Sohel Ahmed Syed Flat #402, Shivshankar 2, Contact Number: +91
... Mentoring and assisting the team for optimum performance towards individual’s contribution. Arranging trainings for the team on new technologies. Documenting the issues and their resolution, new techniques to achieve the complex workflows based on own investigation. Configuring different types of Au ...
... Mentoring and assisting the team for optimum performance towards individual’s contribution. Arranging trainings for the team on new technologies. Documenting the issues and their resolution, new techniques to achieve the complex workflows based on own investigation. Configuring different types of Au ...
Document
... * Now trying to create "Web SQL" DSN... *
Initializing GuestBook by GETting ctguestb.idc
Type the command line you want to run (cmd /c assumed):
...
... * Now trying to create "Web SQL" DSN...
SERVICE DESCRIPTION WEB APPLICATION SECURITY SCANNING
... network components related to the system to potential malicious attacks which may compromise the system integrity, confidentiality, and availability; (2) to identify flaws and loopholes on the application against security breach, if done from outside it is external oriented, if done from inside, it ...
... network components related to the system to potential malicious attacks which may compromise the system integrity, confidentiality, and availability; (2) to identify flaws and loopholes on the application against security breach, if done from outside it is external oriented, if done from inside, it ...
ppt
... • Much of the useful information in first few bytes • Can “packetize” transfer over TCP • HTTP 1.1 recommends using range requests ...
... • Much of the useful information in first few bytes • Can “packetize” transfer over TCP • HTTP 1.1 recommends using range requests ...
Android Reverse Engineering
... Malware is a piece of code which changes the behavior of either the operating system kernel or some security sensitive applications, without a user consent and in such a way that it is then impossible to detect those changes using a documented features of the operating system or the application.[2] ...
... Malware is a piece of code which changes the behavior of either the operating system kernel or some security sensitive applications, without a user consent and in such a way that it is then impossible to detect those changes using a documented features of the operating system or the application.[2] ...
AdvancedSQLInjection
... specified through its name or through its index (an integer) When an existing field is chosen, the result is sorted according to it. However, when a non existing field is chosen, an error occurs Using some trial an error, the exact number of fields can be enumerated (Under the assumption that no mor ...
... specified through its name or through its index (an integer) When an existing field is chosen, the result is sorted according to it. However, when a non existing field is chosen, an error occurs Using some trial an error, the exact number of fields can be enumerated (Under the assumption that no mor ...
Anonymous Proxy Detection and Control
... common approaches is the open proxy. An open proxy is a proxy server that can be accessed by any Internet user. Anonymous open proxies allow any user of the Internet to conceal his or her IP address, identity and location from the service being accessed. The server receives requests from the “anonym ...
... common approaches is the open proxy. An open proxy is a proxy server that can be accessed by any Internet user. Anonymous open proxies allow any user of the Internet to conceal his or her IP address, identity and location from the service being accessed. The server receives requests from the “anonym ...
The Pros and Cons of Open Source Security
... any identifying information into a non-secure web page, the exit relay can detect and store login credentials or critical mission communications. To make matters worse, Tor uses the same circuit for all of each user’s connections. Therefore, once an exit node observes identifying information, it can ...
... any identifying information into a non-secure web page, the exit relay can detect and store login credentials or critical mission communications. To make matters worse, Tor uses the same circuit for all of each user’s connections. Therefore, once an exit node observes identifying information, it can ...
Chapter 2: Application layer
... User-server state: cookies Example: Susan always access Internet always from PC visits specific e1) cookie header line of HTTP response message commerce site for first 2) cookie header line in time HTTP request message when initial HTTP 3) cookie file kept on user’s host, managed by requests ...
... User-server state: cookies Example: Susan always access Internet always from PC visits specific e1) cookie header line of HTTP response message commerce site for first 2) cookie header line in time HTTP request message when initial HTTP 3) cookie file kept on user’s host, managed by requests ...
Toward Real-Time Indexing on Internet 2
... Why are they only available in limited domains? Why isn’t there near real-time WWW searching using push methods now? No Push searching protocol was implemented along with HTTP and now it’s too late to convert all web servers in the world. No universal architecture exists. No centralized data ...
... Why are they only available in limited domains? Why isn’t there near real-time WWW searching using push methods now? No Push searching protocol was implemented along with HTTP and now it’s too late to convert all web servers in the world. No universal architecture exists. No centralized data ...
Intrusion Detection System (IDS)
... The intrusion process ends when some or all objectives of the intruder are realized or the intruder gives up Because multiple perspectives are involved in a single attack, defining what constitutes an attack is difficult ...
... The intrusion process ends when some or all objectives of the intruder are realized or the intruder gives up Because multiple perspectives are involved in a single attack, defining what constitutes an attack is difficult ...
Wireless Application Protocol (wap)
... – designed for computers with “high” performance, color highresolution display, mouse, hard disk – typically, web pages optimized for design, not for communication; ignore end-system characteristics ...
... – designed for computers with “high” performance, color highresolution display, mouse, hard disk – typically, web pages optimized for design, not for communication; ignore end-system characteristics ...
Document
... The intrusion process ends when some or all objectives of the intruder are realized or the intruder gives up Because multiple perspectives are involved in a single attack, defining what constitutes an attack is difficult ...
