Firewalls
... NAT increases the flexibility of connection to the public network. Multiple pools, backup pools, and load sharing/balancing pools can be implemented to help ensure reliable public network connections. Network design is also simplified as planners have more flexibility when creating an address plan. ...
... NAT increases the flexibility of connection to the public network. Multiple pools, backup pools, and load sharing/balancing pools can be implemented to help ensure reliable public network connections. Network design is also simplified as planners have more flexibility when creating an address plan. ...
Security in Wireless Networks and Devices
... Bluetooth was developed in 1994 by Ericsson, a Swedish mobile-phone company, to let small mobile devices such as a laptop make calls over a mobile phone. It is a short-range always-on radio hookup embedded on a microchip. It uses a low-power 2.4 GHz band, which is available globally without a licens ...
... Bluetooth was developed in 1994 by Ericsson, a Swedish mobile-phone company, to let small mobile devices such as a laptop make calls over a mobile phone. It is a short-range always-on radio hookup embedded on a microchip. It uses a low-power 2.4 GHz band, which is available globally without a licens ...
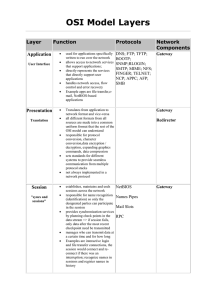
OSI Model Layers
... directly represents the services that directly support user applications handles network access, flow control and error recovery Example apps are file transfer,email, NetBIOS-based applications ...
... directly represents the services that directly support user applications handles network access, flow control and error recovery Example apps are file transfer,email, NetBIOS-based applications ...
chapterw4
... and are transmitted at 64 kbps. Assume propagation delays over the links are negligible. As a packet travels along the route, it encounters an average of 5 packets when it arrives at each node. How long does it take for the packet to get to the receiver if the nodes transmit on a ...
... and are transmitted at 64 kbps. Assume propagation delays over the links are negligible. As a packet travels along the route, it encounters an average of 5 packets when it arrives at each node. How long does it take for the packet to get to the receiver if the nodes transmit on a ...
Part I: Introduction
... service from server e.g., WWW client (browser)/ server; email client/server ...
... service from server e.g., WWW client (browser)/ server; email client/server ...
Current State Of The Literature Related To The Proposed Topic
... The network topology is in general dynamic, because the connectivity among the nodes may vary with time due to node departures, new node arrivals, and the possibility of having mobile nodes. Hence, there is a need for efficient routing protocols to allow the nodes to communicate over multihop paths ...
... The network topology is in general dynamic, because the connectivity among the nodes may vary with time due to node departures, new node arrivals, and the possibility of having mobile nodes. Hence, there is a need for efficient routing protocols to allow the nodes to communicate over multihop paths ...
Network Traversal
... This is done using instrumented programs installed by ISPs at their DNSs. The Host-IP pairs can be used to back-track hackers’ resources. For example, if hacker A uses domain blblbfizzly.com , we can now blacklist it. we look it up in passive dns to find ip pairs we find it matches the following IPs ...
... This is done using instrumented programs installed by ISPs at their DNSs. The Host-IP pairs can be used to back-track hackers’ resources. For example, if hacker A uses domain blblbfizzly.com , we can now blacklist it. we look it up in passive dns to find ip pairs we find it matches the following IPs ...
Introduction to the World Wide Web
... Files to be transmitted are divided into packets Labelled with to, from, and # of # Sent across the network…may take different routes Put together at the destination Missing packets are re-sent ...
... Files to be transmitted are divided into packets Labelled with to, from, and # of # Sent across the network…may take different routes Put together at the destination Missing packets are re-sent ...
Wireless Network Security
... • principal approach for preventing such access is the IEEE 802.1X standard for port-based network access control – provides an authentication mechanism for devices wishing to attach to a LAN or wireless network ...
... • principal approach for preventing such access is the IEEE 802.1X standard for port-based network access control – provides an authentication mechanism for devices wishing to attach to a LAN or wireless network ...
Chapter 7
... New version can bounce off walls, not direct line of sight, but only in same room Infrared used for printers, Palm Pilot PDAs, ...
... New version can bounce off walls, not direct line of sight, but only in same room Infrared used for printers, Palm Pilot PDAs, ...
IOSR Journal of Electrical and Electronics Engineering (IOSR-JEEE)
... of layers that was adhered to in its design: the network infrastructure was designed primarily with a flexibility goal in mind, independent of the applications. The result is, indeed, an extremely flexible network, although the price to pay for this is gross inefficiencies in the operation of the ne ...
... of layers that was adhered to in its design: the network infrastructure was designed primarily with a flexibility goal in mind, independent of the applications. The result is, indeed, an extremely flexible network, although the price to pay for this is gross inefficiencies in the operation of the ne ...
