* Your assessment is very important for improving the workof artificial intelligence, which forms the content of this project
Download Network - Blog Universitas Udayana
Survey
Document related concepts
Deep packet inspection wikipedia , lookup
Wireless security wikipedia , lookup
Registered jack wikipedia , lookup
Internet protocol suite wikipedia , lookup
Distributed firewall wikipedia , lookup
Recursive InterNetwork Architecture (RINA) wikipedia , lookup
Wake-on-LAN wikipedia , lookup
Computer network wikipedia , lookup
Piggybacking (Internet access) wikipedia , lookup
Network tap wikipedia , lookup
Airborne Networking wikipedia , lookup
Transcript
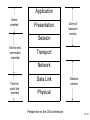
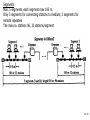
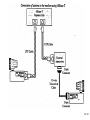
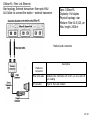
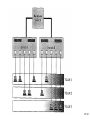
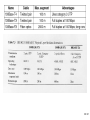
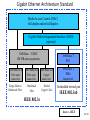
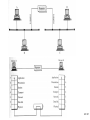
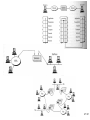
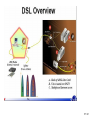
Network Minggu ke – 9 Magister Teknik Elektro Universitas Udayana 1 / 61 • What is a Network? – Allows Computers to Communicate – Share Files, Printers and Other Peripherals – Connect to a Centralized Server 2 / 61 3 / 61 • Network Communications and Protocols – Protocol - The definition of a language that allows computers and networks to communicate • OSI Model – Breaks network protocols down into seven different layers. • Computer Protocols – Languages Computers use to communicate across networks • Network Protocols – Languages Networks use to communicate 4 / 61 Network Communications and Protocols Computer Protocols • NetBEUI (NetBIOS Extended User Interface) • • • • Microsoft Windows File and Printer Sharing Easiest to Setup Works Best on Small Networks – Less Than 25 Computers • Large Networks Require WINS Server • Alternative is NetBIOS over TCP/IP • IPX/SPX and NWLink (NetWare) • Allows Windows computers to communicate with Novell based networks • Available as of Windows 95 and NT 4.0 5 / 61 • TCP/IP – – – – Most widely used protocol today Protocol used across the Internet hence IP Packet based IP Based Networks • • • • • IP Addresses Subnet Masks Gateway DHCP (Dynamic Host Configuration Protocol )Server DNS Server 6 / 61 • Public IP Addresses – Given out in “Blocks” – Computers with Public IP addresses can be directly accessed from the Internet – Poses Potential Security Risk 7 / 61 • Private IP Addresses – Can not directly connect to the Internet – Translated to public IP address prior to sending data on the Internet – Free for anyone to use 8 / 61 • TCP/IP : IP Addresses – – – – Dynamic vs. Static Subnet Mask Gateway DNS Server 9 / 61 10 / 61 11 / 61 Subnetting A Network with two levels of hierarchy (not subnetted) 12 / 61 A Network with three levels of hierarchy (subnetted) 13 / 61 ARP (Address Resolution Protocol) 14 / 61 • Cross Platform Communications – Linux / Unix / Mac OS X • Samba – Allows these operating systems to use the NetBIOS Protocol to communicate with Windows operating systems – Windows • Services for Unix (SFU) – Allows Windows operating systems to use the NFS protocol to communicate with Linux / Unix operating systems 15 / 61 • OSI Model – Breaks network protocols down into seven different layers. • Protocol functions • • • • • • • Segmentation and reassembly Encapsulation Addressing Connection control Multiplexing Ordered delivery Transmission services Flow control Error control synchronization • Computer Protocols – Languages Computers use to communicate across networks • Network Protocols – Languages Networks use to communicate 16 / 61 Layer 17 / 61 Application Usersoriented Presentation Users of transport service Session End-to-end connection oriented Transport Network Data Link Point-topoint link oriented Network service Physical Perspective on the OSI architecture 18 / 61 19 / 61 O P E R A T I N G s y s t e m Applications TCP IP Network Access protocol 20 / 61 21 / 61 22 / 61 Network Protocol • Token Ring – Backbone for large ring topologies – Uses special packet called a Token – Computer holding token allowed to communicate on network • Ethernet – • Designed for LAN technologies - Bus topology; Fast Ethernet: 100 Mbps; Gigabits Ethernet: 1000 Mbps – • Listens to network before transmission – • Uses random wait times to resolve collisions – • Not limited to Ring Topology 23 / 61 24 / 61 • Ethernet implementations 10Base5: