Network Configuration Guide
... more than one router, then you’ll need to bypass all but one of them. The first step is determining whether or not there is a second router present. Follow the cable from your computer, does it connect directly into the back of the modem? If so, then you only have one router (The modem). You will ne ...
... more than one router, then you’ll need to bypass all but one of them. The first step is determining whether or not there is a second router present. Follow the cable from your computer, does it connect directly into the back of the modem? If so, then you only have one router (The modem). You will ne ...
Optimal design of Kelly / Whittle network
... formulate the transition rates. Show that the equilibrium distribution has a product form and satisfies partial balance. Give the distribution of the state observed by a customer arriving to (and entering) queue 2. 7. Again consider the tandem network of part 5. Assume that a customer arriving to a ...
... formulate the transition rates. Show that the equilibrium distribution has a product form and satisfies partial balance. Give the distribution of the state observed by a customer arriving to (and entering) queue 2. 7. Again consider the tandem network of part 5. Assume that a customer arriving to a ...
Routers - Personal Web Pages
... facilitate the exchange of routing information between networks allowing routers to build routing tables dynamically ...
... facilitate the exchange of routing information between networks allowing routers to build routing tables dynamically ...
Understanding Ethernet Switches and Routers
... come with a built-in switch so that you can connect several Ethernet devices using just one device. So again, what is the difference between an Ethernet router and an Ethernet switch? We will refer back to the Open Systems Interconnection Model. Revisiting the OSI Model In Figure 1 you will see the ...
... come with a built-in switch so that you can connect several Ethernet devices using just one device. So again, what is the difference between an Ethernet router and an Ethernet switch? We will refer back to the Open Systems Interconnection Model. Revisiting the OSI Model In Figure 1 you will see the ...
Human Operator Perspective to Autonomic Network
... should be designed in order to be functional from the human operator’s viewpoint. Thus, it is important to learn what the characteristics of the HNO work are from the perspective of these professionals and what the specific demands are that the work sets on human performance. Also the conceptions re ...
... should be designed in order to be functional from the human operator’s viewpoint. Thus, it is important to learn what the characteristics of the HNO work are from the perspective of these professionals and what the specific demands are that the work sets on human performance. Also the conceptions re ...
NeuroEvolution of Augmenting Topologies (Neat)
... neuroevolution methods that begin with large fixed or randomized topologies; by elaborating on existing solutions, it can gradually construct even highly complex solutions. In this dissertation, NEAT is first shown faster than traditional approaches on a challenging reinforcement learning benchmark ...
... neuroevolution methods that begin with large fixed or randomized topologies; by elaborating on existing solutions, it can gradually construct even highly complex solutions. In this dissertation, NEAT is first shown faster than traditional approaches on a challenging reinforcement learning benchmark ...
Multihoming support based on mobile node protocol LIN6
... Mobile computing, which enables access to the Internet on the street, is getting more popular nowadays, as handy phones become more functional, and as wireless LANs and the Internet spreads. Network protocols that support “mobility” are proposed by some organizations such as Internet Engineering Tas ...
... Mobile computing, which enables access to the Internet on the street, is getting more popular nowadays, as handy phones become more functional, and as wireless LANs and the Internet spreads. Network protocols that support “mobility” are proposed by some organizations such as Internet Engineering Tas ...
[2016-NEW!] 200-120 New Questions and Answers -
... A. A higher level of network security can be reached by separating sensitive data traffic from other network traffic. B. A more efficient use of bandwidth can be achieved allowing many physical groups to use the same network infrastructure. C. A more efficient use of bandwidth can be achieved allowi ...
... A. A higher level of network security can be reached by separating sensitive data traffic from other network traffic. B. A more efficient use of bandwidth can be achieved allowing many physical groups to use the same network infrastructure. C. A more efficient use of bandwidth can be achieved allowi ...
Module 2: Assigning IP Addresses in a Multiple Subnet
... Routes packets to other networks Is used when the internal routing table on the host has no information on the destination subnet DHCP automatically delivers the IP address for the default gateway to the client To configure the client manually for the default gateway, use the General tab on the ...
... Routes packets to other networks Is used when the internal routing table on the host has no information on the destination subnet DHCP automatically delivers the IP address for the default gateway to the client To configure the client manually for the default gateway, use the General tab on the ...
Chapter 11 Interior Routing Protocols
... —By kth stage, shortest paths to k nodes closest to (least cost away from) source have been determined —T: Set of nodes so far incorporated —Stage (k + 1), node not in T with shortest path from source added to T —As each node added to T, path from source defined ...
... —By kth stage, shortest paths to k nodes closest to (least cost away from) source have been determined —T: Set of nodes so far incorporated —Stage (k + 1), node not in T with shortest path from source added to T —As each node added to T, path from source defined ...
ECI Emanuel Nachum CANTO 2006
... Large share are at GbE & 10 GbE rates Optical transport delivers majority of IP based services WDM – a service delivery and transport vehicle Optical Networks Division ...
... Large share are at GbE & 10 GbE rates Optical transport delivers majority of IP based services WDM – a service delivery and transport vehicle Optical Networks Division ...
1.You have a network address of 202.200.55.0 with a subnet mask
... (b) Because every subnet must use a different mask to avoid conflicts. (c) Because it allows us to uniquely identify each subnet by its mask number. (d) Because it allows each subnet in a routed system to be correctly sized for the requirement. ...
... (b) Because every subnet must use a different mask to avoid conflicts. (c) Because it allows us to uniquely identify each subnet by its mask number. (d) Because it allows each subnet in a routed system to be correctly sized for the requirement. ...
