Acceptable Use Policy
... d) Configuration of a mail server to accept and process third‐party messages for sending without user identification and authentication e) Hosting web pages advertised within "spam e‐mail" sent from another network ("spamvertising") f) Block Removal – If, as a result of a Client's actions, ETAN’s ma ...
... d) Configuration of a mail server to accept and process third‐party messages for sending without user identification and authentication e) Hosting web pages advertised within "spam e‐mail" sent from another network ("spamvertising") f) Block Removal – If, as a result of a Client's actions, ETAN’s ma ...
white paper
... Key executives in organizations are not necessarily directly opening emails with links / unknown PDFs. The executive’s assistants may be targeted to open links through social engineering, especially with interesting titles like “Last day to sign up for XYZ conference”. At which point, the device of ...
... Key executives in organizations are not necessarily directly opening emails with links / unknown PDFs. The executive’s assistants may be targeted to open links through social engineering, especially with interesting titles like “Last day to sign up for XYZ conference”. At which point, the device of ...
OWASP_Academies_Meeting_GR_presented
... Relatively simple challenges, mainly web exploits that involve JavaScript, PHP, web server misconfigurations, etc. Attempt to address the general idea behind certain network security issues, rather than providing a detailed set-up. Several real-world network attacks rely on the exploitation of ...
... Relatively simple challenges, mainly web exploits that involve JavaScript, PHP, web server misconfigurations, etc. Attempt to address the general idea behind certain network security issues, rather than providing a detailed set-up. Several real-world network attacks rely on the exploitation of ...
A New Service for Increasing the Effectiveness of Network Address Blacklists
... have been involved in some previous illicit activity. Such blacklists are often converted into filtering logic, fortifying the port-based policies of a firewall with malicious address blocks to be ignored in their entirety. To date, two common methods for formulating address-based blacklists have be ...
... have been involved in some previous illicit activity. Such blacklists are often converted into filtering logic, fortifying the port-based policies of a firewall with malicious address blocks to be ignored in their entirety. To date, two common methods for formulating address-based blacklists have be ...
the catalogue here
... Smart Protection Network cloud-based security, pattern files are managed in the cloud and not on your endpoints to free computing resources and optimize performance. Further customize your protection with add-on options for data protection, mobile security, and desktop virtualization—all ...
... Smart Protection Network cloud-based security, pattern files are managed in the cloud and not on your endpoints to free computing resources and optimize performance. Further customize your protection with add-on options for data protection, mobile security, and desktop virtualization—all ...
ARP Spoofing and Man in the Middle attack
... MAC address (i.e., the address of the network card) to one that the attacker can monitor. Because the ARP replies have been forged, the target computer sends frames that were meant for the original destination to the attacker’s computer first so the frames can be read. A successful ARP attempt is in ...
... MAC address (i.e., the address of the network card) to one that the attacker can monitor. Because the ARP replies have been forged, the target computer sends frames that were meant for the original destination to the attacker’s computer first so the frames can be read. A successful ARP attempt is in ...
Document
... the PATHWORKS client, and more commonly known as the PATHWORKS 32 client, that implemented much of DECnet Phase IV for DOS, and 16 and 32 bit Microsoft Windows platforms (all the way through to Windows Server 2003). https://store.theartofservice.com/itil-2011-foundation-complete-certification-kit-fo ...
... the PATHWORKS client, and more commonly known as the PATHWORKS 32 client, that implemented much of DECnet Phase IV for DOS, and 16 and 32 bit Microsoft Windows platforms (all the way through to Windows Server 2003). https://store.theartofservice.com/itil-2011-foundation-complete-certification-kit-fo ...
Aspects of Biological Evolution and Their
... provide a great deal of information to an attacker such as user ids and periods of activity on a system thus allowing for exploits based on social engineering (17, 19). ...
... provide a great deal of information to an attacker such as user ids and periods of activity on a system thus allowing for exploits based on social engineering (17, 19). ...
Security Assessment
... What is the potential impact of the vulnerability? What is the likelihood of the vulnerability being exploited? What should be done to mitigate the vulnerability? Give at least three options if possible Where should the mitigation be done? Who should be responsible for implementing the mitigations? ...
... What is the potential impact of the vulnerability? What is the likelihood of the vulnerability being exploited? What should be done to mitigate the vulnerability? Give at least three options if possible Where should the mitigation be done? Who should be responsible for implementing the mitigations? ...
LogMeIn Security – an In-Depth Look
... enable one or more of the extra security options that LogMeIn provides. One of these options is a sheet of printed One-Time-Passwords (OTPs). When the user enables the OTP option, he is required to print out a list of 9-character random passwords generated by the Gateway. Once this is done, subseque ...
... enable one or more of the extra security options that LogMeIn provides. One of these options is a sheet of printed One-Time-Passwords (OTPs). When the user enables the OTP option, he is required to print out a list of 9-character random passwords generated by the Gateway. Once this is done, subseque ...
Webinar Title - Websense Knowledge Bases
... 12. Does UAC on Windows 7 need to be disabled to install the client as it does in Vista? Yes it is recommended. 13. Once the client is installed and configured, is the configuration valid for all users of the computer? Yes. 14. Is there any reporting with this feature? Yes any traffic that is sent t ...
... 12. Does UAC on Windows 7 need to be disabled to install the client as it does in Vista? Yes it is recommended. 13. Once the client is installed and configured, is the configuration valid for all users of the computer? Yes. 14. Is there any reporting with this feature? Yes any traffic that is sent t ...
