Solution - Andrew.cmu.edu
... 2. Name the common techniques on which error control is based on and explain how they are actually implemented. - Identification of techniques (2) - Explanation of implementation.(ARQ) (8) The question was intended to be ‘Name the common techniques on which error correction is based on’. The answer ...
... 2. Name the common techniques on which error control is based on and explain how they are actually implemented. - Identification of techniques (2) - Explanation of implementation.(ARQ) (8) The question was intended to be ‘Name the common techniques on which error correction is based on’. The answer ...
Communications Networks: Fundamental Concepts and Key
... The caller sends this number by pushing the keys on the telephone set. Each key generates a pair of tones that specify a number. (In the older phone sets the user dials a number which in turn generates a corresponding number of pulses.) ...
... The caller sends this number by pushing the keys on the telephone set. Each key generates a pair of tones that specify a number. (In the older phone sets the user dials a number which in turn generates a corresponding number of pulses.) ...
IAS-W
... stringent time and capacity requirements in areas where the rapid expansion of potential subscribers base requires urgent deployment of telecommunication servicing, including ISDN and high speed data, but the existing cable infrastructure is either not sufficient or not available. In rural areas: IA ...
... stringent time and capacity requirements in areas where the rapid expansion of potential subscribers base requires urgent deployment of telecommunication servicing, including ISDN and high speed data, but the existing cable infrastructure is either not sufficient or not available. In rural areas: IA ...
Basic Service Set (BSS)
... • ESS stations must have the same SSID • The BSSID is the “name” of the BSS (not same as SSID) • APs can be positioned so that cells overlap to facilitate roaming – Wireless devices choose AP based on signal strength – Stations going from one BSS to another will deal with Handoff Wired LAN ...
... • ESS stations must have the same SSID • The BSSID is the “name” of the BSS (not same as SSID) • APs can be positioned so that cells overlap to facilitate roaming – Wireless devices choose AP based on signal strength – Stations going from one BSS to another will deal with Handoff Wired LAN ...
tutorial 1 - Portal UniMAP
... De jure (“by right”) standards are established together by standards organizations and expert committees, while de facto (“by fact”) standards are established by popular use. ...
... De jure (“by right”) standards are established together by standards organizations and expert committees, while de facto (“by fact”) standards are established by popular use. ...
presentation source
... switched network vendor pays the cost of the access line for you and bundles it into your service charges. ...
... switched network vendor pays the cost of the access line for you and bundles it into your service charges. ...
TH 3.4 Tech Talk for Those Not Technically Inclined (Metro C)
... IaaS (infrastructure as a service) a category of "cloud computing"; a provision model in which an organization outsources the equipment used to support operations, including storage, hardware, servers and networking components. The service provider owns the equipment and is responsible for housing, ...
... IaaS (infrastructure as a service) a category of "cloud computing"; a provision model in which an organization outsources the equipment used to support operations, including storage, hardware, servers and networking components. The service provider owns the equipment and is responsible for housing, ...
VPN tunneling protocols
... • Depends on the domain’s functional level (mixed, 2000 native or 2003 native or 2008) • Depend on the machine user is connecting to • Composed of Conditions, Constraints, and Settings – Conditions are criteria that must be met in order for remote access policy to apply to a connection – Allow if me ...
... • Depends on the domain’s functional level (mixed, 2000 native or 2003 native or 2008) • Depend on the machine user is connecting to • Composed of Conditions, Constraints, and Settings – Conditions are criteria that must be met in order for remote access policy to apply to a connection – Allow if me ...
What Is the Purpose of the Components Required for Successful
... A network standard defines guidelines that specify the way computers access a medium, the type(s) of medium, the speeds on different types of networks, and the type of physical cable or wireless technology used. Network communications standards include the following. Ethernet specifies that no centr ...
... A network standard defines guidelines that specify the way computers access a medium, the type(s) of medium, the speeds on different types of networks, and the type of physical cable or wireless technology used. Network communications standards include the following. Ethernet specifies that no centr ...
A Review on Wireless Network
... depending on availability since wireless gives the freedom of choice. Network managers in a dynamic environment minimize the workload caused by moving wired connections. Warehouse workers use wireless network to exchange information with central databases, ...
... depending on availability since wireless gives the freedom of choice. Network managers in a dynamic environment minimize the workload caused by moving wired connections. Warehouse workers use wireless network to exchange information with central databases, ...
426Introduction
... Used analog transmission system Requires setting up a connection before transfer of information can take place (called “circuit switching”) ...
... Used analog transmission system Requires setting up a connection before transfer of information can take place (called “circuit switching”) ...
