REST
... REST stands for Representational State Transfer. (It is sometimes spelled "ReST".) It relies on a stateless, client-server, cacheable communications protocol -- and in virtually all cases, the HTTP protocol is used. REST is an architecture style for designing networked ...
... REST stands for Representational State Transfer. (It is sometimes spelled "ReST".) It relies on a stateless, client-server, cacheable communications protocol -- and in virtually all cases, the HTTP protocol is used. REST is an architecture style for designing networked ...
User Threat Quotient Brochure
... Security intelligence to spot risky users at a glance Today s network attacks center on the user, making users the weakest link in the security chain. Statistics reveal that 80% of security risks are caused by network users. A network generates huge amount of data. This data contains enough cues to ...
... Security intelligence to spot risky users at a glance Today s network attacks center on the user, making users the weakest link in the security chain. Statistics reveal that 80% of security risks are caused by network users. A network generates huge amount of data. This data contains enough cues to ...
User Threat Quotient (UTQ)
... Security intelligence to spot risky users at a glance Today s network attacks center on the user, making users the weakest link in the security chain. Statistics reveal that 80% of security risks are caused by network users. A network generates huge amount of data. This data contains enough cues to ...
... Security intelligence to spot risky users at a glance Today s network attacks center on the user, making users the weakest link in the security chain. Statistics reveal that 80% of security risks are caused by network users. A network generates huge amount of data. This data contains enough cues to ...
Web Server Administration
... A report can be produced to find out which files have been added, changed, and deleted ...
... A report can be produced to find out which files have been added, changed, and deleted ...
Web and HTTP
... Responding to Clients’ Inputs HTML pages are static documents Sometimes users supply input, for example, keywords submitted to a search engine The Web server has to react to this input • The output is an HTML page that is not known in advance In order to react to the input, the Web server may have ...
... Responding to Clients’ Inputs HTML pages are static documents Sometimes users supply input, for example, keywords submitted to a search engine The Web server has to react to this input • The output is an HTML page that is not known in advance In order to react to the input, the Web server may have ...
Organization of American States | Electoral Observation Missions
... Brochures Twitter Facebook Vimeo Flickr Documents o OAS Charter o Inter-American Democratic Charter o Social Charter of the Americas o Declarations and Resolutions General Assembly Regular Sessions Special Sessions Permanent Council o Treaties and Agreements o Library Collection o Document S ...
... Brochures Twitter Facebook Vimeo Flickr Documents o OAS Charter o Inter-American Democratic Charter o Social Charter of the Americas o Declarations and Resolutions General Assembly Regular Sessions Special Sessions Permanent Council o Treaties and Agreements o Library Collection o Document S ...
CS 494/594 Computer and Network Security - UTK-EECS
... Interception: some unauthorized party has gained access to information or resources, e.g., illicit copying of program or data files, wiretapping to obtain data in a network Interruption: information or resources become lost, unavailable, or unusable, e.g., malicious destruction of a hardware devic ...
... Interception: some unauthorized party has gained access to information or resources, e.g., illicit copying of program or data files, wiretapping to obtain data in a network Interruption: information or resources become lost, unavailable, or unusable, e.g., malicious destruction of a hardware devic ...
CS 494/594 Computer and Network Security - UTK-EECS
... Interception: some unauthorized party has gained access to information or resources, e.g., illicit copying of program or data files, wiretapping to obtain data in a network Interruption: information or resources become lost, unavailable, or unusable, e.g., malicious destruction of a hardware devic ...
... Interception: some unauthorized party has gained access to information or resources, e.g., illicit copying of program or data files, wiretapping to obtain data in a network Interruption: information or resources become lost, unavailable, or unusable, e.g., malicious destruction of a hardware devic ...
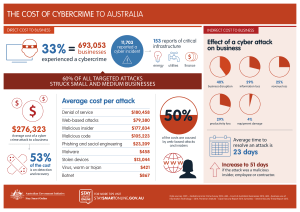
the cost of cybercrime to australia $276323
... Data sources: PWC – Global Economic Crime Survey 2014; ABS – Count of Australian Businesses 2014; ABS – Business use of Information Technology – 2014; Ponemon Institute – Cyber Security Report 2014; Symantec – Internet Security Threat Report 2015. ...
... Data sources: PWC – Global Economic Crime Survey 2014; ABS – Count of Australian Businesses 2014; ABS – Business use of Information Technology – 2014; Ponemon Institute – Cyber Security Report 2014; Symantec – Internet Security Threat Report 2015. ...
ppt - School of Engineering and Computer Science
... • sends header information Content-type: text/html Content-length: 3022 ...
