technical summary 2011
... WSN are a very important instrument to fight digital divide, especially to provide links in those areas without network connectivity. Different people has the same attitudes to pay for mobile services, but a large diffusion of them depends on several factors : economic, social, cultural, etc… ...
... WSN are a very important instrument to fight digital divide, especially to provide links in those areas without network connectivity. Different people has the same attitudes to pay for mobile services, but a large diffusion of them depends on several factors : economic, social, cultural, etc… ...
PPT - 清華大學資訊工程學系
... each other across a network. – Example 1:先在資電館前集合,再出發到餐廳 – Example 2: bus route and schedule – Example 3: traffic regulations ...
... each other across a network. – Example 1:先在資電館前集合,再出發到餐廳 – Example 2: bus route and schedule – Example 3: traffic regulations ...
Network Related Registry Keys
... • BSSID – Basic Service Set Identifier (i.e. MAC address) • Encryption – WEP (Wired Equivalent Privacy) – TKIP (Temporal Key Integrity Protocol) – AES (Advanced Encryption Standard) ...
... • BSSID – Basic Service Set Identifier (i.e. MAC address) • Encryption – WEP (Wired Equivalent Privacy) – TKIP (Temporal Key Integrity Protocol) – AES (Advanced Encryption Standard) ...
requirements for Network Monitoring
... - Each prototype forecasts process-to-process network performance (latency and bandwidth) and available CPU percentage for each machine that it monitors. - The AppLeS scheduling methodology makes extensive use of its facilities and prototype implementations for Legion and Globus/Nexus have been deve ...
... - Each prototype forecasts process-to-process network performance (latency and bandwidth) and available CPU percentage for each machine that it monitors. - The AppLeS scheduling methodology makes extensive use of its facilities and prototype implementations for Legion and Globus/Nexus have been deve ...
Networking
... It has no server. It allows any computer to share the hardware, software, or information located on any other computer in the network. It is commonly found in small organisations. ...
... It has no server. It allows any computer to share the hardware, software, or information located on any other computer in the network. It is commonly found in small organisations. ...
Slide 1 - University of Dayton
... with a wireless network hub or router, which is also used to bridge the wireless network to traditional ethernet or provide a shared Internet connection. Wi-Fi (for Wireless Fidelity) – also called IEEE 802.11b standard, the current popular standard for wireless networking supports data rate of 11 ...
... with a wireless network hub or router, which is also used to bridge the wireless network to traditional ethernet or provide a shared Internet connection. Wi-Fi (for Wireless Fidelity) – also called IEEE 802.11b standard, the current popular standard for wireless networking supports data rate of 11 ...
ALevelComputing_Session13
... Protocols are organised into “layers” which link into each other. This means it is possible to “tweak” individual layers without affecting the whole network standard. Protocols can be divide into 2 parts: logically based and physically based. ...
... Protocols are organised into “layers” which link into each other. This means it is possible to “tweak” individual layers without affecting the whole network standard. Protocols can be divide into 2 parts: logically based and physically based. ...
Wireless Networks and Mobile Communication Systems NET 332D
... – Requires intelligent way to make efficient use of limited bandwidth in error-prone environment ...
... – Requires intelligent way to make efficient use of limited bandwidth in error-prone environment ...
Deployed and Emerging Security Systems for the Internet
... • (also called proxy server) – connections outside are allowed only through proxy – internal host contact proxy, requests connection with the outside, after authenticating the user and if it is configured to provide service for this type of connection (ftp, web, telnet, etc.) proxy relays packets to ...
... • (also called proxy server) – connections outside are allowed only through proxy – internal host contact proxy, requests connection with the outside, after authenticating the user and if it is configured to provide service for this type of connection (ftp, web, telnet, etc.) proxy relays packets to ...
NEMO-Enabled Localized Mobility Support for Internet
... • Users demand the ability to keep their ongoing communications while changing their point of attachment to the network as they move around – E.g., when a user leaves a coffee shop and gets on a bus – buses that move between pavilions at a fair or – a train that moves from one terminal to another at ...
... • Users demand the ability to keep their ongoing communications while changing their point of attachment to the network as they move around – E.g., when a user leaves a coffee shop and gets on a bus – buses that move between pavilions at a fair or – a train that moves from one terminal to another at ...
An Overview of MANET: History, Challenges and Applications
... We can characterized the life cycle of mobile ad hoc network into first, second and third generation. Present ad hoc network are considered the third generation [2][3]. The first generation of ad hoc network can be traced back to 1970’s. In 1970’s, these are called Packet Radio Network (PRNET) [4]. ...
... We can characterized the life cycle of mobile ad hoc network into first, second and third generation. Present ad hoc network are considered the third generation [2][3]. The first generation of ad hoc network can be traced back to 1970’s. In 1970’s, these are called Packet Radio Network (PRNET) [4]. ...
The Deep East Texas Council of Governments (DETCOG)
... band answered the need for true real-time communications with extremely low latency and high QoS. In addition, the RADWIN solution proved to be highly cost-effective for DETCOG. RADWIN’s multiband radio capabilities allowed for flexible radio planning during initial network deployment and for future ...
... band answered the need for true real-time communications with extremely low latency and high QoS. In addition, the RADWIN solution proved to be highly cost-effective for DETCOG. RADWIN’s multiband radio capabilities allowed for flexible radio planning during initial network deployment and for future ...
hw3 - OpenLab
... around the corner that could demand even more bandwidth. The groundbreaking analysis identifies a critical issue facing the Internet – we must take the necessary steps to build out network capacity or potentially face Internet gridlock that could wreak mayhem on Internet services. The article, “The ...
