lect2_3
... Internet applications such as the web? 5. What is the difference between connectionless and connection-oriented service? 6. Which one is connectionless TCP or UDP? 1: Introduction ...
... Internet applications such as the web? 5. What is the difference between connectionless and connection-oriented service? 6. Which one is connectionless TCP or UDP? 1: Introduction ...
PDF File
... issues. From the beginning we used RADWIN’s advanced R-Planner tool to optimize network planning and predict future network growth. This enabled us to build multiple ‘what-if’ scenarios to determine the correct equipment and installation sites.” ...
... issues. From the beginning we used RADWIN’s advanced R-Planner tool to optimize network planning and predict future network growth. This enabled us to build multiple ‘what-if’ scenarios to determine the correct equipment and installation sites.” ...
CISSP – Chapter 7 - Paladin Group, LLC
... Routers connect different networks. Move packets between networks Find the optimal path between networks Layer 3 (network) devices Look at IP addresses not MAC addresses Routers do not forward broadcasts, as such they create different broadcasts domain Can statically determine routes, ...
... Routers connect different networks. Move packets between networks Find the optimal path between networks Layer 3 (network) devices Look at IP addresses not MAC addresses Routers do not forward broadcasts, as such they create different broadcasts domain Can statically determine routes, ...
$doc.title
... Programming in an individual creaUve process. While thinking about a problem, discussions with friends are encouraged. However, when the Ume comes to write code that solves the problem, the program must ...
... Programming in an individual creaUve process. While thinking about a problem, discussions with friends are encouraged. However, when the Ume comes to write code that solves the problem, the program must ...
Network Architecture
... Check connections in rest of network Reboot PC and reset network connections Make sure NIC and its drivers are installed For TCP/IP network, use ping 127.0.0.1 command to determine whether NIC and IP protocol are working Check for an IRQ conflict Check cabling and ports Confirm most current version ...
... Check connections in rest of network Reboot PC and reset network connections Make sure NIC and its drivers are installed For TCP/IP network, use ping 127.0.0.1 command to determine whether NIC and IP protocol are working Check for an IRQ conflict Check cabling and ports Confirm most current version ...
Set Up a Wireless Connection using Apple Mac OS 10.5
... There are several measures you can take to minimise interference and improve the range between your wireless modem and computers. 1. Most wireless problems are due to interference from other network or appliances. You can change the wireless channel used by your modem to try and avoid those interfer ...
... There are several measures you can take to minimise interference and improve the range between your wireless modem and computers. 1. Most wireless problems are due to interference from other network or appliances. You can change the wireless channel used by your modem to try and avoid those interfer ...
ECEN 689 Special Topics in Data Science for Communications
... TCP/UDP Header and Information for ISPs • Have seen that UDP/TCP header information (port numbers) is used at hosts to associate packets to applications • Many of these associations are registered by IANA • The identify of the application that generated a packet can be inferred (to some degree) ...
... TCP/UDP Header and Information for ISPs • Have seen that UDP/TCP header information (port numbers) is used at hosts to associate packets to applications • Many of these associations are registered by IANA • The identify of the application that generated a packet can be inferred (to some degree) ...
ppt
... Represented by something over some medium by something Started with terminals connect to computers Communicated by voltages (currents) on wires (teletype) ...
... Represented by something over some medium by something Started with terminals connect to computers Communicated by voltages (currents) on wires (teletype) ...
A Survey of Energy efficient Network Protocols for Wireless Networks
... – When a mobile needs to transmit data it sends a RTS. If it does not receive a CTS, it goes into a back off state. – If a CTS is received, the mobile sends data while the receiver emits a busy tone. – The other neighboring mobile nodes on receiving the busy tone, refrain from any transmissions and ...
... – When a mobile needs to transmit data it sends a RTS. If it does not receive a CTS, it goes into a back off state. – If a CTS is received, the mobile sends data while the receiver emits a busy tone. – The other neighboring mobile nodes on receiving the busy tone, refrain from any transmissions and ...
pSHIELD STS DEMO Poster
... A monitoring system can be structured into 2 main layers: sensor network layer Physical level: is responsible of the processing of the locally generated data at the node level Transport level: controls the communication between the nodes of the network application layer Integration level: is respons ...
... A monitoring system can be structured into 2 main layers: sensor network layer Physical level: is responsible of the processing of the locally generated data at the node level Transport level: controls the communication between the nodes of the network application layer Integration level: is respons ...