... • sends header information Content-type: text/html Content-length: 3022 ...
SQLrand: Preventing SQL Injection Attacks
... This study surveys the mechanism that is suggested Boyd and Keromytis in 2004, SQLrand: Preventing SQL Injection Attacks. The study presents a functional protection mechanism to prevent SQL injection attacks that are reachable “through a web front-end, and take advantage of flaws in the input valida ...
... This study surveys the mechanism that is suggested Boyd and Keromytis in 2004, SQLrand: Preventing SQL Injection Attacks. The study presents a functional protection mechanism to prevent SQL injection attacks that are reachable “through a web front-end, and take advantage of flaws in the input valida ...
Web basics - s3.amazonaws.com
... Domain Name – Who owns this site? Other examples are yahoo.com,Toyota.com. You buy these! ...
... Domain Name – Who owns this site? Other examples are yahoo.com,Toyota.com. You buy these! ...
PowerPoint
... Neither browser was interested in standards But the need became obvious to web developers ...
... Neither browser was interested in standards But the need became obvious to web developers ...
Shibboleth Access Management System
... that are available freely available for students to download The site also includes lesson plans, discussion questions, and tests that accompany the freely available materials. These materials should only be available to educators. ...
... that are available freely available for students to download The site also includes lesson plans, discussion questions, and tests that accompany the freely available materials. These materials should only be available to educators. ...
Lesson 2: Markup Language and Site Development Essentials
... • To publish a site, you need to know: – The IP address and/or DNS name of the site – User name and authentication information – The destination directory (i.e., folder) on the Web server ...
... • To publish a site, you need to know: – The IP address and/or DNS name of the site – User name and authentication information – The destination directory (i.e., folder) on the Web server ...
User Glossary
... Registered Users: Registered users are individuals who have registered to a site and provide some personal information. Router: A device that forwards data packets along networks. A router is connected to at least two networks, commonly two LANs or WANs or a LAN and its ISP’s network. Routers are l ...
... Registered Users: Registered users are individuals who have registered to a site and provide some personal information. Router: A device that forwards data packets along networks. A router is connected to at least two networks, commonly two LANs or WANs or a LAN and its ISP’s network. Routers are l ...
Security Overview
... – This is a difficult attack to start with for the hacker – Hacker should be able to guess correctly the Initial Sequence Number that the spoofed IP would generate – To prevent IP spoofing, disable source routing on all internal routers – Filter entering packets with a source address of the local ne ...
... – This is a difficult attack to start with for the hacker – Hacker should be able to guess correctly the Initial Sequence Number that the spoofed IP would generate – To prevent IP spoofing, disable source routing on all internal routers – Filter entering packets with a source address of the local ne ...
Use of AI algorithms in design of Web Application Security Testing
... What else could be done, but isn’t (yet) Introduction to YAWATT ...
... What else could be done, but isn’t (yet) Introduction to YAWATT ...
APL and Web Services
... and data that’s largely unavailable for use outside of APL. There is quite a bit more nonAPL-based functionality and data that’s largely unavailable for use within APL. APLers are generally better at solving problems than designing user interfaces. ...
... and data that’s largely unavailable for use outside of APL. There is quite a bit more nonAPL-based functionality and data that’s largely unavailable for use within APL. APLers are generally better at solving problems than designing user interfaces. ...
History of the Web
... browsing editing, email, and so on. He invents the mouse for this purpose. Ted Nelson coins the word Hypertext in A File Structure for the Complex, the Changing, and the Indeterminate. 20th National Conference, Andy van Dam and others build the Hypertext Editing System and FRESS in 1967. ...
... browsing editing, email, and so on. He invents the mouse for this purpose. Ted Nelson coins the word Hypertext in A File Structure for the Complex, the Changing, and the Indeterminate. 20th National Conference, Andy van Dam and others build the Hypertext Editing System and FRESS in 1967. ...
Presentation 2
... .ascx pages which are reusable components, are independent of parent page. user controls are easy to add to any web page once you created combine the other controls to create user ...
... .ascx pages which are reusable components, are independent of parent page. user controls are easy to add to any web page once you created combine the other controls to create user ...
Tara and Orcun
... Web Application Vulnerability Scanning searches for software vulnerabilities within web applications: ...
... Web Application Vulnerability Scanning searches for software vulnerabilities within web applications: ...
Open Source Software
... Disadvantages • More diversity and less coherence • Lack of formal support from a vendor • Modifiable ...
... Disadvantages • More diversity and less coherence • Lack of formal support from a vendor • Modifiable ...