... The intrusion process ends when some or all objectives of the intruder are realized or the intruder gives up Because multiple perspectives are involved in a single attack, defining what constitutes an attack is difficult ...
Semantic Web Toolkits for Java
... Large parts of the current Web rely on scripting languages such as Python, PHP, Perl, JavaScript, ASP, JSP, Ruby, Flash-ActionScript and ColdFusion. These languages are the tools of a generation of web programmers who use them to quickly create serverside and client-side web applications. It is t ...
... Large parts of the current Web rely on scripting languages such as Python, PHP, Perl, JavaScript, ASP, JSP, Ruby, Flash-ActionScript and ColdFusion. These languages are the tools of a generation of web programmers who use them to quickly create serverside and client-side web applications. It is t ...
Web Front-end Architecture Overview HOPEX V1R2 EN
... The HOPEX platform can plan execution of jobs using a specific scheduler. A scheduler instance runs for each environment SSP. When the scheduled date occurs for a job, the associated macro (customizable) is called. Macros can be coded in VB script or Java and use MEGA API script functions. Reference ...
... The HOPEX platform can plan execution of jobs using a specific scheduler. A scheduler instance runs for each environment SSP. When the scheduled date occurs for a job, the associated macro (customizable) is called. Macros can be coded in VB script or Java and use MEGA API script functions. Reference ...
A Hands-On Environment for Teaching Networks
... All incoming (non-SYN) packets are checked for valid capabilities Flows that get ACKs from the server continue to get capabilities ...
... All incoming (non-SYN) packets are checked for valid capabilities Flows that get ACKs from the server continue to get capabilities ...
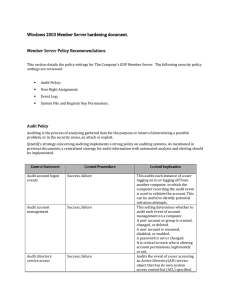
Server hardening - Cisco Security Solutions
... computer to the network can access resources on that computer for which they have permission. Users requiring access to member servers resources should be authenticated. This allows a process to assume the identity of any user and thus gain access to the resources that the user is authorised to acce ...
... computer to the network can access resources on that computer for which they have permission. Users requiring access to member servers resources should be authenticated. This allows a process to assume the identity of any user and thus gain access to the resources that the user is authorised to acce ...
Misbehaving TCP Receivers Can Cause Internet-Wide Congestion Collapse Rob Sherwood Bobby Bhattacharjee
... receives ACKs that are not in the window, it should not generate a RST, but instead an empty packet with the correct sequence number. One of the tenets of the Internet design philosophy is the robustness principle: “be conservative in what you send, and liberal in what you accept,” and it is this pr ...
... receives ACKs that are not in the window, it should not generate a RST, but instead an empty packet with the correct sequence number. One of the tenets of the Internet design philosophy is the robustness principle: “be conservative in what you send, and liberal in what you accept,” and it is this pr ...
Network File System (NFS)
... In many NFS configurations, there are four RPC services responsible for supporting the system: port mapper Typically either rpcbind or portmap, this service is running on a known port (111). NFS was designed to publish itself to this system as a listening service. lock daemon Typically rpc.lockd, de ...
... In many NFS configurations, there are four RPC services responsible for supporting the system: port mapper Typically either rpcbind or portmap, this service is running on a known port (111). NFS was designed to publish itself to this system as a listening service. lock daemon Typically rpc.lockd, de ...
Reassembling
... Internet: if it is a reverse proxy acting on behalf of one or more Web servers. In this case the reverse proxy receives HTTP requests from external clients and forwards them to the actual Web server(s). In all other cases, though, it’s true that a proxy should not have a direct interface on the Inte ...
... Internet: if it is a reverse proxy acting on behalf of one or more Web servers. In this case the reverse proxy receives HTTP requests from external clients and forwards them to the actual Web server(s). In all other cases, though, it’s true that a proxy should not have a direct interface on the Inte ...
Rough Neuro-PSO Web Caching and XML Prefetching
... Web caching is able to reduce bandwidth utilization, network jamming, and network traffic because it stores the repeatedly requested content nearer to users [16]. Xu et al. in [10] proposed solutions by creating proxy management. The Caching dynamic content is obtained by generating data and persona ...
... Web caching is able to reduce bandwidth utilization, network jamming, and network traffic because it stores the repeatedly requested content nearer to users [16]. Xu et al. in [10] proposed solutions by creating proxy management. The Caching dynamic content is obtained by generating data and persona ...
File
... Returns a string containing information about the servlet, such as its author, version, and copyright. ...
... Returns a string containing information about the servlet, such as its author, version, and copyright. ...
Java Servlet - OpenLoop.com
... which run on the client side in web browsers, or for writing Internet applications. The Servlet API brings the power of Java to your servers,too. JavaTM Servlet technology provides web developers with a simple, consistent mechanism for extending the functionality of a web server and for accessing ex ...
... which run on the client side in web browsers, or for writing Internet applications. The Servlet API brings the power of Java to your servers,too. JavaTM Servlet technology provides web developers with a simple, consistent mechanism for extending the functionality of a web server and for accessing ex ...
Introduction CS 239 Security for Networks and System
... • Some serious, some not – “Serious” defined as attempting to gain ...
... • Some serious, some not – “Serious” defined as attempting to gain ...