Malware - UTK-EECS
... Encrypted and Polymorphic Virus A computer virus is code that copies itself into other programs so that it will be executed unbeknownst to the user. One implementation of a virus is the encrypted virus; a type of virus which copies both an encrypted copy of the virus and decryption instructions in t ...
... Encrypted and Polymorphic Virus A computer virus is code that copies itself into other programs so that it will be executed unbeknownst to the user. One implementation of a virus is the encrypted virus; a type of virus which copies both an encrypted copy of the virus and decryption instructions in t ...
Presentación de PowerPoint
... Applications need to identify multiple requests coming from the same user during the same session ...
... Applications need to identify multiple requests coming from the same user during the same session ...
cse 3pwrpoint
... Dynamic Webpage Programming with JavaScript Although HTML creates a webpage, it doesn’t allow the page to perform any actions such as when your are playing an online game and are having to click between different responses that pop up from the page. In order to do those dynamic formats you need to u ...
... Dynamic Webpage Programming with JavaScript Although HTML creates a webpage, it doesn’t allow the page to perform any actions such as when your are playing an online game and are having to click between different responses that pop up from the page. In order to do those dynamic formats you need to u ...
Servlet.ppt - Southern Methodist University
... • Client makes a request for a static resource • Web server responds with the static resource • HTTP is the standard protocol ...
... • Client makes a request for a static resource • Web server responds with the static resource • HTTP is the standard protocol ...
slides - WordPress.com
... • They internally send the request to a new page in the same application • Sometimes parameters define the target page • If not validated, attacker may be able to use unvalidated forward to bypass authentication or authorization checks Typical Impact • Redirect victim to phishing or malware site • A ...
... • They internally send the request to a new page in the same application • Sometimes parameters define the target page • If not validated, attacker may be able to use unvalidated forward to bypass authentication or authorization checks Typical Impact • Redirect victim to phishing or malware site • A ...
03-WAS Common Threats - Professional Data Management
... • Test all applications and any modification to application for security risks before rolling into production environment. • Routinely Audit for user accounts, configuration files and system files for the changes if any and ensure such changes have been authorized. • Purge all the logs after fixing ...
... • Test all applications and any modification to application for security risks before rolling into production environment. • Routinely Audit for user accounts, configuration files and system files for the changes if any and ensure such changes have been authorized. • Purge all the logs after fixing ...
to vulnerable site
... 4. Database runs query containing attack and sends encrypted results back to application 5. Application decrypts data as normal and sends results to the user ...
... 4. Database runs query containing attack and sends encrypted results back to application 5. Application decrypts data as normal and sends results to the user ...
Chapter 7 Review
... submissions to web site may contain malicious code that runs locally when others simple read the post. Serena suggests validating user input before following the user submissions. Which problem might validation solve? A. Cross-site scripting B. Fuzzing C. Hardening D. Patching ...
... submissions to web site may contain malicious code that runs locally when others simple read the post. Serena suggests validating user input before following the user submissions. Which problem might validation solve? A. Cross-site scripting B. Fuzzing C. Hardening D. Patching ...
Hostile Scripts (Zararlı Kod Parçacıkları)
... passersby can enter the house to request services. It is an open gateway that allows anyone anywhere to run an executable program on your server and even send their own programs to run on your server. An open window like this on a server is not the safest thing to have, and security issues are invol ...
... passersby can enter the house to request services. It is an open gateway that allows anyone anywhere to run an executable program on your server and even send their own programs to run on your server. An open window like this on a server is not the safest thing to have, and security issues are invol ...
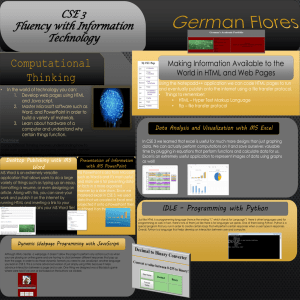
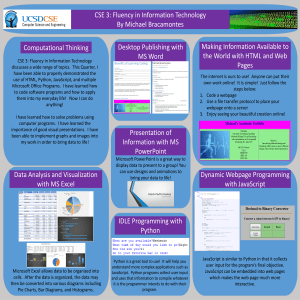
CSE 3 Poster
... Microsoft Excel allows data to be organized into cells. After the data is organized, the data may then be converted into various diagrams including Pie Charts, Bar Diagrams, and Histograms. ...
... Microsoft Excel allows data to be organized into cells. After the data is organized, the data may then be converted into various diagrams including Pie Charts, Bar Diagrams, and Histograms. ...
Chapter 7 Review
... web site may contain malicious code that runs locally when others simply read the post. Serena suggests validating user input before following the user submissions. Which problem might validation solve? A. Cross-site scripting B. Fuzzing C. Hardening D. Patching ...
