Section 5A
... Topology: Physical or logical layout of cables and devices that connect the network nodes Media: wires and cables that carry data from source to destination Bandwidth: amount of data media can ...
... Topology: Physical or logical layout of cables and devices that connect the network nodes Media: wires and cables that carry data from source to destination Bandwidth: amount of data media can ...
Assignment-3
... wide area protocols such as TCP/IP on the Internet A gateway supervises its client devices, gather their data and execute other task ...
... wide area protocols such as TCP/IP on the Internet A gateway supervises its client devices, gather their data and execute other task ...
Document
... transfer of electronic mail File Transfer Protocol (FTP) allows a user to transfer files to and from another computer Telnet used to log onto one computer from another Hyper Text Transfer Protocol (http) allows exchange of Web documents Which of these have you used? ...
... transfer of electronic mail File Transfer Protocol (FTP) allows a user to transfer files to and from another computer Telnet used to log onto one computer from another Hyper Text Transfer Protocol (http) allows exchange of Web documents Which of these have you used? ...
Chapter 15 - KSU Web Home
... transfer of electronic mail File Transfer Protocol (FTP) allows a user to transfer files to and from another computer Telnet used to log onto one computer from another Hyper Text Transfer Protocol (http) allows exchange of Web documents Which of these have you used? ...
... transfer of electronic mail File Transfer Protocol (FTP) allows a user to transfer files to and from another computer Telnet used to log onto one computer from another Hyper Text Transfer Protocol (http) allows exchange of Web documents Which of these have you used? ...
Decision Support System
... The attack is performed in two steps: – 1) from 'visualization station', an unsatisfied employee performs a reprogramming of the sensor that measures the water flow rate in the penstock. In particular a constant water flow rate value is sent to the control center in order to deceive the operator/a t ...
... The attack is performed in two steps: – 1) from 'visualization station', an unsatisfied employee performs a reprogramming of the sensor that measures the water flow rate in the penstock. In particular a constant water flow rate value is sent to the control center in order to deceive the operator/a t ...
Local area Network
... Virtual LANs (VLANs) can help IT managers adapt to these changes more easily and effectively, while increasing overall network performance. By offering a highly flexible means of segmenting a corporate network, VLANs reduce the performance bottlenecks that occur when traditional backbone routers can ...
... Virtual LANs (VLANs) can help IT managers adapt to these changes more easily and effectively, while increasing overall network performance. By offering a highly flexible means of segmenting a corporate network, VLANs reduce the performance bottlenecks that occur when traditional backbone routers can ...
PPT
... • There are various network technologies that can be used to interconnect nodes. • In general, Local Area Networks (LANs) are used to connect hosts within a building. Wide Area Networks (WANs) are used across the country or planet. • We are at an interesting point, as network technology is about to ...
... • There are various network technologies that can be used to interconnect nodes. • In general, Local Area Networks (LANs) are used to connect hosts within a building. Wide Area Networks (WANs) are used across the country or planet. • We are at an interesting point, as network technology is about to ...
E-Surveillance and User Privacy
... signature of allowed binaries – if not allowed, execution denied • Prevents unauthorized indirect branching • Protects from buffer overflow attacks • Cost – 35% performance hit! • Weakness – Does not protect against scripted (interpreted) code attacks – Perl, VB, etc ...
... signature of allowed binaries – if not allowed, execution denied • Prevents unauthorized indirect branching • Protects from buffer overflow attacks • Cost – 35% performance hit! • Weakness – Does not protect against scripted (interpreted) code attacks – Perl, VB, etc ...
Network Device Security Options
... Description of Ricoh Network Security Options available for MFP and Printer Products Network Port Security (ability to close unused network ports) Typically, network-enabled systems from all office equipment vendors are shipped to the customer with all the network ports “open,” making it as easy a ...
... Description of Ricoh Network Security Options available for MFP and Printer Products Network Port Security (ability to close unused network ports) Typically, network-enabled systems from all office equipment vendors are shipped to the customer with all the network ports “open,” making it as easy a ...
Trojan Horse
... documents, Java, ...), if you can help it. Avoid the most common operating systems and email programs, if possible. ...
... documents, Java, ...), if you can help it. Avoid the most common operating systems and email programs, if possible. ...
