1 Introduction To Information Technology
... our attention. That could be voice, image, text and video • What is data? Data is information when dealing with the machine ...
... our attention. That could be voice, image, text and video • What is data? Data is information when dealing with the machine ...
PowerPoint 簡報
... know of holes within systems and the reasons for such holes. Hackers constantly seek further knowledge, freely share what they have discovered, and never, ever intentionally damage data. ...
... know of holes within systems and the reasons for such holes. Hackers constantly seek further knowledge, freely share what they have discovered, and never, ever intentionally damage data. ...
Computer Ethics
... software, is software designed to infiltrate a computer system without the owner's informed consent. ...
... software, is software designed to infiltrate a computer system without the owner's informed consent. ...
Do you know someone may be watching you?
... sources that are hacking into your system by using various techniques in computer science and mathematics. ...
... sources that are hacking into your system by using various techniques in computer science and mathematics. ...
Network Security Analysis Prepared By: cowave Communication
... the users from making illegal changing / deleting of data. Data availability means that computer assets are accessible to authorized parties ...
... the users from making illegal changing / deleting of data. Data availability means that computer assets are accessible to authorized parties ...
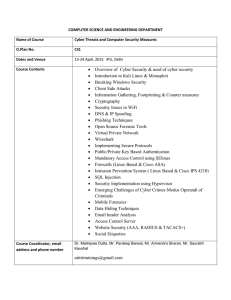
• Overview of Cyber Security & need of cyber security • Introduction
... 13-24 April, 2015 IPU, Delhi ...
... 13-24 April, 2015 IPU, Delhi ...
Networking and System Administration (NaSA) Bachelor of Science in
... expected to increase much faster than average as firms will continue to invest heavily in securing computer networks. Companies are looking for workers knowledgeable about the function and administration of networks. Such employees have become increasingly hard to find as systems administration has ...
... expected to increase much faster than average as firms will continue to invest heavily in securing computer networks. Companies are looking for workers knowledgeable about the function and administration of networks. Such employees have become increasingly hard to find as systems administration has ...
- Longwood Blogs
... Design, build , and test user interfaces using various JavaScript libraries Develop responsive and intuitive components to sort and analyze data Analyze and patch code vulnerabilities in web applications Follow agile practices to collaborate requirements and coordinate development Longwood U ...
... Design, build , and test user interfaces using various JavaScript libraries Develop responsive and intuitive components to sort and analyze data Analyze and patch code vulnerabilities in web applications Follow agile practices to collaborate requirements and coordinate development Longwood U ...
Online dating Virtual gaming Twitter LinkedIn Facebook Google +
... • “The sharing of information, using technology as an enabler, is a culture change that has been fully embraced by political, military, and the business communities.” • “If we do not develop robust capabilities to detect, expose, and hold accountable individuals and organizations who use technology ...
... • “The sharing of information, using technology as an enabler, is a culture change that has been fully embraced by political, military, and the business communities.” • “If we do not develop robust capabilities to detect, expose, and hold accountable individuals and organizations who use technology ...
chapter 5 – basic security
... example, if an attacker knows the target's social security number, they may use that information to gain the trust of their target. The target is then more likely to release further information. ...
... example, if an attacker knows the target's social security number, they may use that information to gain the trust of their target. The target is then more likely to release further information. ...
Cisco Discovery 1 Module 08 Quiz Picture Descriptions
... file, the user’s hard drive crashes and all information on the computer is lost. What type of attack occurred? Worm, virus Trojan horse denial of service 4. In rapid succession, an intruder tries a large number of possibilities to guess passwords. As a result, other users on the network are lo ...
... file, the user’s hard drive crashes and all information on the computer is lost. What type of attack occurred? Worm, virus Trojan horse denial of service 4. In rapid succession, an intruder tries a large number of possibilities to guess passwords. As a result, other users on the network are lo ...
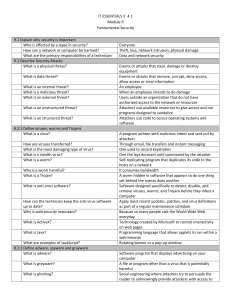
IT ESSENTIALS V. 4.1 Module 9 Fundamental Security 9.1 Explain
... Which wireless security protocol was created by Cisco? What do virus, spyware, and adware detection programs look for? What are the code patterns called? ...
... Which wireless security protocol was created by Cisco? What do virus, spyware, and adware detection programs look for? What are the code patterns called? ...
Mullvad Barnprogram
... Mullvad Barnprogram - A virtual private network (VPN) extends a private network across a public network, such as the Internet. It enables a computer or network-enabled device to send and receive data across shared or public networks as if it were directly connected to the private network, while bene ...
... Mullvad Barnprogram - A virtual private network (VPN) extends a private network across a public network, such as the Internet. It enables a computer or network-enabled device to send and receive data across shared or public networks as if it were directly connected to the private network, while bene ...
Are you looking for an easier way to initiate and
... • Remediation Support and Preventative Analysis ...
... • Remediation Support and Preventative Analysis ...
IIDPS: An Internal Intrusion Detection and
... Over the past several years, the Internet environment has become more complex and untrusted. Enterprise networked systems are inevitably exposed to the increasing threats posed by hackers as well as malicious users internal to a network. IDS technology is one of the important tools used now-a-days, ...
... Over the past several years, the Internet environment has become more complex and untrusted. Enterprise networked systems are inevitably exposed to the increasing threats posed by hackers as well as malicious users internal to a network. IDS technology is one of the important tools used now-a-days, ...
Position: Senior IA/Security Specialist, (Computer Network Defense
... lifecycle management of Computer Network Defense tools needed to sustain a robust cyber security management program and associated network defenses for NAVAIR networks. Responsibilities: • Conduct system administration, analysis, design, implementation, and operation for NAVAIR RDT&E and NMCI/NGEN n ...
... lifecycle management of Computer Network Defense tools needed to sustain a robust cyber security management program and associated network defenses for NAVAIR networks. Responsibilities: • Conduct system administration, analysis, design, implementation, and operation for NAVAIR RDT&E and NMCI/NGEN n ...
Pan-Oston Company, a Houchens Industries Employee Owned
... store fixtures to the retail industry is pleased to announce an immediate opening to join our team in Bowling Green, Kentucky. Computer Operations Specialist Responsibilities Include: ...
... store fixtures to the retail industry is pleased to announce an immediate opening to join our team in Bowling Green, Kentucky. Computer Operations Specialist Responsibilities Include: ...
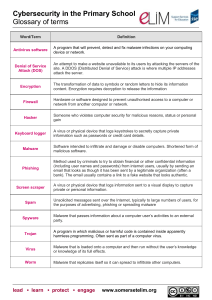
CH 8 – Review - WordPress.com
... Biometrics – devices that scan human features such as the retina to identify an individual Rootkit – a set of programs or utilities designed to allow a hacker to control a victim computer’s hardware and software and permit a hacker to monitor the user’s actions WPA – encryption standard used to prot ...
... Biometrics – devices that scan human features such as the retina to identify an individual Rootkit – a set of programs or utilities designed to allow a hacker to control a victim computer’s hardware and software and permit a hacker to monitor the user’s actions WPA – encryption standard used to prot ...
Open ended challenge rationale
... Hardware or software designed to prevent unauthorised access to a computer or network from another computer or network. ...
... Hardware or software designed to prevent unauthorised access to a computer or network from another computer or network. ...