detection of peer to peer applications
... of controversy and questions challenging the usage of P2P applications. An issue that has been raised is the legality of file sharing. Many files that are being shared between clients do not have authorization of the copyright owner, making it illegal to transfer. Also, the bandwidth consumption of ...
... of controversy and questions challenging the usage of P2P applications. An issue that has been raised is the legality of file sharing. Many files that are being shared between clients do not have authorization of the copyright owner, making it illegal to transfer. Also, the bandwidth consumption of ...
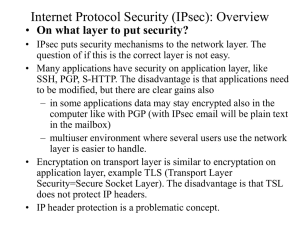
IPSec: Cryptography basics
... (OS) and merged with the IP level. This is called IPsec stack method. All IPsec options can be implemented and the implementation can be very efficient. IP fragmentation can be handled with the same code as IP uses. • If it is not possible to mess up with the native IP implementation IPsec can be im ...
... (OS) and merged with the IP level. This is called IPsec stack method. All IPsec options can be implemented and the implementation can be very efficient. IP fragmentation can be handled with the same code as IP uses. • If it is not possible to mess up with the native IP implementation IPsec can be im ...
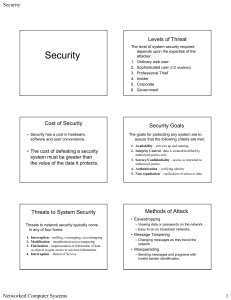
Managing security risks and vulnerabilities
... IBM X-Force reported that halfway through 2013, vulnerability disclosures were on track to surpass the total number disclosed in 2012.2 ...
... IBM X-Force reported that halfway through 2013, vulnerability disclosures were on track to surpass the total number disclosed in 2012.2 ...
Good, Fast, and Cost Effective Priceline Tries to Do All Three
... Loosely Coupled – guaranteed messages are a problem – this is not MQ Series —If timed-out, did you get message, was the data received, should you retry? —Credit card Authorizations - need to build duplication detection at the target site to prevent duplicate authorizations —Reliable web services wil ...
... Loosely Coupled – guaranteed messages are a problem – this is not MQ Series —If timed-out, did you get message, was the data received, should you retry? —Credit card Authorizations - need to build duplication detection at the target site to prevent duplicate authorizations —Reliable web services wil ...
Lecture Notes - Computer Science & Engineering
... Services may rely on the attacked service, causing a cascading and escalating damage Need: support for decision makers to – Evaluate risk and consequences of cyber attacks – Support methods to prevent, deter, and mitigate ...
... Services may rely on the attacked service, causing a cascading and escalating damage Need: support for decision makers to – Evaluate risk and consequences of cyber attacks – Support methods to prevent, deter, and mitigate ...
macro virus - University of Windsor
... *need to have some host program, of which they are a part, executed to activate them *executes secretly, when the host program is run. A typical virus, in a computer, takes control of its Disk Operating System. Whenever it comes in contact with any uninfected piece of software, a fresh copy of the v ...
... *need to have some host program, of which they are a part, executed to activate them *executes secretly, when the host program is run. A typical virus, in a computer, takes control of its Disk Operating System. Whenever it comes in contact with any uninfected piece of software, a fresh copy of the v ...
Reassembling
... 15. Which of the following is a downside of using a reverse proxy? Answer: C. A is incorrect because the log files aren't actually valuable. B is incorrect because a reverse proxy can actually improve network performance because it blocks unnecessary or suspicious requests to the internal Web server ...
... 15. Which of the following is a downside of using a reverse proxy? Answer: C. A is incorrect because the log files aren't actually valuable. B is incorrect because a reverse proxy can actually improve network performance because it blocks unnecessary or suspicious requests to the internal Web server ...
An Introduction to NIST Special Publication 800
... to provide guidance for federal agencies to ensure that certain types of federal information is protected when processed, stored, and used in non-federal information systems. NIST 800-171 applies to Controlled Unclassified Information (also called CUI, described more fully later in this guide) share ...
... to provide guidance for federal agencies to ensure that certain types of federal information is protected when processed, stored, and used in non-federal information systems. NIST 800-171 applies to Controlled Unclassified Information (also called CUI, described more fully later in this guide) share ...
Oracle9i Security
... XML standard that facilitates integration among provisioning environments by defining the protocol for interaction between provisioning service components and agents representing provisioned services. ...
... XML standard that facilitates integration among provisioning environments by defining the protocol for interaction between provisioning service components and agents representing provisioned services. ...
Document
... Legal compliance. For critical applications like, health, public financial records, bank accounts, Government requires the organizations to maintain logs Protecting the trustworthiness of the log sources and also, the logs themselves need to be protected from malicious activities ...
... Legal compliance. For critical applications like, health, public financial records, bank accounts, Government requires the organizations to maintain logs Protecting the trustworthiness of the log sources and also, the logs themselves need to be protected from malicious activities ...
- Learn Group
... recipients into thinking that messages are legitimate traffic, thus inducing them to open e-mail they otherwise might not have. Spoofing can also alter data being transmitted across a network, as in the case of user data protocol (UDP) packet spoofing, which can enable the attacker to get access to ...
... recipients into thinking that messages are legitimate traffic, thus inducing them to open e-mail they otherwise might not have. Spoofing can also alter data being transmitted across a network, as in the case of user data protocol (UDP) packet spoofing, which can enable the attacker to get access to ...
