LAB1-Overview
... Use Cisco CLI Commands to Perform Basic Router & Switch Configuration and Verification Trace the steps used to examine the startup config, make changes to config, and replace the startup config with the running config ...
... Use Cisco CLI Commands to Perform Basic Router & Switch Configuration and Verification Trace the steps used to examine the startup config, make changes to config, and replace the startup config with the running config ...
Load-Sensitive Routing of Long-Lived IP Flows
... a particular source-destination pair, or even coarser levels of aggregation. In particular, several QoSrouting schemes were proposed that select paths based on network load, as well as application traffic characteristics and performance requirements [3–6]. Several QoS-routing protocols have been pro ...
... a particular source-destination pair, or even coarser levels of aggregation. In particular, several QoSrouting schemes were proposed that select paths based on network load, as well as application traffic characteristics and performance requirements [3–6]. Several QoS-routing protocols have been pro ...
VMWARE PUBLIC CLOUD INFRASTRUCTURE – Development environment design and implementation
... administration to a great extent. Therefore, some security-hardening guidelines have not been applied and the development environment will not contain all security aspects that are configured in the production infrastructure. Authentication is handled by Microsoft Active Directory as well as Open LD ...
... administration to a great extent. Therefore, some security-hardening guidelines have not been applied and the development environment will not contain all security aspects that are configured in the production infrastructure. Authentication is handled by Microsoft Active Directory as well as Open LD ...
PDF
... network. All traffic sent from the remote subnet uses Network Address Translation (NAT) to translate an IP address downloaded from the Easy VPN Server. An alternative would be to use Network Extension mode in this configuration to enable the support of devices such as VoIP phones located at the remo ...
... network. All traffic sent from the remote subnet uses Network Address Translation (NAT) to translate an IP address downloaded from the Easy VPN Server. An alternative would be to use Network Extension mode in this configuration to enable the support of devices such as VoIP phones located at the remo ...
RIP version 1
... RIP header - divided into 3 fields –Command field •REQUEST (1)- Request either a partial or full table update from another RIP router. •RESPONSE (2) - A response to a request. ...
... RIP header - divided into 3 fields –Command field •REQUEST (1)- Request either a partial or full table update from another RIP router. •RESPONSE (2) - A response to a request. ...
chapter 2 - Faculty Personal Homepage
... is not cumulative (however, bit errors can still occur if the signal is not regenerated before it degrades too much) ...
... is not cumulative (however, bit errors can still occur if the signal is not regenerated before it degrades too much) ...
21-04-0164-04-0000-Freescale_March2005
... MN receives strong beacon from new network Receive agent advertisement from cellular network Handoff ready request from MN to cellular network Traffic channel release request from MN Reassociation request to new network Data packets forwarded to new network ...
... MN receives strong beacon from new network Receive agent advertisement from cellular network Handoff ready request from MN to cellular network Traffic channel release request from MN Reassociation request to new network Data packets forwarded to new network ...
Circuit-switched fallback.
... handled by legacy Circuit-Switched (CS) networks, while data traffic is handled by LTE Packet-Switched (PS) networks—when and where available—and by 2G/3G networks as a fallback in non-LTE areas. Single radio solutions use CSFB to switch between LTE and 2G/3G access modes. CSFB has become the predom ...
... handled by legacy Circuit-Switched (CS) networks, while data traffic is handled by LTE Packet-Switched (PS) networks—when and where available—and by 2G/3G networks as a fallback in non-LTE areas. Single radio solutions use CSFB to switch between LTE and 2G/3G access modes. CSFB has become the predom ...
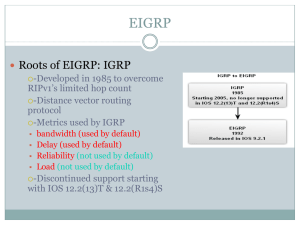
EIGRP
... • The IP-EIGRP module is responsible for sending and receiving EIGRP packets that are encapsulated in IP and for using DUAL to build and maintain the IP routing table. • The IPX EIGRP module is responsible for exchanging routing information about IPX networks with other IPX EIGRP routers. • Apple-Ta ...
