Computer Communications
... – packet switched, like telegrams or letters – propagation by store-and-forward nodes – used by Ethernet, token ring, and FDDI ...
... – packet switched, like telegrams or letters – propagation by store-and-forward nodes – used by Ethernet, token ring, and FDDI ...
Cisco AON Secure File Transfer Extension Module
... barriers faced by organizations with cost-effectively deploying large-scale B2B trading networks. With the introduction of this solution, Cisco is the first to provide full support for the AS2 protocol in a network-embedded form factor. While AS2 has been primarily deployed in retail supply chains, ...
... barriers faced by organizations with cost-effectively deploying large-scale B2B trading networks. With the introduction of this solution, Cisco is the first to provide full support for the AS2 protocol in a network-embedded form factor. While AS2 has been primarily deployed in retail supply chains, ...
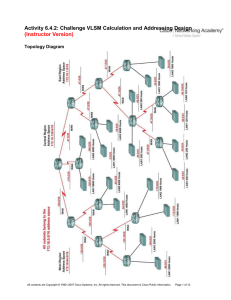
2e_06_6_4_2_vlsm_instr
... All contents are Copyright © 1992–2007 Cisco Systems, Inc. All rights reserved. This document is Cisco Public Information. ...
... All contents are Copyright © 1992–2007 Cisco Systems, Inc. All rights reserved. This document is Cisco Public Information. ...
pdf
... under tight delay constraint. This property is first demonstrated analytically on a family of mobile networks which follow a random graph process. We then establish a similar result empirically with four data sets capturing human mobility, using a new methodology to efficiently compute all the paths ...
... under tight delay constraint. This property is first demonstrated analytically on a family of mobile networks which follow a random graph process. We then establish a similar result empirically with four data sets capturing human mobility, using a new methodology to efficiently compute all the paths ...
Mobile Ad-hoc Clouds
... landscape. The ease of access to a pool of devices is much more arbitrary and based purely on the needs of the user. This pool can act as a provider of an infrastructure for various services that can be processed with volunteer node participation, where the node in the vicinity is itself a service p ...
... landscape. The ease of access to a pool of devices is much more arbitrary and based purely on the needs of the user. This pool can act as a provider of an infrastructure for various services that can be processed with volunteer node participation, where the node in the vicinity is itself a service p ...
3-1-3_Scalable
... HSR - logical partitions and location management (cont’d) • Each subnetwork has at least one Home Agent to manage membership • Each member of the subnet registers its own hierarchical address with Home Agent – periodical/event driven registration; stale addresses are timed out by Home Agent • Home ...
... HSR - logical partitions and location management (cont’d) • Each subnetwork has at least one Home Agent to manage membership • Each member of the subnet registers its own hierarchical address with Home Agent – periodical/event driven registration; stale addresses are timed out by Home Agent • Home ...
PowerPoint Presentation - requirements for delivering MPLS
... • Clarified problem statement in Section 3 – Last IETF, Yakov asked a question about the scalability of CTE LSPs ...
... • Clarified problem statement in Section 3 – Last IETF, Yakov asked a question about the scalability of CTE LSPs ...
http://www.gratisexam.com/
... Explanation/Reference: This can be a hard question if you don’t remember to invert the 7th bit of the first octet in the MAC address! Always look for the 7th bit when studying for the CCENT/CCNA and when using EUI64, invert it. The EUI-64 autoconfiguration then inserts an FF:FE in the middle of the ...
... Explanation/Reference: This can be a hard question if you don’t remember to invert the 7th bit of the first octet in the MAC address! Always look for the 7th bit when studying for the CCENT/CCNA and when using EUI64, invert it. The EUI-64 autoconfiguration then inserts an FF:FE in the middle of the ...
User`s Manual
... translation, conversion into any electronic medium or machine scannable form is not permitted, either in whole or in part. An exception is the preparation of a backup copy of the software for your own use. For devices with embedded software, the end-user license agreement on the enclosed CD applies. ...
... translation, conversion into any electronic medium or machine scannable form is not permitted, either in whole or in part. An exception is the preparation of a backup copy of the software for your own use. For devices with embedded software, the end-user license agreement on the enclosed CD applies. ...
Internet Connectivity for Ad hoc Mobile Networks
... The Mobile IP protocol [9, 10] is currently being standardized by the IP Routing for Wireless/Mobile Hosts (MobileIP) Working Group [1] of the Internet Engineering Task Force (IETF). Mobile IP provides transparent routing of IP datagrams to mobile nodes in the Internet, such that mobile users can co ...
... The Mobile IP protocol [9, 10] is currently being standardized by the IP Routing for Wireless/Mobile Hosts (MobileIP) Working Group [1] of the Internet Engineering Task Force (IETF). Mobile IP provides transparent routing of IP datagrams to mobile nodes in the Internet, such that mobile users can co ...
AXIS 262 User`s Manual
... comprehensive surveillance solution for detecting shoplifters, reducing false alarms, increasing personnel safety or viewing your premises remotely. Easy to install and use, the AXIS 262 is a complete recording solution that connects directly to your network and is manageable remotely via a local ar ...
... comprehensive surveillance solution for detecting shoplifters, reducing false alarms, increasing personnel safety or viewing your premises remotely. Easy to install and use, the AXIS 262 is a complete recording solution that connects directly to your network and is manageable remotely via a local ar ...