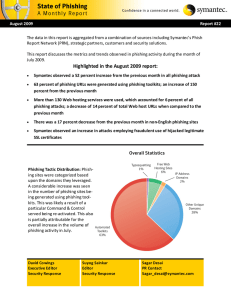
Highlighted in the August 2009 report
... padlock icon, while offering a false sense of security to the victims. In this particular attack, the certificates were legitimate because they matched the compromised legitimate domain. The fake pages that were spoofing the target brands in actuality had no connection with the displayed domain or t ...
... padlock icon, while offering a false sense of security to the victims. In this particular attack, the certificates were legitimate because they matched the compromised legitimate domain. The fake pages that were spoofing the target brands in actuality had no connection with the displayed domain or t ...
Tenable Malware Detection
... DNS entries, database access requests, web based attacks targeting web applications and suspect internet communications. Network sniffing is also an extremely useful tool when looking for botnet infiltration, and for the forensic analysis of what activity the bots in your environment have conducted. ...
... DNS entries, database access requests, web based attacks targeting web applications and suspect internet communications. Network sniffing is also an extremely useful tool when looking for botnet infiltration, and for the forensic analysis of what activity the bots in your environment have conducted. ...
Remote Access—Attack Vectors
... VPNs incorrectly used a corrupted route target (RT) to forward traffic, causing a leak—from one VPN to another. The solution to these leaks, aside from vendor patches, is hardening a system specifically to prevent route failures, DNS leaks and IP leaks outside a VPN connection, even after the prefer ...
... VPNs incorrectly used a corrupted route target (RT) to forward traffic, causing a leak—from one VPN to another. The solution to these leaks, aside from vendor patches, is hardening a system specifically to prevent route failures, DNS leaks and IP leaks outside a VPN connection, even after the prefer ...
Lecture Notes - Computer Science & Engineering
... Damage of the target may not reflect the real amount of damage Services may rely on the attacked service, causing a cascading and escalating damage Need: support for decision makers to – Evaluate risk and consequences of cyber attacks – Support methods to prevent, deter, and mitigate ...
... Damage of the target may not reflect the real amount of damage Services may rely on the attacked service, causing a cascading and escalating damage Need: support for decision makers to – Evaluate risk and consequences of cyber attacks – Support methods to prevent, deter, and mitigate ...
amisha
... monitor and analyze browsing activities * Cache can be used to block certain requests Web Caching ...
... monitor and analyze browsing activities * Cache can be used to block certain requests Web Caching ...
doc.gold.ac.uk
... Online Security Issues Overview • Early Internet days – Most popular use: electronic mail ...
... Online Security Issues Overview • Early Internet days – Most popular use: electronic mail ...
The Inexact Science of Internet Filtering for the K
... • live CDs/USB thumb drives to boot operating system free of filtering software or other restrictions • SSH port forwarding, tunneling/proxy software • cached results from search engines, web syndication services; web translations services • killing the filtering software processes GTRI_B-‹#› ...
... • live CDs/USB thumb drives to boot operating system free of filtering software or other restrictions • SSH port forwarding, tunneling/proxy software • cached results from search engines, web syndication services; web translations services • killing the filtering software processes GTRI_B-‹#› ...
Computer Science Illuminated, 3rd Edition
... True or False? An attribute is an HTML tag that links to another Web page. ...
... True or False? An attribute is an HTML tag that links to another Web page. ...
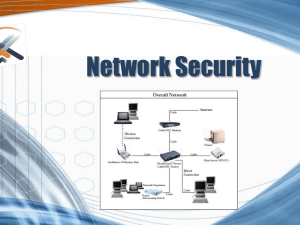
Network Security
... • The goal of access control is to prevent attackers from gaining access, and stops them if they do. • The best way to accomplish this is by: – Determine who needs access to the resources located on the server. – Decide the access permissions for each resource. – Implement specific access control po ...
... • The goal of access control is to prevent attackers from gaining access, and stops them if they do. • The best way to accomplish this is by: – Determine who needs access to the resources located on the server. – Decide the access permissions for each resource. – Implement specific access control po ...
071008
... The BufferedReader reads all characters sent by the server using readLine() and displays each line to System.out. July 10, 2008 ...
... The BufferedReader reads all characters sent by the server using readLine() and displays each line to System.out. July 10, 2008 ...
Spear Phishing Attacks—Why They are Successful and How to Stop
... There’s been a rapid and dramatic shift from broad, scattershot attacks to advanced targeted attacks that have had serious consequences for victim organizations. Some of the most famous advanced targeted attacks, such as the attack on RSA, on HBGary Federal, and Operation Aurora all used spear phish ...
... There’s been a rapid and dramatic shift from broad, scattershot attacks to advanced targeted attacks that have had serious consequences for victim organizations. Some of the most famous advanced targeted attacks, such as the attack on RSA, on HBGary Federal, and Operation Aurora all used spear phish ...
Introduction to Computer Security
... and disable “on-command” • Discovery of botnets with 10-100 systems is a daily occurrence; 10,000 system botnets are found almost weekly; and one botnet with 100,000 hosts has even been found (according to Johannes Ullrich, CTO of the Internet Storm Center). ...
... and disable “on-command” • Discovery of botnets with 10-100 systems is a daily occurrence; 10,000 system botnets are found almost weekly; and one botnet with 100,000 hosts has even been found (according to Johannes Ullrich, CTO of the Internet Storm Center). ...
Sohel Ahmed Syed Flat #402, Shivshankar 2, Contact Number: +91
... Mentoring and assisting the team for optimum performance towards individual’s contribution. Arranging trainings for the team on new technologies. Documenting the issues and their resolution, new techniques to achieve the complex workflows based on own investigation. Configuring different types of Au ...
... Mentoring and assisting the team for optimum performance towards individual’s contribution. Arranging trainings for the team on new technologies. Documenting the issues and their resolution, new techniques to achieve the complex workflows based on own investigation. Configuring different types of Au ...