lecture 17
... Local area networks: connects two or more devices in a limited geographical region. Wide are network: networks that cover large geographical areas. Value-added network: a type of wide area network that are private, data-only networks managed by third parties that provide telecommunication and compu ...
... Local area networks: connects two or more devices in a limited geographical region. Wide are network: networks that cover large geographical areas. Value-added network: a type of wide area network that are private, data-only networks managed by third parties that provide telecommunication and compu ...
Ports and IPv6
... processes that use Transmission Control Protocol (TCP). The same number of ports are available for application processes that use User Datagram Protocol (UDP). ...
... processes that use Transmission Control Protocol (TCP). The same number of ports are available for application processes that use User Datagram Protocol (UDP). ...
CSCI6268L19
... – Open Shortest Path First, Link-State Protocol – These protocols assume “modest sized” networks – A routing protocol decides how to forward packets based on routing tables ...
... – Open Shortest Path First, Link-State Protocol – These protocols assume “modest sized” networks – A routing protocol decides how to forward packets based on routing tables ...
Chapter 24 - William Stallings, Data and Computer
... conveys SSL related alerts to the peer entity compressed and encrypted ...
... conveys SSL related alerts to the peer entity compressed and encrypted ...
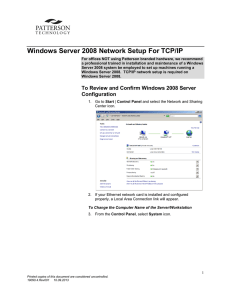
Windows Server 2008 Network Setup For TCP/IP
... Windows Server 2008 Network Setup For TCP/IP For offices NOT using Patterson branded hardware, we recommend a professional trained in installation and maintenance of a Windows Server 2008 system be employed to set up machines running a Windows Server 2008. TCP/IP network setup is required on Windows ...
... Windows Server 2008 Network Setup For TCP/IP For offices NOT using Patterson branded hardware, we recommend a professional trained in installation and maintenance of a Windows Server 2008 system be employed to set up machines running a Windows Server 2008. TCP/IP network setup is required on Windows ...
Ethernet switches, hubs, etc
... • Reconstruct the ‘real’ bits from selected chips – Allows multiple stations to ‘talk’ at the same time • By using different ‘chips’ they don’t interfere with each others’ transmissions – 54 Mbps/2.4 GHz carrier signal = 44 separate ‘channels’ ...
... • Reconstruct the ‘real’ bits from selected chips – Allows multiple stations to ‘talk’ at the same time • By using different ‘chips’ they don’t interfere with each others’ transmissions – 54 Mbps/2.4 GHz carrier signal = 44 separate ‘channels’ ...
3.1 telecommunications, networks and the internet
... Internet Addressing, Architecture, and Governance The Domain Name System: Every device connected to the Internet has a unique 32-bit numeric IP address. A Domain Name System (DNS) converts IP addresses to English-like domain names. The domain name is the name that corresponds to the unique 32-bit nu ...
... Internet Addressing, Architecture, and Governance The Domain Name System: Every device connected to the Internet has a unique 32-bit numeric IP address. A Domain Name System (DNS) converts IP addresses to English-like domain names. The domain name is the name that corresponds to the unique 32-bit nu ...
PPT - University of Pittsburgh
... • We need some sort of address in order to identify different nodes, as if every house has a mailing address in order to receive mail from others • The one used by Internet Protocol is called IP address • Every host on the Internet has a unique IP address, made up of four numbers. E.g.. 192.56.215.1 ...
... • We need some sort of address in order to identify different nodes, as if every house has a mailing address in order to receive mail from others • The one used by Internet Protocol is called IP address • Every host on the Internet has a unique IP address, made up of four numbers. E.g.. 192.56.215.1 ...
SOHO Network Administration
... SOHO Network generally use a small Ethernet Network switch or hub and cat 5 cabling, or a WIFI wireless network. ...
... SOHO Network generally use a small Ethernet Network switch or hub and cat 5 cabling, or a WIFI wireless network. ...
A Configuration Protocol for Embedded Networked Devices on Secure Wireless Networks
... assistants, industrial monitoring and control, and health monitoring systems. Devices wishing to join a wired network, such as Ethernet, typically need only be plugged into a hub or switch to gain network connectivity. The device may then utilize higher-level configuration protocols such as DHCP or ...
... assistants, industrial monitoring and control, and health monitoring systems. Devices wishing to join a wired network, such as Ethernet, typically need only be plugged into a hub or switch to gain network connectivity. The device may then utilize higher-level configuration protocols such as DHCP or ...
Lecture Slides - Stony Brook University
... CAM table exhaustion: can turn a switch into a hub macof (part of dsniff) ...
