Are Clouds Secure? - San Francisco Bay Area ISSA Chapter
... are not impacted by ‘cloud computing’ • There are plenty of existing sources of useful information about information security, and we will not attempt to recreate those sources, nor ...
... are not impacted by ‘cloud computing’ • There are plenty of existing sources of useful information about information security, and we will not attempt to recreate those sources, nor ...
Are Clouds Secure?
... are not impacted by ‘cloud computing’ • There are plenty of existing sources of useful information about information security, and we will not attempt to recreate those sources, nor ...
... are not impacted by ‘cloud computing’ • There are plenty of existing sources of useful information about information security, and we will not attempt to recreate those sources, nor ...
Term Simple Definition Advanced Definition Absorption (RF
... of the wireless signal, position the access point above any large objects in the area. An adjustment of the antennas may be necessary. An internetworking device that seamlessly connects wired and wireless networks. Access A device that provides wireless points combined with a Access Point (AP) clien ...
... of the wireless signal, position the access point above any large objects in the area. An adjustment of the antennas may be necessary. An internetworking device that seamlessly connects wired and wireless networks. Access A device that provides wireless points combined with a Access Point (AP) clien ...
Network Connection Guide
... I can’t get my hardware to connect to the Network (middle light remains red or flashing red). Check the network Name and Password to make sure they were entered properly (no special characters) and make sure lower/upper case have been accounted for. To connect in network mode, SkyTrak requires a 2.4 ...
... I can’t get my hardware to connect to the Network (middle light remains red or flashing red). Check the network Name and Password to make sure they were entered properly (no special characters) and make sure lower/upper case have been accounted for. To connect in network mode, SkyTrak requires a 2.4 ...
Theme 1: Let`s start with the basics
... be used without having to boost the signal is 100m. UTP is sensitive to eavesdropping although the twisting does help reduce the ...
... be used without having to boost the signal is 100m. UTP is sensitive to eavesdropping although the twisting does help reduce the ...
Competency: Defend and Attack (virus, spam, spyware - FBLA-PBL
... 16. Develop and document a plan to avoid data loss, including backups and remote storage. Competency: Physical Security Tasks 1. Define physical security. 2. Identify names, purposes, and characteristics of hardware and software security issues including wireless, data, and physical security. 3. Des ...
... 16. Develop and document a plan to avoid data loss, including backups and remote storage. Competency: Physical Security Tasks 1. Define physical security. 2. Identify names, purposes, and characteristics of hardware and software security issues including wireless, data, and physical security. 3. Des ...
U N I T
... As sensor nodes must be low power, their hardware design will tradeoff computation capabilities for lower power consumption. As such, the nodes will have limited processing power and memory resources. An operating system for sensor networks should deliver the required application services without us ...
... As sensor nodes must be low power, their hardware design will tradeoff computation capabilities for lower power consumption. As such, the nodes will have limited processing power and memory resources. An operating system for sensor networks should deliver the required application services without us ...
Document
... cable, coaxial cable, fiber-optic cable, and wireless links. • Each node uses a special device, called a network interface card (NIC). The card connects to the network media and controls the flow of data. • NICs must use a common network technology to communicate. The most popular network technologi ...
... cable, coaxial cable, fiber-optic cable, and wireless links. • Each node uses a special device, called a network interface card (NIC). The card connects to the network media and controls the flow of data. • NICs must use a common network technology to communicate. The most popular network technologi ...
Connecting your Blu-ray Disc™ / DVD Player to your
... – I do not know whether my wireless LAN router is compatible with Wi-Fi Protected Setup (WPS). – I cannot find the instruction manuals of the wireless LAN router. Consult the manufacturer of the wireless LAN router. – I am not sure whether my Wi-Fi network is secure. – How can I show the Wi-Fi ...
... – I do not know whether my wireless LAN router is compatible with Wi-Fi Protected Setup (WPS). – I cannot find the instruction manuals of the wireless LAN router. Consult the manufacturer of the wireless LAN router. – I am not sure whether my Wi-Fi network is secure. – How can I show the Wi-Fi ...
IOSR Journal of Computer Engineering (IOSR-JCE) e-ISSN: 2278-0661, p-ISSN: 2278-8727 PP 00-00 www.iosrjournals.org
... route discovery, or target TCP acknowledgments in a TCP session to severely degrade the throughput of an endto-end flow. To address this problem we proposed two schemes that provide encryption techniques to hide the packets from jammer. And packets are delivered to receiver and with confidentiality ...
... route discovery, or target TCP acknowledgments in a TCP session to severely degrade the throughput of an endto-end flow. To address this problem we proposed two schemes that provide encryption techniques to hide the packets from jammer. And packets are delivered to receiver and with confidentiality ...
