ppt
... • Original attack required hours of collected data to successfully find encryption key • 2007 – WEP cracked under 60 seconds by researchers from Germany • WPA • A quick preliminary solution to WEP issues • However vulnerable to a password guessing attack ...
... • Original attack required hours of collected data to successfully find encryption key • 2007 – WEP cracked under 60 seconds by researchers from Germany • WPA • A quick preliminary solution to WEP issues • However vulnerable to a password guessing attack ...
Computer Networks - Texas State Department of Computer Science
... On a cable modem in your house… To download a music file of some sort To download a 3GB movie in MP4 format ...
... On a cable modem in your house… To download a music file of some sort To download a 3GB movie in MP4 format ...
Computer Networks
... Each device name in a network must be unique. NetBEUI software installed on each of the networked computers is all that is necessary to configure devices in order to share resources and create a network. If a small company does want to connect to the Internet, the necessary software and protocols ar ...
... Each device name in a network must be unique. NetBEUI software installed on each of the networked computers is all that is necessary to configure devices in order to share resources and create a network. If a small company does want to connect to the Internet, the necessary software and protocols ar ...
NETWORK PLANNING TASK FORCE “FY `06 FALL SESSIONS”
... internal routers, faculty, staff, students with legitimate need for remote access to Windows file sharing, Exchange, etc. need a mechanism or approach to get through the filters. ■ Option 1: Central Campus VPN Service ■ Advantages ■ Besides providing remote access to Netbios, also provides network e ...
... internal routers, faculty, staff, students with legitimate need for remote access to Windows file sharing, Exchange, etc. need a mechanism or approach to get through the filters. ■ Option 1: Central Campus VPN Service ■ Advantages ■ Besides providing remote access to Netbios, also provides network e ...
Computer Networking
... • ATM physical layer : deals with voltages, bit timings, and framing on the physical dedium • ATM layer : the core of the ATM standard, defines the structure of the ATM cell • AAL : roughly analogous to the transport layer in the Internet Protocol stack : support many different types of services – A ...
... • ATM physical layer : deals with voltages, bit timings, and framing on the physical dedium • ATM layer : the core of the ATM standard, defines the structure of the ATM cell • AAL : roughly analogous to the transport layer in the Internet Protocol stack : support many different types of services – A ...
Notes chapter 6
... wireless link typically used to connect mobile(s) to base station also used as backbone link multiple access protocol coordinates link access various data rates, ...
... wireless link typically used to connect mobile(s) to base station also used as backbone link multiple access protocol coordinates link access various data rates, ...
Prevent Interference Between Co-Located, Wireless
... Cygnet and XSPOC polling hosts were still reporting errors. There were 2 types of errors reported most commonly by Cygnet and XSPOC. One of the errors was a "socket connect failure". This meant Cygnet or XSPOC could not even communicate with the radio to create a terminal session. Looking into speci ...
... Cygnet and XSPOC polling hosts were still reporting errors. There were 2 types of errors reported most commonly by Cygnet and XSPOC. One of the errors was a "socket connect failure". This meant Cygnet or XSPOC could not even communicate with the radio to create a terminal session. Looking into speci ...
Wireless Tips - Pearsoncmg.com
... Wireless WANs are used by corporations to connect buildings together and by wireless ISPs (WISPs) to connect businesses and residences to the Internet. Although more and more people are now using wireless local-area networks (LANs) either at work or at home, far fewer people are familiar with outdoo ...
... Wireless WANs are used by corporations to connect buildings together and by wireless ISPs (WISPs) to connect businesses and residences to the Internet. Although more and more people are now using wireless local-area networks (LANs) either at work or at home, far fewer people are familiar with outdoo ...
Chapter 3
... systems “on the same page” asynchronous - start signal is sent, then a character, then a stop signal – receiving system sets up a timing mechanism when start signal is received – slow transmission rates ...
... systems “on the same page” asynchronous - start signal is sent, then a character, then a stop signal – receiving system sets up a timing mechanism when start signal is received – slow transmission rates ...
ppt - The Stanford University InfoLab
... web” anymore than UPS is the interstate highway system. • But, we will focus on services available on the ‘Net such as the world wide web. ...
... web” anymore than UPS is the interstate highway system. • But, we will focus on services available on the ‘Net such as the world wide web. ...
Study Guide
... 21. When converting to binary from dotted decimal, remember that each group, which consists of one to three decimal digits represents a group of ______________ digits. If the decimal number that is being converted is less than 128, ______ will be needed to be added to the left of the equivalent bina ...
... 21. When converting to binary from dotted decimal, remember that each group, which consists of one to three decimal digits represents a group of ______________ digits. If the decimal number that is being converted is less than 128, ______ will be needed to be added to the left of the equivalent bina ...
CSCI-1305 Introduction To Information Technology
... • His idea has become a key element in just about every computer network including the Internet. ...
... • His idea has become a key element in just about every computer network including the Internet. ...
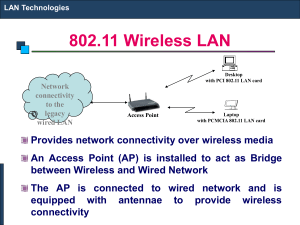
802.11 Wireless LAN
... A repeater receives a signal, regenerates it, and passes it on. It can regenerate and retime network signals at the bit level to allow them to travel a longer distance on the media. It operates at Physical Layer of OSI The Four Repeater Rule for 10-Mbps Ethernet should be used as a standard when ext ...
