Interacting Network Elements: Chaos and Congestion Propagation
... In mobile and ad hoc networks bandwidth is a scarce resource. Unlike in over provisioned Internet core networks, network elements in these are often used up to their limits over an extended period of time. Adaptive elastic traffic flows, such as TCP, struggle with each other for higher bandwidth sha ...
... In mobile and ad hoc networks bandwidth is a scarce resource. Unlike in over provisioned Internet core networks, network elements in these are often used up to their limits over an extended period of time. Adaptive elastic traffic flows, such as TCP, struggle with each other for higher bandwidth sha ...
What is the internet - New Mexico State University
... a network of networks based on the TCP/IP protocols, * a community of people who use and develop those networks, * a collection of resources that can be reached from those networks. ...
... a network of networks based on the TCP/IP protocols, * a community of people who use and develop those networks, * a collection of resources that can be reached from those networks. ...
Resume - Trelco Limited Company
... Responsible for the technical support of hardware, systems, applications, network administration and configuration of system security for the five regional airport offices of the Department Of Homeland Security in Kansas City. I use advanced diagnostic techniques to identify problems, investigate ca ...
... Responsible for the technical support of hardware, systems, applications, network administration and configuration of system security for the five regional airport offices of the Department Of Homeland Security in Kansas City. I use advanced diagnostic techniques to identify problems, investigate ca ...
Technology and Convergence Looking Back and Looking
... Consumer perspective: freedom to use broadband to access content, applications and devices of their choice Company perspective: broadband networks may not “discriminate” in favor of their own or affiliated content, applications or devices ...
... Consumer perspective: freedom to use broadband to access content, applications and devices of their choice Company perspective: broadband networks may not “discriminate” in favor of their own or affiliated content, applications or devices ...
1. Assume that for the network represented on the right the routing
... are generated using the link-state algorithm. The network consists of four routers (A-D) and three passive networks (U1-U3). a) Calculate the routing table for node A using the Dijkstra's algorithm. Justify your answer showing all intermediate steps. b) Now imagine that this network represented part ...
... are generated using the link-state algorithm. The network consists of four routers (A-D) and three passive networks (U1-U3). a) Calculate the routing table for node A using the Dijkstra's algorithm. Justify your answer showing all intermediate steps. b) Now imagine that this network represented part ...
PPT
... Key Establishment Each Sensor node establishes three kinds of keys: a NodeBase key that can be used for communication with the base station, pair-wise keys for immediate communication with neighbors and a group key that allows secure one to many communications. These keys provide flexibility in the ...
... Key Establishment Each Sensor node establishes three kinds of keys: a NodeBase key that can be used for communication with the base station, pair-wise keys for immediate communication with neighbors and a group key that allows secure one to many communications. These keys provide flexibility in the ...
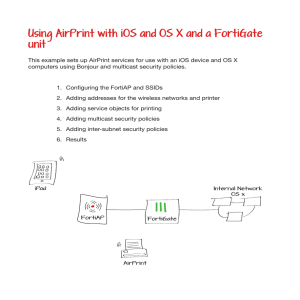
Using AirPrint with iOS and OS X and a FortiGate unit
... Adding multicast security policies Go to Policy > Policy > Multicast Policy. Create two policies to allow multicast traffic from WLAN1 and WLAN2 for iOS devices. For the first policy, set Incoming Interface to WLAN1, Source Address to the SSID1 IP, Outgoing Interface to WLAN2, and Destination Addre ...
... Adding multicast security policies Go to Policy > Policy > Multicast Policy. Create two policies to allow multicast traffic from WLAN1 and WLAN2 for iOS devices. For the first policy, set Incoming Interface to WLAN1, Source Address to the SSID1 IP, Outgoing Interface to WLAN2, and Destination Addre ...
Windows XP Professional
... Multiplexer Topology Bus Ring Star Mesh UTP STP PVC Plenum-Rated Noise EMI RFI Crosstalk ...
... Multiplexer Topology Bus Ring Star Mesh UTP STP PVC Plenum-Rated Noise EMI RFI Crosstalk ...
slides - IEEE HPSR 2012
... Luiz André Barroso, Urs Hölzle, “The Datacenter as a Computer: An Introduction to the Design of Warehouse-Scale Machines”, http://www.morganclaypool.com/doi/abs/10.2200/S00193ED1V01Y200905CAC006?prevSearch=allfield%253A%2528Urs%2529&searchHistoryKey= ...
... Luiz André Barroso, Urs Hölzle, “The Datacenter as a Computer: An Introduction to the Design of Warehouse-Scale Machines”, http://www.morganclaypool.com/doi/abs/10.2200/S00193ED1V01Y200905CAC006?prevSearch=allfield%253A%2528Urs%2529&searchHistoryKey= ...
lecture02
... packets, can be potentially lost, can be potentially delivered out-of-order • What you may want: application-to-application (end-to-end) channel, communication stream, reliable, in-order delivery ...