Packet Tracer Scenario
... manage the event. The following is the detailed network description of ISP, Company, Agency1 and Agency 2: ...
... manage the event. The following is the detailed network description of ISP, Company, Agency1 and Agency 2: ...
Introduction to Distributed Systems & Networking
... – Consequently, applications need to perform their retransmits ...
... – Consequently, applications need to perform their retransmits ...
for networks
... transmitted simultaneously (usually an entire byte is transmitted along a bundle of parallel lines) – On PCs information sent to your printer employs parallel transmissions ...
... transmitted simultaneously (usually an entire byte is transmitted along a bundle of parallel lines) – On PCs information sent to your printer employs parallel transmissions ...
Communications & Networks
... Client & Server Networks • A method of network organisation • Each workstation is called a client • Each workstation is connected to a central system called a server • The server can be used for: – Holding all the data files and application software – Organising printing on the network – Organising ...
... Client & Server Networks • A method of network organisation • Each workstation is called a client • Each workstation is connected to a central system called a server • The server can be used for: – Holding all the data files and application software – Organising printing on the network – Organising ...
network_layer
... every site that wants to allow its user to roam has to create a home agent. every site that wants to allow visitors has to create a foreign agent. when a mobile host shows up at a foreign site, it contacts the foreign agent there and registers. the foreign agent then contacts the user’s home agent ...
... every site that wants to allow its user to roam has to create a home agent. every site that wants to allow visitors has to create a foreign agent. when a mobile host shows up at a foreign site, it contacts the foreign agent there and registers. the foreign agent then contacts the user’s home agent ...
Wireless Dome HD IP Camera with Night Vision, IP66
... • 30 fps at 1280 x 960 (960P) • Multi-level users management and passwords definition • Supports image snapshot • 1 input of alarm and 1 output of alarm • Giving alarm of motion detection via email or APP • Supports Dynamic IP (DDNS) and UPNP LAN and Internet (ADSL, Cable Modem) • Compliant with ONV ...
... • 30 fps at 1280 x 960 (960P) • Multi-level users management and passwords definition • Supports image snapshot • 1 input of alarm and 1 output of alarm • Giving alarm of motion detection via email or APP • Supports Dynamic IP (DDNS) and UPNP LAN and Internet (ADSL, Cable Modem) • Compliant with ONV ...
Cybersecurity Chapter 3 Test Review
... Pete, the security administrator, wants to ensure that traffic to the corporate intranet is secure using HTTPS. He configures the firewall to deny traffic to port 80. Now users cannot connect to the intranet even through HTTPS. Which of the following is MOST likely causing the issue? The web server ...
... Pete, the security administrator, wants to ensure that traffic to the corporate intranet is secure using HTTPS. He configures the firewall to deny traffic to port 80. Now users cannot connect to the intranet even through HTTPS. Which of the following is MOST likely causing the issue? The web server ...
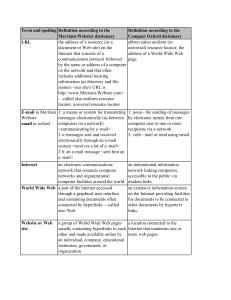
Table 9.1 Spelling and definitions.pdf
... World Wide Web a part of the Internet accessed through a graphical user interface and containing documents often connected by hyperlinks —called also Web ...
... World Wide Web a part of the Internet accessed through a graphical user interface and containing documents often connected by hyperlinks —called also Web ...
Computer networking devices are units that mediate data in a
... Repeater: device to amplify or regenerate digital signals received while setting them from one part of a network into another. Works on OSI layer 1. ...
... Repeater: device to amplify or regenerate digital signals received while setting them from one part of a network into another. Works on OSI layer 1. ...
Part I: Introduction - Computer Science Division
... Basic Service Set (BSS) (aka “cell”) in infrastructure mode contains: wireless hosts access point (AP): base station ad hoc mode: hosts only ...
... Basic Service Set (BSS) (aka “cell”) in infrastructure mode contains: wireless hosts access point (AP): base station ad hoc mode: hosts only ...
Networks
... speed Server – needs a lot of RAM and a fast hard drive Location of the files and software – if they are all on the server it creates a lot of traffic on the network. ...
... speed Server – needs a lot of RAM and a fast hard drive Location of the files and software – if they are all on the server it creates a lot of traffic on the network. ...
Interacting Network Elements: Chaos and Congestion Propagation
... H-1117 Budapest, Pázmány P. s. 1/A, Hungary ...
... H-1117 Budapest, Pázmány P. s. 1/A, Hungary ...