Introduction to Computer Networking
... Each of the past three centuries has been dominated by a single technology. People were doing lot of paper work in organizations because, lack of advance systems which will help them in their day today work. The 18th century was the time of the great mechanical systems accompanying the Industrial re ...
... Each of the past three centuries has been dominated by a single technology. People were doing lot of paper work in organizations because, lack of advance systems which will help them in their day today work. The 18th century was the time of the great mechanical systems accompanying the Industrial re ...
2 Enhanced TDD
... multiple antennas, digital processing techniques, and complex algorithms to modify the transmitted and received signals at a base station and at a user terminal. In addition, MIMO techniques can provide significant improvements in the radio-link capacity by making positive use of the complex multipa ...
... multiple antennas, digital processing techniques, and complex algorithms to modify the transmitted and received signals at a base station and at a user terminal. In addition, MIMO techniques can provide significant improvements in the radio-link capacity by making positive use of the complex multipa ...
How to test an IPS
... Testing for anti-scanning There are two main steps in scanning a target network. 1. Identification, intended to discover hosts and services that may be reachable by the attacker. This operation will provide results such has IP addresses and open ports on the target infrastructure. 2. Qualification, ...
... Testing for anti-scanning There are two main steps in scanning a target network. 1. Identification, intended to discover hosts and services that may be reachable by the attacker. This operation will provide results such has IP addresses and open ports on the target infrastructure. 2. Qualification, ...
Secure Network Design Office of Nuclear Regulatory Research NUREG/CR-7117
... NRC to provide information on technical criteria that can aid reviewers and other stakeholders in the evaluation (or development) of secure digital networks. SNL first produced a Letter Report detailing the results of their investigations concerning secure network design (Reference 1 — for this and ...
... NRC to provide information on technical criteria that can aid reviewers and other stakeholders in the evaluation (or development) of secure digital networks. SNL first produced a Letter Report detailing the results of their investigations concerning secure network design (Reference 1 — for this and ...
May 2015 - TMA Associates
... correspond to similar cases, and may be classes or subclasses of what we label. The advantage is that unsupervised learning, by definition, doesn’t require data where the outcome we are seeking is known, so much more data may be available to find clusters than to find outcomes directly. In fact, a n ...
... correspond to similar cases, and may be classes or subclasses of what we label. The advantage is that unsupervised learning, by definition, doesn’t require data where the outcome we are seeking is known, so much more data may be available to find clusters than to find outcomes directly. In fact, a n ...
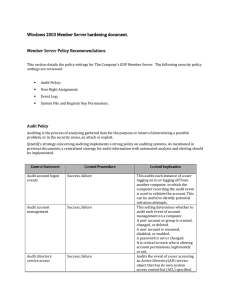
Server hardening - Cisco Security Solutions
... administrators and service groups could mitigate the risk. However Microsoft set this by default on a default setup therfore this option does not need to be explicitly set (i.e not defined). Users with this privilege could expose sensitive data to the network by creating a new shared object. Do not ...
... administrators and service groups could mitigate the risk. However Microsoft set this by default on a default setup therfore this option does not need to be explicitly set (i.e not defined). Users with this privilege could expose sensitive data to the network by creating a new shared object. Do not ...
Remote Access—Attack Vectors
... A VPN provides protection, but it also presents an attractive target to attackers for two reasons: First, the VPN transmits sensitive information over public and shared networks. The extension of the network outside the perimeter makes assets much more accessible for attackers. The hackers no longer ...
... A VPN provides protection, but it also presents an attractive target to attackers for two reasons: First, the VPN transmits sensitive information over public and shared networks. The extension of the network outside the perimeter makes assets much more accessible for attackers. The hackers no longer ...
PPT_ch01 - Mercer University Computer Science Department
... type of computer, operating system, software, and network connection a computer uses – An attacker who knows that information can more easily determine the weaknesses of the system to attack it ...
... type of computer, operating system, software, and network connection a computer uses – An attacker who knows that information can more easily determine the weaknesses of the system to attack it ...
Security+ Guide to Network Security Fundamentals, Third Edition
... type of computer, operating system, software, and network connection a computer uses – An attacker who knows that information can more easily determine the weaknesses of the system to attack it ...
... type of computer, operating system, software, and network connection a computer uses – An attacker who knows that information can more easily determine the weaknesses of the system to attack it ...
Security
... of protection methods and mechanisms to maintain the safe operation of a computer system must also take into account the external environment of the system cannot rely on orderly behavior of users and ...