... around the corner that could demand even more bandwidth. The groundbreaking analysis identifies a critical issue facing the Internet – we must take the necessary steps to build out network capacity or potentially face Internet gridlock that could wreak mayhem on Internet services. The article, “The ...
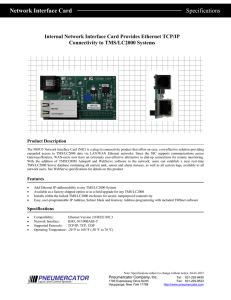
Network Interface Card Specifications
... Add Ethernet IP-addressability to any TMS/LC2000 System Available as a factory-shipped option or as a field upgrade for any TMS/LC2000 Installs within the locked TMS/LC2000 enclosure for secure, tamperproof connectivity Easy, user-programmable IP Address, Subnet Mask and Gateway Address programming ...
... Add Ethernet IP-addressability to any TMS/LC2000 System Available as a factory-shipped option or as a field upgrade for any TMS/LC2000 Installs within the locked TMS/LC2000 enclosure for secure, tamperproof connectivity Easy, user-programmable IP Address, Subnet Mask and Gateway Address programming ...
Networks
... HomeRF, 802.11b – radio waves; NIC connects to transceiver with antenna or to wireless access point Ethernet – twisted pair cables; Ethernet NIC cards and cables to connect devices ...
... HomeRF, 802.11b – radio waves; NIC connects to transceiver with antenna or to wireless access point Ethernet – twisted pair cables; Ethernet NIC cards and cables to connect devices ...
Networks and Telecommunications
... Sometimes one building will contain a few small LANs, and occasionally a LAN will span a group of nearby buildings Wide Area Network (WAN) - is a geographically dispersed telecommunications network Metropolitan Area Network (MAN) - interconnects users in a geographic area or region larger than ...
... Sometimes one building will contain a few small LANs, and occasionally a LAN will span a group of nearby buildings Wide Area Network (WAN) - is a geographically dispersed telecommunications network Metropolitan Area Network (MAN) - interconnects users in a geographic area or region larger than ...
Joint Topology Control and Routing in Mobile Ad Hoc Networks
... s how to bring together ways of controlling the flow of data over such networks simultaneously with minimising the in http://www.completewebresource.com/wireless-area%20network.JPG ...
... s how to bring together ways of controlling the flow of data over such networks simultaneously with minimising the in http://www.completewebresource.com/wireless-area%20network.JPG ...
Workware Wireless FAQ - AV/IT Installer
... secure application that runs on your company’s enterprise network. From iOS or Android devices, you have the option to open a web browser window and select your preferred cloud service (eg. Google Drive, Dropbox, or Facebook) to share media or files from the cloud to the session. Or on Windows or Mac ...
... secure application that runs on your company’s enterprise network. From iOS or Android devices, you have the option to open a web browser window and select your preferred cloud service (eg. Google Drive, Dropbox, or Facebook) to share media or files from the cloud to the session. Or on Windows or Mac ...
The Internet as a Universal Communication Network
... “A cellular data network can provide relatively low-speed data service over a large coverage area. On the other hand, WLAN provides high-speed data service over a geographically small area. An integrated network combines the strengths of each.” Source:A. Salkintzis, C. Fors, R. Pazhyannur, Motorola, ...
... “A cellular data network can provide relatively low-speed data service over a large coverage area. On the other hand, WLAN provides high-speed data service over a geographically small area. An integrated network combines the strengths of each.” Source:A. Salkintzis, C. Fors, R. Pazhyannur, Motorola, ...
A Present-Day Approach For 5G Technology
... transactions (e-payment, e-transaction) support, will offer services like documentation. Prio r to the fifth generation technology that users provide experienced very high bandwidth. This powerful fifth-generation technologies and creates a great demand in the future in which var ious new advanced f ...
... transactions (e-payment, e-transaction) support, will offer services like documentation. Prio r to the fifth generation technology that users provide experienced very high bandwidth. This powerful fifth-generation technologies and creates a great demand in the future in which var ious new advanced f ...
Chapter 5 Overview of Network Services - computerscience
... • To use Active Directory, at least one server must be configured as a Domain Controller (DC). • It is recommended that there be at least two DCs in each domain, for fault tolerance. • Replication is the process of copying data from one computer to one or more other computers and synchronizing that ...
... • To use Active Directory, at least one server must be configured as a Domain Controller (DC). • It is recommended that there be at least two DCs in each domain, for fault tolerance. • Replication is the process of copying data from one computer to one or more other computers and synchronizing that ...
Chapter 6 slides, Computer Networking, 3rd edition
... frames containing AP’s name (SSID) and MAC address Host selects (the best) AP to associate with may perform authentication to get access will typically run DHCP to get IP address in AP’s subnet ...
... frames containing AP’s name (SSID) and MAC address Host selects (the best) AP to associate with may perform authentication to get access will typically run DHCP to get IP address in AP’s subnet ...
Network Administrator - San Luis Obispo Superior Court
... implements, and maintains the Court’s data network which includes: local area and wide area network circuits, routers, servers and other equipment to meet departmental and courtwide requirements. Responsibilities of this position include the creation, administration and maintenance of standards and ...
... implements, and maintains the Court’s data network which includes: local area and wide area network circuits, routers, servers and other equipment to meet departmental and courtwide requirements. Responsibilities of this position include the creation, administration and maintenance of standards and ...