Thick Ethernet or Thicknet 25 / 61 26 / 61 10Base2: Thin Ethernet or Cheapernet It uses bus topology with an internal transceiver or p2p connection via an external transceiver. If the station uses an internal transceiver, there is no need for an AUI cable If the station lacks a transceiver, then an external transceiver can be used in conjunction with the AUI 27 / 61 Segments Max. 5 segments, each segment max 185 m. Only 3 segments for connecting stations to medium; 2 segments for remote repeaters The max.no. stations 96, 32 stations/segment 28 / 61 Medium & Connectors Descriptions Thin coaxial cable Spec. in table BNC-type coaxial connectors For the end of each segment BNC-type barrel connector To connect 2 sections of a segment together BNC-type terminators 50-ohm terminator BNC-type tee connectors To connect the medium to the external transceiver or to the NIC 29 / 61 30 / 61 10Base-T: Twisted-Pair Ethernet Physically is star topology, logically is bus topology The stations are connected to a hub with either an internal or external transceiver Internal transceiver: no need AUI cable External transceiver: AUI cable for connecting the transceiver – interface Medium & connectors: twisted-pair cable and RJ-45 connectors 31 / 61 32 / 61 10Base-FL: Fiber Link Ethernet Star topology, External transceiver: fiber-optic MAU AUI Cable: to connect the station – external transceiver Spec. 10Base-FL: Duplexity: Full-duplex Physical topology: star Medium: Fiber 62.5/125 m Max. length: 2000 m Medium and connectors Descriptions Medium & Connectors Fiber optic cable Graded index multimode with a 62.5 m core and 125 m cladding ST connector Type for fiber-optic medium 33 / 61 VLAN (Virtual Local Area Network) A subnetwork or a segment of a local area network configured by software, not by physical wiring 34 / 61 35 / 61 VPN (Virtual Private Network) A network that is private, but virtual It is private because it guarantees privacy inside the organization. It is virtual because it does not use real private WANs; the network is physically public, but virtually private 36 / 61 37 / 61 38 / 61 Network Fast Ethernet 39 / 61 Gigabit Ethernet Architecture Standard Media Access Control (MAC) full duplex and/or half duplex Gigabit Media Independent Interface (GMII) (optional) 1000 Base – X PHY 8B/10B auto-negotiation 1000 Base-LX 1000 Base T PCS 1000 Base-SX 1000 Base-CX Fiber optic transceiver Fiber optic transceiver Copper transceiver Single Mode or Multimode Fiber Multimode Fiber Shieled Copper Cable 1000 Base T PMA transceiver Unshielded twisted pair IEEE 802.3ab IEEE 802.3z Source - IEEE 40 / 61 Gigabit Ethernet Technology Figure 4-23.Gigabit Ethernet cabling. 1000 BASE SX fiber - short wavelength 1000 BASE LX fiber - long wavelength 1000 BASE CX copper - shielded twisted pair 1000 BASE T copper - unshielded twisted pair * Based on Fiber Channel physical signaling technology. 41 / 61 Network Hardware 42 / 61 43 / 61 44 / 61 45 / 61 46 / 61 47 / 61 48 / 61 Network Hardware • NIC – Network Interface Card • Cabling – – – – Cat 5 Cat 5e Cat 6 Fiber Optic • Hub or Repeater – Repeats information out to all ports – Creates unnecessary network traffic – Least sophisticated of all network equipment • Switch – Analyzes packets and routes directly to destination port – More efficient than hub 49 / 61 Network Hardware • Router – More sophisticated than Switch – Knows what type of traffic – Can be used as first line of defense when securing a network • Firewall – Not only knows type of traffic, but analyzes traffic for potential vulnerabilities. – Rule based analysis 50 / 61 • WAP – Wireless Access Point – – – – – Slower than traditional wired networks Great for open spaces Quickly reduces distances inside buildings Can reach over a few miles with proper equipment Less expensive than wired counterparts 51 / 61 Internet Connection • Types of Connections – Dial Up • Slow • Maximum Throughput 50Kbps – Satellite • • Available even in rural areas • • Long response times (Latency) • • Maximum Throughput 50Kbps up and 400Kbps down 52 / 61 – DSL / Cable • • Increase speeds as needed • • Requires Phone Company or Cable Company Support – T1 • • Maximum throughput 1,500 Kbps 53 / 61 xDSL 54 / 61 55 / 61 56 / 61 57 / 61 58 / 61 59 / 61 60 / 61 Network Security • • • • Firewalls Router VPN – Virtual Private Networking Wireless - WiFi – WEP – Wireless Encryption Protocol – WPA – WiFi Protected Access – Ethernet Address Lockdown • Physical Security 61 / 61