... • The IP-EIGRP module is responsible for sending and receiving EIGRP packets that are encapsulated in IP and for using DUAL to build and maintain the IP routing table. • The IPX EIGRP module is responsible for exchanging routing information about IPX networks with other IPX EIGRP routers. • Apple-Ta ...
ITN_instructorPPT_Chapter8
... the first and last addresses cannot be assigned to hosts Loopback address - 127.0.0.1 a special address that hosts use to direct traffic to themselves (addresses 127.0.0.0 to 127.255.255.255 are reserved) Link-Local address - 169.254.0.0 to 169.254.255.255 (169.254.0.0/16) addresses can be autom ...
... the first and last addresses cannot be assigned to hosts Loopback address - 127.0.0.1 a special address that hosts use to direct traffic to themselves (addresses 127.0.0.0 to 127.255.255.255 are reserved) Link-Local address - 169.254.0.0 to 169.254.255.255 (169.254.0.0/16) addresses can be autom ...
Welcome to ENTC 415
... Optical Burst Switching (OBS) • Group of packets a grouped in to ‘bursts’, which is the transmission unit • Before the transmission, a control packet is sent out – The control packet contains the information of burst arrival time, burst duration, and destination address ...
... Optical Burst Switching (OBS) • Group of packets a grouped in to ‘bursts’, which is the transmission unit • Before the transmission, a control packet is sent out – The control packet contains the information of burst arrival time, burst duration, and destination address ...
Link Layer
... “Taking Turns” protocols Channel partitioning MAC protocols: share channel efficiently and fairly at high load inefficient at low load: delay in channel access, 1/N bandwidth allocated even if only 1 active node! Random access MAC protocols efficient at low load: single node can fully utilize ...
... “Taking Turns” protocols Channel partitioning MAC protocols: share channel efficiently and fairly at high load inefficient at low load: delay in channel access, 1/N bandwidth allocated even if only 1 active node! Random access MAC protocols efficient at low load: single node can fully utilize ...
PAN‐OS Web Interface Reference Guide
... Specifies that all subinterfaces belonging to this Layer 3 interface are untagged. PAN‐OS® selects an untagged subinterface as the ingress interface based on the packet destination. If the destination is the IP address of an untagged subinterface, it maps to the subinterface. This also means tha ...
... Specifies that all subinterfaces belonging to this Layer 3 interface are untagged. PAN‐OS® selects an untagged subinterface as the ingress interface based on the packet destination. If the destination is the IP address of an untagged subinterface, it maps to the subinterface. This also means tha ...
BreezeMAX PRO 5000 CPE
... invoice date (the "Warranty Period")". During the Warranty Period, Alvarion may release to its Customers firmware updates, which include additional performance improvements and/or bug fixes, upon availability (the "Warranty"). Bug fixes, temporary patches and/or workarounds may be supplied as Firmwa ...
... invoice date (the "Warranty Period")". During the Warranty Period, Alvarion may release to its Customers firmware updates, which include additional performance improvements and/or bug fixes, upon availability (the "Warranty"). Bug fixes, temporary patches and/or workarounds may be supplied as Firmwa ...
Section 4: From ARPANET to the Internet
... Q15: The programming language which is used with HyperCard is called _________________. (Answer: Hyper Talk). Q16: The Web –WWW was invented in 1989 by ___________________. (Answer: Tim Berners-Lee). Note: The special requirements of a hypertext system for CERN were, Berners-Lee believed, that it sh ...
... Q15: The programming language which is used with HyperCard is called _________________. (Answer: Hyper Talk). Q16: The Web –WWW was invented in 1989 by ___________________. (Answer: Tim Berners-Lee). Note: The special requirements of a hypertext system for CERN were, Berners-Lee believed, that it sh ...