Name: Leo Mendoza WAN (used to be slow, noisy)
... Connectionless application - sends data with no connection (E-mail).Operates over both too, but packet switched subnet may be more efficient. Routing - each node in WAN is a router. Transmission line should provide the best path to the destination.The subnet is essentially a weighted network graph. ...
... Connectionless application - sends data with no connection (E-mail).Operates over both too, but packet switched subnet may be more efficient. Routing - each node in WAN is a router. Transmission line should provide the best path to the destination.The subnet is essentially a weighted network graph. ...
ECPE 5984 - Virginia Alliance for Secure Computing and Networking
... hidden variables, phf. WWW server IIS/RDP - ../../../../ attack to get files from the server. Alternate data streams ( Win95 names). ...
... hidden variables, phf. WWW server IIS/RDP - ../../../../ attack to get files from the server. Alternate data streams ( Win95 names). ...
Ping, traceroute, etc.
... • A hop is when a packet is transmitted from one node to the next. • “Some Internet Service Providers (ISPs) advertise how many hops away from Internet backbone they are. Theoretically, the fewer hops it takes to get your data onto the backbone, the faster your access will be.” (webopedia) ...
... • A hop is when a packet is transmitted from one node to the next. • “Some Internet Service Providers (ISPs) advertise how many hops away from Internet backbone they are. Theoretically, the fewer hops it takes to get your data onto the backbone, the faster your access will be.” (webopedia) ...
Questions from CIS410 Section 2
... 55. Bridges perform functions such as ________ and forwarding MAC frames. a. filtering b. calculating c. repeating d. processing 56. Which type of gateway changes a protocol from that of one communication architecture to that of another a gateway handles difference upper level protocol. a. protocol ...
... 55. Bridges perform functions such as ________ and forwarding MAC frames. a. filtering b. calculating c. repeating d. processing 56. Which type of gateway changes a protocol from that of one communication architecture to that of another a gateway handles difference upper level protocol. a. protocol ...
Document
... A secure tunnel to a private network through a public network Once established, local node appears to be a node in the private network in a secure ...
... A secure tunnel to a private network through a public network Once established, local node appears to be a node in the private network in a secure ...
attacks
... Unsolicited commercial email. ◦ Has been used as a vector for malicious code attacks. ◦ Wastes computer and human resources i.e. it is a DOS attack ...
... Unsolicited commercial email. ◦ Has been used as a vector for malicious code attacks. ◦ Wastes computer and human resources i.e. it is a DOS attack ...
Security Overview
... Too much reliance on technology alone for security • Most employees do not know the security policies for their organizations ...
... Too much reliance on technology alone for security • Most employees do not know the security policies for their organizations ...
WAN Technologies
... WANs provide for the exchange of data packets/frames between routers/bridges and the LANs they support. A WAN interconnects LANs that are usually ...
... WANs provide for the exchange of data packets/frames between routers/bridges and the LANs they support. A WAN interconnects LANs that are usually ...
Second Presentation
... • 10 Airborne Nodes/Routing Nodes (Wireless) • Random Walk • Random Speed ...
... • 10 Airborne Nodes/Routing Nodes (Wireless) • Random Walk • Random Speed ...
What is a Network?
... Disadvantages: Trackers are unreliable and if it goes down, the file is lost. ...
... Disadvantages: Trackers are unreliable and if it goes down, the file is lost. ...
Network Administrator - San Luis Obispo Superior Court
... implements, and maintains the Court’s data network which includes: local area and wide area network circuits, routers, servers and other equipment to meet departmental and courtwide requirements. Responsibilities of this position include the creation, administration and maintenance of standards and ...
... implements, and maintains the Court’s data network which includes: local area and wide area network circuits, routers, servers and other equipment to meet departmental and courtwide requirements. Responsibilities of this position include the creation, administration and maintenance of standards and ...
UNIT 5. Instruction to Computer Networks
... Internet Protocol (IP协议) :One of the most important protocols Uses connectionless(无连接) delivery – it does not guarantee delivery ...
... Internet Protocol (IP协议) :One of the most important protocols Uses connectionless(无连接) delivery – it does not guarantee delivery ...
Introduction
... Another benefit of inSSIDer is that it displays the encryption type used on a specific network. This is important information if you are doing a penetration test or a security audit. If your company is using wired equivalent privacy (WEP), it would be wise to switch to Wi-Fi protected access (WPA) o ...
... Another benefit of inSSIDer is that it displays the encryption type used on a specific network. This is important information if you are doing a penetration test or a security audit. If your company is using wired equivalent privacy (WEP), it would be wise to switch to Wi-Fi protected access (WPA) o ...
Language Support for Concurrency
... – Worse availability: depend on every machine being up • Lamport: “a distributed system is one where I can’t do work because some machine I’ve never heard of isn’t working!” ...
... – Worse availability: depend on every machine being up • Lamport: “a distributed system is one where I can’t do work because some machine I’ve never heard of isn’t working!” ...