... web site may contain malicious code that runs locally when others simply read the post. Serena suggests validating user input before following the user submissions. Which problem might validation solve? A. Cross-site scripting B. Fuzzing C. Hardening D. Patching ...
Compensation 101 - Christopher S. Foree
... lot of information in the client’s browser (e.g. cookies, cache) C. Since XSS relies on code that gets executed on a client’s browser, client-side data can be manipulated and hijacked, and the user can be redirected to malicious websites ...
... lot of information in the client’s browser (e.g. cookies, cache) C. Since XSS relies on code that gets executed on a client’s browser, client-side data can be manipulated and hijacked, and the user can be redirected to malicious websites ...
Maritime Cyber Vulnerabilities in the Energy Domain
... IT Systems • Shipboard computers are Linux based, and computers collect all the data into a storage center. – Inside database network server – Outside database network server via internet ...
... IT Systems • Shipboard computers are Linux based, and computers collect all the data into a storage center. – Inside database network server – Outside database network server via internet ...
Web Application Security
... etc. Site D can build a cross-site profile of browsing behavior Browsers now report if a cookie's URL differs from its origin there are sometimes legitimate reasons for this ...
... etc. Site D can build a cross-site profile of browsing behavior Browsers now report if a cookie's URL differs from its origin there are sometimes legitimate reasons for this ...
Web Application Security
... etc. Site D can build a cross-site profile of browsing behavior Browsers now report if a cookie's URL differs from its origin there are sometimes legitimate reasons for this ...
... etc. Site D can build a cross-site profile of browsing behavior Browsers now report if a cookie's URL differs from its origin there are sometimes legitimate reasons for this ...
Web Application Security Vulnerabilities Yen
... application components in some languages that do not properly validate input can be crashed and, in some cases, used to take control of a process. These components can include CGI, libraries, drivers, and web application server components. ...
... application components in some languages that do not properly validate input can be crashed and, in some cases, used to take control of a process. These components can include CGI, libraries, drivers, and web application server components. ...
pptx - cse.sc.edu
... • SQLi Attack: consists of tweaking the input fields of the web page (which can be visible or hidden) in order to alter the query sent to the back-end database. • XSS Attack: consists of injecting HTML and/or other scripting code (usually Javascript) in a vulnerable web page • E.g. Malicious adds, l ...
... • SQLi Attack: consists of tweaking the input fields of the web page (which can be visible or hidden) in order to alter the query sent to the back-end database. • XSS Attack: consists of injecting HTML and/or other scripting code (usually Javascript) in a vulnerable web page • E.g. Malicious adds, l ...
Web Application Security
... or introduce security problems. Attackers can tamper with any part of an HTTP request to try to bypass the site’s security mechanisms URL, query string, headers, cookies, form fields, hidden fields, etc. ...
... or introduce security problems. Attackers can tamper with any part of an HTTP request to try to bypass the site’s security mechanisms URL, query string, headers, cookies, form fields, hidden fields, etc. ...
Role of Web Application Vulnerabilities in Information
... Server side scan Detection of logical flaws Self learning capabilities Detection of server misconfiguration More of white box testing Learn from previous learning experience ...
... Server side scan Detection of logical flaws Self learning capabilities Detection of server misconfiguration More of white box testing Learn from previous learning experience ...
Document
... – Browser sends cookies – Appears as if the user made the request (clicked the link or filled out the form) ...
... – Browser sends cookies – Appears as if the user made the request (clicked the link or filled out the form) ...
WWW Lab1
... Introduce HTML basics. Take the “magic” out of the Internet. Demonstrate how to create and edit WEB pages. To discuss utility and ethical issues surrounding the creation and use of WWW Nets. ...
... Introduce HTML basics. Take the “magic” out of the Internet. Demonstrate how to create and edit WEB pages. To discuss utility and ethical issues surrounding the creation and use of WWW Nets. ...
網站安全 - 國立暨南國際大學
... mechanism to transport an attack to an end user's browser. • A successful attack can disclose the end user's session token, attack the local machine, or spoof content to fool the user. ...
... mechanism to transport an attack to an end user's browser. • A successful attack can disclose the end user's session token, attack the local machine, or spoof content to fool the user. ...
FLAX: Systematic Discovery of Client-Side Validation Vulnerabilities
... FLAX is a hybrid approach named a ‘taint enhanced ...
... FLAX is a hybrid approach named a ‘taint enhanced ...
Slides - CSE - USF - University of South Florida
... Detection Mechanisms for Broken Authentication and Session Management ...
... Detection Mechanisms for Broken Authentication and Session Management ...