slides - network systems lab @ sfu
... Network interface: connection between host/router and physical link routers typically have multiple interfaces host typically has one interface Unique IP addresses associated with each interface ...
... Network interface: connection between host/router and physical link routers typically have multiple interfaces host typically has one interface Unique IP addresses associated with each interface ...
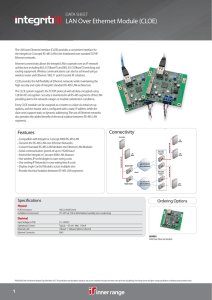
LAN Over Ethernet Module (CLOE)
... the Integriti (or Concept) RS-485 LAN to be distributed over standard TCP/IP Ethernet networks. Ethernet connectivity allows the Integriti LAN to operate over an IP network architecture including 802.3i (10baseT) and 802.3U (100baseT) switching and routing equipment. Wireless communications can also ...
... the Integriti (or Concept) RS-485 LAN to be distributed over standard TCP/IP Ethernet networks. Ethernet connectivity allows the Integriti LAN to operate over an IP network architecture including 802.3i (10baseT) and 802.3U (100baseT) switching and routing equipment. Wireless communications can also ...
GNET-1の概要
... resource management is one of the key issues. Grid middleware should allocate appropriate resources, including network resources, according to user’s request. Network resource manager should provide resource management service to Grid middleware. Network Service A standard open interface between Gri ...
... resource management is one of the key issues. Grid middleware should allocate appropriate resources, including network resources, according to user’s request. Network resource manager should provide resource management service to Grid middleware. Network Service A standard open interface between Gri ...
Problem Statement
... – iPAD: 256M memory, 16G storage – iPhone(X generation): 20M available memory in practice – Current P2P Streaming occupation:~100M memory and ~1G storage ...
... – iPAD: 256M memory, 16G storage – iPhone(X generation): 20M available memory in practice – Current P2P Streaming occupation:~100M memory and ~1G storage ...
DTPC Acceptable Use Guidelines for Dube iConnect
... or by listing an IP address that belongs to Dube iConnect in any unsolicited email whether sent through Dube iConnect's network or not; 6. Failure to secure a customer's mail server against public relay as a protection to themselves and the broader Internet community. Public relay occurs when a mail ...
... or by listing an IP address that belongs to Dube iConnect in any unsolicited email whether sent through Dube iConnect's network or not; 6. Failure to secure a customer's mail server against public relay as a protection to themselves and the broader Internet community. Public relay occurs when a mail ...
Configuration ADSL - AK-NORD
... Do not connect the AK-DinRail-ADSL / the EVA-KIT-ADSL into the network in any way if a DHCP server is already available in the network! When starting up the connected devices it might happen that both DHCP servers assign different IP addresses to the devices and the existing network will not work co ...
... Do not connect the AK-DinRail-ADSL / the EVA-KIT-ADSL into the network in any way if a DHCP server is already available in the network! When starting up the connected devices it might happen that both DHCP servers assign different IP addresses to the devices and the existing network will not work co ...
The Token Based Switch: Per-Packet Access Authorisation to Optical Shortcuts Mihai-Lucian Cristea
... may be associated with arbitrary IP addresses. In essence, tokens are like IPsec authentication headers (AH [3]) except that we aim for authentication that is more efficient in computation and more flexible than IPsec standard (we can authenticate various fields from Ethernet or IP headers by using ...
... may be associated with arbitrary IP addresses. In essence, tokens are like IPsec authentication headers (AH [3]) except that we aim for authentication that is more efficient in computation and more flexible than IPsec standard (we can authenticate various fields from Ethernet or IP headers by using ...
Operating Systems and Networks - Summaries
... Types of lookups ........................................................................................................................................55 ...
... Types of lookups ........................................................................................................................................55 ...
Exhibit 15 - Network Standards
... telecommunication network can be divided into seven distinct groups of related functions, or layers. Each communicating user or program is at a computer that can provide those seven layers of function. So in a given message between users, there will be a flow of data down through the layers in the s ...
... telecommunication network can be divided into seven distinct groups of related functions, or layers. Each communicating user or program is at a computer that can provide those seven layers of function. So in a given message between users, there will be a flow of data down through the layers in the s ...
152-background - University of California, Santa Cruz
... Network links can be point-to-point or multipoint and implemented with several transmission media. Information exchanged can be represented in multiple media (audio, text, video, images, etc.) Services provided to users can vary widely. May 17 ...
... Network links can be point-to-point or multipoint and implemented with several transmission media. Information exchanged can be represented in multiple media (audio, text, video, images, etc.) Services provided to users can vary widely. May 17 ...
Weekly Review Slides - CSE Labs User Home Pages
... – Carry bits/information for many people at same time ...
... – Carry bits/information for many people at same time ...
d - Temple University
... Enables a node to ensure that the identity of the peer node it is communicating with. ...
... Enables a node to ensure that the identity of the peer node it is communicating with. ...
Vodafone Broadband Complete User Guide
... When you access the internet wirelessly, you do not need to connect the red PC/LAN cable so once your computer has connected you will be able to browse the internet from anywhere within the range of your device. Once you have correctly connected the cables to your Broadband Complete modem will conne ...