SinoCDN LinkEasy Solution
... • The benefits of this deployment for Telecom Carrier are – The account administrative functions of LE-2000 can be kept within the LAN, thus it will not be affected even if the WAN link is congested or disconnected – For VLAN configuration, deploying LE-2000 in Hotel/Property premises would allow fl ...
... • The benefits of this deployment for Telecom Carrier are – The account administrative functions of LE-2000 can be kept within the LAN, thus it will not be affected even if the WAN link is congested or disconnected – For VLAN configuration, deploying LE-2000 in Hotel/Property premises would allow fl ...
Information Security Policies and Standards
... resources in accordance with the Least Privilege Principle. ...
... resources in accordance with the Least Privilege Principle. ...
The Infrastructure Technologies
... IP address allocated dynamically at login time Must use a protocol such as Dynamic Host ...
... IP address allocated dynamically at login time Must use a protocol such as Dynamic Host ...
Network Use Policy UPPS No. 04.01.05
... 03.06 Interference – degradation of network communication signal due to electrical pulses or electromagnetic radiation from an external source. 03.07 Internet – A global computer network providing a variety of information and communication facilities, consisting of interconnected networks using sta ...
... 03.06 Interference – degradation of network communication signal due to electrical pulses or electromagnetic radiation from an external source. 03.07 Internet – A global computer network providing a variety of information and communication facilities, consisting of interconnected networks using sta ...
MIS 301 - Pervasive E
... Smartphones. Internet-enabled cell phones that support mobile applications. Wi-Fi (Wireless Fidelity). 802.11b standard which means most of the wireless local area networks. Global positioning system (GPS) . A satellite based tracking system determines a GPS device’s location. WLAN. Wireless local a ...
... Smartphones. Internet-enabled cell phones that support mobile applications. Wi-Fi (Wireless Fidelity). 802.11b standard which means most of the wireless local area networks. Global positioning system (GPS) . A satellite based tracking system determines a GPS device’s location. WLAN. Wireless local a ...
The University of Oklahoma Virtual Private Network
... Provides type of firewall by hiding internal IP addresses. Enables a company to use more internal IP addresses. Since they're used internally only, there's no possibility of conflict with IP addresses used by other companies and organizations. Allows a company to combine multiple ISDN connections in ...
... Provides type of firewall by hiding internal IP addresses. Enables a company to use more internal IP addresses. Since they're used internally only, there's no possibility of conflict with IP addresses used by other companies and organizations. Allows a company to combine multiple ISDN connections in ...
physcial_sci_networks_part1
... have to do with making sure that when a sender sends a 1 bit that the receiver receives a 1 bit and not a 0 bit. • Example issues to be agreed when building this layer – How many volts to represent a 1 – How many volts to represent a 0 – How many microseconds a bit lasts. – Does transmission proceed ...
... have to do with making sure that when a sender sends a 1 bit that the receiver receives a 1 bit and not a 0 bit. • Example issues to be agreed when building this layer – How many volts to represent a 1 – How many volts to represent a 0 – How many microseconds a bit lasts. – Does transmission proceed ...
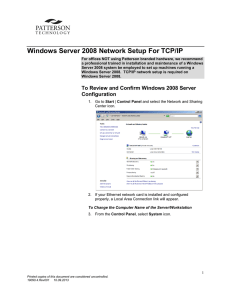
Windows Server 2008 Network Setup For TCP/IP
... Windows Server 2008 Network Setup For TCP/IP For offices NOT using Patterson branded hardware, we recommend a professional trained in installation and maintenance of a Windows Server 2008 system be employed to set up machines running a Windows Server 2008. TCP/IP network setup is required on Windows ...
... Windows Server 2008 Network Setup For TCP/IP For offices NOT using Patterson branded hardware, we recommend a professional trained in installation and maintenance of a Windows Server 2008 system be employed to set up machines running a Windows Server 2008. TCP/IP network setup is required on Windows ...
The Internet of Things - Fab Central
... so. The code to run IP can be squeezed into a few kilobytes and run on a one-dollar microcontroller. The IP information adds about 100 bits to each message, which typically has a negligible impact on the response time and power requirements. In return for this modest overhead, the network avoids the ...
... so. The code to run IP can be squeezed into a few kilobytes and run on a one-dollar microcontroller. The IP information adds about 100 bits to each message, which typically has a negligible impact on the response time and power requirements. In return for this modest overhead, the network avoids the ...
Network - Blog Universitas Udayana
... – Analyzes packets and routes directly to destination port – More efficient than hub ...