... CAM table exhaustion: can turn a switch into a hub macof (part of dsniff) ...
What computers talk about and how. COS 116 4/6/2006
... Internet is actually a bunch of connected computers called routers Packets hop from router to router until they reach destination ...
... Internet is actually a bunch of connected computers called routers Packets hop from router to router until they reach destination ...
CSCI 3421 Data communications and Networking
... Propagation Delay: Time to get to the destination End-to-End Delay: (Latency, Ping Time), sum of all delays from source to destination Run traceroute and ping to explore delay Other delay can occur (e.g., SMTP congestion control) ...
... Propagation Delay: Time to get to the destination End-to-End Delay: (Latency, Ping Time), sum of all delays from source to destination Run traceroute and ping to explore delay Other delay can occur (e.g., SMTP congestion control) ...
Hacking Overview - Computer Engineering
... Traceroute uses this to find the route to a given system. Useful for System Administration ...
... Traceroute uses this to find the route to a given system. Useful for System Administration ...
Chapter 6: Wireless and Mobile Networks
... exceeds # wired phone subscribers! computer nets: laptops, palmtops, PDAs, Internet-enabled phone promise anytime untethered Internet access two important (but different) challenges ...
... exceeds # wired phone subscribers! computer nets: laptops, palmtops, PDAs, Internet-enabled phone promise anytime untethered Internet access two important (but different) challenges ...
Introduction
... Store and Forward or Packet-Switched When a packet is sent from one router to the other via one or more intermediate router in its entirety, stored there until the required output is free. Message divided into packets ...
... Store and Forward or Packet-Switched When a packet is sent from one router to the other via one or more intermediate router in its entirety, stored there until the required output is free. Message divided into packets ...
Slide 1
... Channel Interference: transmissions can cause interference at the access points, degrading effective throughput and the channel capacity. Multiple Network Access: nodes in the multihop hotspot need: a wireless network adapter with more than one radio; or a wireless network adapter with the capab ...
... Channel Interference: transmissions can cause interference at the access points, degrading effective throughput and the channel capacity. Multiple Network Access: nodes in the multihop hotspot need: a wireless network adapter with more than one radio; or a wireless network adapter with the capab ...
Telecommunications and Networking - University of Baltimore Home
... – "a group of interconnected computers, workstations, or computer devices (such as printers and data storage systems).” ...
... – "a group of interconnected computers, workstations, or computer devices (such as printers and data storage systems).” ...
Solution
... a collision dprop < L/R ? Why or why not? There will be a collision in the sense that while a node is transmitting it will start to receive a packet from the other node. 2. Why is an ARP query sent with a broadcast frame? Why is an ARP response sent within a frame with a specific destination MAC add ...
... a collision dprop < L/R ? Why or why not? There will be a collision in the sense that while a node is transmitting it will start to receive a packet from the other node. 2. Why is an ARP query sent with a broadcast frame? Why is an ARP response sent within a frame with a specific destination MAC add ...
ModuleONEandTWO
... 1970s- As computers became more affordable, Bulletin Board Systems (BBSs) was created so that people could read messages on a discussion board. Speeds were still 300bps. 1980s- Quickly, more and more people used the bulletin boards and higher speed was needed to compensate. 1990- Modem speeds ...
... 1970s- As computers became more affordable, Bulletin Board Systems (BBSs) was created so that people could read messages on a discussion board. Speeds were still 300bps. 1980s- Quickly, more and more people used the bulletin boards and higher speed was needed to compensate. 1990- Modem speeds ...
Welcome to CS 444/544!
... • An internetwork is typically comprised of many physical networks over which data travels • There are many different types of physical networks: – Circuit-switched vs. packet-switched networks – Local Area Networks (LAN) vs. Wide Area Networks ...
... • An internetwork is typically comprised of many physical networks over which data travels • There are many different types of physical networks: – Circuit-switched vs. packet-switched networks – Local Area Networks (LAN) vs. Wide Area Networks ...
physcial_sci_networks_part2
... – Users when faced with a complex process may attempt to undermine the system • Sharing of passwords • Not logging out ...
... – Users when faced with a complex process may attempt to undermine the system • Sharing of passwords • Not logging out ...
Wireless LAN Management
... • IEEE 802.11 outline that the secret key used by WEP needs to be controlled by external key management – Normally, key management is done by user (define 4 different secret keys) – RADIUS (Remote Dial-In User Service) not use in small business or home users ...
... • IEEE 802.11 outline that the secret key used by WEP needs to be controlled by external key management – Normally, key management is done by user (define 4 different secret keys) – RADIUS (Remote Dial-In User Service) not use in small business or home users ...