Red Teaming: The Art of Ethical Hacking
... The term “hacker” was initially used for skilled computer enthusiasts that could “hack” their way through technical problems. Today, hackers pose one of the principal threats against our information infrastructure by exploiting vulnerabilities in code and circumventing security measures. Hacking use ...
... The term “hacker” was initially used for skilled computer enthusiasts that could “hack” their way through technical problems. Today, hackers pose one of the principal threats against our information infrastructure by exploiting vulnerabilities in code and circumventing security measures. Hacking use ...
Chapter 10
... • Commercial policy information classification: “public” or “company confidential” • Comprehensive security plan goals – Protect system’s privacy, integrity, availability; authenticate users – Selected to satisfy Figure 10-2 requirements ...
... • Commercial policy information classification: “public” or “company confidential” • Comprehensive security plan goals – Protect system’s privacy, integrity, availability; authenticate users – Selected to satisfy Figure 10-2 requirements ...
Network Infrastructure Security Good Practice Guide
... The good practice set does not contain mandatory requirements that centers are required to implement. Instead, it outlines a number of good practices with respect to enterprise ICT security and acceptable use. The prudence of implementing specific good practices identified in this guide will depend ...
... The good practice set does not contain mandatory requirements that centers are required to implement. Instead, it outlines a number of good practices with respect to enterprise ICT security and acceptable use. The prudence of implementing specific good practices identified in this guide will depend ...
Power Point - ECE Users Pages - Georgia Institute of Technology
... Size the same throughout a session. Windows Operating Systems tend to change the window size during a session. Time to Live: FreeBsd or Linux typically use 64, Windows ...
... Size the same throughout a session. Windows Operating Systems tend to change the window size during a session. Time to Live: FreeBsd or Linux typically use 64, Windows ...
EC2004_ch12
... before they were settled, saving Spitfire $316,000 in charges Authorize.Net merchants were charged $0.35 for each transaction The criminals acquired thousands of valid credit card numbers to sell on the black market © Prentice Hall 2004 ...
... before they were settled, saving Spitfire $316,000 in charges Authorize.Net merchants were charged $0.35 for each transaction The criminals acquired thousands of valid credit card numbers to sell on the black market © Prentice Hall 2004 ...
Managing security risks and vulnerabilities
... in the loss of intellectual property, disrupt critical operations and damage an organization’s image, brand and public reputation. Meanwhile, security teams often take approaches that are largely reactive instead of proactive; it is not uncommon for them to spend the majority of their time—and budge ...
... in the loss of intellectual property, disrupt critical operations and damage an organization’s image, brand and public reputation. Meanwhile, security teams often take approaches that are largely reactive instead of proactive; it is not uncommon for them to spend the majority of their time—and budge ...
CompTIA Security (SY0-401)
... skills required to identify risk, to participate in risk mitigation activities, and to provide infrastructure, application, information, and operational security. In addition, the successful candidate will apply security controls to maintain confidentiality, integrity, and availability, identify app ...
... skills required to identify risk, to participate in risk mitigation activities, and to provide infrastructure, application, information, and operational security. In addition, the successful candidate will apply security controls to maintain confidentiality, integrity, and availability, identify app ...
The Guidelines on Cyber Security onboard Ships - ics
... used to locate known vulnerabilities in a company and onboard a ship. Examples of some tools and techniques that may be used in these circumstances include: ...
... used to locate known vulnerabilities in a company and onboard a ship. Examples of some tools and techniques that may be used in these circumstances include: ...
Guidelines on Cyber Security onboard ships
... used to locate known vulnerabilities in a company and onboard a ship. Examples of some tools and techniques that may be used in these circumstances include: ...
... used to locate known vulnerabilities in a company and onboard a ship. Examples of some tools and techniques that may be used in these circumstances include: ...
Anonymous Proxy Detection and Control
... To scan transmitted content for malware or Trojans before delivery ...
... To scan transmitted content for malware or Trojans before delivery ...
Certification Exam Objectives: SY0-401
... skills required to identify risk, to participate in risk mitigation activities, and to provide infrastructure, application, information, and operational security. In addition, the successful candidate will apply security controls to maintain confidentiality, integrity, and availability, identify app ...
... skills required to identify risk, to participate in risk mitigation activities, and to provide infrastructure, application, information, and operational security. In addition, the successful candidate will apply security controls to maintain confidentiality, integrity, and availability, identify app ...
Estimating Impact and Frequency of Risks to
... vulnerabilities in the system. However, the latter is not always possible in practise. The risk levels of a vulnerability defines its severity. This does not always mean that two vulnerabilities having the same risk level pose the same severity in terms of reducing the service level (safety and miss ...
... vulnerabilities in the system. However, the latter is not always possible in practise. The risk levels of a vulnerability defines its severity. This does not always mean that two vulnerabilities having the same risk level pose the same severity in terms of reducing the service level (safety and miss ...
IPSec: Cryptography basics
... (OS) and merged with the IP level. This is called IPsec stack method. All IPsec options can be implemented and the implementation can be very efficient. IP fragmentation can be handled with the same code as IP uses. • If it is not possible to mess up with the native IP implementation IPsec can be im ...