... – Analyzes packets and routes directly to destination port – More efficient than hub ...
Chapter 1
... Size and Portability (large vs. small) Ability to Avoid Physical Contact (lots vs. little) Value of Asset (very high vs. variable) Network Security / G. Steffen ...
... Size and Portability (large vs. small) Ability to Avoid Physical Contact (lots vs. little) Value of Asset (very high vs. variable) Network Security / G. Steffen ...
Chapter 1
... Size and Portability (large vs. small) Ability to Avoid Physical Contact (lots vs. little) Value of Asset (very high vs. variable) Network Security / G. Steffen ...
... Size and Portability (large vs. small) Ability to Avoid Physical Contact (lots vs. little) Value of Asset (very high vs. variable) Network Security / G. Steffen ...
A Comparative Study of Wireless Technologies: Zigbee, Bluetooth
... IEEE standard. As compared to other technologies UWB has one of its unique features is that its signal is pass though through doors and obstacles. All these six protocols have authentication mechanisms in which Zigbee, wavenis and UWB uses advanced encryption method whereas Bluetooth LE uses E0 stre ...
... IEEE standard. As compared to other technologies UWB has one of its unique features is that its signal is pass though through doors and obstacles. All these six protocols have authentication mechanisms in which Zigbee, wavenis and UWB uses advanced encryption method whereas Bluetooth LE uses E0 stre ...
Policy Template
... volunteers; or suspension or expulsion in the case of a student. Additionally, individuals are subject to loss of [AGENCY] Information Resources access privileges, civil, and criminal prosecution. ...
... volunteers; or suspension or expulsion in the case of a student. Additionally, individuals are subject to loss of [AGENCY] Information Resources access privileges, civil, and criminal prosecution. ...
Performance Evaluation of VoIP and TCP over wireless networks
... performance problems in voip over 802.11 wireless lan 1 , IEEE transactions on vehicular technology, vol. 54, no. 1, january 2005. • Mirko Franceschinis, Marco Mellia, Michela Meo, and Maurizio Munafo. Measuring TCP over WiFi: A real case. Proceedings of the First ...
... performance problems in voip over 802.11 wireless lan 1 , IEEE transactions on vehicular technology, vol. 54, no. 1, january 2005. • Mirko Franceschinis, Marco Mellia, Michela Meo, and Maurizio Munafo. Measuring TCP over WiFi: A real case. Proceedings of the First ...
Wireless security
.jpg?width=300)
Wireless security is the prevention of unauthorized access or damage to computers using wireless networks. The most common types of wireless security are Wired Equivalent Privacy (WEP) and Wi-Fi Protected Access (WPA). WEP is a notoriously weak security standard. The password it uses can often be cracked in a few minutes with a basic laptop computer and widely available software tools. WEP is an old IEEE 802.11 standard from 1999, which was outdated in 2003 by WPA, or Wi-Fi Protected Access. WPA was a quick alternative to improve security over WEP. The current standard is WPA2; some hardware cannot support WPA2 without firmware upgrade or replacement. WPA2 uses an encryption device that encrypts the network with a 256-bit key; the longer key length improves security over WEP.Many laptop computers have wireless cards pre-installed. The ability to enter a network while mobile has great benefits. However, wireless networking is prone to some security issues. Hackers have found wireless networks relatively easy to break into, and even use wireless technology to hack into wired networks. As a result, it is very important that enterprises define effective wireless security policies that guard against unauthorized access to important resources. Wireless Intrusion Prevention Systems (WIPS) or Wireless Intrusion Detection Systems (WIDS) are commonly used to enforce wireless security policies.The risks to users of wireless technology have increased as the service has become more popular. There were relatively few dangers when wireless technology was first introduced. Hackers had not yet had time to latch on to the new technology, and wireless networks were not commonly found in the work place. However, there are many security risks associated with the current wireless protocols and encryption methods, and in the carelessness and ignorance that exists at the user and corporate IT level. Hacking methods have become much more sophisticated and innovative with wireless access. Hacking has also become much easier and more accessible with easy-to-use Windows- or Linux-based tools being made available on the web at no charge.Some organizations that have no wireless access points installed do not feel that they need to address wireless security concerns. In-Stat MDR and META Group have estimated that 95% of all corporate laptop computers that were planned to be purchased in 2005 were equipped with wireless cards. Issues can arise in a supposedly non-wireless organization when a wireless laptop is plugged into the corporate network. A hacker could sit out in the parking lot and gather information from it through laptops and/or other devices, or even break in through this wireless card–equipped laptop and gain access to the wired network.