... packets, can be potentially lost, can be potentially delivered out-of-order • What you may want: application-to-application (end-to-end) channel, communication stream, reliable, in-order delivery ...
Internet Secure Protocols
... First / last router under control of system administration. Demilitarized zone. Security is low, since not protected by firewall. Locate webservers and other services there that generate potentially unsafe traffic. ...
... First / last router under control of system administration. Demilitarized zone. Security is low, since not protected by firewall. Locate webservers and other services there that generate potentially unsafe traffic. ...
COEN 351
... First / last router under control of system administration. Demilitarized zone. Security is low, since not protected by firewall. Locate webservers and other services there that generate potentially unsafe traffic. ...
... First / last router under control of system administration. Demilitarized zone. Security is low, since not protected by firewall. Locate webservers and other services there that generate potentially unsafe traffic. ...
The Internet is a global communication network which acts as a
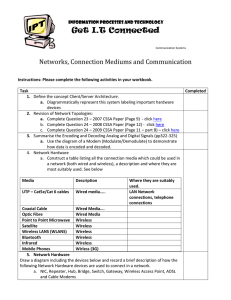
... 1. Define the concept Client/Server Architecture. a. Diagrammatically represent this system labeling important hardware devices 2. Revision of Network Topologies: a. Complete Question 23 – 2007 CSSA Paper (Page 9) - click here b. Complete Question 24 – 2008 CSSA Paper (Page 12) - click here c. Compl ...
... 1. Define the concept Client/Server Architecture. a. Diagrammatically represent this system labeling important hardware devices 2. Revision of Network Topologies: a. Complete Question 23 – 2007 CSSA Paper (Page 9) - click here b. Complete Question 24 – 2008 CSSA Paper (Page 12) - click here c. Compl ...
SMC1255TX / SMC1255TX/LP www.smc.com
... to help future-proof your network at both the home and office. The EZ Card™ Fast Ethernet PCI Card with Personal Firewall (SMC1255TX) provides a solid network connection while the included software, SMC Etherguard Personal Firewall and WinEtool Personal Sniffer, protects and manages your network. SM ...
... to help future-proof your network at both the home and office. The EZ Card™ Fast Ethernet PCI Card with Personal Firewall (SMC1255TX) provides a solid network connection while the included software, SMC Etherguard Personal Firewall and WinEtool Personal Sniffer, protects and manages your network. SM ...
Enterprise Network Management
... Collect flow information from hosts, and Combine with topology information from routeing protocols ...
... Collect flow information from hosts, and Combine with topology information from routeing protocols ...
Enterprise Network Management
... Collect flow information from hosts, and Combine with topology information from routeing protocols ...
... Collect flow information from hosts, and Combine with topology information from routeing protocols ...
Nauman Parkar
... Handling admin web page, Monitoring the network traffic and usage of the user’s data in the network, new connections, Renewal, MAC details. ...
... Handling admin web page, Monitoring the network traffic and usage of the user’s data in the network, new connections, Renewal, MAC details. ...
Computer Security
... Logical containers used to group users, systems, and resources Does not restrict administration based upon the physical location of device Each VLAN has its own security policy Used in switches Can be static or dynamic ...
... Logical containers used to group users, systems, and resources Does not restrict administration based upon the physical location of device Each VLAN has its own security policy Used in switches Can be static or dynamic ...
Basic Network Concepts
... • A class B address block only specifies the first two bytes of the addresses an organization may use; for instance, 167.1. • A class A address block only specifies the first byte of the address range—for instance, 18—and therefore has room for over 16 million nodes. ...
... • A class B address block only specifies the first two bytes of the addresses an organization may use; for instance, 167.1. • A class A address block only specifies the first byte of the address range—for instance, 18—and therefore has room for over 16 million nodes. ...
TcpIp and Firewalls
... uses ICMP to test for deliverability Sends a message and marks it not to be fragmented Looks for ICMP response saying too large Repeat the process with a smaller packet if necessary • Firewall must allow ICMP ...
... uses ICMP to test for deliverability Sends a message and marks it not to be fragmented Looks for ICMP response saying too large Repeat the process with a smaller packet if necessary • Firewall must allow ICMP ...
D efe ns iv
... exploitation. Students will learn more sophisticated hacker exploitation techniques, primarily against emergent ...
... exploitation. Students will learn more sophisticated hacker exploitation techniques, primarily against emergent ...
3CR860-95
... Secure, High-Speed, Shared Internet Access for Home and Small Offices The 3Com® OfficeConnect® Secure Router provides protected, high-speed Internet access for multiple users in home and small or branch office environments. With this router, up to 253 users can economically share a single cable or D ...
... Secure, High-Speed, Shared Internet Access for Home and Small Offices The 3Com® OfficeConnect® Secure Router provides protected, high-speed Internet access for multiple users in home and small or branch office environments. With this router, up to 253 users can economically share a single cable or D ...