... (OS) and merged with the IP level. This is called IPsec stack method. All IPsec options can be implemented and the implementation can be very efficient. IP fragmentation can be handled with the same code as IP uses. • If it is not possible to mess up with the native IP implementation IPsec can be im ...
Document
... electronically transmitted message that is used to verify the origin and contents of a message • Digital certificates: Data files used to establish the identity of users and electronic assets for protection of online transactions • Public Key Infrastructure (PKI): Use of public key cryptography work ...
... electronically transmitted message that is used to verify the origin and contents of a message • Digital certificates: Data files used to establish the identity of users and electronic assets for protection of online transactions • Public Key Infrastructure (PKI): Use of public key cryptography work ...
Management Information Systems Chapter 10 Security and Control
... electronically transmitted message that is used to verify the origin and contents of a message • Digital certificates: Data files used to establish the identity of users and electronic assets for protection of online transactions • Public Key Infrastructure (PKI): Use of public key cryptography work ...
... electronically transmitted message that is used to verify the origin and contents of a message • Digital certificates: Data files used to establish the identity of users and electronic assets for protection of online transactions • Public Key Infrastructure (PKI): Use of public key cryptography work ...
The Importance of Cybersecurity
... N-Sentinel is a comprehensive, cybersecurity monitoring program specifically designed to meet the needs of utilities. It includes a sensor placed nonintrusive to network traffic, within the utility’s network. It delivers 24 x 7 monitoring of an internal and/or perimeter network for intrusion attempt ...
... N-Sentinel is a comprehensive, cybersecurity monitoring program specifically designed to meet the needs of utilities. It includes a sensor placed nonintrusive to network traffic, within the utility’s network. It delivers 24 x 7 monitoring of an internal and/or perimeter network for intrusion attempt ...
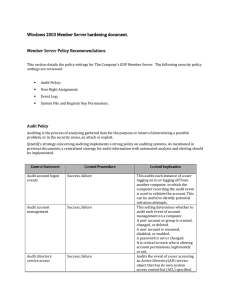
Server hardening - Cisco Security Solutions
... the ability to create or modify tokens can change the level of access for any currently logged on account. They could escalate their own privileges or create a DoS condition. Do not assign the create a token object right to any users. Processes that require this privilege should use the local system ...
... the ability to create or modify tokens can change the level of access for any currently logged on account. They could escalate their own privileges or create a DoS condition. Do not assign the create a token object right to any users. Processes that require this privilege should use the local system ...
Organizations That Use TLS/SSL
... For organizations that store or process payment information, such as donor credit card numbers, implementing TLS/SSL may be a requirement of the Payment Card Industry Data Security Standard (PCI DSS). This standard was created by the PCI Security Standards Council, a group of several major payment c ...
... For organizations that store or process payment information, such as donor credit card numbers, implementing TLS/SSL may be a requirement of the Payment Card Industry Data Security Standard (PCI DSS). This standard was created by the PCI Security Standards Council, a group of several major payment c ...
CH9
... The probability that a vulnerability will be known and used social engineering A type of nontechnical attack that uses some ruse to trick users into revealing information or performing an action that compromises a computer or network spam The electronic equivalent of junk mail Copyright © 2012 P ...
... The probability that a vulnerability will be known and used social engineering A type of nontechnical attack that uses some ruse to trick users into revealing information or performing an action that compromises a computer or network spam The electronic equivalent of junk mail Copyright © 2012 P ...
detection of peer to peer applications
... patterns and packets. Network scanning looks for common ports or protocols that may be open. These methods are useful for detecting P2P applications such as Piolet. Piolet is an executable which can be dropped and run from anywhere. It requires no installation and leaves no footprint behind. An admi ...
... patterns and packets. Network scanning looks for common ports or protocols that may be open. These methods are useful for detecting P2P applications such as Piolet. Piolet is an executable which can be dropped and run from anywhere. It requires no installation and leaves no footprint behind. An admi ...
Physical Security
... the Internet, from web servers to browsers. • When a secure connection is needed, SSL/TLS is used and appears in the address as https://. • If the protocol is https:, your connection is secure. • If the protocol is http:, then the connection is carried by plaintext for anyone to see. ...
... the Internet, from web servers to browsers. • When a secure connection is needed, SSL/TLS is used and appears in the address as https://. • If the protocol is https:, your connection is secure. • If the protocol is http:, then the connection is carried by plaintext for anyone to see. ...
Introduction CS 239 Security for Networks and System
... companies, business partners, government sites, universities, etc. • 39% from outside US – Only based on IP address, though CS 236 Online ...
... companies, business partners, government sites, universities, etc. • 39% from outside US – Only based on IP address, though CS 236 Online ...
Lecture 13, Part 1
... companies, business partners, government sites, universities, etc. • 39% from outside US – Only based on IP address, though CS 236 Online ...
... companies, business partners, government sites, universities, etc. • 39% from outside US – Only based on IP address, though CS 236 Online ...
COMPUTER CRIME Computer crime
... Education for Problem Prevention What to do and not to do with computer resources such as The ...
... Education for Problem Prevention What to do and not to do with computer resources such as The ...