Chapter 1: A First Look at Windows 2000 Professional
... Routers can provide VPN connections Router to router VPN connections allow remote sites to connect to corporate headquarters using the Internet Extranet connections can also be made between corporate partners ...
... Routers can provide VPN connections Router to router VPN connections allow remote sites to connect to corporate headquarters using the Internet Extranet connections can also be made between corporate partners ...
A Survey of Computer Network Topology and Analysis Examples
... Reference 8 discusses the concept of a Tree-Bus Topological Network. Key to this concept is the absence of any intermediate processing, there is no active component on the net between any two given nodes, with the possible exception of some signal power boost devices. Any packet sent out from one no ...
... Reference 8 discusses the concept of a Tree-Bus Topological Network. Key to this concept is the absence of any intermediate processing, there is no active component on the net between any two given nodes, with the possible exception of some signal power boost devices. Any packet sent out from one no ...
Mobility Models and Traces
... has been online for time ttt, sent/received bbb bytes – Every 30 minutes, each online user is reported for its traffic usage in the past 30 mins ...
... has been online for time ttt, sent/received bbb bytes – Every 30 minutes, each online user is reported for its traffic usage in the past 30 mins ...
Slides - TERENA Networking Conference 2008
... • Different stakeholders working together to provide a quality service • That reaches the users! • GÉANT2 is not just a backbone network! ...
... • Different stakeholders working together to provide a quality service • That reaches the users! • GÉANT2 is not just a backbone network! ...
slides ppt
... • Let RTT be the round-trip time [sec] Let xr be the mean bandwidth of flow r [pkts/sec] Let y be the total bandwidth of all flows [pkts/sec] Let C be the total available capacity [pkts/sec] • TCP and the network act so as to solve maximise r U(xr) - (y - C log y/C-1)+ over xr where y=r xr ...
... • Let RTT be the round-trip time [sec] Let xr be the mean bandwidth of flow r [pkts/sec] Let y be the total bandwidth of all flows [pkts/sec] Let C be the total available capacity [pkts/sec] • TCP and the network act so as to solve maximise r U(xr) - (y - C log y/C-1)+ over xr where y=r xr ...
Slides for Chapter 3: Networking and Internetworking
... differ. Encryption is also performed in this layer, if required. At this level reliability and adaptation are performed, such as detection of failures and automatic recovery. This is the lowest level at which messages (rather than packets) are handled. Messages are addressed to communication ports a ...
... differ. Encryption is also performed in this layer, if required. At this level reliability and adaptation are performed, such as detection of failures and automatic recovery. This is the lowest level at which messages (rather than packets) are handled. Messages are addressed to communication ports a ...
ITRC2008-nakao
... Birth of Private PlanetLab (enabled by MyPLC) PlanetLab → Public PlanetLab Private PlanetLab Smaller-scale, experimental PlanetLab-like environment ...
... Birth of Private PlanetLab (enabled by MyPLC) PlanetLab → Public PlanetLab Private PlanetLab Smaller-scale, experimental PlanetLab-like environment ...
Security+ Guide to Network Security Fundamentals, Fourth Edition
... and .org top level domains with IPv6 support has increased by 1,900 percent. “This dramatic increase can be primarily attributed to the introduction of support of IPv6 by a single registrar, GoDaddy,” said Infoblox, the IT network automation and control company that sponsored the census, in a statem ...
... and .org top level domains with IPv6 support has increased by 1,900 percent. “This dramatic increase can be primarily attributed to the introduction of support of IPv6 by a single registrar, GoDaddy,” said Infoblox, the IT network automation and control company that sponsored the census, in a statem ...
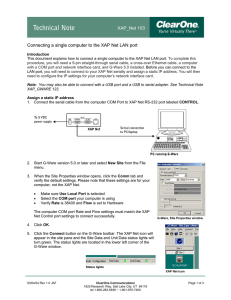
Connecting a Single Computer to the XAP Net LAN Port
... connects, a XAP Net icon appears in the Site pane. The Site Data and Unit Data status lights in the lower left corner of the G-Ware window will turn green. To make a crossover Ethernet cable An Ethernet crossover cable is an unshielded twisted pair Category 5 (UTP-CAT 5) network cable. The XAP Net h ...
... connects, a XAP Net icon appears in the Site pane. The Site Data and Unit Data status lights in the lower left corner of the G-Ware window will turn green. To make a crossover Ethernet cable An Ethernet crossover cable is an unshielded twisted pair Category 5 (UTP-CAT 5) network cable. The XAP Net h ...
ECE544 - WINLAB
... – concept of multiple “logical IP subnets” (LIS) • Divided a large ATM into a number of LISs connected by routers ...
... – concept of multiple “logical IP subnets” (LIS) • Divided a large ATM into a number of LISs connected by routers ...
An Open Source Network Monitoring Tool for Software Defined
... relatively early stage of adoption, major networking vendors are increasingly starting to define their strategy around this technology. While there has been a hesitancy to completely migrate networks to an SDN-based model, networking operators, vendors and providers are all increasingly adopting SDN ...
... relatively early stage of adoption, major networking vendors are increasingly starting to define their strategy around this technology. While there has been a hesitancy to completely migrate networks to an SDN-based model, networking operators, vendors and providers are all increasingly adopting SDN ...






![[2016-NEW!] 200-120 New Questions and Answers -](http://s1.studyres.com/store/data/000108812_1-bba6a7d69201d6f7aa4d0f7684ac7604-300x300.png)