... When you access the internet wirelessly, you do not need to connect the red PC/LAN cable so once your computer has connected you will be able to browse the internet from anywhere within the range of your device. Once you have correctly connected the cables to your Broadband Complete modem will conne ...
Manual: Emerson Smart Wireless Gateway 1410
... This device must be installed to ensure a minimum antenna separation distance of 20 cm from all persons. ...
... This device must be installed to ensure a minimum antenna separation distance of 20 cm from all persons. ...
ppt
... latency and reduce the number of required signaling messages. • As long as the MN stays inside one MAP domain it only needs to update its location with the MAP. • The localized mobility management can also be completely handled on the network side without MN's involvement at the IP mobility protocol ...
... latency and reduce the number of required signaling messages. • As long as the MN stays inside one MAP domain it only needs to update its location with the MAP. • The localized mobility management can also be completely handled on the network side without MN's involvement at the IP mobility protocol ...
P2P Networks
... A large amount of polluted or corrupted content has been published in file-sharing systems, and it is difficult for a user to distinguish such content from the original digital content they seek. ...
... A large amount of polluted or corrupted content has been published in file-sharing systems, and it is difficult for a user to distinguish such content from the original digital content they seek. ...
Converged Monitoring Fabric For Software Defined Networks Defined Network for Virtual Environments
... systems. This enables complete traffic access and visibility, including traffic that is forwarded from an OpenFlow switch within an SDN. Traffic that enters the vMesh network can be made available to tools and systems on the LAN and across WAN segments, including private clouds. The VSS vMesh techno ...
... systems. This enables complete traffic access and visibility, including traffic that is forwarded from an OpenFlow switch within an SDN. Traffic that enters the vMesh network can be made available to tools and systems on the LAN and across WAN segments, including private clouds. The VSS vMesh techno ...
Update a postal address for your broadband bill
... When you access the internet wirelessly, you do not need to connect the PC/LAN cable so once your computer has connected you will be able to browse the internet from anywhere within the range of your device. Once you have correctly connected the cables to your Broadband Complete modem will connect t ...
... When you access the internet wirelessly, you do not need to connect the PC/LAN cable so once your computer has connected you will be able to browse the internet from anywhere within the range of your device. Once you have correctly connected the cables to your Broadband Complete modem will connect t ...
Middleware issues for ad hoc networks
... DHT allows an uniform distribution of IDs and workload on nodes providing the service The subject-based routing defines a logarithmic lookup cost on the network dimension (O(log N)) A lot of application can adapt their contents to this ...
... DHT allows an uniform distribution of IDs and workload on nodes providing the service The subject-based routing defines a logarithmic lookup cost on the network dimension (O(log N)) A lot of application can adapt their contents to this ...
Analysing the performance of the OpenFlow
... analysed to see how the system is functioning and performing. For example, applications of networking simulation area include network traffic, data transfer rate, packet counts and round trip time for packets transmission. OMNeT++ will be the first step for Australia when attempting to implement a n ...
... analysed to see how the system is functioning and performing. For example, applications of networking simulation area include network traffic, data transfer rate, packet counts and round trip time for packets transmission. OMNeT++ will be the first step for Australia when attempting to implement a n ...
Characteristics of Communication Systems
... activity across that region. WAN – covers a large geographical area such as a city or country. Communication channels include telephone lines, Microwave, satellites, etc. ...
... activity across that region. WAN – covers a large geographical area such as a city or country. Communication channels include telephone lines, Microwave, satellites, etc. ...
Routing protocols
... through lower-capacity WAN connections. When complex routing policies are required. For example, static routes can be used to guarantee that traffic destined for a specific host traverses a designated network path. To provide a more secure network environment. The administrator is aware of all subne ...
... through lower-capacity WAN connections. When complex routing policies are required. For example, static routes can be used to guarantee that traffic destined for a specific host traverses a designated network path. To provide a more secure network environment. The administrator is aware of all subne ...
agencies - Cooperative Ecosystem Studies Units
... Rocky Mountains – University of Montana Colorado Plateau – Northern Arizona University North Atlantic Coast – University of Rhode Island Southern Appalachian Mountains – University of ...
... Rocky Mountains – University of Montana Colorado Plateau – Northern Arizona University North Atlantic Coast – University of Rhode Island Southern Appalachian Mountains – University of ...
router
... Same routing protocol need not be run within the AS But, to the outside world, an AS should present a consistent picture of what ASs are reachable through it Stub AS: has only a single connection to the outside world. Multihomed AS: has multiple connections to the outside world, but refuses to carry ...
... Same routing protocol need not be run within the AS But, to the outside world, an AS should present a consistent picture of what ASs are reachable through it Stub AS: has only a single connection to the outside world. Multihomed AS: has multiple connections to the outside world, but refuses to carry ...
SmartCenter - CheckFirewalls.com
... network, VPN tunnel, and user activity. This solution presents administrators with graphical views of metrics such as bandwidth, roundtrip time, packet loss, and VPN tunnel status. Armed with information provided by SmartView Monitor, administrators can maximize performance of their networks and man ...
... network, VPN tunnel, and user activity. This solution presents administrators with graphical views of metrics such as bandwidth, roundtrip time, packet loss, and VPN tunnel status. Armed with information provided by SmartView Monitor, administrators can maximize performance of their networks and man ...