The Inexact Science of Internet Filtering for the K
... proxy solution can address this! • Lack of delegated administration for firewall means no way to know what new protections have been offered by SmartDefense beyond its out-of-the-box capability without ...
... proxy solution can address this! • Lack of delegated administration for firewall means no way to know what new protections have been offered by SmartDefense beyond its out-of-the-box capability without ...
Click for PDF - Cyber Security Services
... using Java for business purposes while minimising their risk. 12. The newly introduced mitigation strategy #6 ‘Automated dynamic analysis’ extracts the behavioural analysis functionality from the existing two mitigation strategies ‘Email content filtering’ and ‘Web content filtering’. A ...
... using Java for business purposes while minimising their risk. 12. The newly introduced mitigation strategy #6 ‘Automated dynamic analysis’ extracts the behavioural analysis functionality from the existing two mitigation strategies ‘Email content filtering’ and ‘Web content filtering’. A ...
Umfang von PCI-Audits reduzieren mit Cisco TrustSec - Analyse und Bewertung von Verizon
... resulting rules are no longer simple to understand and may not clearly correlate with the original business goals. They also do not account for user, device, or server roles, leading to some complexity in how protected assets are classified, and are at risk of misconfiguration. Cisco TrustSec simpli ...
... resulting rules are no longer simple to understand and may not clearly correlate with the original business goals. They also do not account for user, device, or server roles, leading to some complexity in how protected assets are classified, and are at risk of misconfiguration. Cisco TrustSec simpli ...
I What is Solaris
... enhancements to improve performance and reduce server load. In conjunction with NIS+(Network Information Service) , Auto FS, CacheFS and several other services, NFS provides the user with automatic data location, navigation, and data access over wide area networks. Auto FS makes remote file systems ...
... enhancements to improve performance and reduce server load. In conjunction with NIS+(Network Information Service) , Auto FS, CacheFS and several other services, NFS provides the user with automatic data location, navigation, and data access over wide area networks. Auto FS makes remote file systems ...
Control Panel Security
... cylinder lock kits that fit in pre-drilled or punched holes and are available with two key configurations. See Appendix, #1. Securing an enclosure may be as simple as replacing a standard key hole with inserts that have alternative key shapes, such as square bits, triangular holes, and Daimler or Fi ...
... cylinder lock kits that fit in pre-drilled or punched holes and are available with two key configurations. See Appendix, #1. Securing an enclosure may be as simple as replacing a standard key hole with inserts that have alternative key shapes, such as square bits, triangular holes, and Daimler or Fi ...
user manual - SetupRouter
... Wi-Fi Protected Access (WPA) and Wired Equivalent Privacy (WEP) are wireless encryption protocols used to encrypt the data traffic within the wireless network. AirTies RT-205 supports both encryption standards. WPA is the latest and most advanced wireless encryption standard and provides you with t ...
... Wi-Fi Protected Access (WPA) and Wired Equivalent Privacy (WEP) are wireless encryption protocols used to encrypt the data traffic within the wireless network. AirTies RT-205 supports both encryption standards. WPA is the latest and most advanced wireless encryption standard and provides you with t ...
TCA Report Template - Transport Certification Australia
... TCA acknowledges that each transport operator is different. Therefore, this document should be treated as a general overview of the information required.Transport operators may also be requested by TCA to provide additional information relating to their specific environment. Broadly, the Desk-top As ...
... TCA acknowledges that each transport operator is different. Therefore, this document should be treated as a general overview of the information required.Transport operators may also be requested by TCA to provide additional information relating to their specific environment. Broadly, the Desk-top As ...
Slides on Security
... from the outside world into a private network. • Firewalls can be implemented in a router. • A firewall can restrict certain types of traffic activity on a network based on: – Source or destination IP address – Port number – Protocol – data contents (virus scanning) ...
... from the outside world into a private network. • Firewalls can be implemented in a router. • A firewall can restrict certain types of traffic activity on a network based on: – Source or destination IP address – Port number – Protocol – data contents (virus scanning) ...
Nuview Union School District
... of collaborative efforts between the district’s IT department and curriculum and instruction staff to ensure that the required technology will be in place for the testing. Network bandwidth, wireless access, proper number of online testing devices, and maintenance of these devices must all be evalua ...
... of collaborative efforts between the district’s IT department and curriculum and instruction staff to ensure that the required technology will be in place for the testing. Network bandwidth, wireless access, proper number of online testing devices, and maintenance of these devices must all be evalua ...
Data Exfiltration and DNS
... DNS is increasingly being used as a pathway for data exfiltration either by malware-infected devices or by malicious insiders. According to a recent DNS security survey, 46 percent of respondents experienced DNS exfiltration and 45 percent experienced DNS tunneling. DNS tunneling involves tunneling ...
... DNS is increasingly being used as a pathway for data exfiltration either by malware-infected devices or by malicious insiders. According to a recent DNS security survey, 46 percent of respondents experienced DNS exfiltration and 45 percent experienced DNS tunneling. DNS tunneling involves tunneling ...
Chapter 4
... Threat – any circumstance or event that has potential to cause harm to a system or network. Threat can be ...
... Threat – any circumstance or event that has potential to cause harm to a system or network. Threat can be ...
Network security - The Open University
... you will compare this with what happens when you use a computer, and relate it to the issues discussed in this unit. After pressing the start button on my PC, certain elements of the operating system load before I am asked to enter a password. This was set by the IT administrators before I took deli ...
... you will compare this with what happens when you use a computer, and relate it to the issues discussed in this unit. After pressing the start button on my PC, certain elements of the operating system load before I am asked to enter a password. This was set by the IT administrators before I took deli ...