* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download computer networking
Computer security wikipedia , lookup
Wireless security wikipedia , lookup
Deep packet inspection wikipedia , lookup
Recursive InterNetwork Architecture (RINA) wikipedia , lookup
Computer network wikipedia , lookup
Piggybacking (Internet access) wikipedia , lookup
Wake-on-LAN wikipedia , lookup
Airborne Networking wikipedia , lookup
Distributed firewall wikipedia , lookup
Network tap wikipedia , lookup
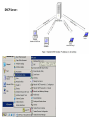
Al AlBayt University Computer Networking Presented by: Eng. Gader Al-khawaldeh Network Engineer Computer Center [email protected] COMPUTER NETWORKING: A computer network, often simply referred to as a network, is a collection of computers and devices connected by communications channels that facilitates communications among users and allows users to share resources with other users. Networks may be classified according to a wide variety of characteristics. This article provides a general overview of types and categories and also presents the basic components of a network. History: Back the beginnings of the Internet to the year 1969, when I felt and Advanced Research Projects Agency at the Pentagon Defense Advanced Research Projects Agency (DARPA) and the need to develop a means for the exchange of information between the secret research institution researchers scattered in places as far apart. The solution was to establish a computer network linking they by four computers, called a large network Apranet, and number of nodes of the network is rising rapidly to become a computer 37 node. After a brief set up another network called the military network Milnet to follow up on military research secret, as has the U.S. National Science National Science Foundation (NSF) in 1984, the establishment of centers of computers high-performance supercomputers and put at the disposal of universities to take advantage of the resources of those universities and take advantage of these universities the capacity of supercomputers in academic research. There is a need then to link these centers with each other on the one hand and universities on the other hand, it was not necessary to use the network Apranet or equivalent for this purpose, but this use is not possible, prompting the body to create its own network I called «Network Authority National Science »NSFNET. In 1987, relied on telephone lines for communication between networks instead of a network the National Science NSF, and has since begun the process of opening the network for users other than academics. And the increasing breadth of this network has become even at the beginning of the nineties of the twentieth century, a global network known today as the «Internet». Network Devices:Network devices are components used to connect computers or other electronic devices together so that they can share files or resources like printers or fax machines. 1-Router 2-Switche 3-Firewall 4-Cabling 5- Network card Router :• In packet-switched networks such as the Internet, a router is a device or, in some cases, software in a computer, that determines the next network point to which a packet should be forwarded toward its destination. • The router is connected to at least two networks and decides which way to send each information packet based on its current understanding of the state of the networks it is connected to. • A router is located at any gateway (where one network meets another), including each point-of-presence on the Internet • A router may create or maintain a table of the available routes and their conditions and use this information along with distance and cost algorithms to determine the best route for a given packet. • Typically, a packet may travel through a number of network points with routers before arriving at its destination. • Routing is a function associated with the Network layer (layer 3) in the standard model of network programming IP: Internet Protocol Short for Internet Protocol, IP is an address of a computer or other network device on a network using IP or TCP/IP. For example, the number "166.70.10.23" is an example of such an address. These addresses are similar to an addresses used on a house and is what allows data to reach the appropriate destination on a network. There are five classes of available IP ranges: Class A, Class B, Class C, Class D and Class E, while only A, B and C are commonly used. Each class allows for a range of valid IP addresses. Class Address Range Subnet Masking Supports Class A 1.0.0.1 to 126.255.255.254 255.0.0.0 Supports 16 million hosts on each of 127 networks. Class B 128.1.0.1 to 191.255.255.254 255.255.0.0 Supports 65,000 hosts on each of 16,000 networks. Class C 192.0.1.1 to 223.255.254.254 255.255.255.0 Supports 254 hosts on each of 2 million networks. Private and Public IP Addresses Private IP: Is IP address space for private internets (local networks): Class A :10.0.0.0 - 10.255.255.255 Class B :172.16.0.0 - 172.31.255.255 Class C :192.168.0.0 - 192.168.255.255 Firewall :• A firewall is a set of related programs, located at a network gateway server, that protects the resources of a private network from users from other networks. (The term also implies the security policy that is used with the programs.) • An enterprise with an intranet that allows its workers access to the wider Internet installs a firewall to prevent outsiders from accessing its own private data resources and for controlling what outside resources its own users have access to. • Basically, a firewall, working closely with a router program, examines each network packet to determine whether to forward it toward its destination. • A number of companies make firewall products. Features include logging and reporting, automatic alarms at given thresholds of attack, and a graphical user interface for controlling the firewall. Switch :• In a telecommunications network, a switch is a device that channels incoming data from any of multiple input ports to