... A repeater receives a signal, regenerates it, and passes it on. It can regenerate and retime network signals at the bit level to allow them to travel a longer distance on the media. It operates at Physical Layer of OSI The Four Repeater Rule for 10-Mbps Ethernet should be used as a standard when ext ...
1- A well-structured document usually contains a number of clues
... 8- transceivers, perform both the sending and receiving of signals (T) 9- (WANs) connect together two or more LANs that are geographically separated. (T) 10-Messages between nodes are sent in one continuous stream and no need to broken up into small chunks called frames (F) 11- A repeater increases ...
... 8- transceivers, perform both the sending and receiving of signals (T) 9- (WANs) connect together two or more LANs that are geographically separated. (T) 10-Messages between nodes are sent in one continuous stream and no need to broken up into small chunks called frames (F) 11- A repeater increases ...
Slide 1
... • IEEE standard for low cost, low speed, low power wireless communication • Targeted at device to device communication • Supports multiple frequencies, including the worldwide unlicensed 2.4 GHz band – Sixteen 802.15.4 channels – Shares spectrum with 802.11 (WiFi) and Bluetooth ...
... • IEEE standard for low cost, low speed, low power wireless communication • Targeted at device to device communication • Supports multiple frequencies, including the worldwide unlicensed 2.4 GHz band – Sixteen 802.15.4 channels – Shares spectrum with 802.11 (WiFi) and Bluetooth ...
Enterprise Ethernet gets a sharper edge TextStart Highly reliable
... As Fig. 1 (see PDF) shows, the LFR Ethernet removes loops and the STP. The terminal server or PC connects with two access switches through two bundled links to enhance access reliability. Two (or more) access switches are stacked, and aggregation switches are arranged within a cluster switching sys ...
... As Fig. 1 (see PDF) shows, the LFR Ethernet removes loops and the STP. The terminal server or PC connects with two access switches through two bundled links to enhance access reliability. Two (or more) access switches are stacked, and aggregation switches are arranged within a cluster switching sys ...
Chapter 6 slides, Computer Networking, 3rd edition
... access of data frames: avoid collisions of long data frames sender first transmits small request-to-send (RTS) packets to BS using CSMA RTSs may still collide with each other (but they’re short) BS broadcasts clear-to-send CTS in response to RTS ...
... access of data frames: avoid collisions of long data frames sender first transmits small request-to-send (RTS) packets to BS using CSMA RTSs may still collide with each other (but they’re short) BS broadcasts clear-to-send CTS in response to RTS ...
Chapter 6 slides, Computer Networking, 3rd edition
... # wireless Internet-connected devices equals # wireline Internet-connected devices laptops, Internet-enabled phones promise anytime untethered Internet access ...
... # wireless Internet-connected devices equals # wireline Internet-connected devices laptops, Internet-enabled phones promise anytime untethered Internet access ...
Networking - Institute of Mathematics and Informatics
... • Computer communications – Exchange of information between computers for the purpose of cooperative action ...
... • Computer communications – Exchange of information between computers for the purpose of cooperative action ...
The Infrastructure Technologies
... Signals transmitted in the context of a Carrier Signal Known frequency Known amplitude ...
... Signals transmitted in the context of a Carrier Signal Known frequency Known amplitude ...
NETWORK DEVICES.doc
... This is a communications device that connects multiple computers or other routers together and transmits data to its correct destination on a network. A router can be used on any size network. On the largest scale, routers along the internet backbone forward data packets to their destination using t ...
... This is a communications device that connects multiple computers or other routers together and transmits data to its correct destination on a network. A router can be used on any size network. On the largest scale, routers along the internet backbone forward data packets to their destination using t ...
Cisco 646-203
... A. access to backup data B. rapid access to rich media used in online training C. firewall protection for storage-area networks (SANs) D. network redundancy to ensure file access in branch offices Answer: A QUESTION 9 A company with 100 employees predicts that its employee number will triple in the ...
... A. access to backup data B. rapid access to rich media used in online training C. firewall protection for storage-area networks (SANs) D. network redundancy to ensure file access in branch offices Answer: A QUESTION 9 A company with 100 employees predicts that its employee number will triple in the ...
No Slide Title
... Summary of technical issues Already done end devices, MTS security roaming ...
... Summary of technical issues Already done end devices, MTS security roaming ...
Internet History and Architectural Principles
... Numerical example How long does it take to send a file of 640,000 bits from host A to host B over a circuit-switched network? All links are 1.536 Mbps Each link uses TDM with 24 slots/sec 500 msec to establish end-to-end circuit ...
... Numerical example How long does it take to send a file of 640,000 bits from host A to host B over a circuit-switched network? All links are 1.536 Mbps Each link uses TDM with 24 slots/sec 500 msec to establish end-to-end circuit ...
Computer Vision I: Introduction
... communications device (hub/switch) A node sends a signal to the hub ...
... communications device (hub/switch) A node sends a signal to the hub ...