Windows Peer-to-Peer Network Configuration Guide
... necessary that only one workstation act as the server, with the other workstations, or clients, accessing Pathways from that single “server”. The installation of Pathways can either be performed from one of the workstations or from the server itself, as long as it installed to a drive that is common ...
... necessary that only one workstation act as the server, with the other workstations, or clients, accessing Pathways from that single “server”. The installation of Pathways can either be performed from one of the workstations or from the server itself, as long as it installed to a drive that is common ...
Ch14
... 14. Which utility allows a Linux computer to access shares on a Windows-based computer? a. nis b. nfsmount c. smb d. smbclient Answer: d 15. The TCP/IP address of 127.0.0.1 is also referred to as the __________. a. local address b. lookup address c. local host d. loopback address Answer: d 16. The l ...
... 14. Which utility allows a Linux computer to access shares on a Windows-based computer? a. nis b. nfsmount c. smb d. smbclient Answer: d 15. The TCP/IP address of 127.0.0.1 is also referred to as the __________. a. local address b. lookup address c. local host d. loopback address Answer: d 16. The l ...
ch02 - Test Bank 1
... 67. ____________________, a network layer mechanism that helps systems manage addresses, uses a device like a router to segregate the external Internet from an internal intranet or network. 68. In ____________________ networks, the individual users or clients directly interact and share resources, w ...
... 67. ____________________, a network layer mechanism that helps systems manage addresses, uses a device like a router to segregate the external Internet from an internal intranet or network. 68. In ____________________ networks, the individual users or clients directly interact and share resources, w ...
CN2-Unit-1-Packet-switching-networks-by-Deepa
... node 4 but the cost has increased to 6.Node 3 finds its shortest path is still through node 4 but the cost has increased to 7.Node 4 and Node 5 finds the shortest path is not changed. Node 2 transmits its updates to node1,node4 and node 5 and transmits its updates to node 1 and 4. (update 4) Node ...
... node 4 but the cost has increased to 6.Node 3 finds its shortest path is still through node 4 but the cost has increased to 7.Node 4 and Node 5 finds the shortest path is not changed. Node 2 transmits its updates to node1,node4 and node 5 and transmits its updates to node 1 and 4. (update 4) Node ...
Link Layer
... “Taking Turns” MAC protocols channel partitioning MAC protocols: share channel efficiently and fairly at high load inefficient at low load: delay in channel access, 1/N bandwidth allocated even if only 1 active node! Random access MAC protocols efficient at low load: single node can fully uti ...
... “Taking Turns” MAC protocols channel partitioning MAC protocols: share channel efficiently and fairly at high load inefficient at low load: delay in channel access, 1/N bandwidth allocated even if only 1 active node! Random access MAC protocols efficient at low load: single node can fully uti ...
Chapter 5 Notes - SFU computing science
... “Taking Turns” MAC protocols channel partitioning MAC protocols: share channel efficiently and fairly at high load inefficient at low load: delay in channel access, 1/N bandwidth allocated even if only 1 active node! Random access MAC protocols efficient at low load: single node can fully uti ...
... “Taking Turns” MAC protocols channel partitioning MAC protocols: share channel efficiently and fairly at high load inefficient at low load: delay in channel access, 1/N bandwidth allocated even if only 1 active node! Random access MAC protocols efficient at low load: single node can fully uti ...
Introduction to IPv6 protocol
... – Router Advertisement (RA) : • periodic advertisement (of the availability of a router) which contains: • list of prefixes used on the link (autoconf) • a possible value for Max Hop Limit (TTL of IPv4) • value of MTU ...
... – Router Advertisement (RA) : • periodic advertisement (of the availability of a router) which contains: • list of prefixes used on the link (autoconf) • a possible value for Max Hop Limit (TTL of IPv4) • value of MTU ...