Introduction to Routing
... That is another static algorithm, in witch every incoming packet is sent out on every outgoing line except the one it arrived on. Flooding generates infinite number of duplicate packets unless some measures are taken to damp the process. One such measure is to have a hop counter in the header of eac ...
... That is another static algorithm, in witch every incoming packet is sent out on every outgoing line except the one it arrived on. Flooding generates infinite number of duplicate packets unless some measures are taken to damp the process. One such measure is to have a hop counter in the header of eac ...
A Distributive Polling Based Mobile Data Gathering in WSN
... environment, a pure static WSN could face the problems like covering the whole area of interest, holes in the coverage area. Some of the WSN architectures have been proposed based on Mobile Elements. There is large number of approaches to resolve the above problem. Clustering is a method used to ove ...
... environment, a pure static WSN could face the problems like covering the whole area of interest, holes in the coverage area. Some of the WSN architectures have been proposed based on Mobile Elements. There is large number of approaches to resolve the above problem. Clustering is a method used to ove ...
Enabling Hitless Engineering of MPLS Networks
... Engineering tools to address fragmentation – “Traffic Engineering puts traffic where the bandwidth is, Network Engineering creates bandwidth where the traffic will be..” – Relatively little focus on engineering tools – Network engineering requires “global” knowledge, TE is a per-LSP ...
... Engineering tools to address fragmentation – “Traffic Engineering puts traffic where the bandwidth is, Network Engineering creates bandwidth where the traffic will be..” – Relatively little focus on engineering tools – Network engineering requires “global” knowledge, TE is a per-LSP ...
Chs6-8min
... send datagram to next-hop specified in table (ENCAPSULATE) and quit; compute N, the network prefix of address D; if N matches any directly-connected network address deliver datagram to destination D over that network (ENCAPSULATE); else if table contains a route for network prefix N send datagram to ...
... send datagram to next-hop specified in table (ENCAPSULATE) and quit; compute N, the network prefix of address D; if N matches any directly-connected network address deliver datagram to destination D over that network (ENCAPSULATE); else if table contains a route for network prefix N send datagram to ...
Chapter 20 - William Stallings, Data and Computer Communications
... Transport Protocols The foregoing observations should make us reconsider the widely held view that birds live only in the present. In fact, birds are aware of more than immediately present stimuli; they remember the past and anticipate the future. —The Minds of Birds, Alexander Skutch ...
... Transport Protocols The foregoing observations should make us reconsider the widely held view that birds live only in the present. In fact, birds are aware of more than immediately present stimuli; they remember the past and anticipate the future. —The Minds of Birds, Alexander Skutch ...
Transport Protocols
... Transport Protocols The foregoing observations should make us reconsider the widely held view that birds live only in the present. In fact, birds are aware of more than immediately present stimuli; they remember the past and anticipate the future. —The Minds of Birds, Alexander Skutch ...
... Transport Protocols The foregoing observations should make us reconsider the widely held view that birds live only in the present. In fact, birds are aware of more than immediately present stimuli; they remember the past and anticipate the future. —The Minds of Birds, Alexander Skutch ...
1 Kyung Hee University Chapter 19 Network Layer
... If the address is given in binary notation, the first few bits can tell us the class of the address. If the address is given in decimal-dotted notation, the first byte defines the class. ...
... If the address is given in binary notation, the first few bits can tell us the class of the address. If the address is given in decimal-dotted notation, the first byte defines the class. ...
NwksTCPIP
... An algorithm for coalescing a number of small outgoing messages, and sending them all at once. As long as there is a sent packet for which the sender has received no acknowledgment, the sender should keep buffering its output until it has a full packet's worth of output, so that output can be sent a ...
... An algorithm for coalescing a number of small outgoing messages, and sending them all at once. As long as there is a sent packet for which the sender has received no acknowledgment, the sender should keep buffering its output until it has a full packet's worth of output, so that output can be sent a ...
Chapter4_4th - Northwestern University
... Datagrams with source or destination in this network have 10.0.0/24 address for source, destination (as usual) ...
... Datagrams with source or destination in this network have 10.0.0/24 address for source, destination (as usual) ...
Computer Networks Homework 1
... transmission rate is known and not bursty, bandwidth can be reserved for each application session circuit with no significant waste. In addition, we need not worry greatly about the overhead costs of setting up and tearing down a circuit connection, which are amortized over the lengthy duration of a ...
... transmission rate is known and not bursty, bandwidth can be reserved for each application session circuit with no significant waste. In addition, we need not worry greatly about the overhead costs of setting up and tearing down a circuit connection, which are amortized over the lengthy duration of a ...
Chapter 2 Hardware Installation
... check the VPI and VCI Parameters. Change these settings if they are inconsistent with the information your DSL service provider provides. ...
... check the VPI and VCI Parameters. Change these settings if they are inconsistent with the information your DSL service provider provides. ...
Multicast - s3.amazonaws.com
... msg broadcast on LAN to all hosts host: Host Membership Report msg to indicate group membership ...
... msg broadcast on LAN to all hosts host: Host Membership Report msg to indicate group membership ...