... of protection methods and mechanisms to maintain the safe operation of a computer system must also take into account the external environment of the system cannot rely on orderly behavior of users and ...
Learn About Software-Defined Secure Networks
... How has this happened? Here are some recent developments that have weakened the perimeter approach to network security: Failing to deploy at all endpoints – Any smartphone or tablet that connects to a corporate network is an endpoint, and must be secured. If employees in an organization use VPN to c ...
... How has this happened? Here are some recent developments that have weakened the perimeter approach to network security: Failing to deploy at all endpoints – Any smartphone or tablet that connects to a corporate network is an endpoint, and must be secured. If employees in an organization use VPN to c ...
Slide 1
... Source of Information for AirDefense Detection Fault Database Used to Diagnose or Confirm Events ...
... Source of Information for AirDefense Detection Fault Database Used to Diagnose or Confirm Events ...
Success story: China Telecom e-surfing cloud storage
... first half year of offering this service, with monthly growth of 22,165 users and the total storage space reaching 21,150.38 GB. China Telecom, relying on the favorable resources provided by Huawei UDS, provides diversified cloud storage services to its broadband, phone, and Internet customers. Cust ...
... first half year of offering this service, with monthly growth of 22,165 users and the total storage space reaching 21,150.38 GB. China Telecom, relying on the favorable resources provided by Huawei UDS, provides diversified cloud storage services to its broadband, phone, and Internet customers. Cust ...
international journal of economics and law
... inter-state conflicts with tragic consequences, millions of refugees and migrants who go from one continent to another in spite of a large number of resolutions at the level of the international community on human rights. If we would test the top management of large companies about their knowledge o ...
... inter-state conflicts with tragic consequences, millions of refugees and migrants who go from one continent to another in spite of a large number of resolutions at the level of the international community on human rights. If we would test the top management of large companies about their knowledge o ...
NEW YORK TECH-SECURITY CONFERENCE
... Distributed Denial of Service (DDoS) attacks attempt to make an online service unavailable by overwhelming it with traffic from multiple sources. They target a wide variety of important resources, from consumer-facing financial and news websites, to internally-oriented employee intranet links, and p ...
... Distributed Denial of Service (DDoS) attacks attempt to make an online service unavailable by overwhelming it with traffic from multiple sources. They target a wide variety of important resources, from consumer-facing financial and news websites, to internally-oriented employee intranet links, and p ...
Internet Techniques
... Professor for Communications Systems at the FernUniversität Hagen Main interests: Communications Systems, Networks and Protocols; Network Security ...
... Professor for Communications Systems at the FernUniversität Hagen Main interests: Communications Systems, Networks and Protocols; Network Security ...
Network Management
... UDP (rather than TCP) as the transport layer protocol. SNMPv2 allows the use of TCP for ”reliable, connection-oriented” service. Any device that does not run SNMPv2 must be managed by proxy. ...
... UDP (rather than TCP) as the transport layer protocol. SNMPv2 allows the use of TCP for ”reliable, connection-oriented” service. Any device that does not run SNMPv2 must be managed by proxy. ...
Proactive Compliance for Insider Threat Protection
... of the United States Government.” The conversation has moved to encompass not only cybersecurity and Information Assurance (IA), but also insider threat, which today is one of the most prevalent threats to our nation’s security. In this paper, we explore the mandated compliance guidelines, from Exec ...
... of the United States Government.” The conversation has moved to encompass not only cybersecurity and Information Assurance (IA), but also insider threat, which today is one of the most prevalent threats to our nation’s security. In this paper, we explore the mandated compliance guidelines, from Exec ...
Certified Penetration Testing Specialist
... information on the latest vulnerabilities and defenses. This class also enhances the business skills needed to identify protection opportunities, justify testing activities and optimize security controls appropriate to the business needs in order to reduce business risk. We go far beyond simply teac ...
... information on the latest vulnerabilities and defenses. This class also enhances the business skills needed to identify protection opportunities, justify testing activities and optimize security controls appropriate to the business needs in order to reduce business risk. We go far beyond simply teac ...
IDS and IPS
... An IPS looks at the contents of the packets and/or can correlate over time to determine if an attack is happening. An IPS works in tandem with a firewall to make sure that the traffic the firewall permitted is actual legitimate traffic. ...
... An IPS looks at the contents of the packets and/or can correlate over time to determine if an attack is happening. An IPS works in tandem with a firewall to make sure that the traffic the firewall permitted is actual legitimate traffic. ...