Multicast
... Routers periodically poll hosts on subnets to see if any active receivers remain If no active receivers remain, routers propagate leave messages upstream to reduce unnecessary traffic Frequent polling can increase overhead Separate protocols for finding group membership address - sd ...
... Routers periodically poll hosts on subnets to see if any active receivers remain If no active receivers remain, routers propagate leave messages upstream to reduce unnecessary traffic Frequent polling can increase overhead Separate protocols for finding group membership address - sd ...
ppt
... Multicast stream source = origin of multicast stream multicast address = an IP address in the Class D range (224.0.0.0 – 239.255.255.255), used to refer to multiple recipients. A multicast address is also called a multicast group or channel. multicast stream = stream of IP packets with multicast add ...
... Multicast stream source = origin of multicast stream multicast address = an IP address in the Class D range (224.0.0.0 – 239.255.255.255), used to refer to multiple recipients. A multicast address is also called a multicast group or channel. multicast stream = stream of IP packets with multicast add ...
Catalyst 2K/3K Switches Software Feature Overview
... Access switch has a variety of identity mechanism for user authentication and adding user awareness is the natural progression ...
... Access switch has a variety of identity mechanism for user authentication and adding user awareness is the natural progression ...
A1604_Bluetooth_Technology_Powerpoint
... Quick synchronization between Bluetooth enabled devices Omni directional --> No line-of-sight requirement Ability to establish connection (between any portable devices and a wired network) Uses globally available unlicensed ISM radio band Frequency range : ...
... Quick synchronization between Bluetooth enabled devices Omni directional --> No line-of-sight requirement Ability to establish connection (between any portable devices and a wired network) Uses globally available unlicensed ISM radio band Frequency range : ...
Link Layer
... Two types of “links”: point-to-point PPP (point-to-point protocol) for dial-up access point-to-point link between Ethernet switch and host broadcast (shared wire or medium) traditional Ethernet upstream HFC (Hybrid fiber coaxial cable) 802.11 wireless LAN ...
... Two types of “links”: point-to-point PPP (point-to-point protocol) for dial-up access point-to-point link between Ethernet switch and host broadcast (shared wire or medium) traditional Ethernet upstream HFC (Hybrid fiber coaxial cable) 802.11 wireless LAN ...
Case Studies on IP-based Interconnection for Voice Services
... interest, operators will migrate from TDMvIC to IPvIC on a voluntary basis. However, in other cases regulatory intervention may be necessary. From a regulatory perspective, during the migration phase at least two crucial aspects have to be considered. Firstly, there are several different solutions w ...
... interest, operators will migrate from TDMvIC to IPvIC on a voluntary basis. However, in other cases regulatory intervention may be necessary. From a regulatory perspective, during the migration phase at least two crucial aspects have to be considered. Firstly, there are several different solutions w ...
18. APJ Instructor Forum
... • Divide a class C network 192.168.168.0/24 for subnets that can fit 3,5,10,42,110 hosts ...
... • Divide a class C network 192.168.168.0/24 for subnets that can fit 3,5,10,42,110 hosts ...
Cisco 110 Series Unmanaged Switches Data Sheet
... Give your office network a boost of speed and performance at a low price that takes almost no time to set up. Easily build a highly reliable network to connect your computers, printers, copiers, and other office equipment. If your business is like most small companies, you do not have an IT staff to ...
... Give your office network a boost of speed and performance at a low price that takes almost no time to set up. Easily build a highly reliable network to connect your computers, printers, copiers, and other office equipment. If your business is like most small companies, you do not have an IT staff to ...
Computer Science Illuminated, 3rd Edition
... True or False? A computer network is a collection of connected computing devices that may communicate and share resources. ...
... True or False? A computer network is a collection of connected computing devices that may communicate and share resources. ...
HP 2920 Switch Series data sheet
... Allows only specified ports to communicate with each other • RADIUS/TACACS+ Eases switch management security administration by using a password authentication server • IEEE 802.1X, MAC, or Web authentication Provides concurrent network access control and Web authentication of up to 24 clients per po ...
... Allows only specified ports to communicate with each other • RADIUS/TACACS+ Eases switch management security administration by using a password authentication server • IEEE 802.1X, MAC, or Web authentication Provides concurrent network access control and Web authentication of up to 24 clients per po ...