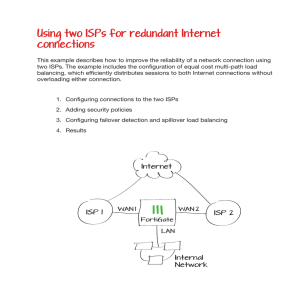
Using two ISPs for redundant Internet connections
... This example describes how to improve the reliability of a network connection using two ISPs. The example includes the configuration of equal cost multi-path load balancing, which efficiently distributes sessions to both Internet connections without overloading either connection. ...
... This example describes how to improve the reliability of a network connection using two ISPs. The example includes the configuration of equal cost multi-path load balancing, which efficiently distributes sessions to both Internet connections without overloading either connection. ...
Members First Credit Union
... Prioritize requests as well as the ability to escalate requests to other IT staff members and/or our vendor support teams. Work in a coordinated fashion with the Infrastructure Team and Operations Manager to establish and maintain SLAs, reporting, operational needs, etc. Lead staff in troubleshootin ...
... Prioritize requests as well as the ability to escalate requests to other IT staff members and/or our vendor support teams. Work in a coordinated fashion with the Infrastructure Team and Operations Manager to establish and maintain SLAs, reporting, operational needs, etc. Lead staff in troubleshootin ...
Information Security
... Using specialized VPN devices or built-in into a firewall If both your sites have Internet connectivity, they can be connected using VPN ...
... Using specialized VPN devices or built-in into a firewall If both your sites have Internet connectivity, they can be connected using VPN ...
circuit-level gateway
... • According to RFC 2828, the term firewall refers to an internetwork gateway that restricts data communication traffic to and from one of the connected networks and thus protects that network's system resources against threats from the other network • According to Cheswick and Bellovin, a firewall ( ...
... • According to RFC 2828, the term firewall refers to an internetwork gateway that restricts data communication traffic to and from one of the connected networks and thus protects that network's system resources against threats from the other network • According to Cheswick and Bellovin, a firewall ( ...
Framework
... Some can handle normal traffic but cannot handle traffic during heavy attacks Need to regularly check firewalls logs: ...
... Some can handle normal traffic but cannot handle traffic during heavy attacks Need to regularly check firewalls logs: ...
PowerPoint XP
... Instead of sharing a common network medium, all nodes in the network can be connected directly to a router/switch ...
... Instead of sharing a common network medium, all nodes in the network can be connected directly to a router/switch ...
Document
... Instead of sharing a common network medium, all nodes in the network can be connected directly to a router/switch ...
... Instead of sharing a common network medium, all nodes in the network can be connected directly to a router/switch ...
Charles Whitfield Jr
... maintenance of the Network Elements of Lucent’s Wavestar Optical Line System OLS (A dense Wavelength division Multiplexer with the capacity to transport up to 80 signals). Additional key responsibilities included: ...
... maintenance of the Network Elements of Lucent’s Wavestar Optical Line System OLS (A dense Wavelength division Multiplexer with the capacity to transport up to 80 signals). Additional key responsibilities included: ...
Physical Networks
... Internetworking • Users perceive a single, virtual network through which all machines can be reached • Users do not need to know the underlying details of the network • Application-level programs do not need to know the underlying details of the network ...
... Internetworking • Users perceive a single, virtual network through which all machines can be reached • Users do not need to know the underlying details of the network • Application-level programs do not need to know the underlying details of the network ...
Some Tools for Computer Security Incident Response
... Snort is a free and open source network intrusion prevention system (NIPS) and network intrusion detection system (NIDS). Snort’s has the ability to perform real-time traffic analysis and packet logging on Internet Protocol (IP) networks. Snort performs protocol analysis, content searching, and cont ...
... Snort is a free and open source network intrusion prevention system (NIPS) and network intrusion detection system (NIDS). Snort’s has the ability to perform real-time traffic analysis and packet logging on Internet Protocol (IP) networks. Snort performs protocol analysis, content searching, and cont ...
ITGS
... are connected together » the info from one hard disk is mirrored onto another one every time something is saved, so that if a hard disk fails, the computer switches to its mirror ...
... are connected together » the info from one hard disk is mirrored onto another one every time something is saved, so that if a hard disk fails, the computer switches to its mirror ...