DNSCatProxy: A Pluggable Transport based on DNS Tunneling Irvin Zhan Abstract
... The Tor protocol enforces online privacy and anonymity. Relays within the Tor network are unable to link a connection’s source and destination, nor are the servers that the Tor users connect to able to figure out the IP address of the Tor user. This is because the Tor protocol uses a layered system ...
... The Tor protocol enforces online privacy and anonymity. Relays within the Tor network are unable to link a connection’s source and destination, nor are the servers that the Tor users connect to able to figure out the IP address of the Tor user. This is because the Tor protocol uses a layered system ...
Technology that thinks ahead
... ■■ The transition of network functionalities to the cloud is likely to enable faster deployment of networks and reduction of costs, and help Nokia Networks’ customers provide a better experience to their own customers. ■■ Automation of services is likely to increase across every stage of network l ...
... ■■ The transition of network functionalities to the cloud is likely to enable faster deployment of networks and reduction of costs, and help Nokia Networks’ customers provide a better experience to their own customers. ■■ Automation of services is likely to increase across every stage of network l ...
Integrating Cisco Press Resources into the Academy Classroom
... Networking Basics and Terminology Ethernet Bridges • Examine incoming signal, interpret signal as 0’s and 1’s, find the destination MAC address listed in the frame • If destination MAC address is reachable via a different interface than the one on which it was received, then clean, regenerate and f ...
... Networking Basics and Terminology Ethernet Bridges • Examine incoming signal, interpret signal as 0’s and 1’s, find the destination MAC address listed in the frame • If destination MAC address is reachable via a different interface than the one on which it was received, then clean, regenerate and f ...
On Modern DNS Behavior and Properties
... of transport port numbers. A final—yet crucial—example is that DNS mappings foster agility within the network such that traffic can be directed with fine granularity. There are alternate methods for directing traffic through the network—i.e., routing changes— but these are more cumbersome than using ...
... of transport port numbers. A final—yet crucial—example is that DNS mappings foster agility within the network such that traffic can be directed with fine granularity. There are alternate methods for directing traffic through the network—i.e., routing changes— but these are more cumbersome than using ...
JNCIA Study Guide - Open Shortest Path First (OSPF)
... Init The Init state is reached when an OSPF router receives a hello packet but the local router ID is not listed in the received Neighbor field. This means that bidirectional communication has not been established between the peers. Attempt The Attempt state is valid only for Non-Broadcast Multi-Acc ...
... Init The Init state is reached when an OSPF router receives a hello packet but the local router ID is not listed in the received Neighbor field. This means that bidirectional communication has not been established between the peers. Attempt The Attempt state is valid only for Non-Broadcast Multi-Acc ...
NOTICE OF USE AND DISCLOSURE
... Class C – Continuously listening ......................................................................................... 70 17 Class C: Continuously listening end-device................................................................ 71 17.1 Second receive window duration for Class C ............. ...
... Class C – Continuously listening ......................................................................................... 70 17 Class C: Continuously listening end-device................................................................ 71 17.1 Second receive window duration for Class C ............. ...
Issue - IETF
... For IP-in-IP encapsulation the multicast routers can route based on the outer header. For non-IP encapsulation, multicast routing must use the inner header, which may need translation to make it usable. ...
... For IP-in-IP encapsulation the multicast routers can route based on the outer header. For non-IP encapsulation, multicast routing must use the inner header, which may need translation to make it usable. ...
July 2001 - IEEE 802
... Classification • Each device broadcasts periodically information about its availability for the others by sending id_info PDU • With this PDU the broadcasting device informs that it can be contacted during the next e.g. 1ms – The PDU contains IEEE address and 8-bit device service field – Mini device ...
... Classification • Each device broadcasts periodically information about its availability for the others by sending id_info PDU • With this PDU the broadcasting device informs that it can be contacted during the next e.g. 1ms – The PDU contains IEEE address and 8-bit device service field – Mini device ...
User Manual
... interface only supports 2048 input bytes and maximum 2048 output bytes. Each byte can be 8 discrete inputs or outputs, but analog or pulse I/O take up 1 byte for low resolution values (8-bit) or 2 bytes for high resolution values (16-bit). An “output” is a value coming into the 105G via the fieldbus ...
... interface only supports 2048 input bytes and maximum 2048 output bytes. Each byte can be 8 discrete inputs or outputs, but analog or pulse I/O take up 1 byte for low resolution values (8-bit) or 2 bytes for high resolution values (16-bit). An “output” is a value coming into the 105G via the fieldbus ...
sip:username@domain
... The registrar is a special SIP entity that receives registrations from users, extracts information about their current location (IP address, port and username in this case) and stores the information into location ...
... The registrar is a special SIP entity that receives registrations from users, extracts information about their current location (IP address, port and username in this case) and stores the information into location ...
6 The model to classify the requirements for Smart Grid
... The phrase "is required to" indicates a requirement which must be strictly followed and from which no deviation is permitted if conformance to this Deliverable is to be claimed. The phrase "is prohibited from" indicates a requirement which must be strictly followed and from which no deviation is per ...
... The phrase "is required to" indicates a requirement which must be strictly followed and from which no deviation is permitted if conformance to this Deliverable is to be claimed. The phrase "is prohibited from" indicates a requirement which must be strictly followed and from which no deviation is per ...