Universal Ethernet network range extender
... Ethernet is the ubiquitous technology for Local Area Network (LAN) installation, and the majority of networks in place use the 100BASE-T network standards. However, many security installations demand network connections that exceed the maximum 100 metres (328 feet) distance limit for wired Ethernet. ...
... Ethernet is the ubiquitous technology for Local Area Network (LAN) installation, and the majority of networks in place use the 100BASE-T network standards. However, many security installations demand network connections that exceed the maximum 100 metres (328 feet) distance limit for wired Ethernet. ...
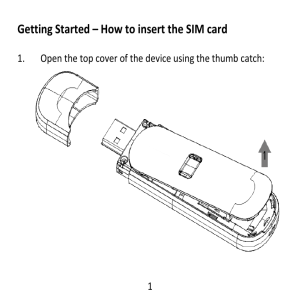
User Guide
... antenna to connect to the mobile network. To get the best performance from your device do not cover or shield the device in any way as this will lead to increased output power. Always leave a clear space around the device to allow the transmit and receive signals to propagate. It is not intended to ...
... antenna to connect to the mobile network. To get the best performance from your device do not cover or shield the device in any way as this will lead to increased output power. Always leave a clear space around the device to allow the transmit and receive signals to propagate. It is not intended to ...
modul 3 LOCAL AREA NETWORK
... 1. Prove that the total number of links in a point-to-point network with N computers is (N2-N)/2 2. For each of bus, star and ring topologies, discuss the consequences if a station has broken. 3. In most technologies, a sending station can choose the amount of data in a frame, but the frame header i ...
... 1. Prove that the total number of links in a point-to-point network with N computers is (N2-N)/2 2. For each of bus, star and ring topologies, discuss the consequences if a station has broken. 3. In most technologies, a sending station can choose the amount of data in a frame, but the frame header i ...
PPT 1.0M
... that do not work when integrated together. • Inconsistency between different releases of Internet Drafts, e.g. IPv6 mobility support drafts #13, #16, etc. • Differences between implementations built on different OS kernels. • Not new problems, but really experiencing them are good lessons for deploy ...
... that do not work when integrated together. • Inconsistency between different releases of Internet Drafts, e.g. IPv6 mobility support drafts #13, #16, etc. • Differences between implementations built on different OS kernels. • Not new problems, but really experiencing them are good lessons for deploy ...
Chapter 25 The Internet
... • Uses Layer 7 – browsers communicate directly with the proxy server software when desiring a Web site © 2010 The McGraw-Hill Companies, Inc. All rights reserved ...
... • Uses Layer 7 – browsers communicate directly with the proxy server software when desiring a Web site © 2010 The McGraw-Hill Companies, Inc. All rights reserved ...
(LAN) INsecurity 2005 - NotBobTec Enterprises, Incorporeal
... Quick Review of WLAN Security Terminology ...
... Quick Review of WLAN Security Terminology ...
Configuring, Managing, and Troubleshooting
... Configure Routing and Remote Access user authentication. Manage remote access. Manage TCP/IP routing. Implement secure access between private networks. Troubleshoot user access to remote access services. Troubleshoot Routing and Remote Access routing. ...
... Configure Routing and Remote Access user authentication. Manage remote access. Manage TCP/IP routing. Implement secure access between private networks. Troubleshoot user access to remote access services. Troubleshoot Routing and Remote Access routing. ...
The Basics of Application Monitoring
... While classful addressing was the basis for IP internetworking, the limitations became so great that without new methods of controlling IP allocation, the available IP address space would not have lasted into the late 90’s. It was clear that steps had to be taken to preserve IPv4 address space where ...
... While classful addressing was the basis for IP internetworking, the limitations became so great that without new methods of controlling IP allocation, the available IP address space would not have lasted into the late 90’s. It was clear that steps had to be taken to preserve IPv4 address space where ...
Document
... (QoS) of the call. In a network with dedicated bandwidth for VoIP, we can calculate the max number of simultaneous calls based on the allocated bandwidth. ...
... (QoS) of the call. In a network with dedicated bandwidth for VoIP, we can calculate the max number of simultaneous calls based on the allocated bandwidth. ...
Network Virtualization for QoS-Aware Resource Management
... and incoming bandwidth, respectively. On the other hand, according to [24], it is possible to optimize an emulated switch to achieve the bandwidth of 5Gbps between co-hosted VMs compared to about 500Mbps using default solutions. The performance degradation can be reduced when an appropriate hardware ...
... and incoming bandwidth, respectively. On the other hand, according to [24], it is possible to optimize an emulated switch to achieve the bandwidth of 5Gbps between co-hosted VMs compared to about 500Mbps using default solutions. The performance degradation can be reduced when an appropriate hardware ...
IOSR Journal of Computer Engineering (IOSR-JCE) e-ISSN: 2278-0661, p-ISSN: 2278-8727 PP
... allowing for extreme network flexibility. While MANETs can be completely self contained infrastructure less network, they can also be tied to an IP-based global or local network. The mobile devices are free to move randomly and arrange themselves randomly. The Communication takes place in MANET by u ...
... allowing for extreme network flexibility. While MANETs can be completely self contained infrastructure less network, they can also be tied to an IP-based global or local network. The mobile devices are free to move randomly and arrange themselves randomly. The Communication takes place in MANET by u ...