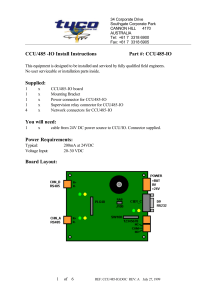
485-CCU HUB - Tyco Safety Products ANZ
... the CCU/IO-485 to port A or B of the CCU/485-IO using the following connection diagram. Up to eight CCU/IO-485 boards can be chained off one channel of the CCU/485-IO, giving up to 16 CCU/IO-485 boards connected to one CCU/485-IO. Appendix A contains information on wiring for this configuration. Che ...
... the CCU/IO-485 to port A or B of the CCU/485-IO using the following connection diagram. Up to eight CCU/IO-485 boards can be chained off one channel of the CCU/485-IO, giving up to 16 CCU/IO-485 boards connected to one CCU/485-IO. Appendix A contains information on wiring for this configuration. Che ...
Network Working Group S. Blake Request for
... throughput", "maximize reliability", or "minimize cost". Network nodes may select routing paths or forwarding behaviors which are suitably engineered to satisfy the service request. This model is subtly different from our architecture. Note that we do not describe the use of the DS field as an input ...
... throughput", "maximize reliability", or "minimize cost". Network nodes may select routing paths or forwarding behaviors which are suitably engineered to satisfy the service request. This model is subtly different from our architecture. Note that we do not describe the use of the DS field as an input ...
1. Use Cases
... 4. Register Traps (TrapInfo objects) to the Monitor module using/scanning the MIBTree. 2a. If the configuration file is unavailable or could not be parsed, do nothing and skip to line no.3 1. Failed to obtain information from the Moscad. 2. Elements defined in the configuration file do not appear in ...
... 4. Register Traps (TrapInfo objects) to the Monitor module using/scanning the MIBTree. 2a. If the configuration file is unavailable or could not be parsed, do nothing and skip to line no.3 1. Failed to obtain information from the Moscad. 2. Elements defined in the configuration file do not appear in ...
vRealize Automation Load Balancing
... every time a vRealize Automation or vRealize Orchestrator node goes down. Currently, NSX does not support email notification for such a scenario. You can set up an email notification with F5 by following methods: Configuring the BIG-IP system to deliver locally generated email messages Configuri ...
... every time a vRealize Automation or vRealize Orchestrator node goes down. Currently, NSX does not support email notification for such a scenario. You can set up an email notification with F5 by following methods: Configuring the BIG-IP system to deliver locally generated email messages Configuri ...
Read More - National Knowledge Network
... healthcare and agricultural institutions across the country to address such paradigm shift. The leading mission oriented agencies in the fields of nuclear, space and defence research are also part of NKN. By facilitating the flow of information and knowledge, the network addresses the critical issue ...
... healthcare and agricultural institutions across the country to address such paradigm shift. The leading mission oriented agencies in the fields of nuclear, space and defence research are also part of NKN. By facilitating the flow of information and knowledge, the network addresses the critical issue ...
3rd Edition, Chapter 5
... Single sender and single receiver E.g., dial-up links point-to-point protocol (PPP) broadcast (shared wire or medium) Multiple senders and multiple receivers E.g., traditional Ethernet, 802.11 wireless LAN need Multiple Access protocol (MAC) ...
... Single sender and single receiver E.g., dial-up links point-to-point protocol (PPP) broadcast (shared wire or medium) Multiple senders and multiple receivers E.g., traditional Ethernet, 802.11 wireless LAN need Multiple Access protocol (MAC) ...
slides - Network and Systems Laboratory
... Expt. 2: Promotion to supernode To Answer: What kind of node will be promote to SN? Setup several Skype clients One behind a saturated network uplink One behind a NAT ...
... Expt. 2: Promotion to supernode To Answer: What kind of node will be promote to SN? Setup several Skype clients One behind a saturated network uplink One behind a NAT ...
dynamic metric in ospf networks
... The massive growth of the Internet has led to increased requirements for reliable network infrastructure. The effectiveness of network communication depends on the ability of routers to determine the best path to send and forward packets to the desired destination. Open Shortest Path First (OSPF) pr ...
... The massive growth of the Internet has led to increased requirements for reliable network infrastructure. The effectiveness of network communication depends on the ability of routers to determine the best path to send and forward packets to the desired destination. Open Shortest Path First (OSPF) pr ...








![here - Campaign[x]](http://s1.studyres.com/store/data/008744944_1-0f4fd57a8eb108cf9826822f0ba0b000-300x300.png)