the specific output port that will take the data toward its intended destination. • On an Ethernet local area network (LAN), a switch determines from the physical device (Media Access Control or MAC) address in each incoming message frame which output port to forward it to and out of. • In a wide area packet-switched network such as the Internet, a switch determines from the IP address in each packet which output port to use for the next part of its trip to the intended destination. • In the Open Systems Interconnection (OSI) communications model, a switch performs the Layer 2 or Data-link layer function. Network Connection Media used in the university:- •UTP Cable •Fiber Optic Cable UTP cable:• UTP cable is also the most common cable used in computer networking. Modern Ethernet, the most common data networking standard, utilizes UTP cables. • Twisted pair cabling is often used in data networks for short and medium length connections because of its relatively lower costs compared to optical fiber and coaxial cable. • UTP is also finding increasing use in video applications, primarily in security cameras. Most common cable categories Category Bandwidth Applications Notes Cat1 0.4 MHz Telephone and modem lines Not described in EIA/TIA recommmendations. Unsuitable for modern systems. Cat2 ? MHz Older terminal systems, e.g. IBM 3270 Not described in EIA/TIA recommmendations. Unsuitable for modern systems. Cat3 16MHz 10BASE-T and 100BASE-T4 Ethernet Described in EIA/TIA-568. Unsuitable for speeds above 16 Mbit/s. Cat4 20MHz 16 Mbit/s Token Ring Cat5 100MHz 100BASE-TX & 1000BASE-T Ethernet Cat5e 100MHz 100BASE-TX & 1000BASE-T Ethernet Enhanced Cat5. Practically the same as Cat5, but with better testing standards so Gigabit Ethernet works reliably. Cat6 250MHz 1000BASE-T Ethernet Most commonly installed cable in Finland according to the 2002 standard. SFS-EN 50173-1 Cat6e 250MHz (500MHz according to some) 10GBASE-T (under development) Ethernet Not a standard; a cable maker's own label. Cat6a 500MHz 10GBASE-T (under development) Ethernet Standard under development (ISO/IEC 11801:2002 Amendment 2). Cat7 600MHz No applications yet. Four pairs, U/FTP (shielded pairs). Standard under development. 1000MHz Telephone, CATV, 1000BASE-T in the same cable. Four pairs, S/FTP (shielded pairs, braidscreened cable). Standard under development. 1200MHz Four pairs, S/FTP (shielded pairs, braidUnder development, no applications yet. screened cable). Standard under development. Cat7a Cat8 UTP cable:- (cont) Optical Fiber • Optical fiber are mainly used to transmit information over long distances and with high bit rates. Their benefits are numerous: the signal transmitted on the fiber is not disturbed by any electromagnetic wave created by power cables or electric machines. • It also provides more security, as these cables can be fully dielectric. Besides, they provide a weight and space saving due to their small diameter, only 250 μm. • An optical fiber is made up of three main parts: the core, the cladding and the coating. In the center, the “core” is made of doped silica and is surrounded by the “cladding”, made of natural silica. • The light signal propagates along the core and the signal is reflected on the surface between the core and the cladding. Different fiber types • Multimode fiber are used for Local Area Networks (LAN) where the network links can be up to 2,000 meters. Two standard sizes of core are offered: 62.5 μm and 50 μm (with better performances). Multimode fiber have a graded index profile to reduce the dispersion of the signal during the transmission. The high size of the core is interesting for easy connection and does not require high cost test equipment. • Single mode fiber are able to transmit over longer distances. The installation is more delicate as they have a smaller core of 9 μm. This implies more precise connectors and test equipment. St SC MT-RJ LX proxy server:• A server that sits between a client application, such as a Web browser, and a real server. It intercepts all requests to the real server to see if it can fulfill the requests itself. If not, it forwards the request to the real server. • an enterprise that uses the Internet, a proxy server is a server that acts as an intermediary between a workstation user and the Internet so that the enterprise can ensure security, administrative control, and caching service. • A proxy server is associated with or part of a gateway server that separates the enterprise network from the outside network and a firewall server that protects the enterprise network from outside intrusion. proxy server:- DHCP Server:• Short for Dynamic Host Configuration Protocol, a protocol for assigning dynamic IP addresses to devices on a network. • With dynamic addressing, a device can have a different IP address every time it connects to the network. In some systems, the device's IP address can even change while it is still connected. DHCP also supports a mix of static and dynamic IP addresses. • Dynamic addressing simplifies network administration because the software keeps track of IP addresses rather than requiring an administrator to manage the task. This means that a new computer can be added to a network without the hassle of manually assigning it a unique IP address. Many ISPs use dynamic IP addressing for dial-up users. DHCP Server:- DNS Server:• Short for Domain Name System (or Service or Server), an Internet service that translates domain names into IP addresses. Because domain names are alphabetic, they're easier to remember. The Internet however, is really based on IP addresses. • Every time you use a domain name, therefore, a DNS service must translate the name into the corresponding IP address. • For example, the domain name www.example.com might translate to 198.105.232.4 • The DNS system is, in fact, its own network. If one DNS server doesn't know how to translate a particular domain name, it asks another one, and so on, until the correct IP address is returned. DNS Server:- Thank You