomputers Used by businesses with large amounts of data that need to be stored in a central computer ...
... Less powerful and less expensive than supercomputers Used by businesses with large amounts of data that need to be stored in a central computer ...
General Assembly 1 Background Guide
... enterprise, and government operations all rely on technology; all manner of weapons systems, including drones and nuclear weapons, are controlled by networks that could be subject to hacking and attacks. Sensitive government information is also often stored online and past leaks have put numerous in ...
... enterprise, and government operations all rely on technology; all manner of weapons systems, including drones and nuclear weapons, are controlled by networks that could be subject to hacking and attacks. Sensitive government information is also often stored online and past leaks have put numerous in ...