Network Notes - w w w .conta.uom .gr
... • A network is a set of connected devices (nodes) which share resources and can access each other • public vs. private network – local loop is a public network – your organization’s LAN is private ...
... • A network is a set of connected devices (nodes) which share resources and can access each other • public vs. private network – local loop is a public network – your organization’s LAN is private ...
2. Who controls or owns the Internet?
... The Internet is a worldwide collection of interconnected networks. It is actually comprised of thousands of independent networks at academic institutions, military installations, government agencies, commercial enterprises, and other organizations. The Internet has its roots in a networking project ...
... The Internet is a worldwide collection of interconnected networks. It is actually comprised of thousands of independent networks at academic institutions, military installations, government agencies, commercial enterprises, and other organizations. The Internet has its roots in a networking project ...
The Internet and the Web
... if a copy is found, it sends a conditional request to the server essentially: "send this page/image only if it has been changed since the timestamp" if the server copy has not changed, the server sends back a brief message and the browser simply uses the cached copy ...
... if a copy is found, it sends a conditional request to the server essentially: "send this page/image only if it has been changed since the timestamp" if the server copy has not changed, the server sends back a brief message and the browser simply uses the cached copy ...
Data communication and Networking
... to SMDS's arrival in 1995, the only way to connect LANs was through a dedicated private line. ...
... to SMDS's arrival in 1995, the only way to connect LANs was through a dedicated private line. ...
Video-surveillance Citizen Network
... The principal goal of the project was to establish an effective and highly scalable video-surveillance and public safety system that records in real time several streets of the city by using a total amount of 33 IP cameras. All videos should be sent to a control center to be monitored 24x7 by the po ...
... The principal goal of the project was to establish an effective and highly scalable video-surveillance and public safety system that records in real time several streets of the city by using a total amount of 33 IP cameras. All videos should be sent to a control center to be monitored 24x7 by the po ...
Turkish lottery agents move to 3G wireless mobile
... RICON 3G routers are connected to the GTech lottery terminals with via a 9 pin serial port interface. The antenna used in RICON 3G wireless mobile router was able to be placed externally for optimal maximum signal strength. The routers dual SIM’s are securely protected within the router making the d ...
... RICON 3G routers are connected to the GTech lottery terminals with via a 9 pin serial port interface. The antenna used in RICON 3G wireless mobile router was able to be placed externally for optimal maximum signal strength. The routers dual SIM’s are securely protected within the router making the d ...
Open Protocol
... Each physical device (or set of devices) is represented by a Widget in an preconfigured application (App). Web Services are used to exchange data between the App and server, whatever the equipment Widgets are aggregated to create an unique App Easy skinning to comply with Hotel ambiance and guest ne ...
... Each physical device (or set of devices) is represented by a Widget in an preconfigured application (App). Web Services are used to exchange data between the App and server, whatever the equipment Widgets are aggregated to create an unique App Easy skinning to comply with Hotel ambiance and guest ne ...
midterm
... Allows much closer and ‘one-to-one’ contact between customer and seller Offer customers the components of a product/service then the customer creates their own version by ‘pulling’ what they want ...
... Allows much closer and ‘one-to-one’ contact between customer and seller Offer customers the components of a product/service then the customer creates their own version by ‘pulling’ what they want ...
Chapter 6
... provider puts the latest technology to your door, your home/office is still wired with old fashioned technology, so all the provider’s efforts do not help once the signal reaches your location and you are constrained (limited) by the technology in your own ...
... provider puts the latest technology to your door, your home/office is still wired with old fashioned technology, so all the provider’s efforts do not help once the signal reaches your location and you are constrained (limited) by the technology in your own ...
find_panel.Nick
... Time/Warner Cable: Not using standard ports is a violation of the AUP because it interferes with traffic shaping Small ISP: Inserting advertisements into all viewed web pages!? ...
... Time/Warner Cable: Not using standard ports is a violation of the AUP because it interferes with traffic shaping Small ISP: Inserting advertisements into all viewed web pages!? ...
Hopfield networks
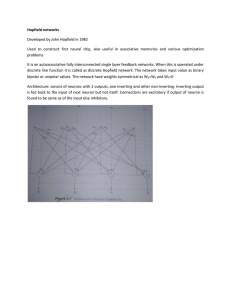
... Developed by John Hopfield in 1982 Used to construct first neural chip, also useful in associative memories and various optimization problems It is an autoassociative fully interconnected single layer feedback networks. When this is operated under discrete line function it is called as discrete Hopf ...
... Developed by John Hopfield in 1982 Used to construct first neural chip, also useful in associative memories and various optimization problems It is an autoassociative fully interconnected single layer feedback networks. When this is operated under discrete line function it is called as discrete Hopf ...